Method and apparatus implementing remote access control based on portable memory apparatus
A portable storage and remote access technology, applied in the field of remote access control, can solve problems such as heavy burden on application servers, attacks, and increased risk of application servers, and achieve the effect of reducing authentication burden and preventing authentication blocking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
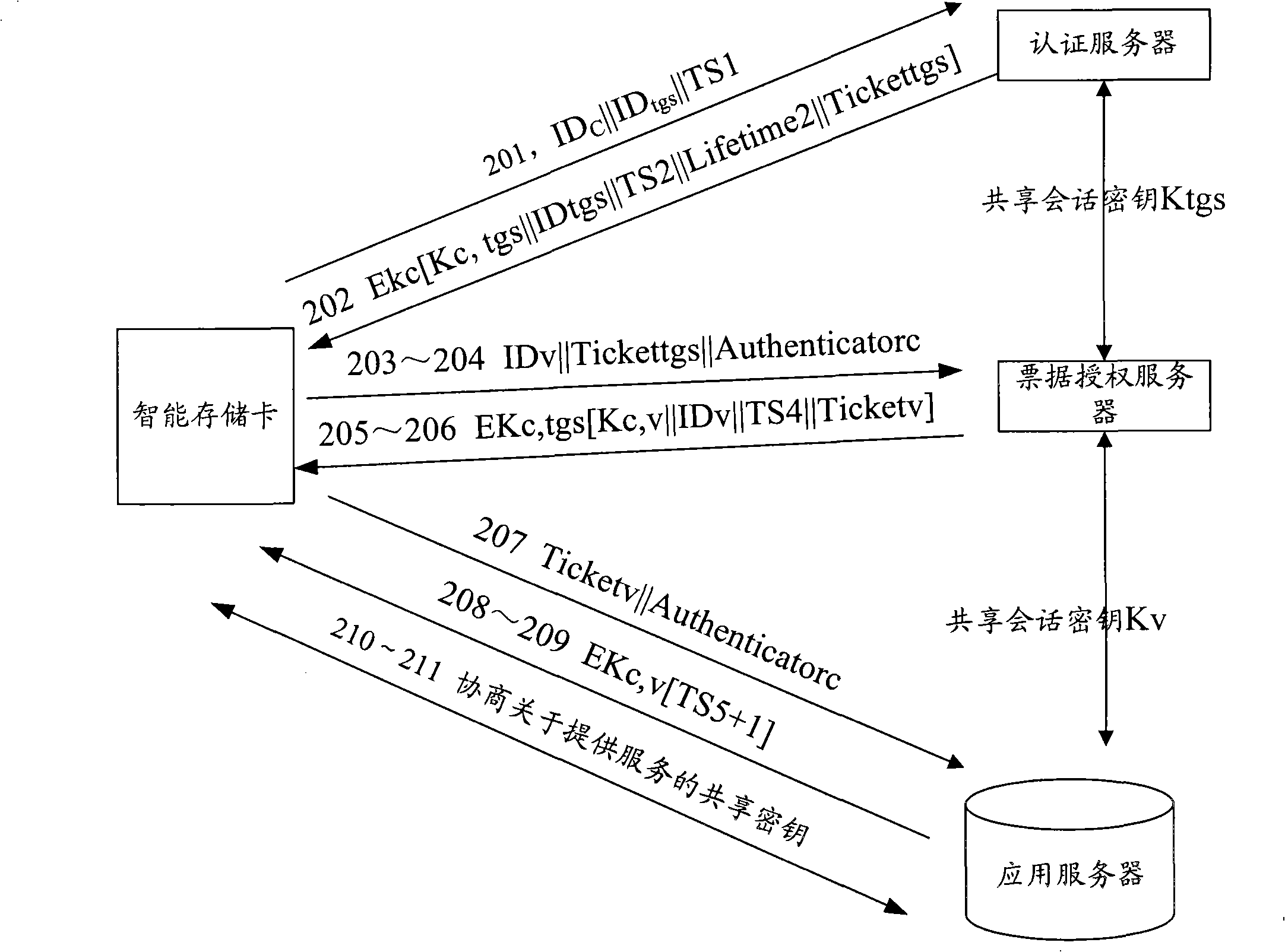
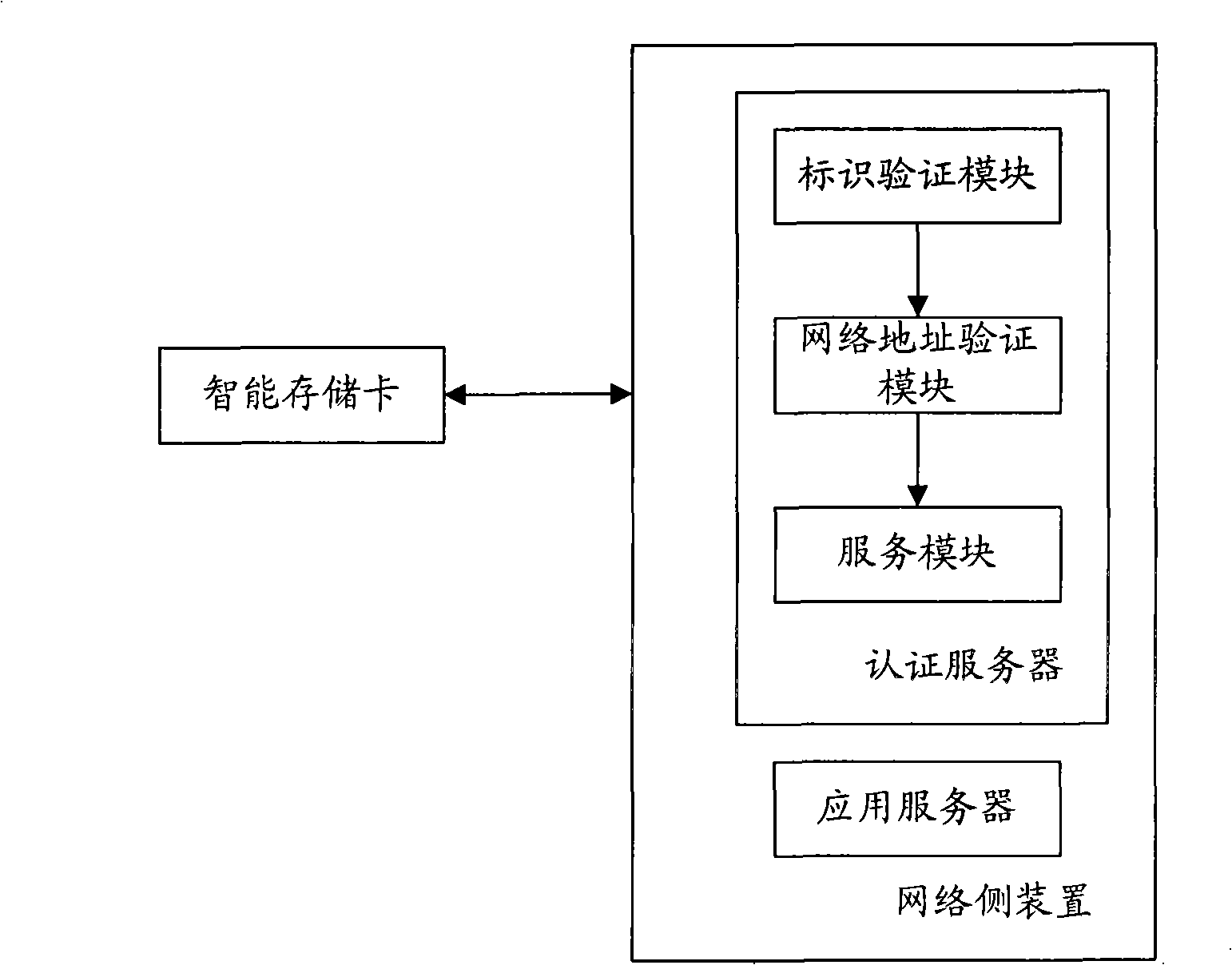
Image
Examples
example 1
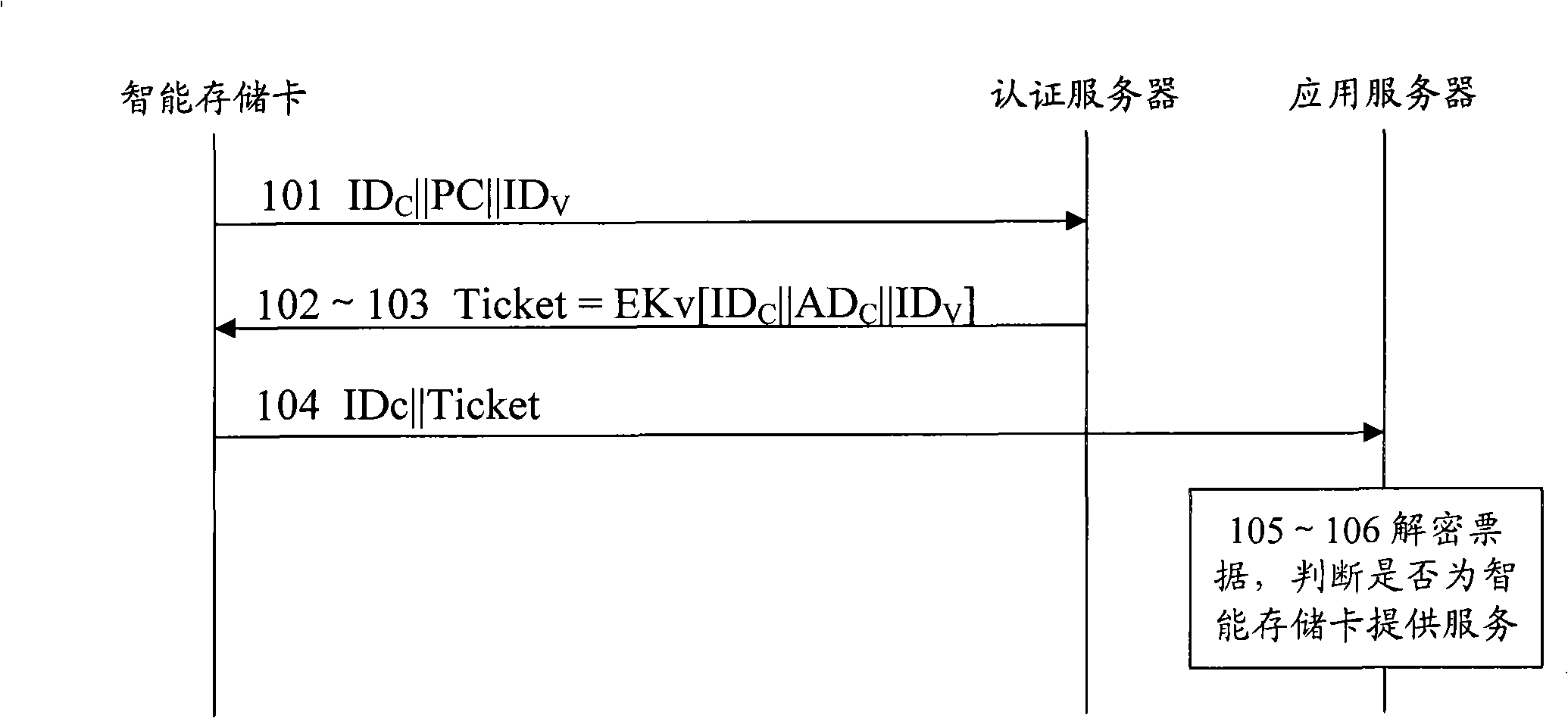
[0040] see figure 1 , which is a flowchart example 1 of a method for realizing remote access control based on a portable storage device in the present invention, including the following steps:
[0041] Step 101, the smart memory card sends an access request message to the AS.
[0042] When the user wants to log in to the workstation to request the application server to provide services, he inserts the smart memory card into the workstation and enters the PIN for starting the smart memory card. After the smart memory card is started, it sends an access request message to the AS. Here, for simplicity of description, C represents the smart memory card, and V represents the application server.
[0043] The access request message includes the ID of the smart memory card (ID C ), the identification of the application server to be accessed by the smart memory card (ID V ) and the PC corresponding to the self-identification stored in the smart memory card. PC can be a long passwor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com