Patents
Literature
251 results about "Computer access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
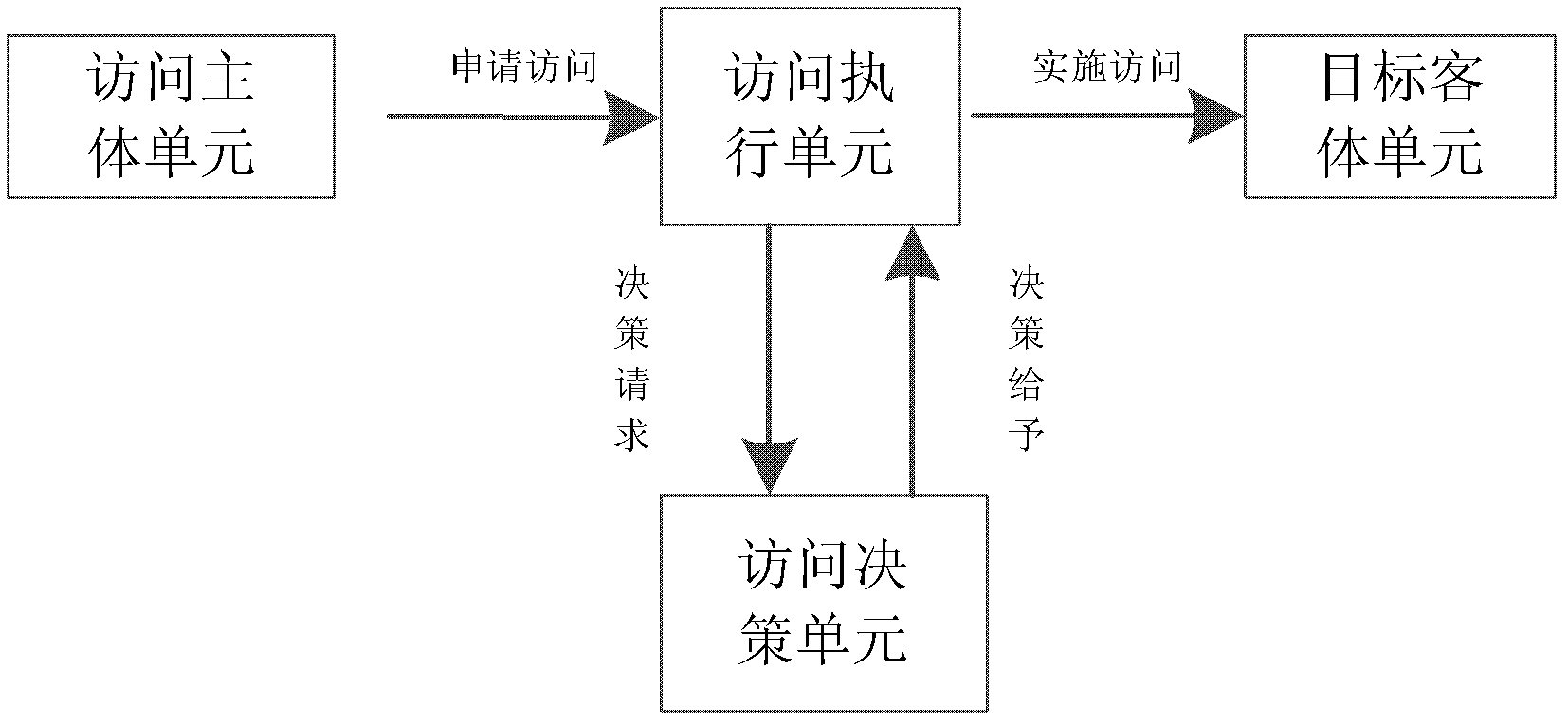
In computer security, general access control includes identification, authorization, authentication, access approval, and audit. A more narrow definition of access control would cover only access approval, whereby the system makes a decision to grant or reject an access request from an already authenticated subject, based on what the subject is authorized to access. Authentication and access control are often combined into a single operation, so that access is approved based on successful authentication, or based on an anonymous access token. Authentication methods and tokens include passwords, biometric scans, physical keys, electronic keys and devices, hidden paths, social barriers, and monitoring by humans and automated systems.
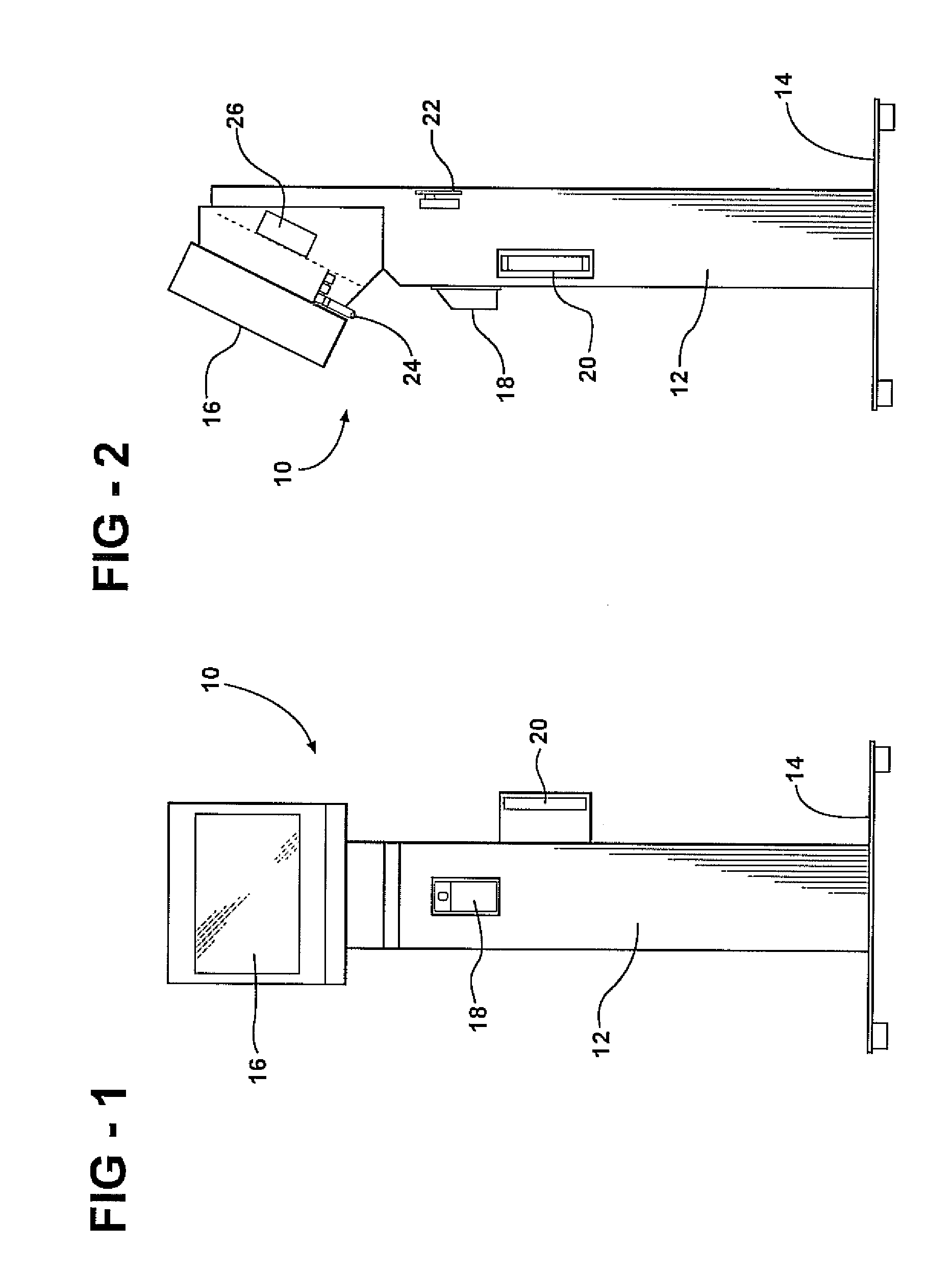
Method and apparatus for providing secure access control for protected information
InactiveUS20070136603A1Quick fixComputer security arrangementsSecuring communicationInternet privacyHigh assurance
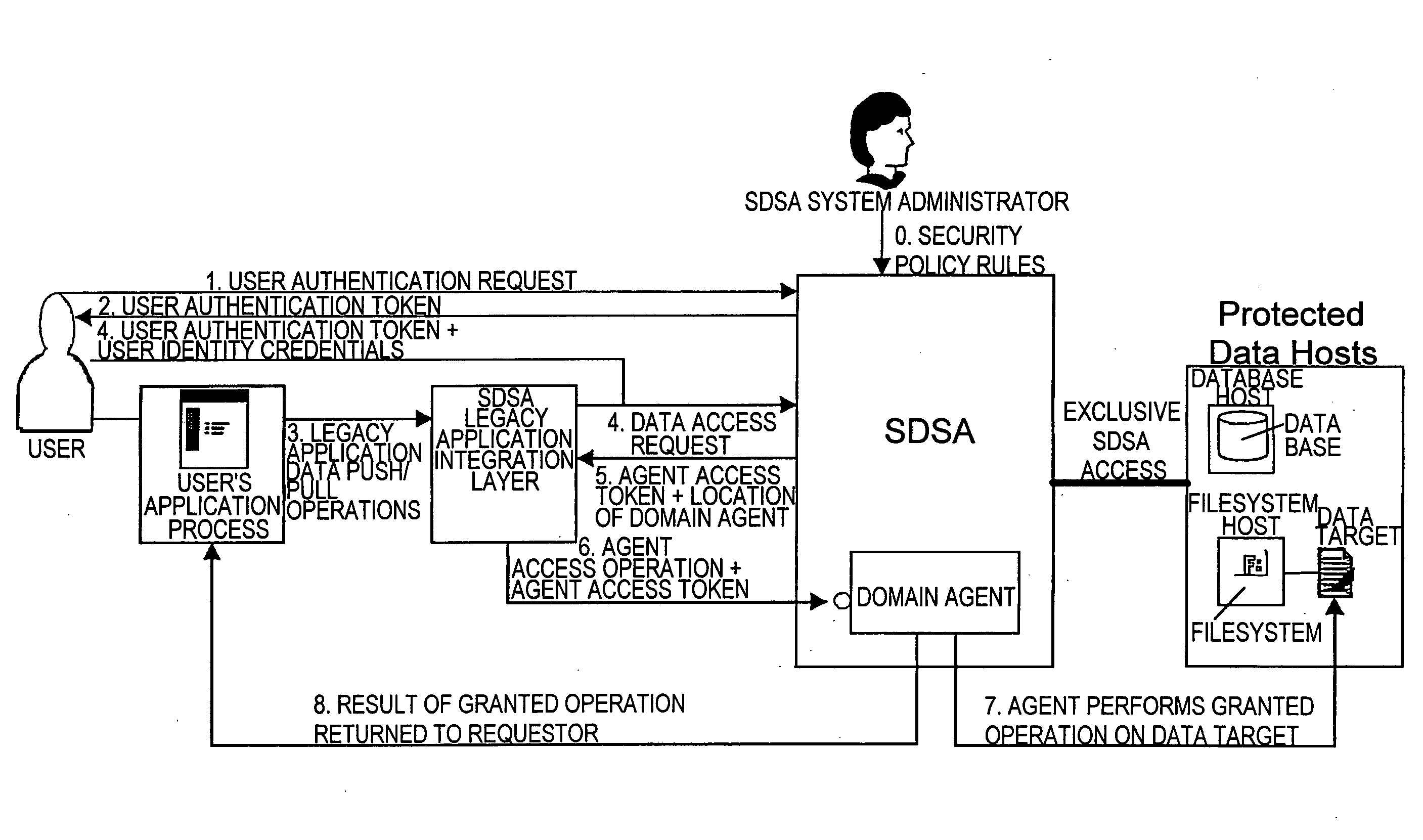
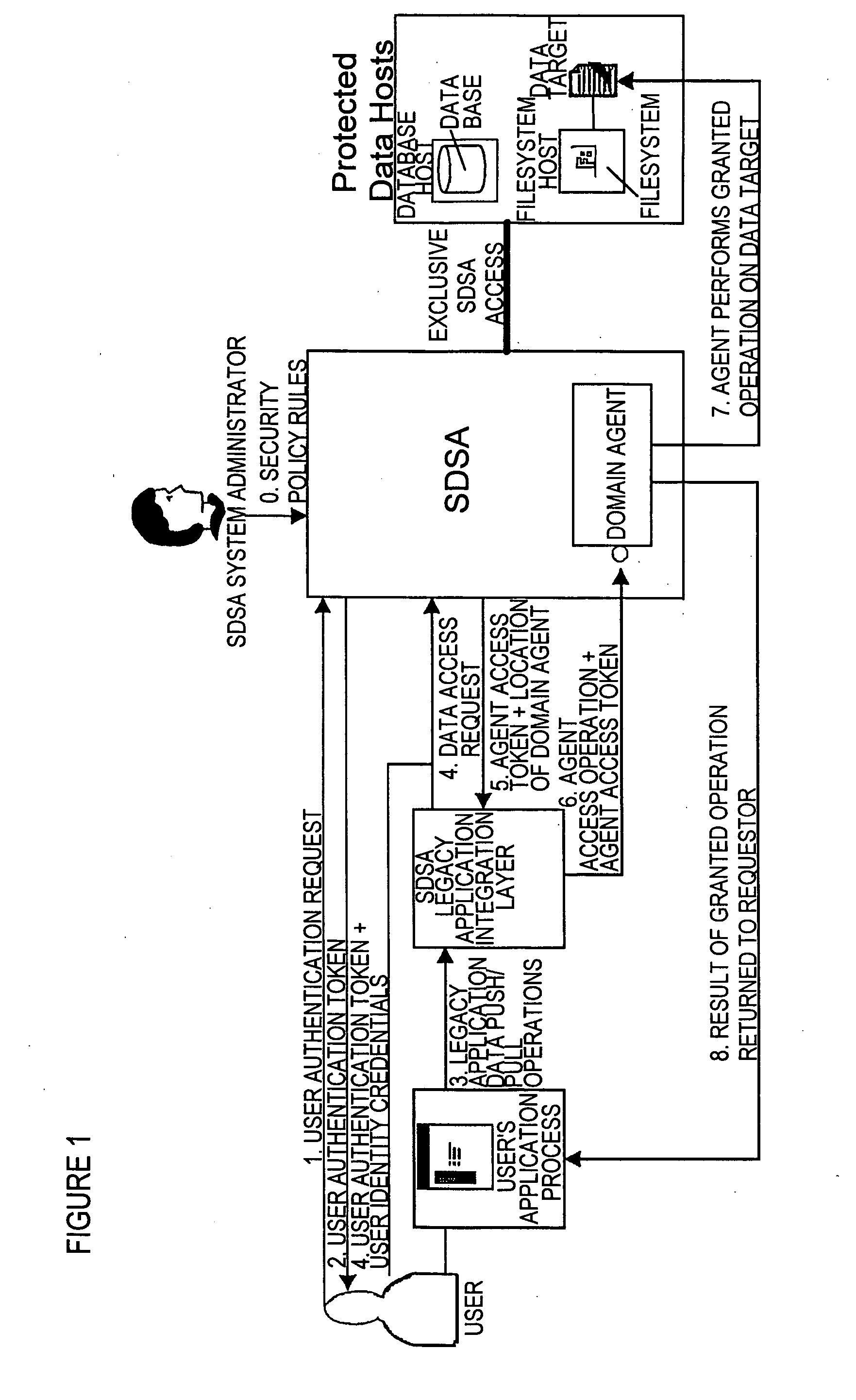
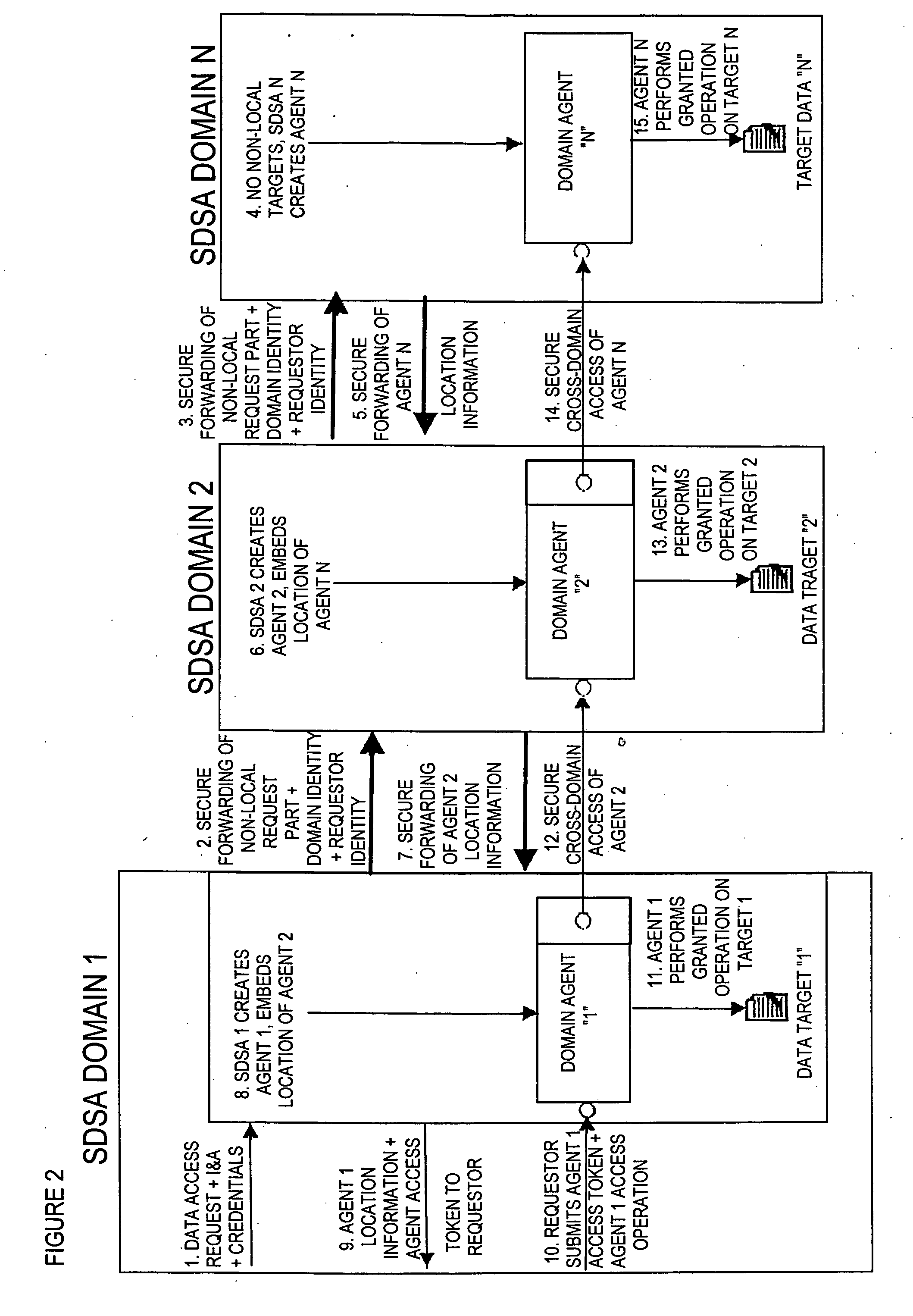
There are provided methods and apparatuses for processing requests from requestors, methods and apparatuses for transmitting indicia representative of information from a first domain to a second domain, methods comprising, and apparatuses for, determining whether a requestor is authorized to perform a desired operation on a target comprising at least one element which comprises an information set of indicia and arrangements of stored data, as well as computer-readable media having computer-executable commands for performing the same. In some aspects of the present invention, there are provided high-assurance data security apparatuses and methods, in particular, user data protection via enforcement of policy-based access control.
Owner:SENSIS CORPORATION
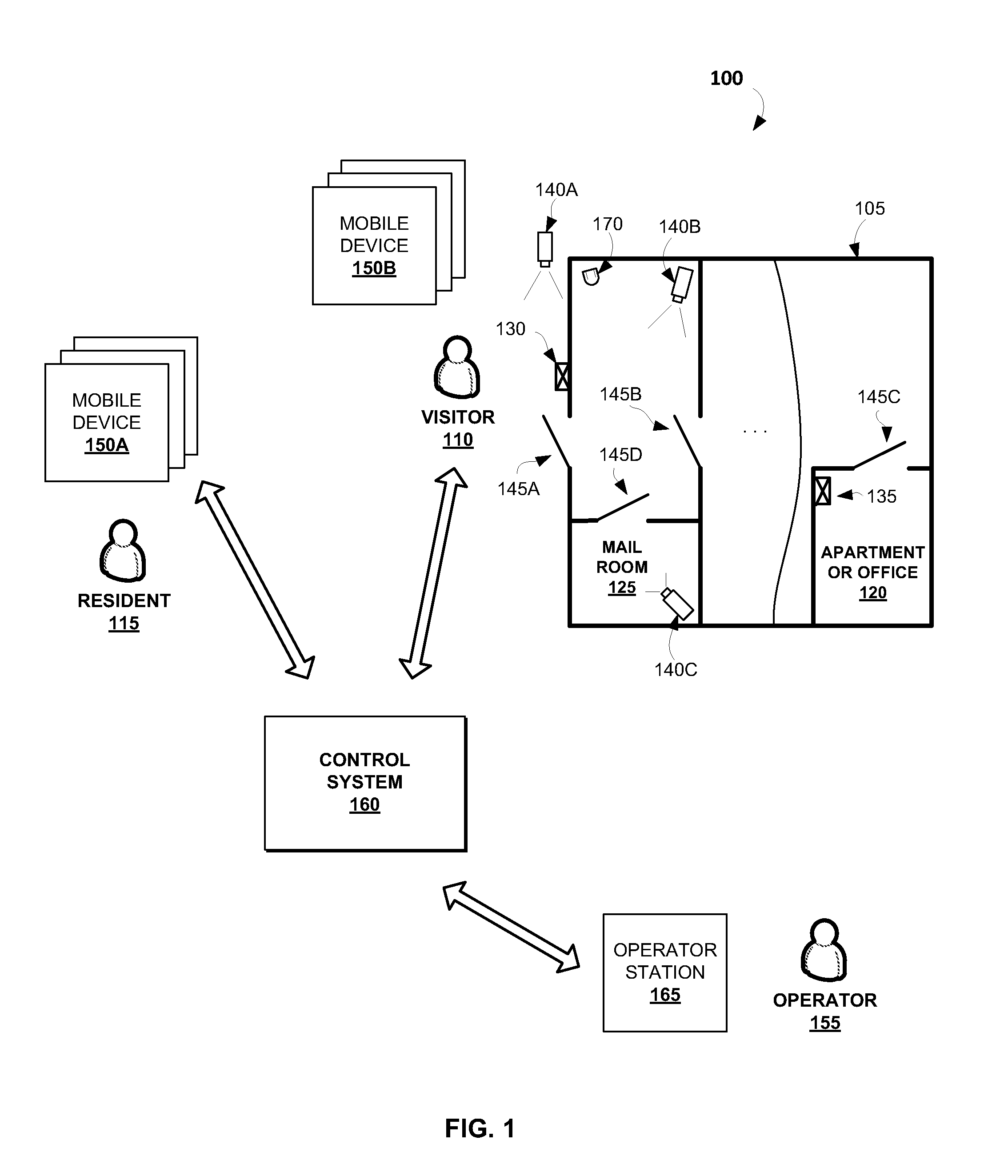
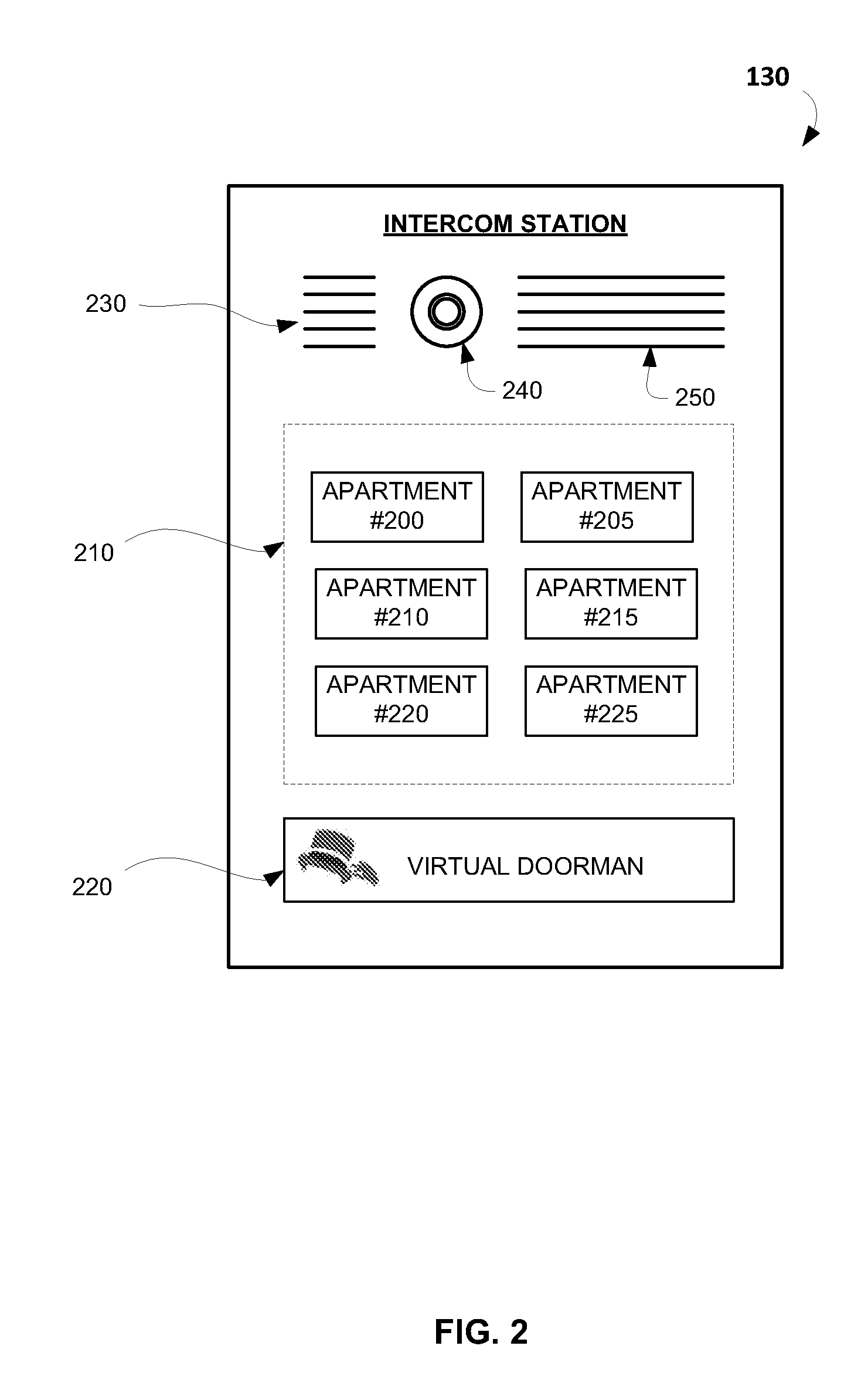
Remote access control to residential or office buildings
InactiveUS20130017812A1Efficient methodEliminate needElectric signal transmission systemsDigital data processing detailsRemote controlIntercom
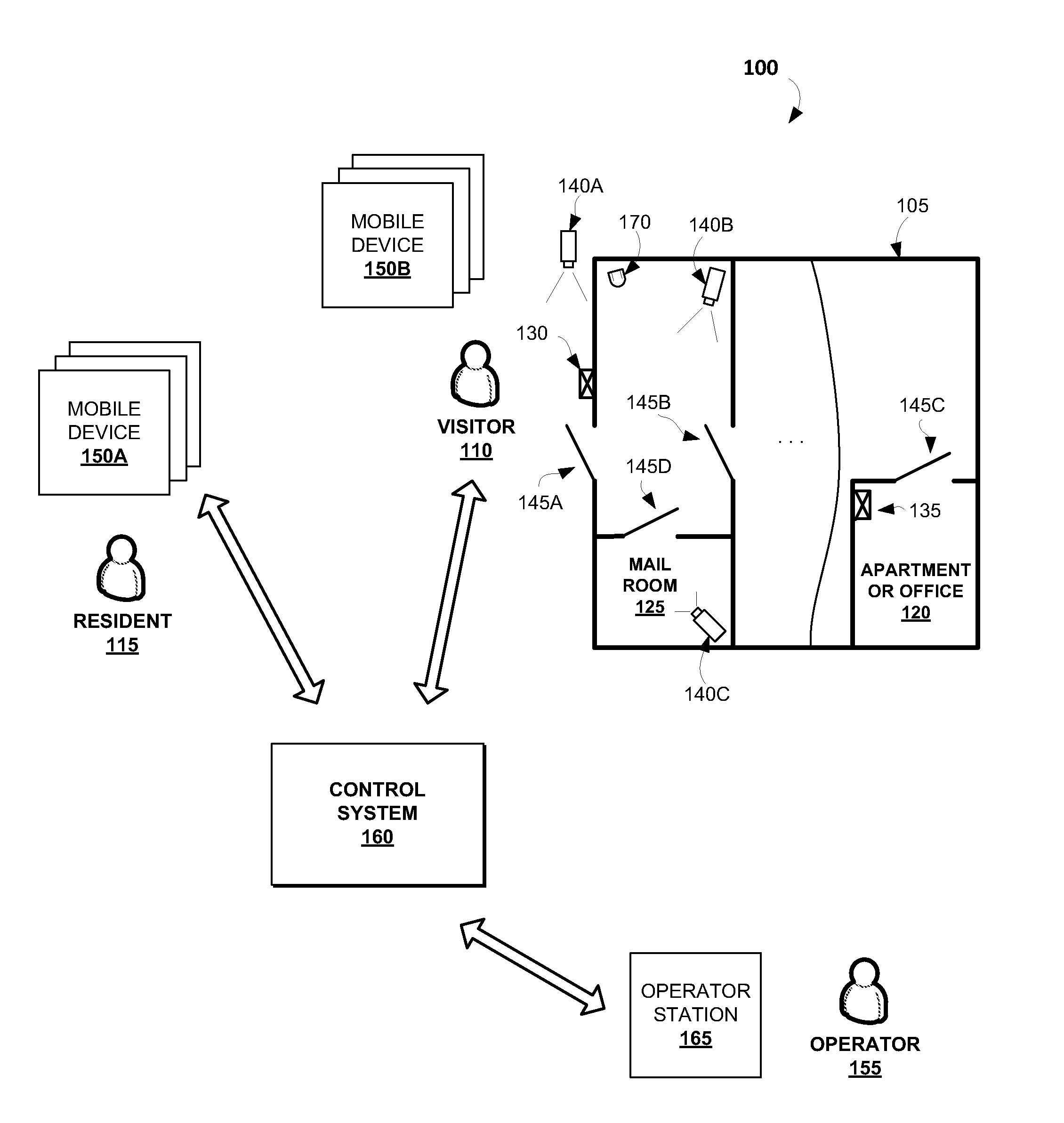
Disclosed are computer-implemented methods and systems for providing remote access control to residential or office buildings. The disclosed methods allow employing virtual doorman functions in non-doorman buildings. An example method may comprise: receiving a call signal of an intercom station, the call signal comprising a resident identifier which indicates a resident with whom a visitor is trying to communicate, receiving a video stream generated by at least one camera, the video stream comprising one or more images of the visitor, retrieving visitor data associated with the resident identifier, the visitor data comprising one or more visitor profiles, and providing access to the building for the visitor based upon one or more predetermined criteria.
Owner:FOSTER COLIN
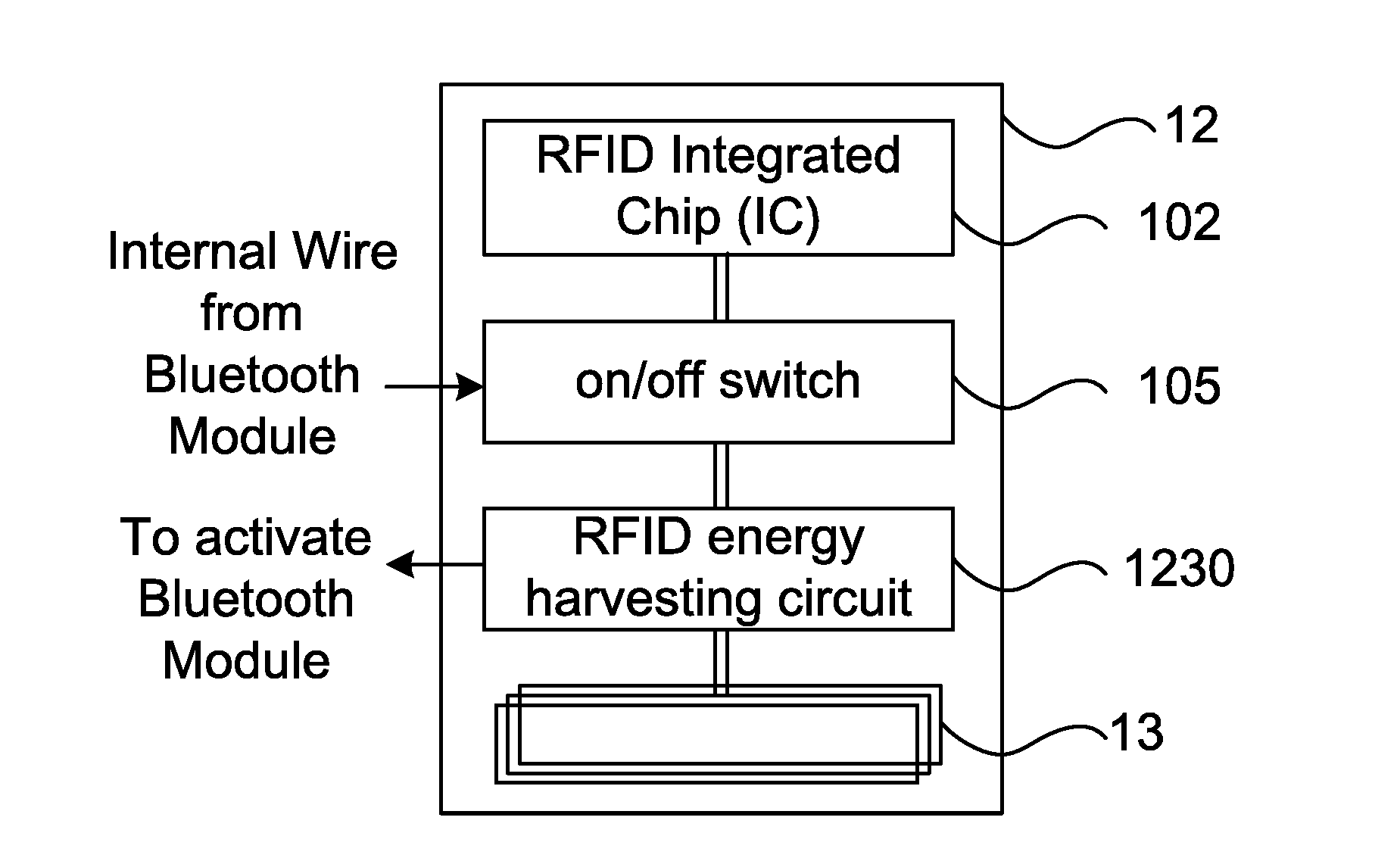
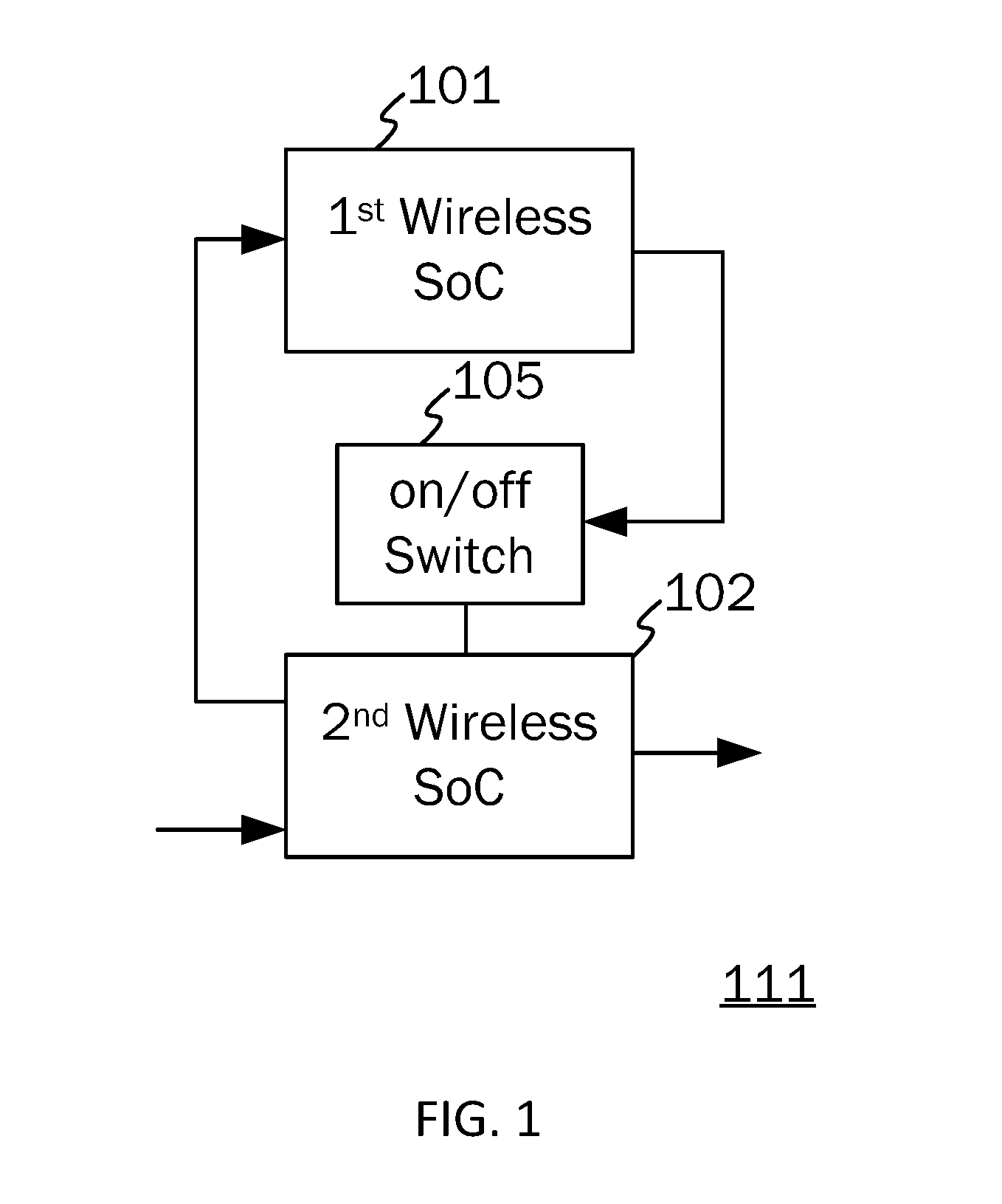
Cross-platform automated perimeter access control system and method adopting selective adapter
InactiveUS20160241999A1Extend battery lifeTurn easilyNon-electrical signal transmission systemsNear-field in RFIDControl systemOpto electronic
Integrated cross-platform perimeter access control system with a RFID-to-Bluetooth selective adapter configured with a RFID lock, a wireless communication conversion unit configured for operating under a first wireless communication platform and a second wireless communication platform, and a smartphone is disclosed. RFID-to-Bluetooth selective adapter is installed above sensor area of RFID lock to facilitate RFID lock to interrogate the RFID-to-Bluetooth selective adapter. RFID-to-Bluetooth selective adapter equipped with photo sensor unit can be turned on in a contactless manner using smartphone with camera light source. Methods adapted for short-range or long range space / room management automation, transportation vehicle rental management, and automated vehicle parking lot management are included. Low-power infrared proximity sensing circuit of infrared type having an infrared transmitter and receiver unit or of capacitive type having a metal plate can be added to the RFID-to-Bluetooth selective adapter so that the RFID reader can be actuated to perform RFID signal reading.
Owner:POLARIS TECH GLOBAL
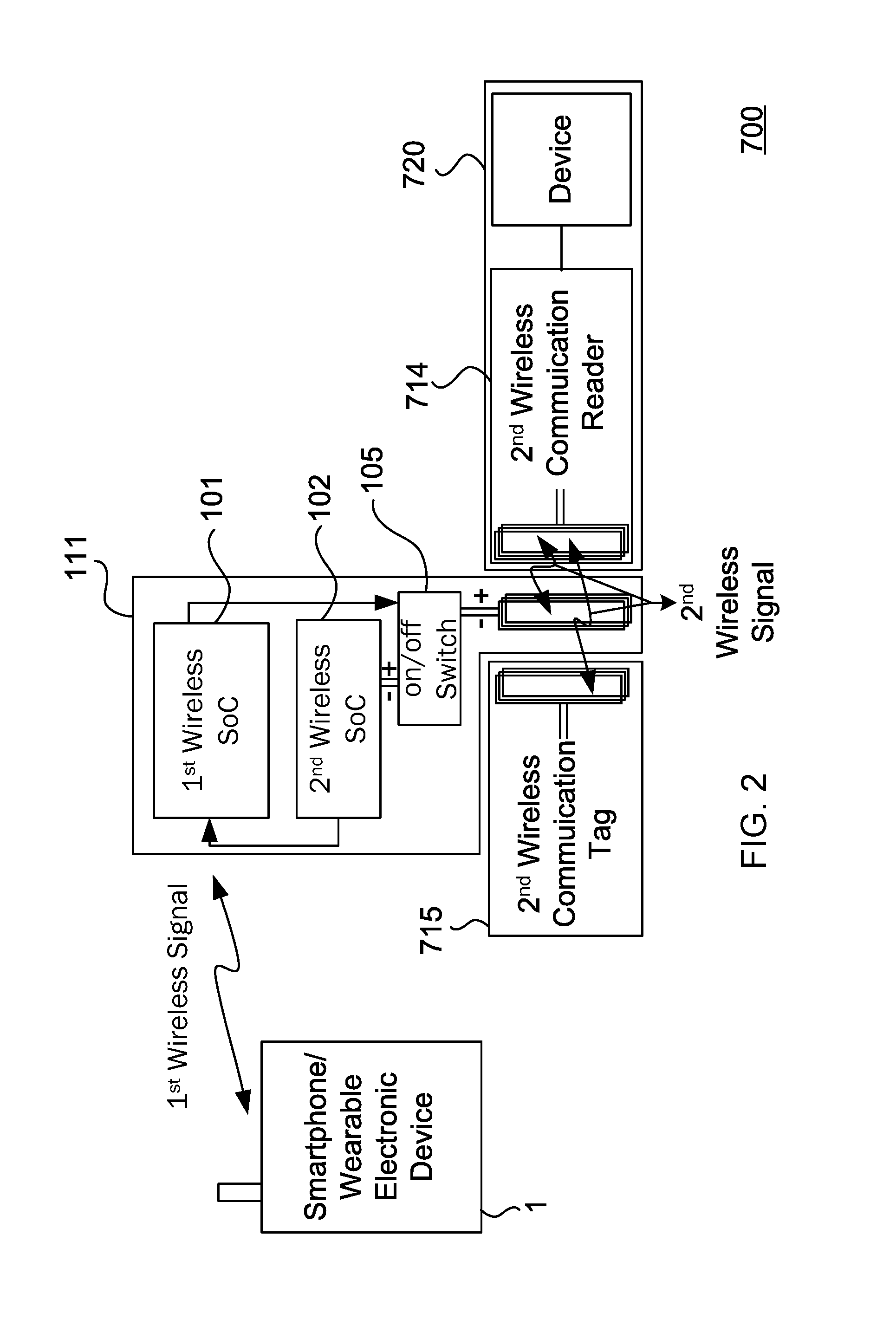
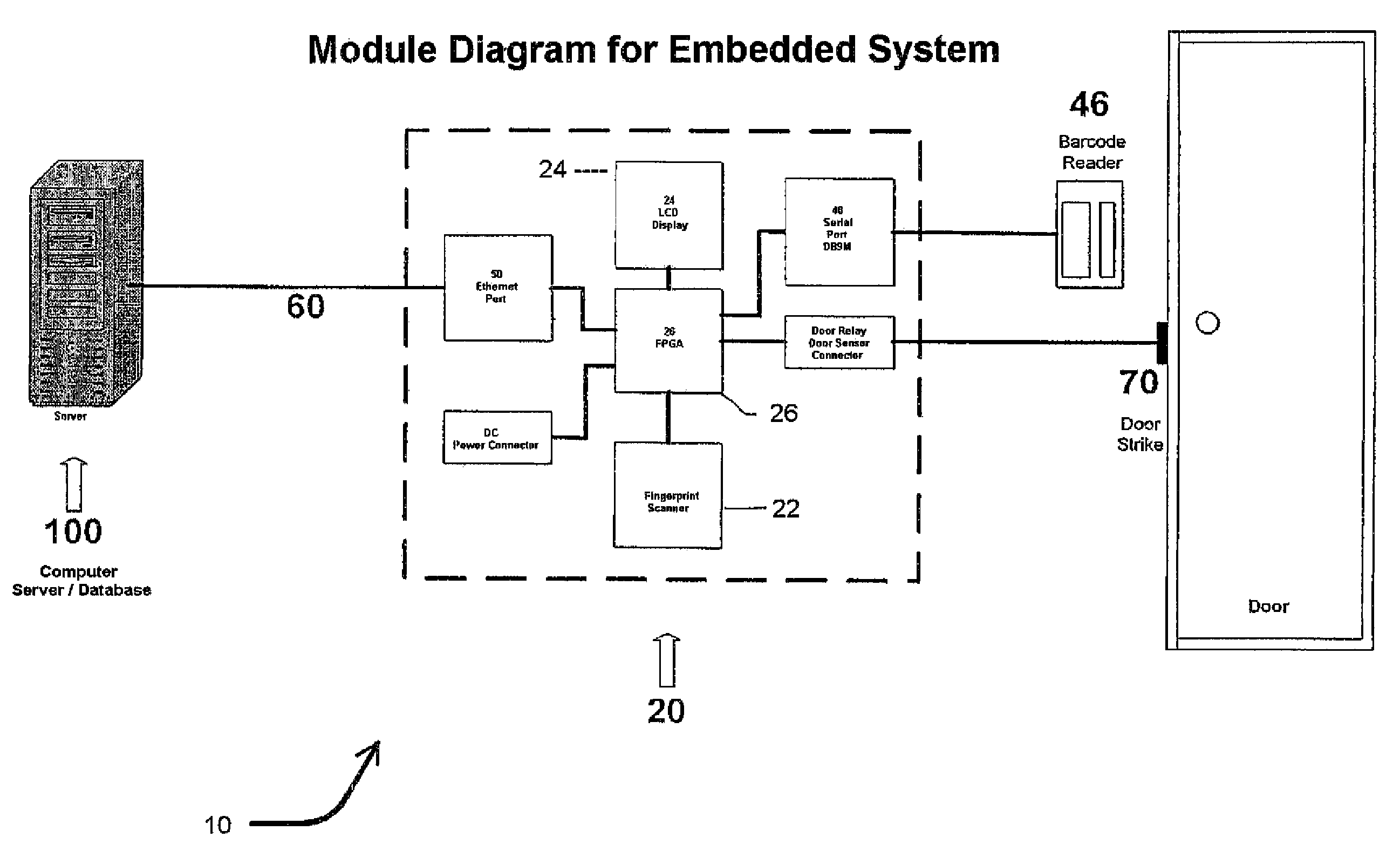
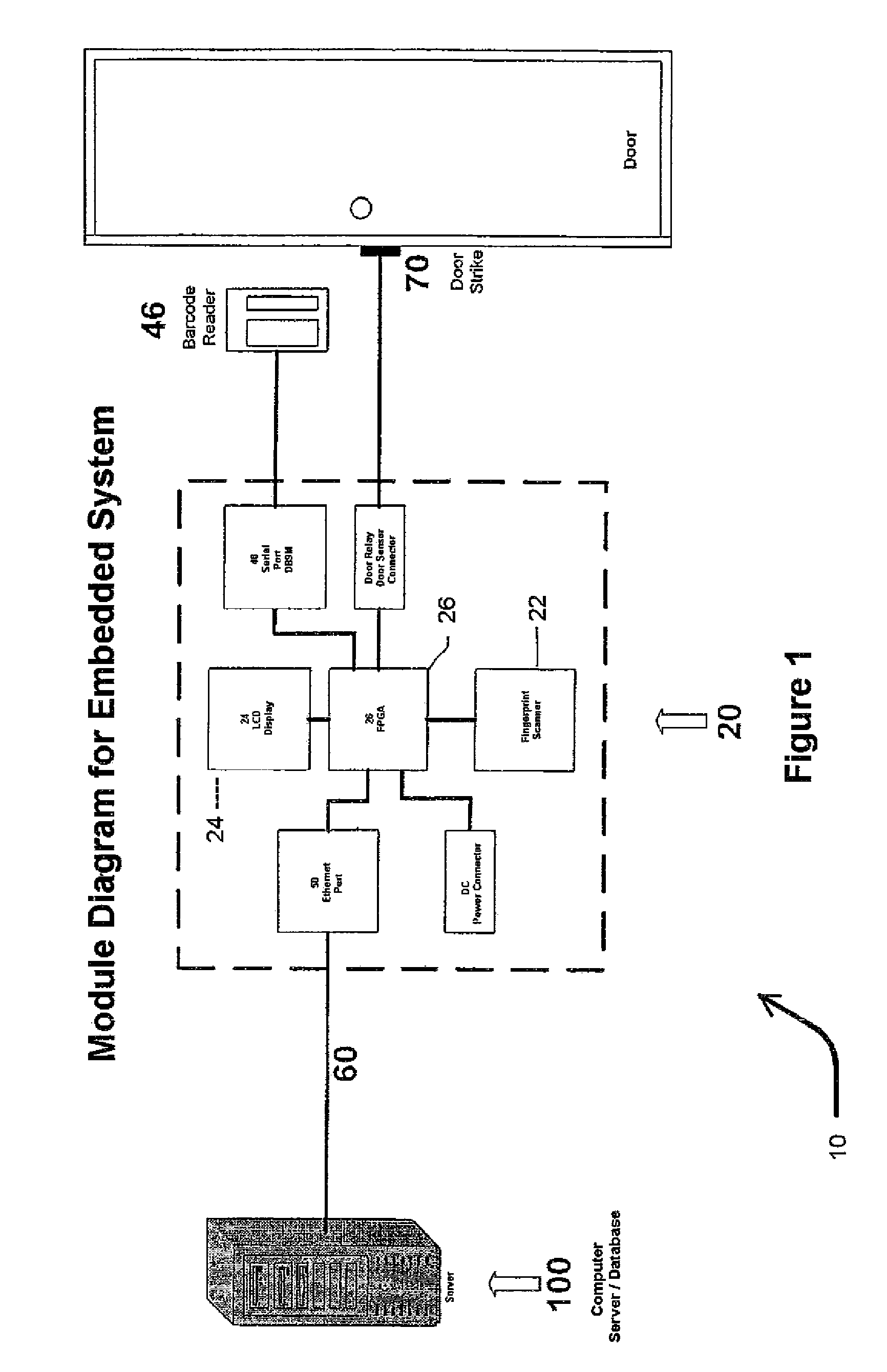
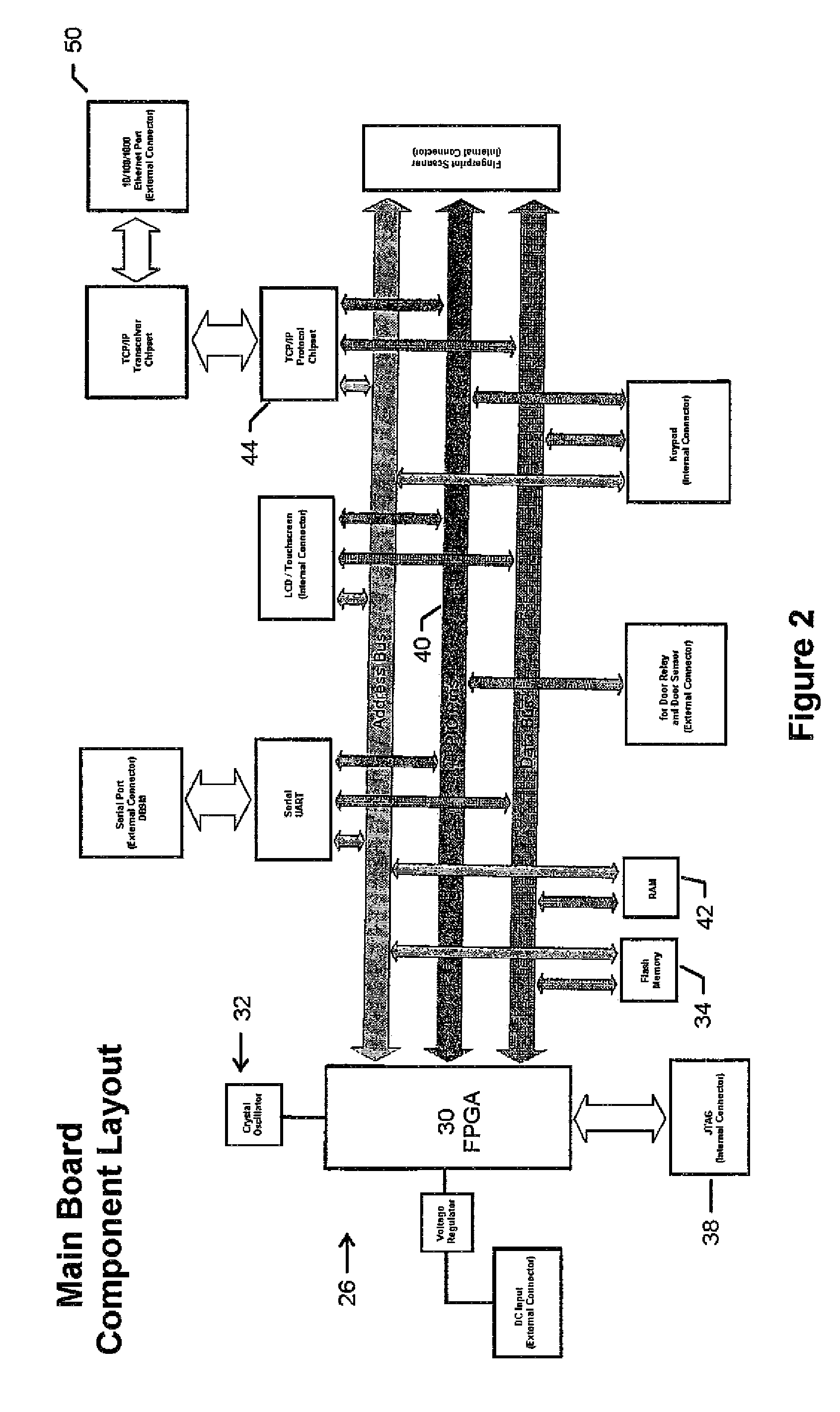
Biometric access control and time and attendance network including configurable system-on-chip (CSOC) processors with embedded programmable logic
ActiveUS7424618B2Compact efficient designCost efficient designElectric signal transmission systemsDigital data processing detailsHard disc driveHuman interaction
A biometric access control and time and attendance system comprises an integrated network including one or more remote access devices in electronic communication with a computer database. Each remote access device comprises a silicon chip based system and preferably includes a biometric input device, a liquid crystal display (LCD), computer processing capabilities based on embedded system architecture with configurable system-on-chip (CSOC) technology, and an electrical output for controlling a door lock or the like. The use of CSOC architecture in lieu of conventional personal computer technology (e.g. mother boards, hard drives, video controllers and the like) allows for a more compact and cost efficient design. A plurality of remote access devices is configured for communication with a primary computer database wherein data corresponding to biometric samples for all authorized users is stored. In an embodiment wherein the biometric input devices comprise fingerprint scanners, the devices are configured to facilitate fingerprint identification by incorporating an auto-targeting capability that enables the user to simply place his or her finger on the fingerprint scanner whereafter the system adjusts the scanned image by automatically shifting the scanned image data to a properly targeted position thereby enabling the system compare the scanned print to the biometric samples in the system's data storage memory. Auto-targeting capability eliminates the requirement for manual targeting present in systems of the background art thereby improving system performance and minimizing reliance on human interaction. The present invention contemplates the use of auto-targeting with other biometric systems, such as facial recognition and / or retinal scanning systems, or any other biometric identification technology.
Owner:PROFILE SOLUTIONS
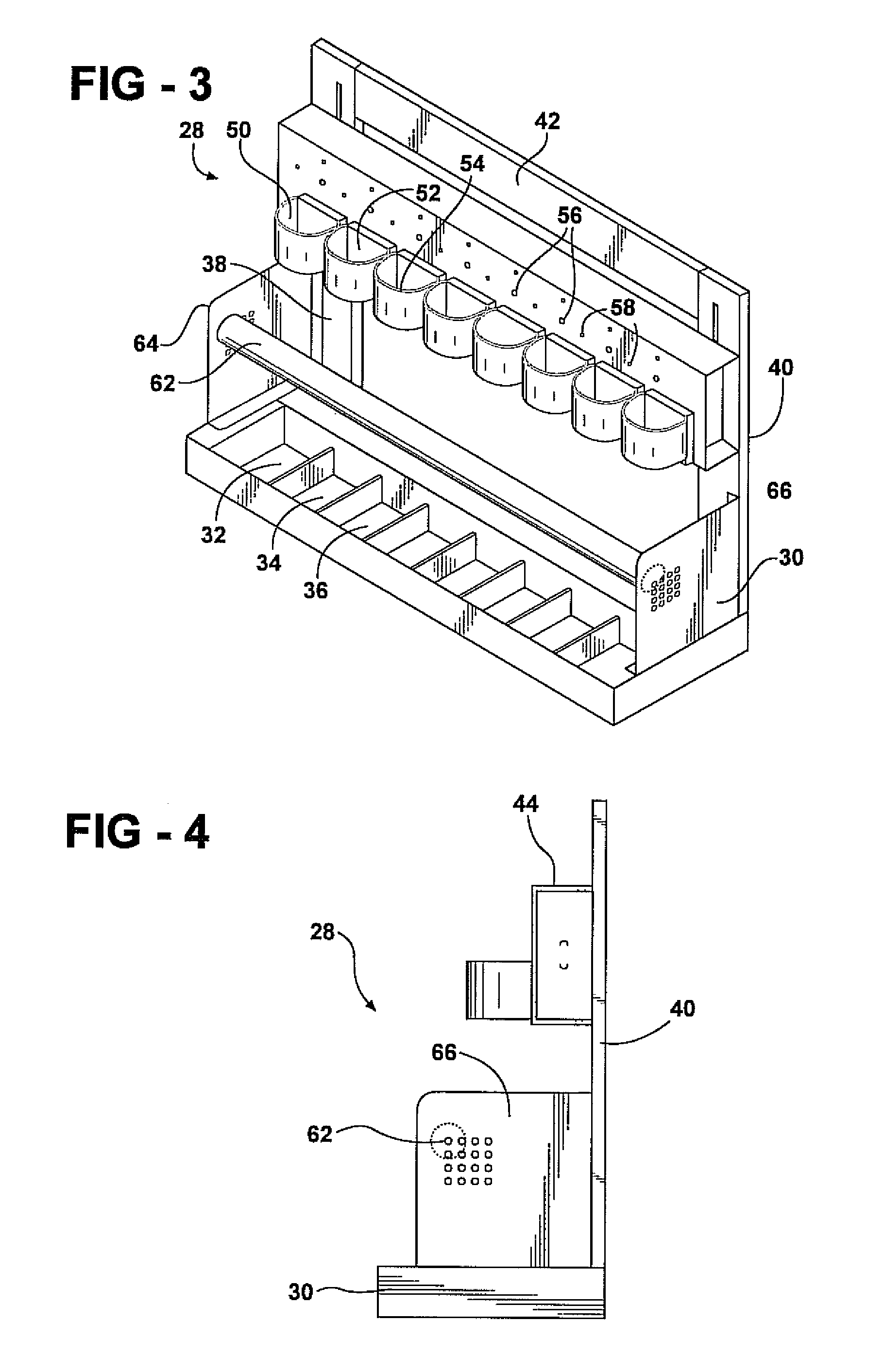
Biometric access control system
ActiveUS8207816B2Electric signal transmission systemsDigital data processing detailsLocking mechanismControl system
A biometric access control system for tracking critical assets and including an ID station incorporating a biometric input reader, an RFID antenna and reader and a wired or wireless (Bluetooth) communication device. A remotely positioned structure includes either or both of a rack or a locker for holding a plurality of the critical assets in individually locked fashion. A processor control built into the ID station operatively actuates each of a plurality of individual locking mechanisms incorporated into the rack structure or locker, in response to successive biometric and weapon selection inputs communicating with the processor, and for determining at least one of user identification and weapon release authorization prior to the processor actuating the locking mechanism to release the weapon. An associated computer writeable medium operates with the processor and establishes a series of subroutines for establishing user identification, weapons rating, selective weapon release / reentry and associated maintenance and record keeping log reports.
Owner:LAW ENFORCEMENT INTELLIGENT DEVICES
Biometric access control system incorporating a touchscreen accessible and kiosk based id station operating in combination with multiple critical asset retaining racks and locers for permitting selective biometric input and processor driven/wireless release authorization, maintenance and inventory control of any plurality of critical assets and including an associated computer writeable medium operating with the id station for enabling asset release, reentry and associated inventory control
ActiveUS20080252414A1Quick ViewElectric signal transmission systemsDigital data processing detailsLocking mechanismControl system
A biometric access control system for tracking critical assets and including an ID station incorporating a biometric input reader, an RFID antenna and reader and a wired or wireless (Bluetooth) communication device. A remotely positioned structure includes either or both of a rack or a locker for holding a plurality of the critical assets in individually locked fashion. A processor control built into the ID station operatively actuates each of a plurality of individual locking mechanisms incorporated into the rack structure or locker, in response to successive biometric and weapon selection inputs communicating with the processor, and for determining at least one of user identification and weapon release authorization prior to the processor actuating the locking mechanism to release the weapon. An associated computer writeable medium operates with the processor and establishes a series of subroutines for establishing user identification, weapons rating, selective weapon release / reentry and associated maintenance and record keeping log reports.
Owner:LAW ENFORCEMENT INTELLIGENT DEVICES
Computer access control using password reset
ActiveUS20080022393A1Access controlDigital data processing detailsUnauthorized memory use protectionComputer usersPassword
The present invention relates to a method for method or system which is able to control access to a new computer user password reset. The system is preloaded with a random password that does not needed to be known by anyone. There are two main situations in which this method will be used. The first situation involves a locally managed password and account where the user does not log in to a domain. The second situation involves remote management, where the user logs in to a domain.
Owner:LENOVO PC INT
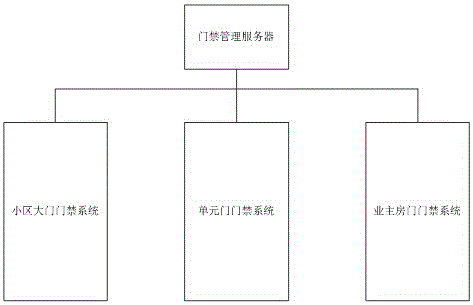
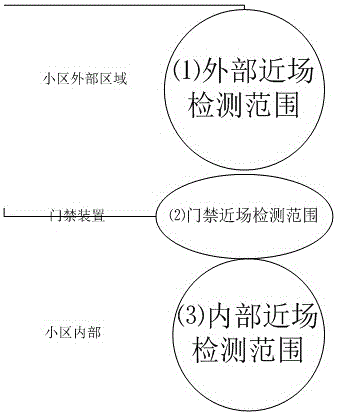
Community access control system and method
ActiveCN105761339AEasy to useImprove reliabilityIndividual entry/exit registersSystems managementArrival time
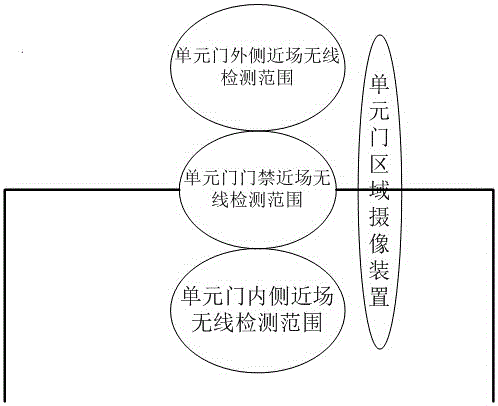
The invention discloses a community access control system and method. The community access control system comprises community gate access control, unit gate access control, proprietor gate access control and an access management server, wherein the community gate access control realizes proprietor identity verification, fellow visitor identification and visitor registration functions; the unit gate access control realizes user arrival time pre-judgment, elevator dispatching and visitor walking navigation functions; the proprietor gate access control realizes proprietor identity verification and proprietor trip reminder functions. The invention provides a brand new access control system management plan, which is a full set of safety access control solutions for the process from going out to backing home, and provides multiple humanization functions to improve the user experience. The time when a user arrives at a unit gate is pre-judged, and an elevator is dispatched in advance for waiting. The destination floor of the elevator can be automatically set for going up and down. When the visitor arrives on the destination floor, the walking navigation route can be broadcasted by voice, so that the high-end atmospheric grade effect is achieved. An indoor partition authorized visit function is realized, so that the proprietor has no need to worry about maintenance workers entering the room to maintain when the proprietor is not at home.
Owner:CHENGDU BILSUM SCI & TECH DEVCO
Remote access control system based on terminal fingerprint identification
InactiveCN103136820AEasy to useFulfil requirementsCharacter and pattern recognitionIndividual entry/exit registersElectronic accessUser needs
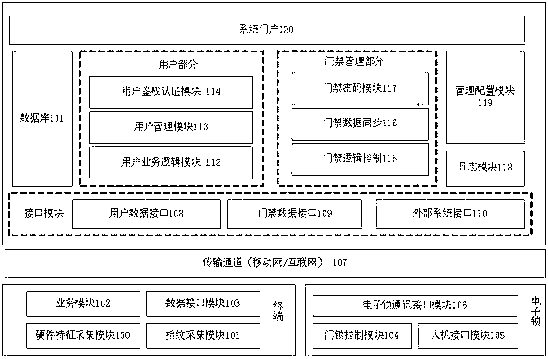
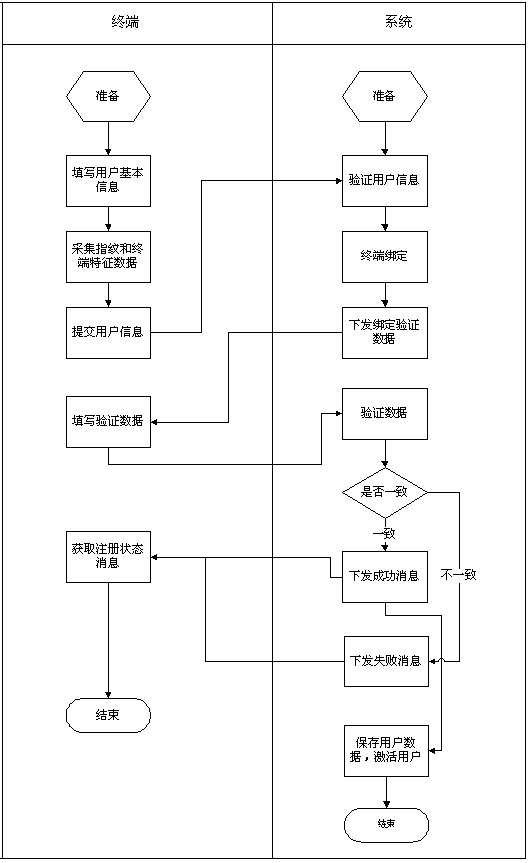
The invention discloses a remote access control system based on terminal fingerprint identification. The remote access control system comprises a mobile terminal, a service logic module, a fingerprint verification module, an access control module. According to the remote access control system, the mobile terminal provided with a fingerprint collection device is used for collecting fingerprints of users, registration and terminal binding are conducted in the system, when a user needs an access permission, the user real-timely requests at a terminal, the system judges fingerprint data and terminal data of the user and endows the user the corresponding access permission after verification, and the user uses a password to open an access or uses the system to open the access in a remote mode after obtaining the permission. The remote access control system collects the fingerprints of the users and distributes electronic door lock permissions to the users in a remote mode through the system so as to provide the users a convenient and quick electronic access control access method.
Owner:SHANGHAI BOLU INFORMATION TECH
Door access control system and method
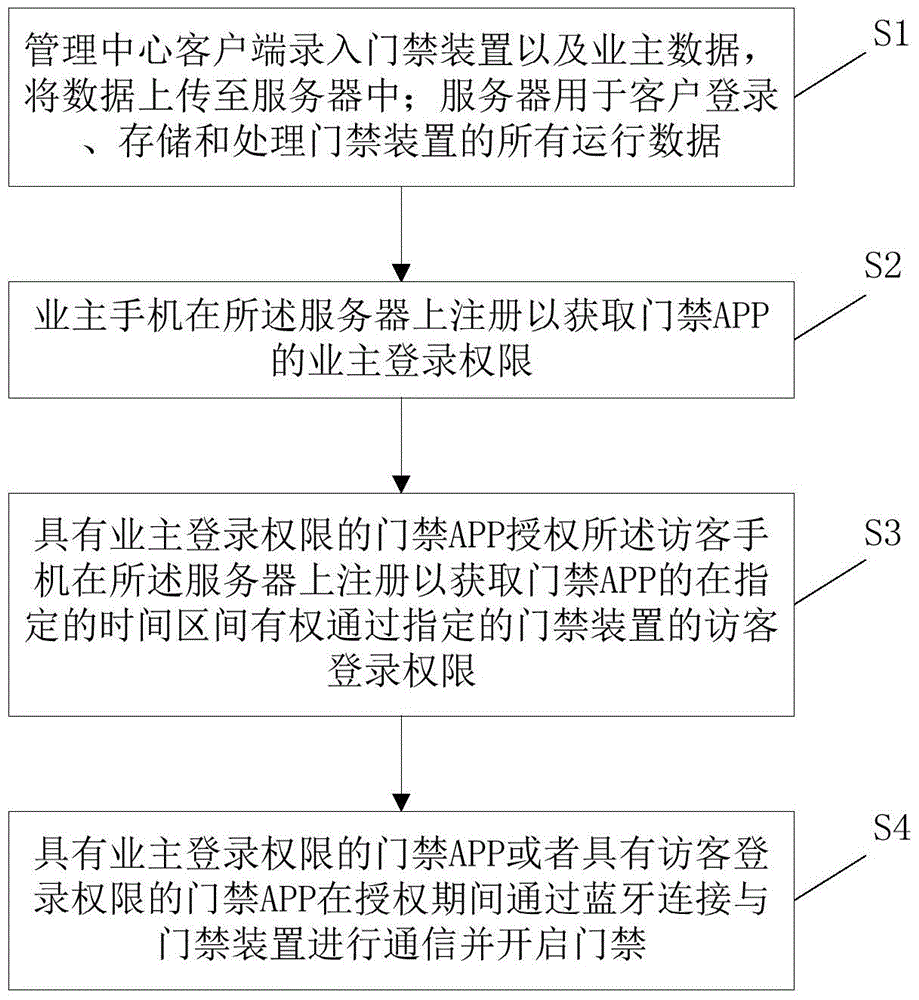
ActiveCN105719376AEasy to operateNo internet requiredIndividual entry/exit registersControl systemMedia access control
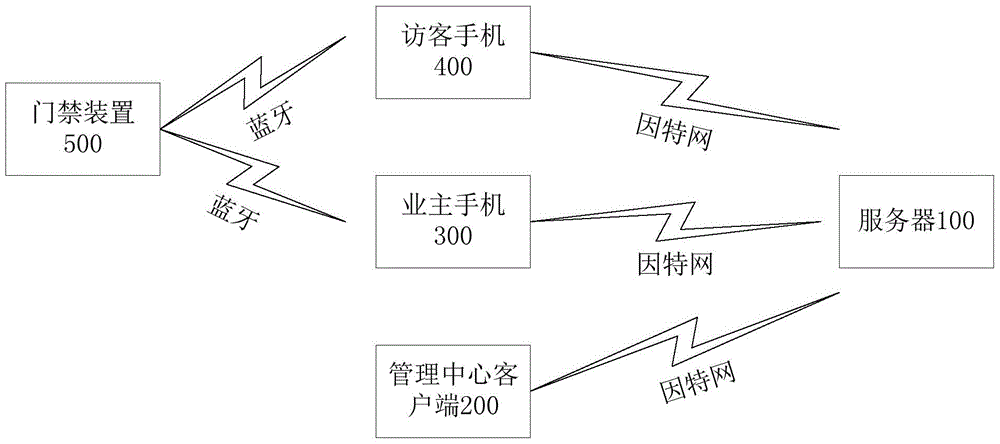
A door access control system and method is provided. The method comprises: a door access device; a server; and an owner's cellphone, a visitor's cellphone and a management center client that are in communication connection with the server; the management center client records door access device data and owner's data and uploads the data to the server; the server is used for managing a door access APP and storing and processing all running data of the door access device; the owner's cellphone registers on the server to acquire an owner login permission of the door access APP, the door access APP with the owner login permission authorizes the visitor's cellphone to register on the server to acquire a visitor login right of the door access APP to pass through a specified door access device within a specified time interval. An owner may authorize a visitor directly through the door access AP, operating is simple, temporary authorization from a management office or security staff is not required, and great convenience is brought to the owner and visitor; authentications of the owner and visitor are all controlled via the server, there is no need for pushing authorization information to a door access control for updating, and the door access control need not be networked.
Owner:深圳慧锐通智能技术股份有限公司
Computer security access control system and method
InactiveCN101986325AImplement secure storage protectionLow costDigital data authenticationOperational systemControl system
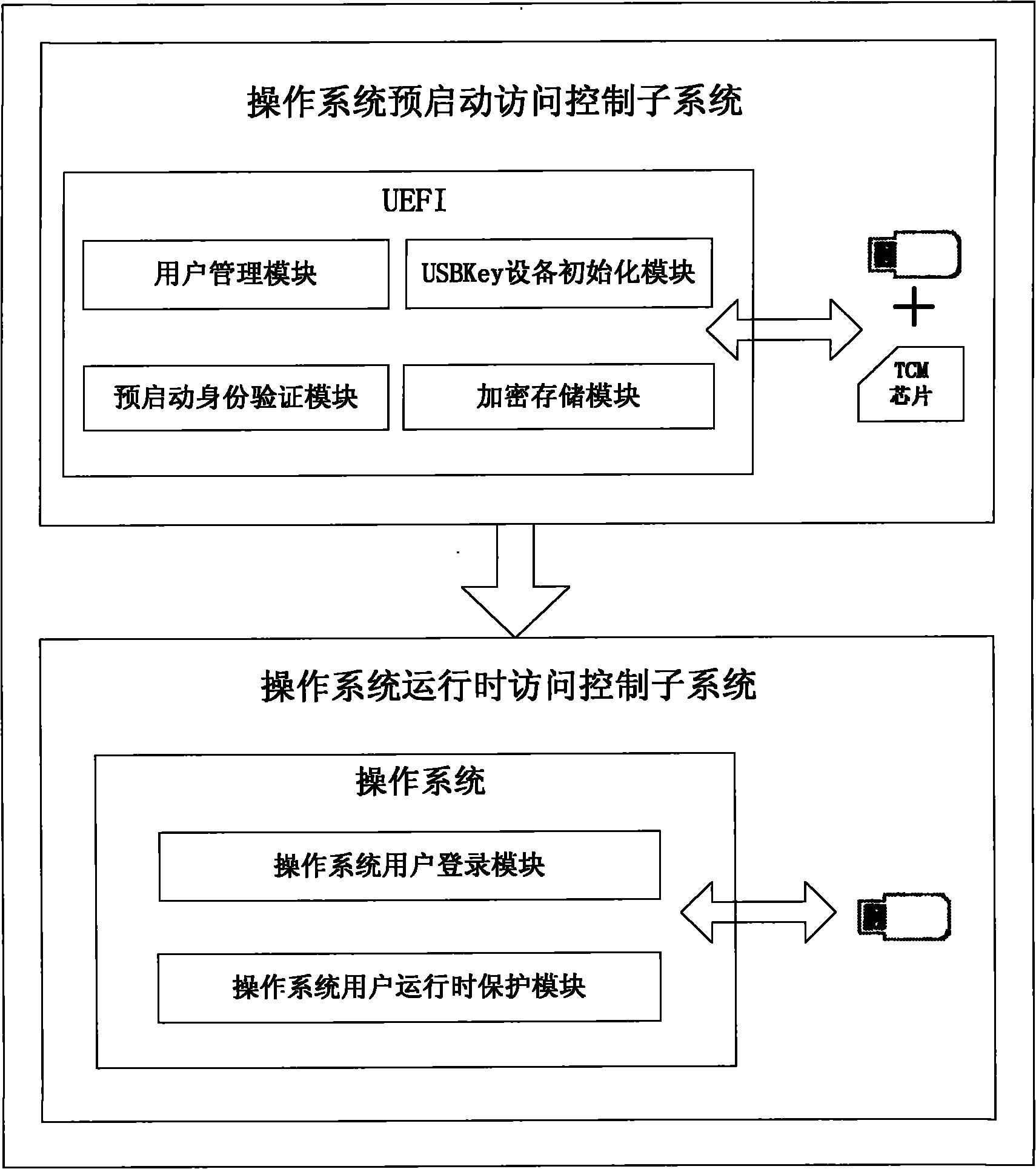
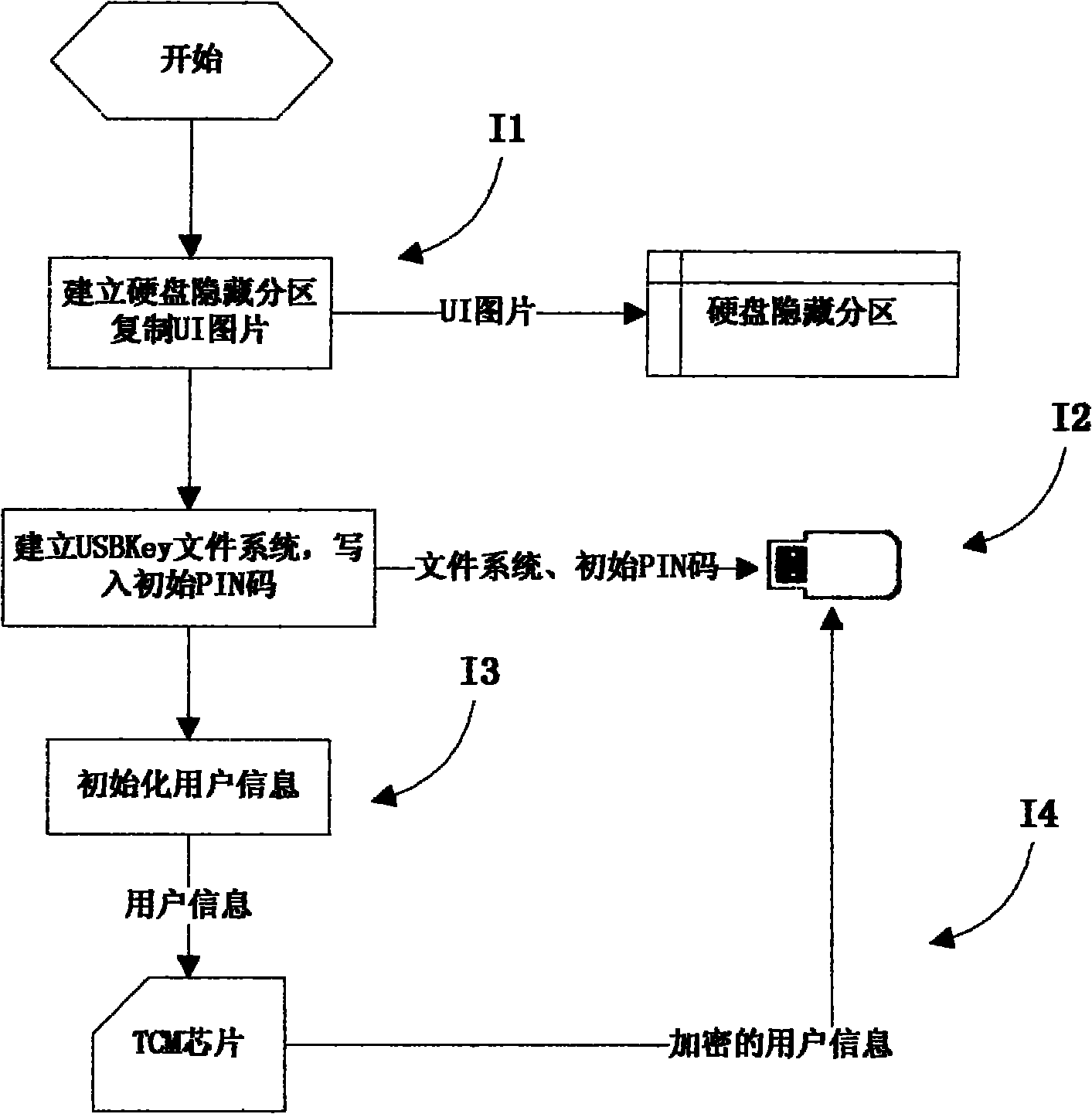
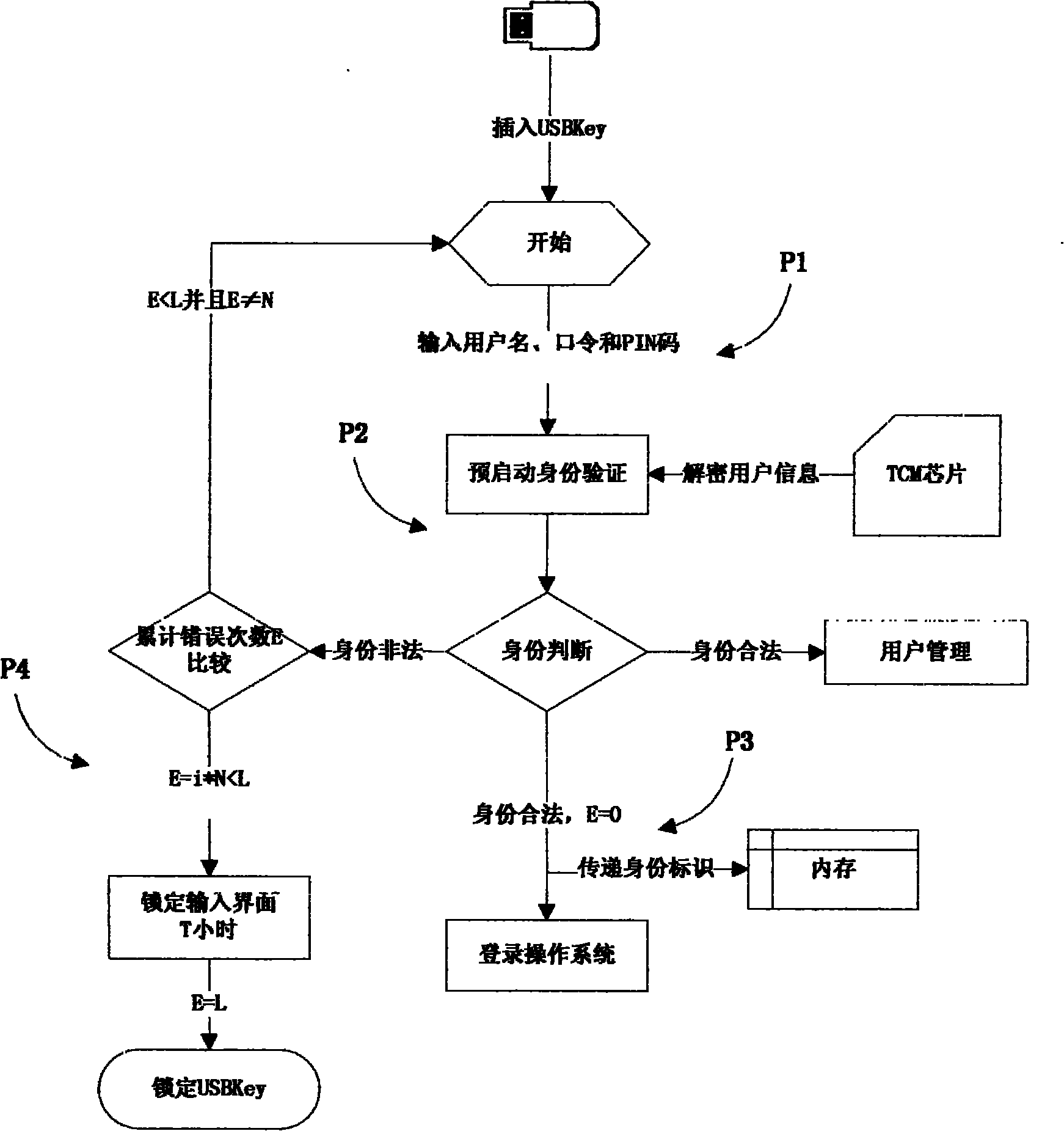
The invention discloses a computer security access control system and a computer security access control method, and belongs to the technical field of information security. A unified extensible firmware interface (UEFI) chip and a transmission control module (TCM) chip are included; a control system comprises an operating system pre-booting access control subsystem and an operating system running access control subsystem, wherein the operating system pre-booting access control subsystem comprises USBKey equipment, a USBkey equipment initialization module, a user management module, an operating system pre-booting identity authentication module and an encryption storage module; and the operating system running access control subsystem comprises USBKey equipment, an operating system user logon module, and an operating system user running protection module. The control method comprises an initialization method, an operating system pre-booting access control method and an operating system running access control method. The invention solves the problems that in the operating system, the reliability of access control is low, user identity information storage is insecure, and identity protection is insufficient in the running process after a user with legal identity logs on.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
A method and device for secure access control based on user
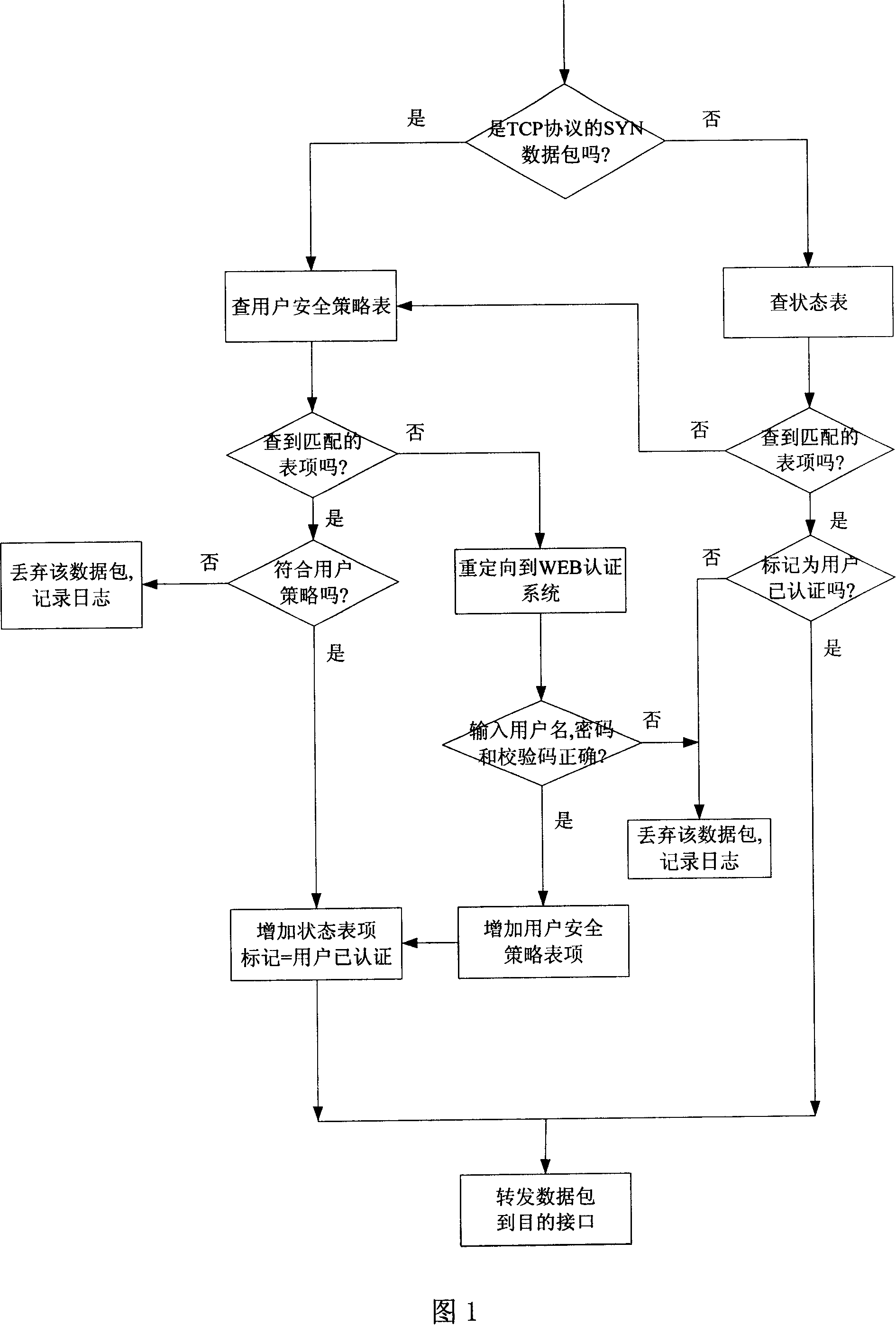
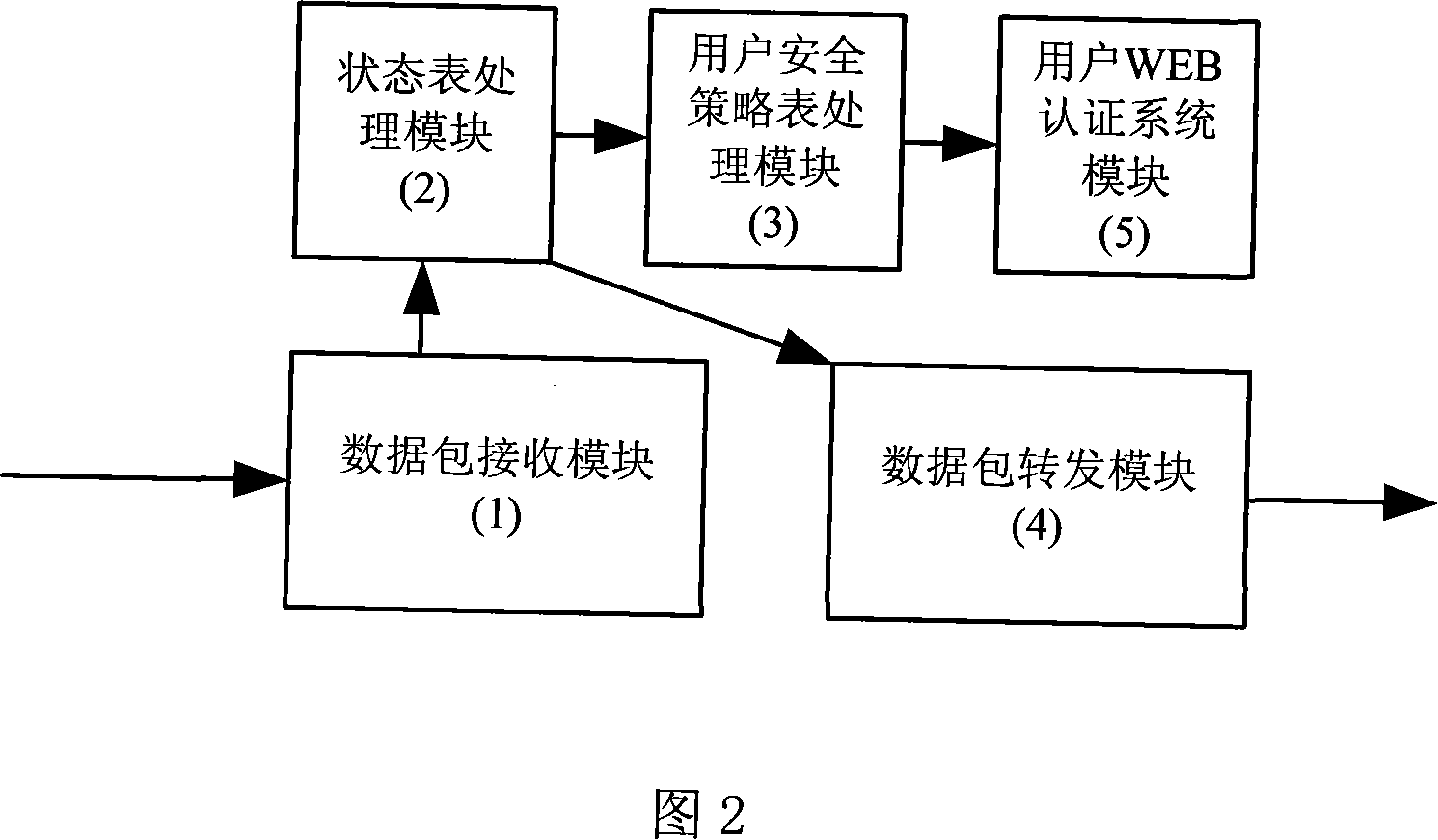
ActiveCN101087187AImprove usabilityImprove securityNetworks interconnectionSecuring communicationRelevant informationIp address
The invention discloses a method and device for safe access control based on user, and it extends the state list of firewall, adds the list option of user strategy in the firewall system, and the list of user strategy records the information of user. After the firewall receives the data packet, it adds the list of user security strategy according to original IP address, and then auto correlation process is done according to searching result to realize safe access control. The invention solves the problems of auto correlation without mounting the client software on terminal computer, and adds the user name and cipher based on WEB for user accessing external network, improves the easiness, security and convenience, and reaches the aims that the firewall system can manage the authority of fine grain and trace the secure event.
Owner:奇安信网神信息技术(北京)股份有限公司
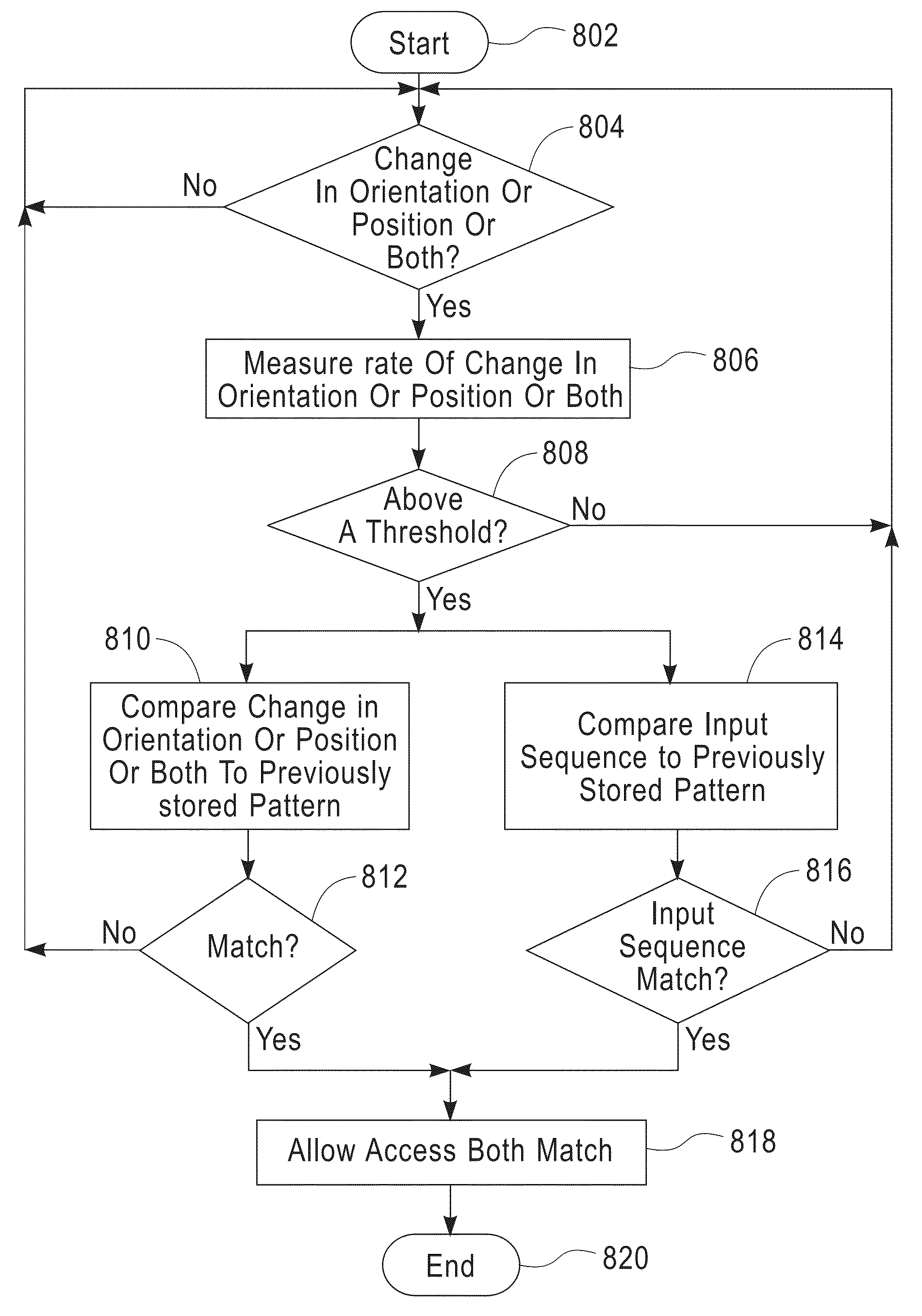
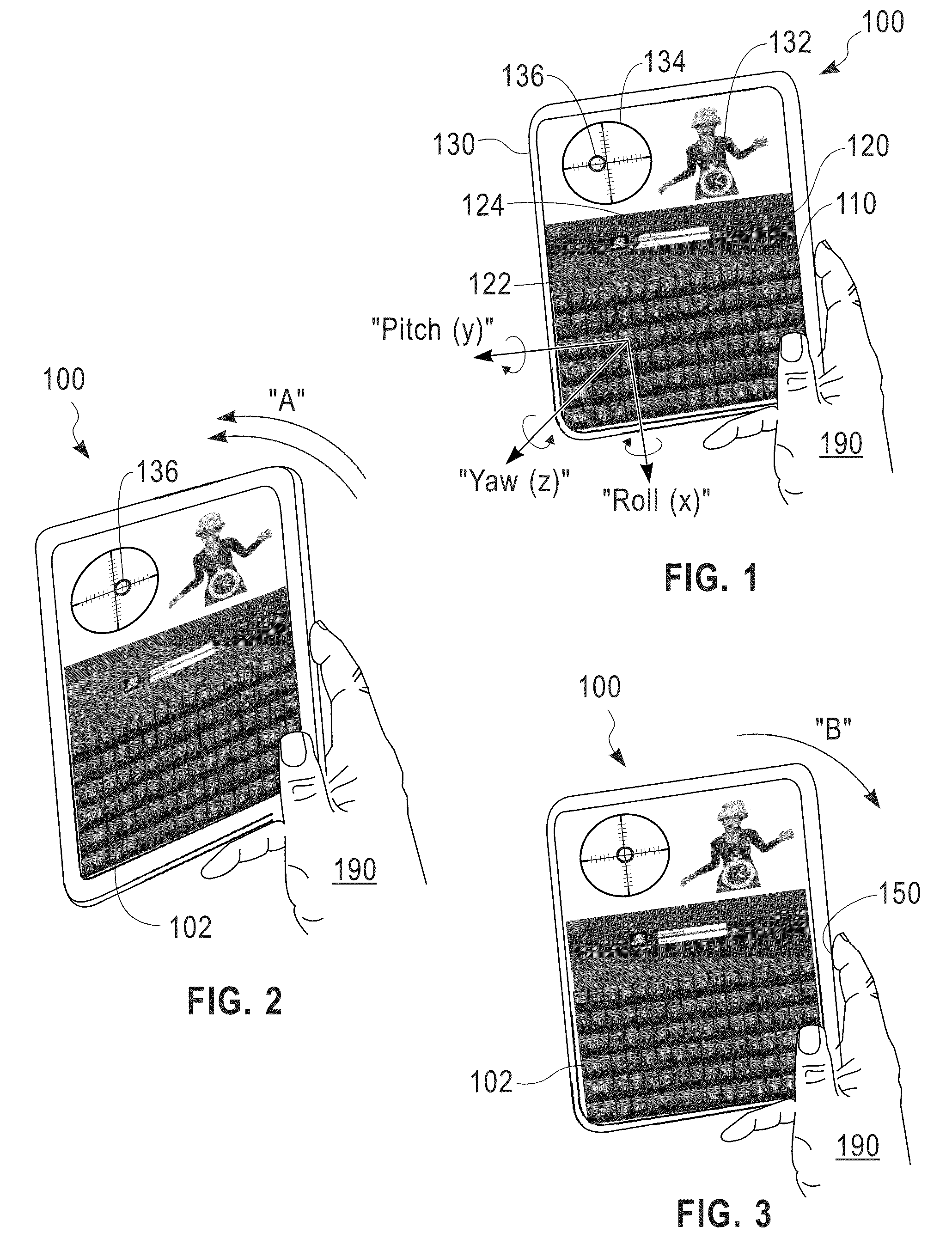
User access control based on handheld device orientation
ActiveUS8832823B2Digital data processing detailsUnauthorized memory use protectionUser inputPassword
Owner:AIRBNB
Central access control system
ActiveUS7042333B2Electric signal transmission systemsMultiple keys/algorithms usageControl systemDisplay device
An access control system for work vehicles has a display, an operator input device and a computer configured to program individual vehicles keys to operate individual vehicles or groups of vehicles.
Owner:BLUE LEAF I P INC +1
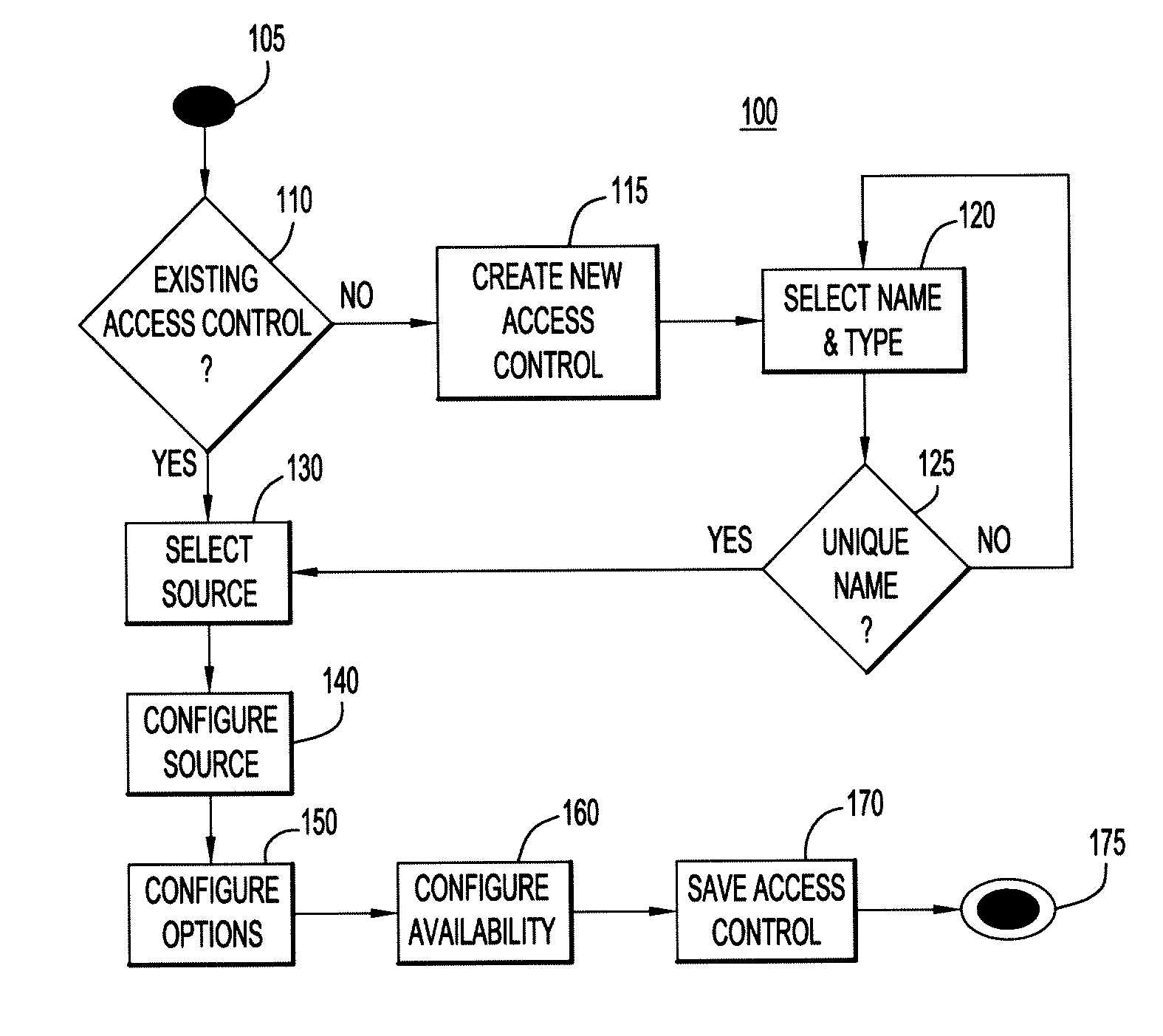
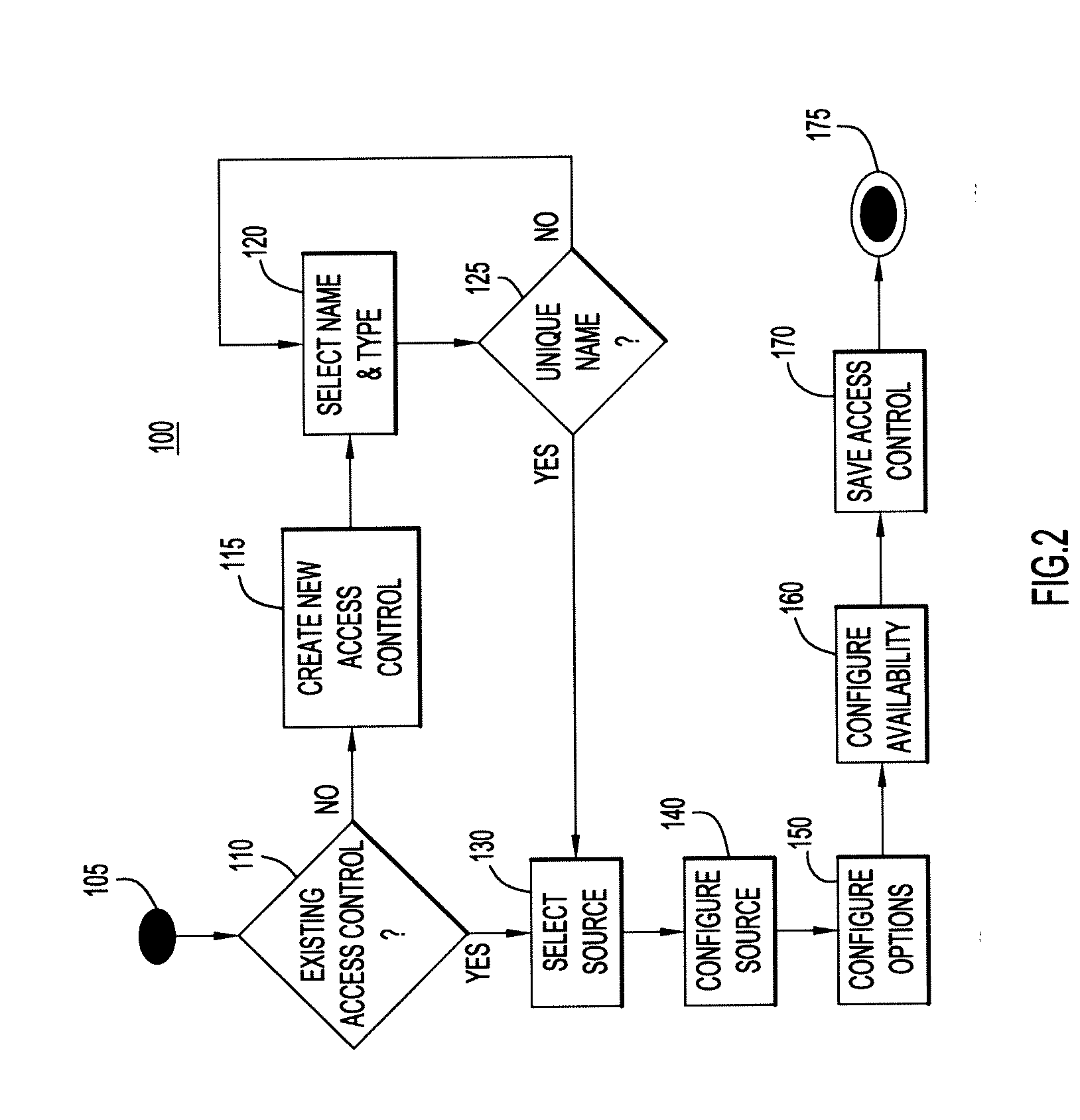
Policy Creation Using Dynamic Access Controls
InactiveUS20110321117A1Digital data processing detailsUnauthorized memory use protectionWeb serviceLinked data
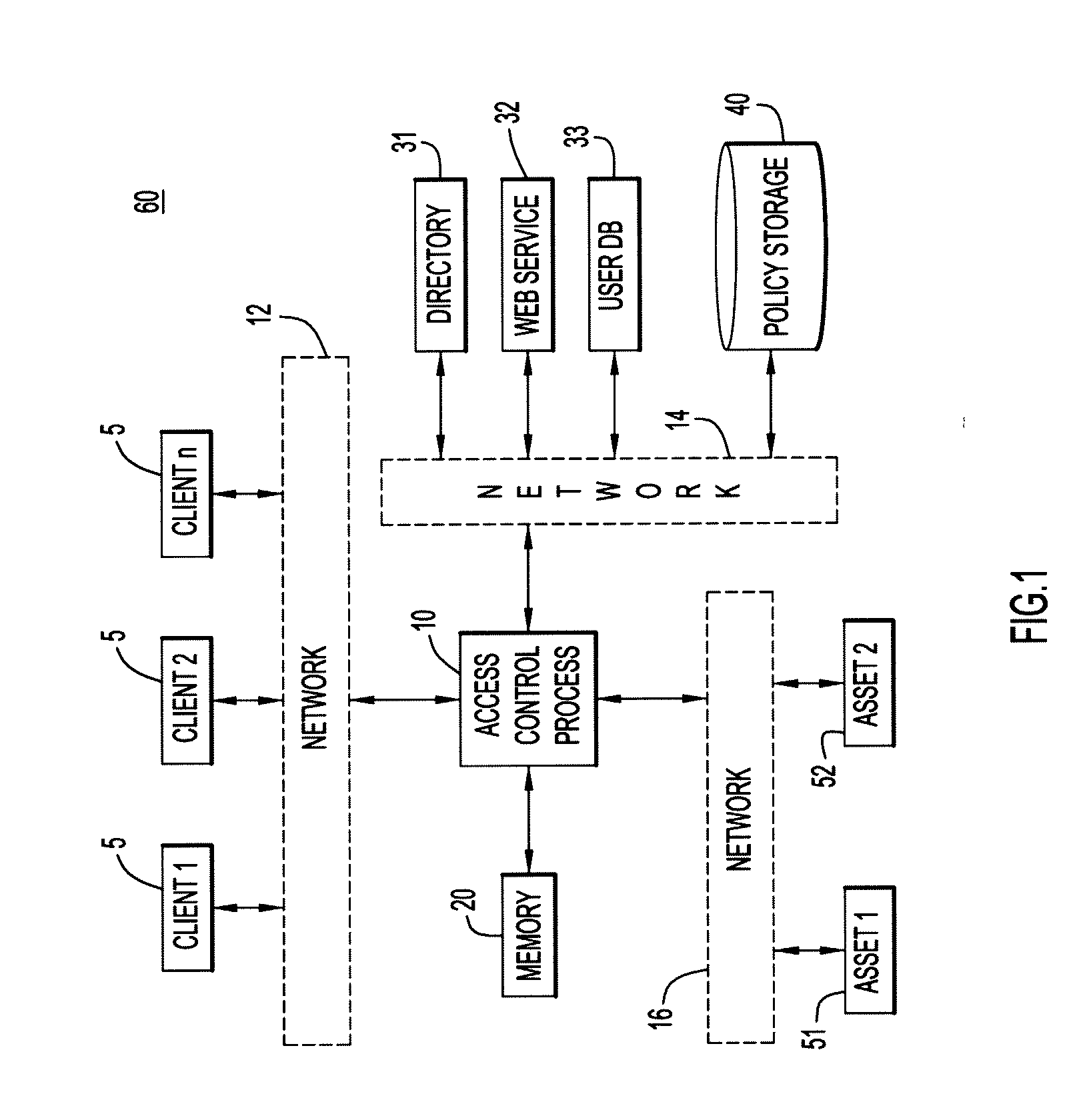
A method and system for dynamically managing access to assets such as an electronic document or a hardware component, using policies that comprise one or more dynamic access controls, which are linked to data sources such as databases or web services. The access controls are dynamic because, each time the policy is invoked, the policy and its component access controls must be evaluated with respect to the current information in the linked data sources.
Owner:EXCELIS INC
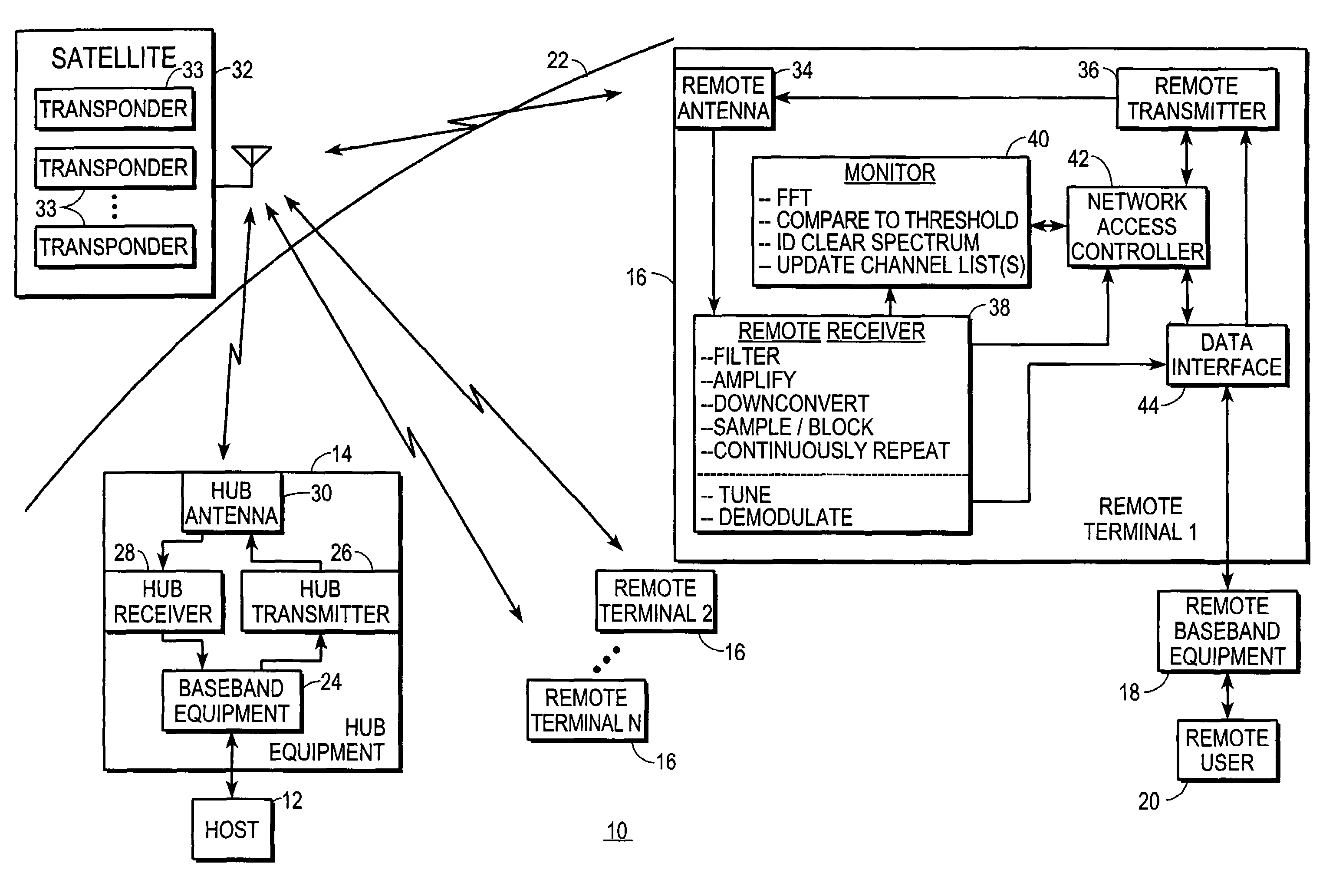
System and method for multiple access control in satellite communications system
ActiveUS7376418B2Guaranteed cost-effective operationEffective bandwidthRadio/inductive link selection arrangementsRadio transmissionCommunications systemFrequency spectrum
Owner:NENABER TERRY +1
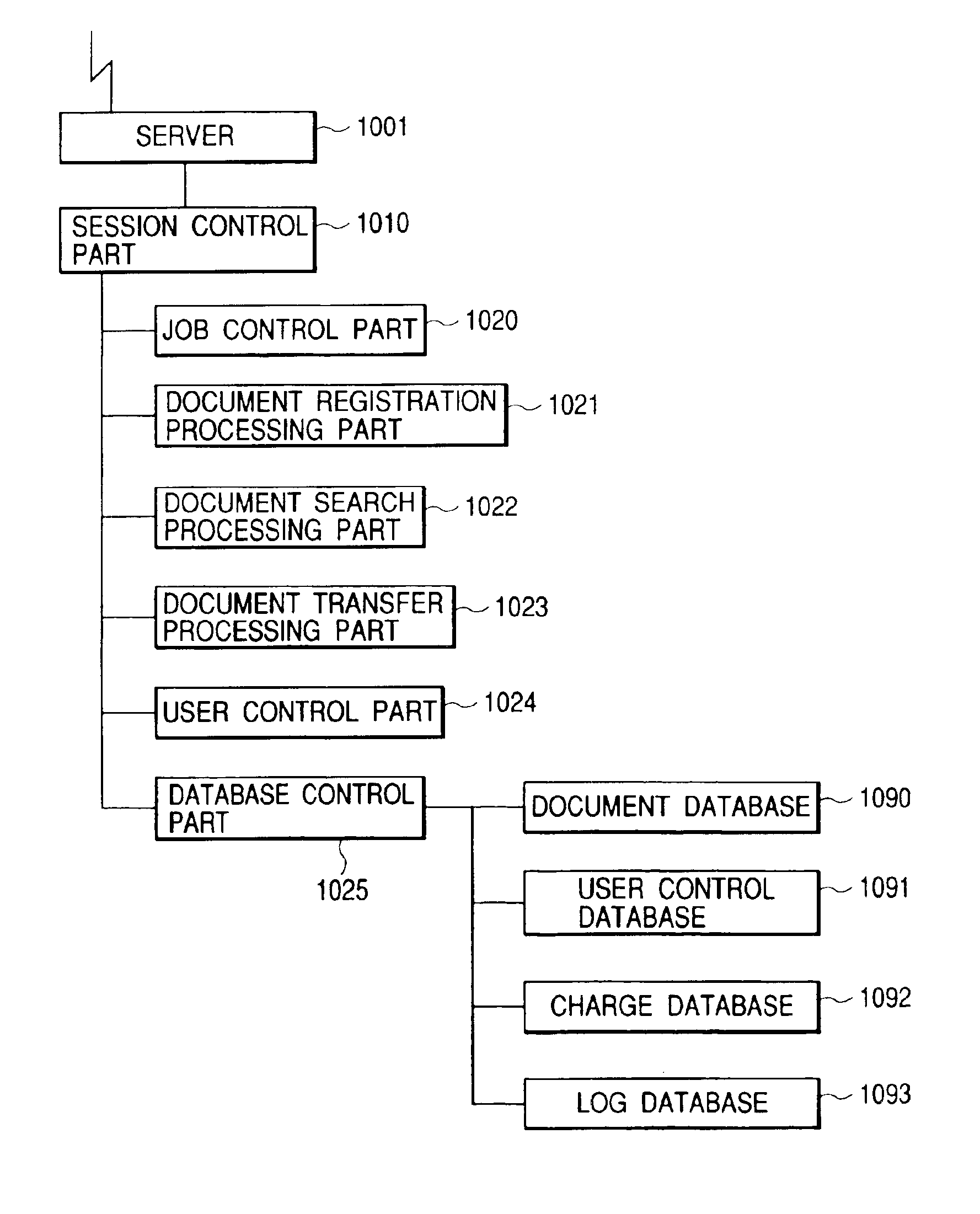
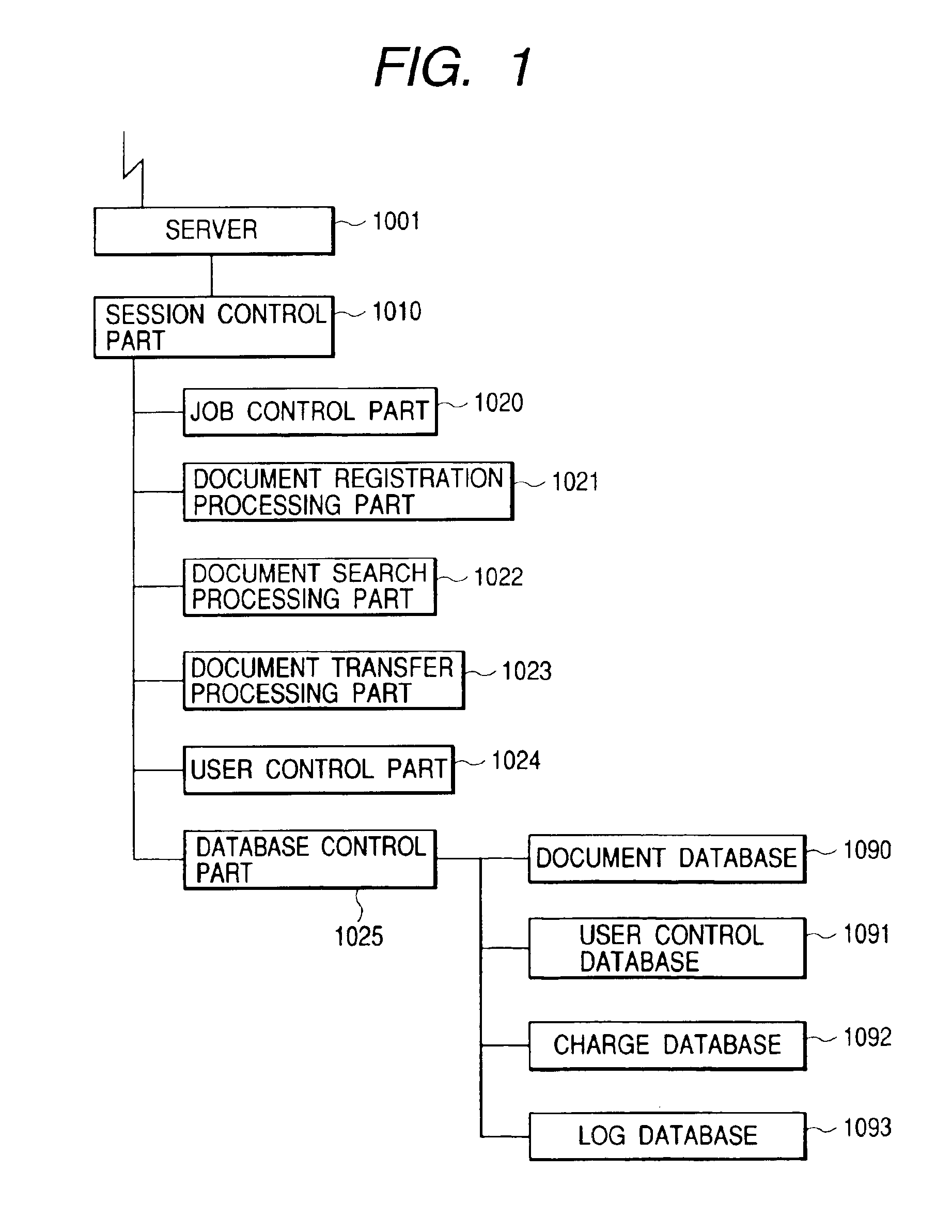
Document control apparatus, document control system, document control method and storage medium
To provide a document control apparatus, a document control system, a document control method and a storage medium that are capable of providing more certain access control by the unit of document and a system (service) for allowing access in the form of charging additional charge with a fixed grace period, and are capable of supporting more flexible and certain storing service. The document control system includes a Web server, a session control part for controlling access, a job control part for controlling job execution, a document registration processing part for registering, updating and deleting a document, a document search processing part for searching an accumulated and controlled document, a document transfer processing part for transmitting and receiving document data, a user control part for controlling user information, a database control part for controlling document data, registration user, charge information and document access histories, and databases.
Owner:CANON KK
Method and apparatus implementing remote access control based on portable memory apparatus
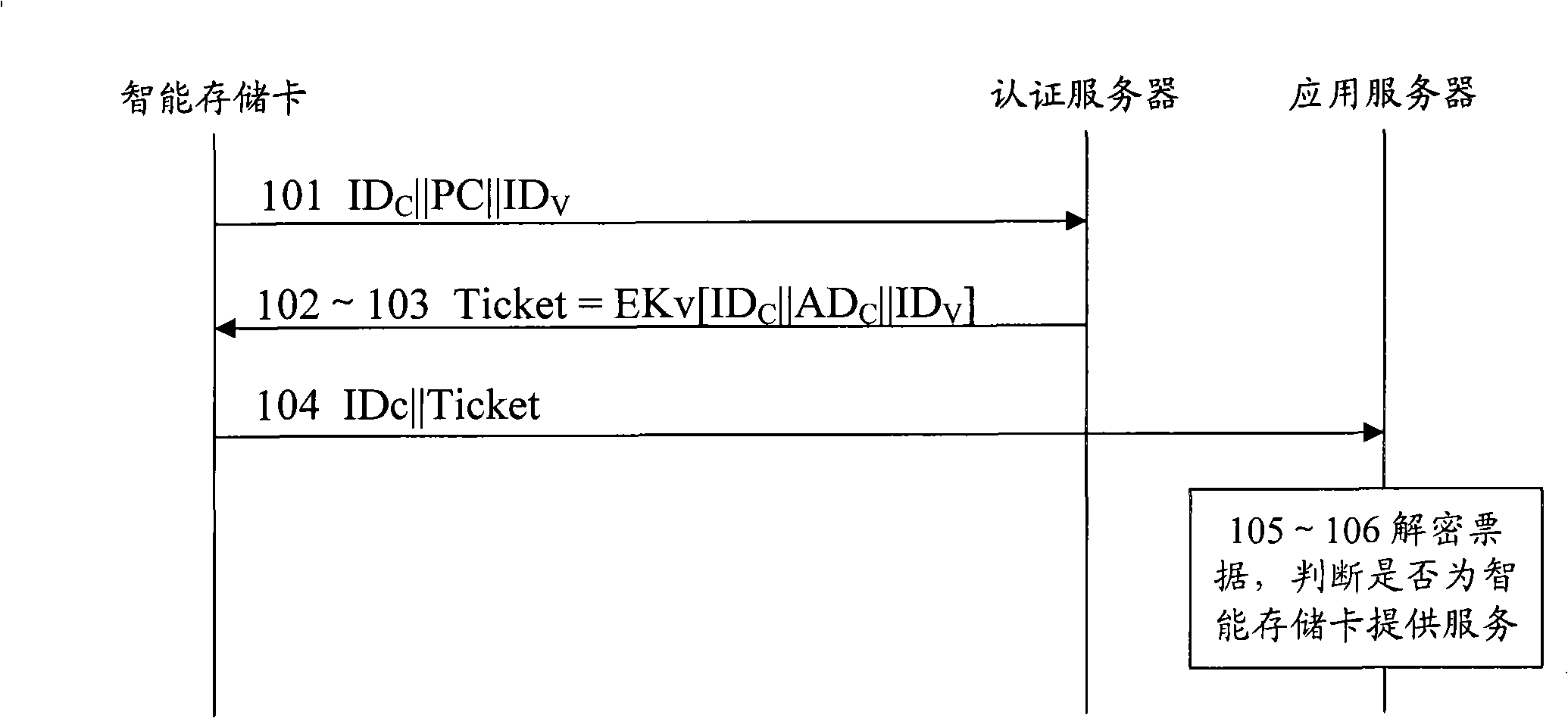
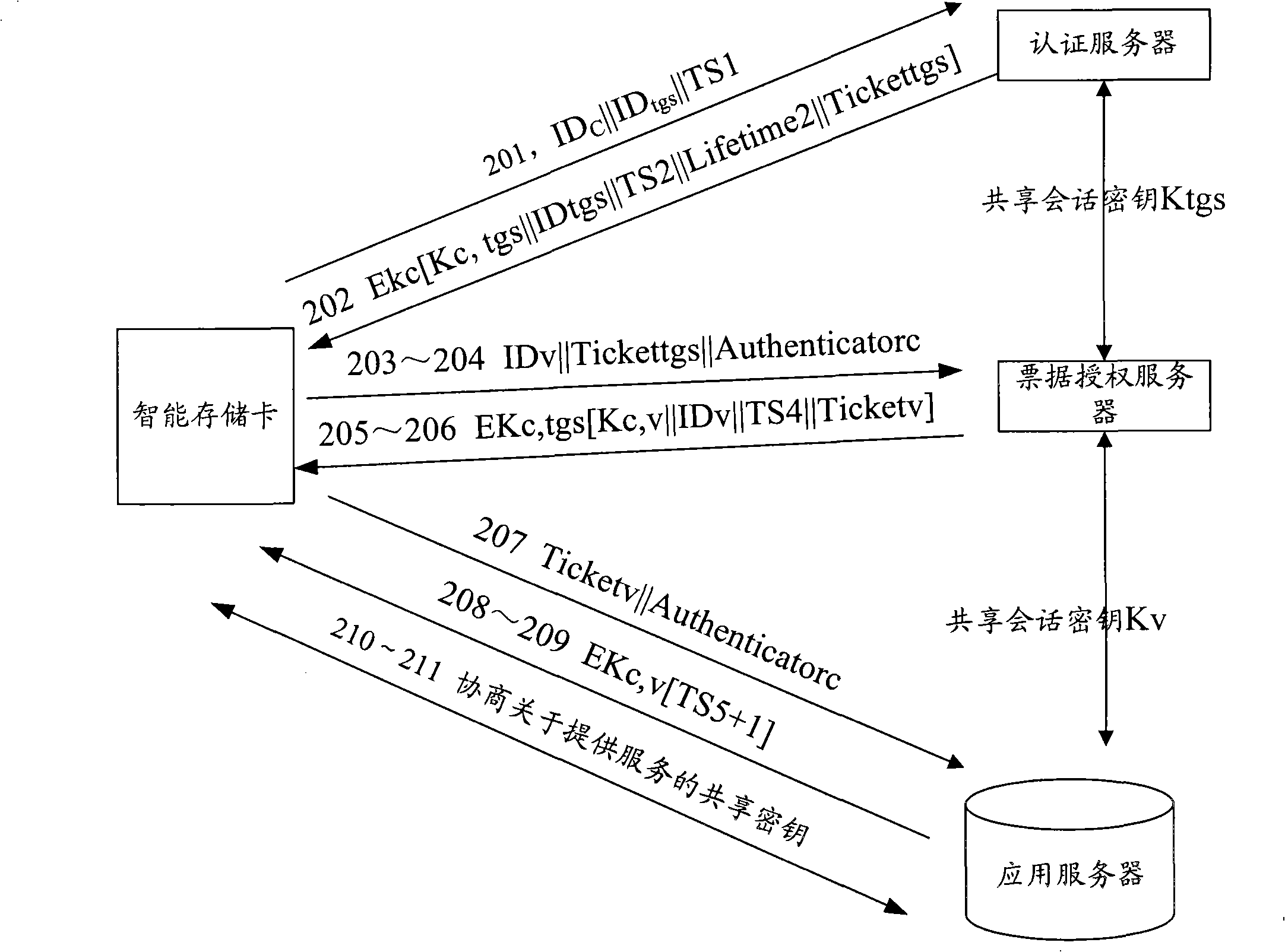
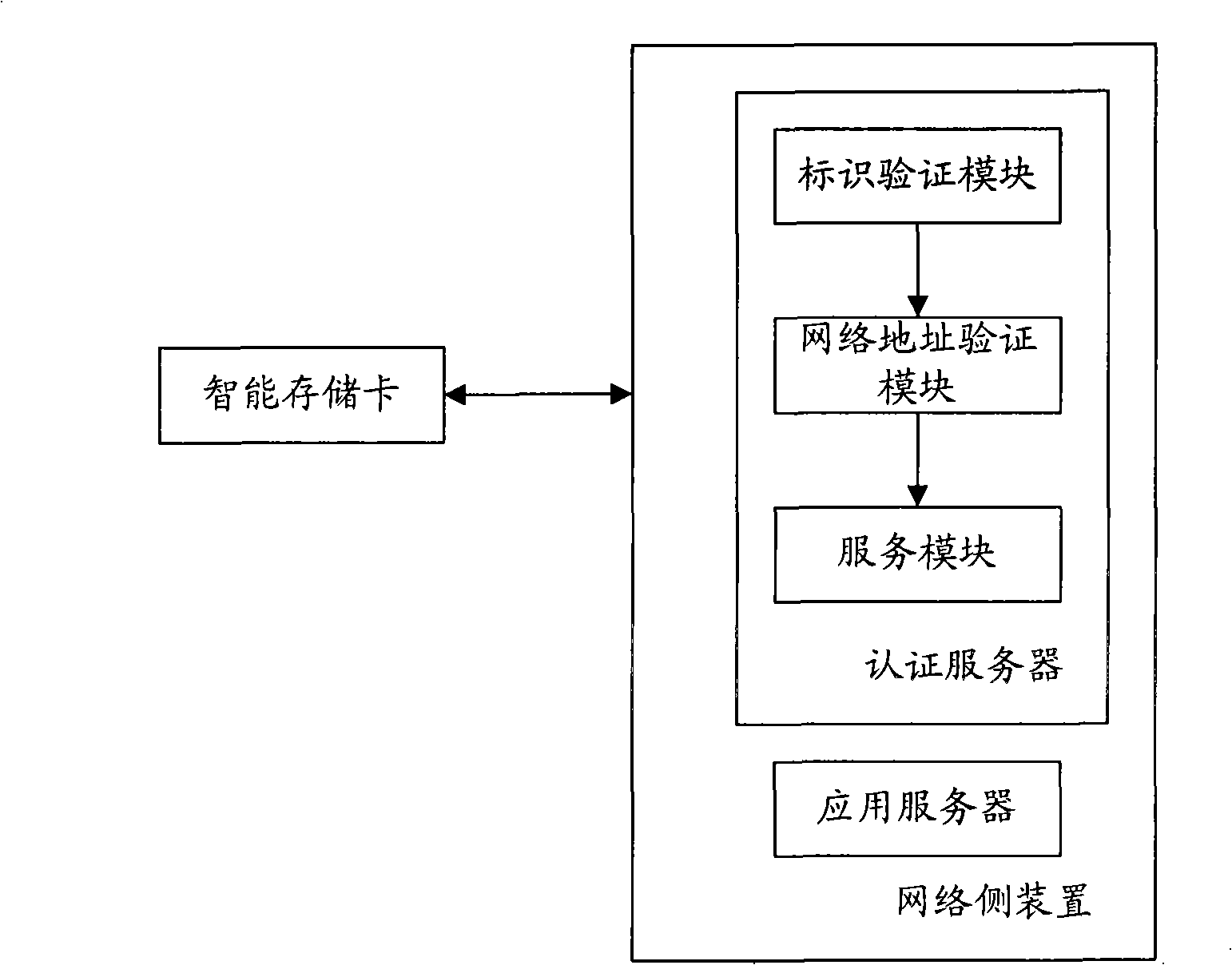
InactiveCN101340436AReduce the certification burdenPrevent Authentication BlockingUser identity/authority verificationComputer hardwareApplication server
The invention discloses a method and a device for realizing remote access control based on a portable storage device, the method comprises that: an authentication server receives a request access message which is sent by an intelligent storage card, and the request access message comprises an identifier of the intelligent storage card, the identifier of an application server and an identifier related key; the authentication server obtains the stored identifier related key which is corresponding to the identifier of the intelligent storage card and compares with the identifier related key in the request access message, if the two are consistent, a request access response message is returned to the intelligent storage card; the application server receives a service request message which contains the identifier of the intelligent storage card and a note and is sent by the intelligent storage card, a key decryption note which is shared with the authentication server is adopted for verifying the consistency of the identifier of the intelligent storage card which is contained in the note and the identifier of he intelligent storage card which is not encrypted in the service request message, thereby providing the service for the intelligent storage card. The proposal of the invention can realize the separation of the authentication and the application, thereby alleviating the burden on the application server for carrying out the authentication of the intelligent storage card.
Owner:POTEVIO INFORMATION TECH
Secure access control system and method for network terminal nodes
InactiveCN104796261AReal-time monitoring of identity informationReal-time monitoring of the access verification processUser identity/authority verificationNetwork terminationPrivate network
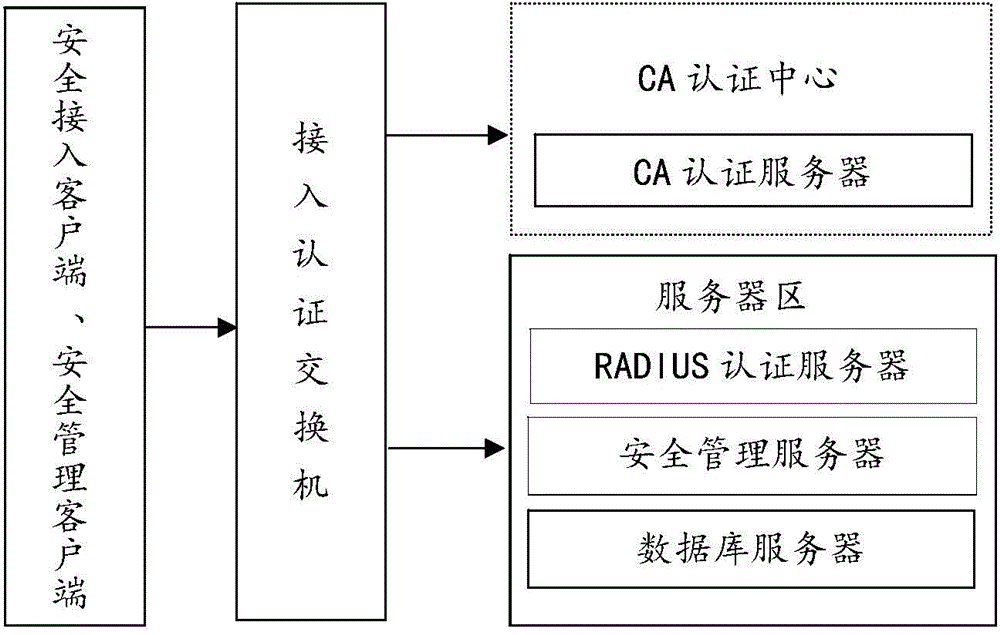
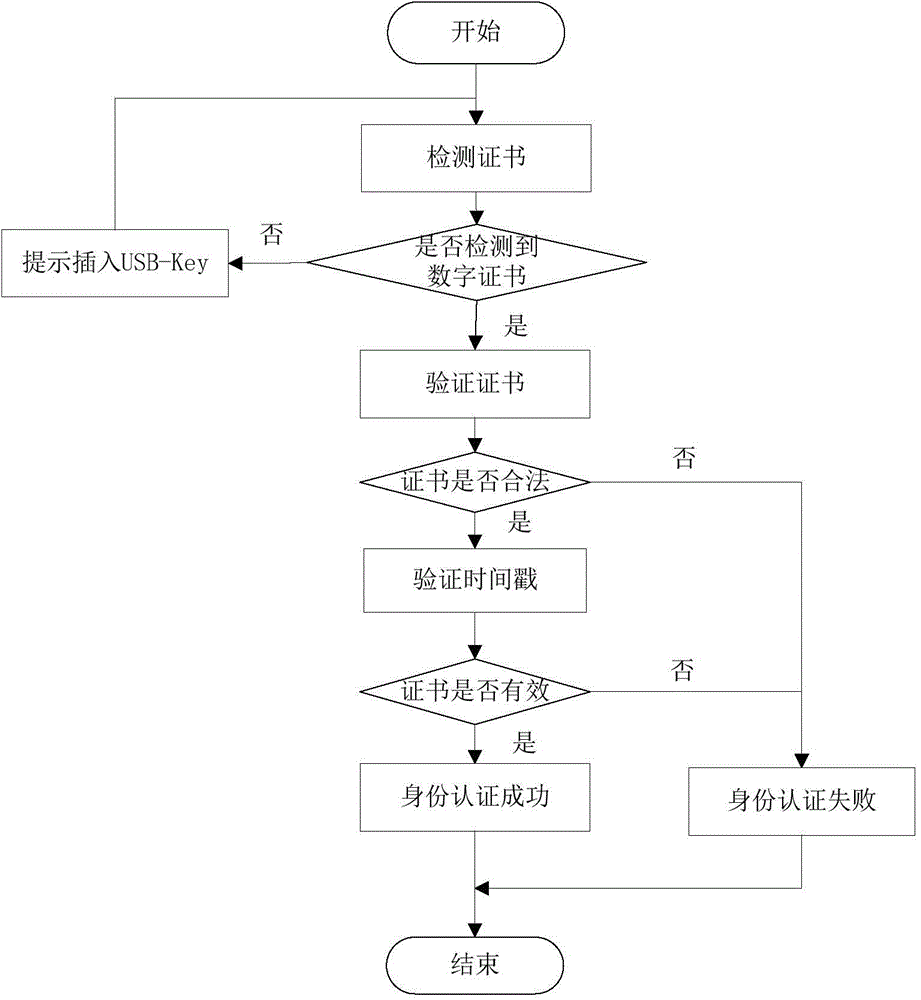
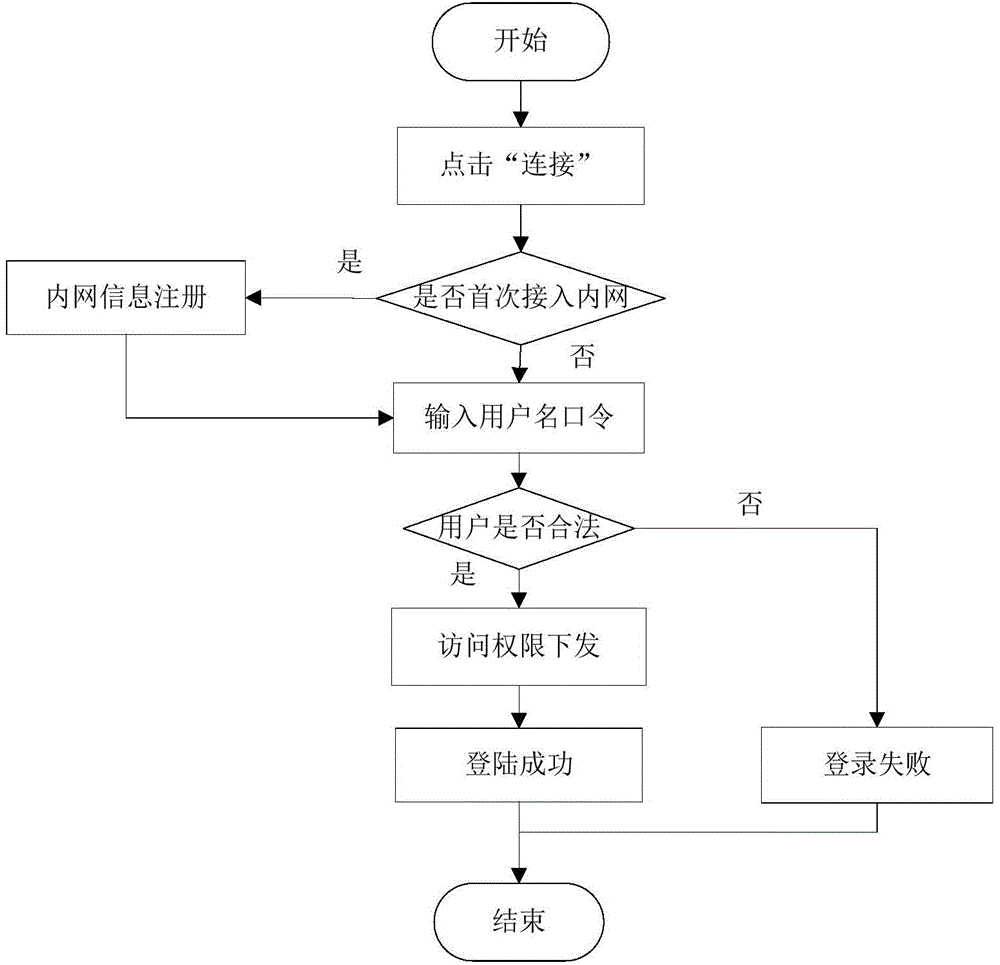
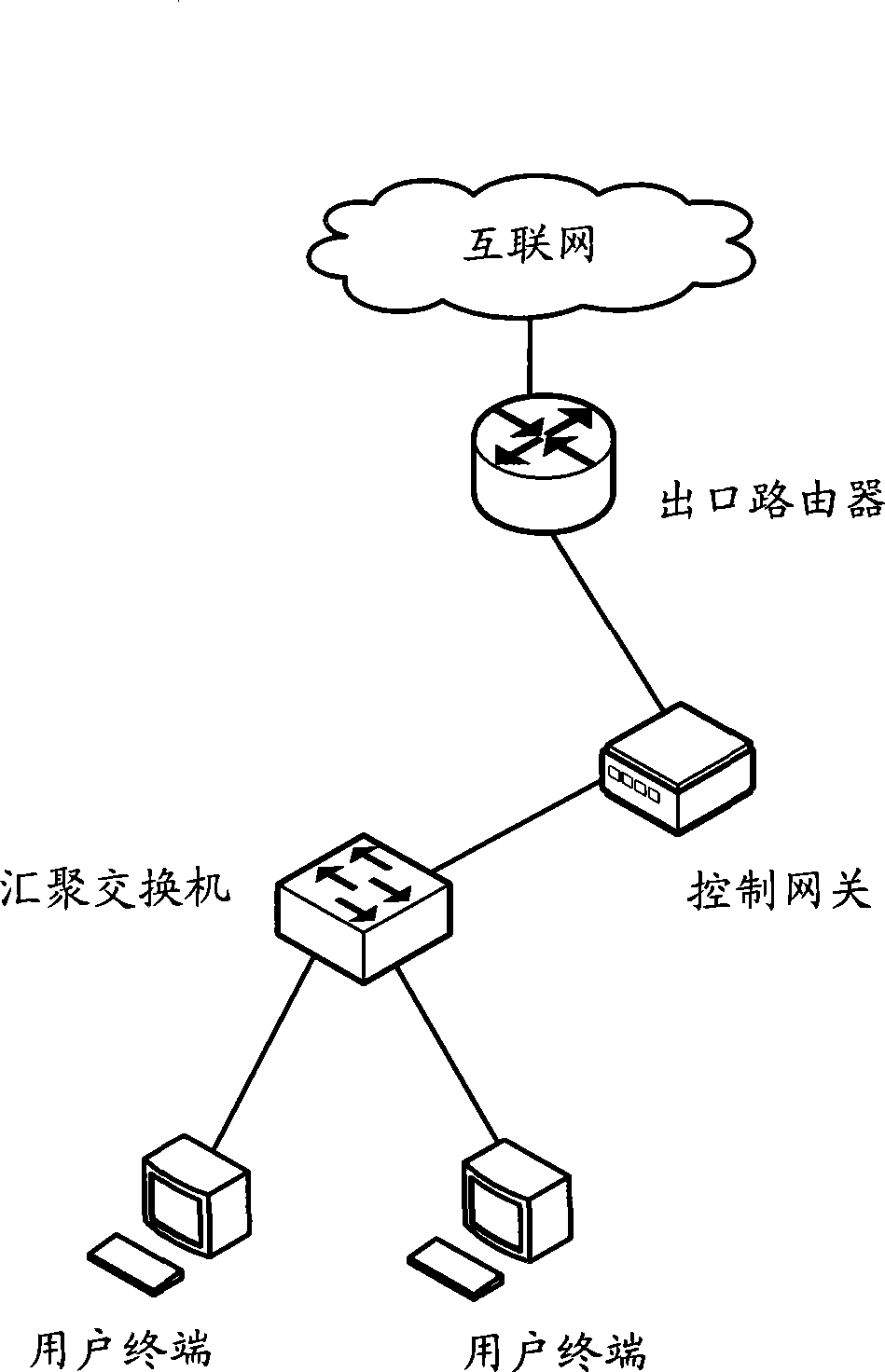
The invention discloses a secure access control system and method for network terminal nodes. A C / S (client / server) architecture is provided between a secure access client and a CA (certificate authority) authentication server, and another C / S architecture is provided between the secure access client and an RADIUS (remote authentication dial-in user service) authentication server; the two C / S architectures are used for user identity authentication and terminal access authentication, respectively. A B / S (browser / server) architecture is provided between a security management client and a security management server and is used mainly for registering and checking user information, setting network access group permissions and controlling and monitoring secure access in real time. The secure access control system and method has the advantages that the access terminals can be subjected to trusted identity authentication, trusted access authentication, terminal proxy authentication, network access permission control and network access state real-time monitoring; a trusted terminal access control system based on identity authentication is achieved and is stable and reliable and is high in authentication efficiency, violations such as NAT (network address translation) and proxy services can be detected and warned accurately, network states of terminal users are monitored and controlled through a web management interface, and the needs of private networks for safety management can be fully met.
Owner:CHANGAN UNIV
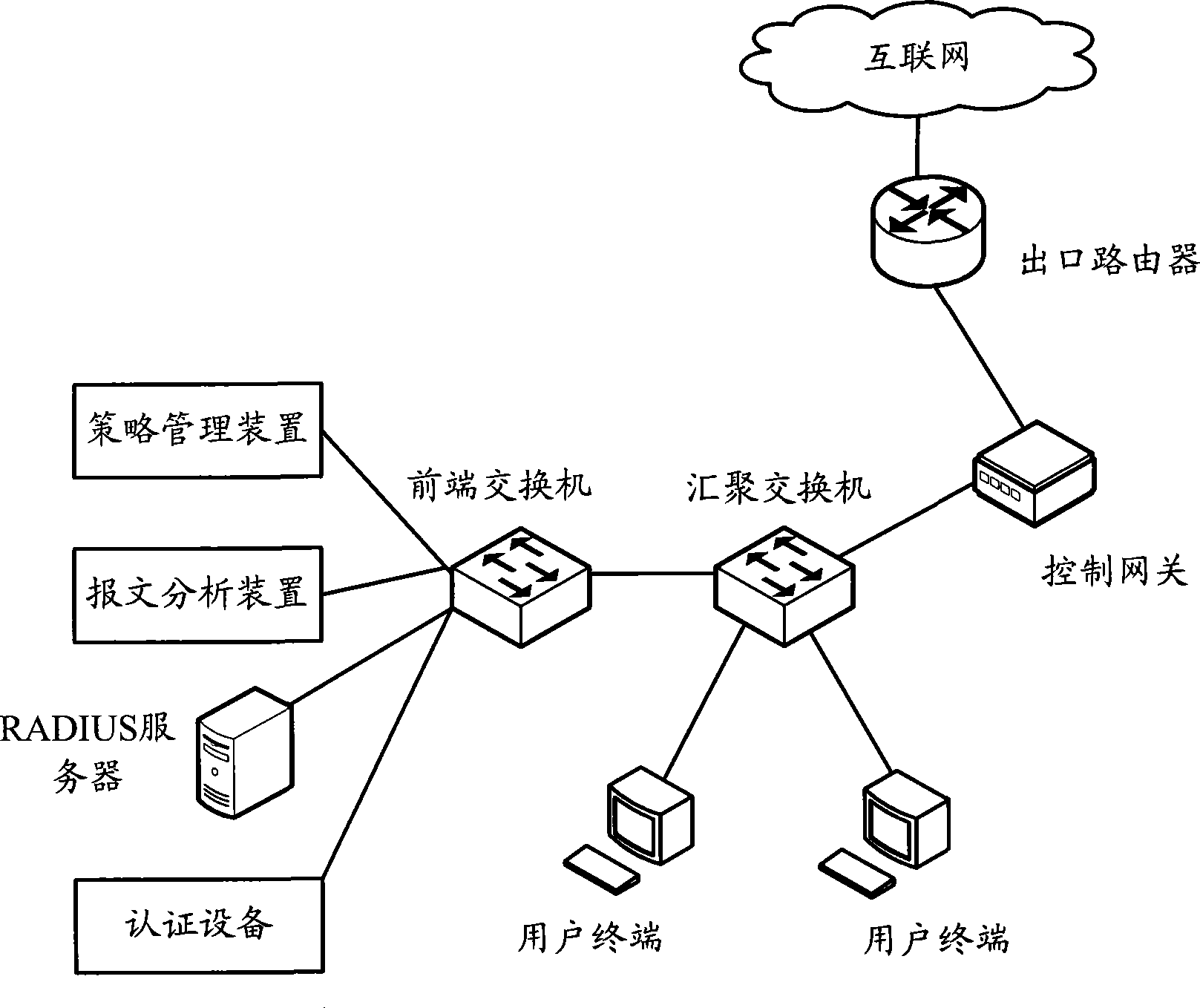
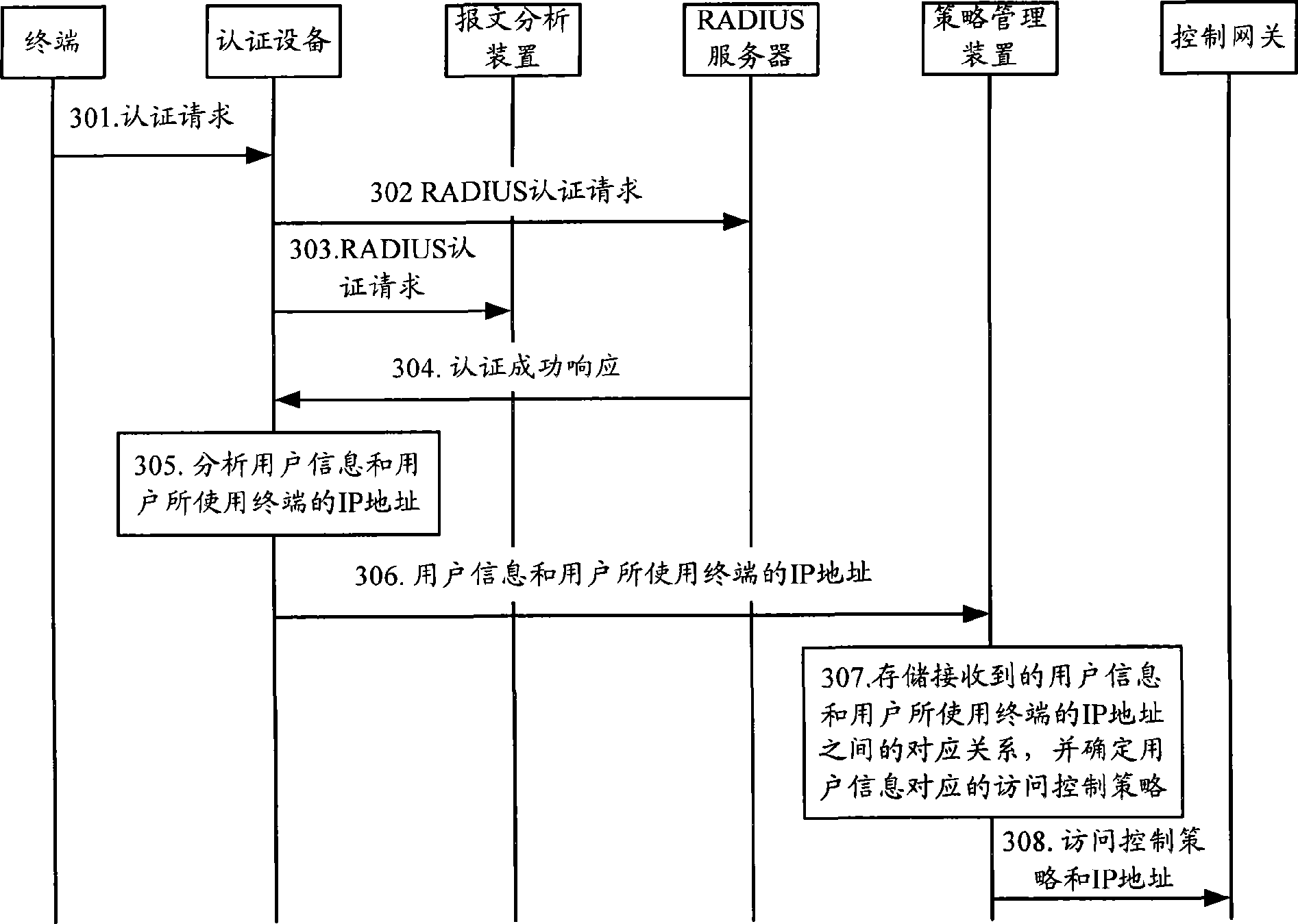
Method and system for controlling user access
The invention provides a user access control method and a system thereof. A message analyzing device and a strategy management device are accessed in the network in advance, and the corresponding relation of user information and access control strategy is deployed in the strategy management device; the message analyzing device acquires the user information and the IP address information of the terminal used by the user when the user logs on, and sends the user information and the IP address information of the terminal used by the user to the strategy management device; the strategy management device confirms the access control strategy information corresponding to the received user information according to the deployed corresponding relation, and sends the confirmed access control strategy information and the IP address information of the terminal used by the user to a control gateway, so that the control gateway can make use of the access control strategy information to perform access control to the terminal used by the user. The user access control method and the system thereof can realize user access control more easily and exert no pressure to the control gateway.
Owner:NEW H3C TECH CO LTD
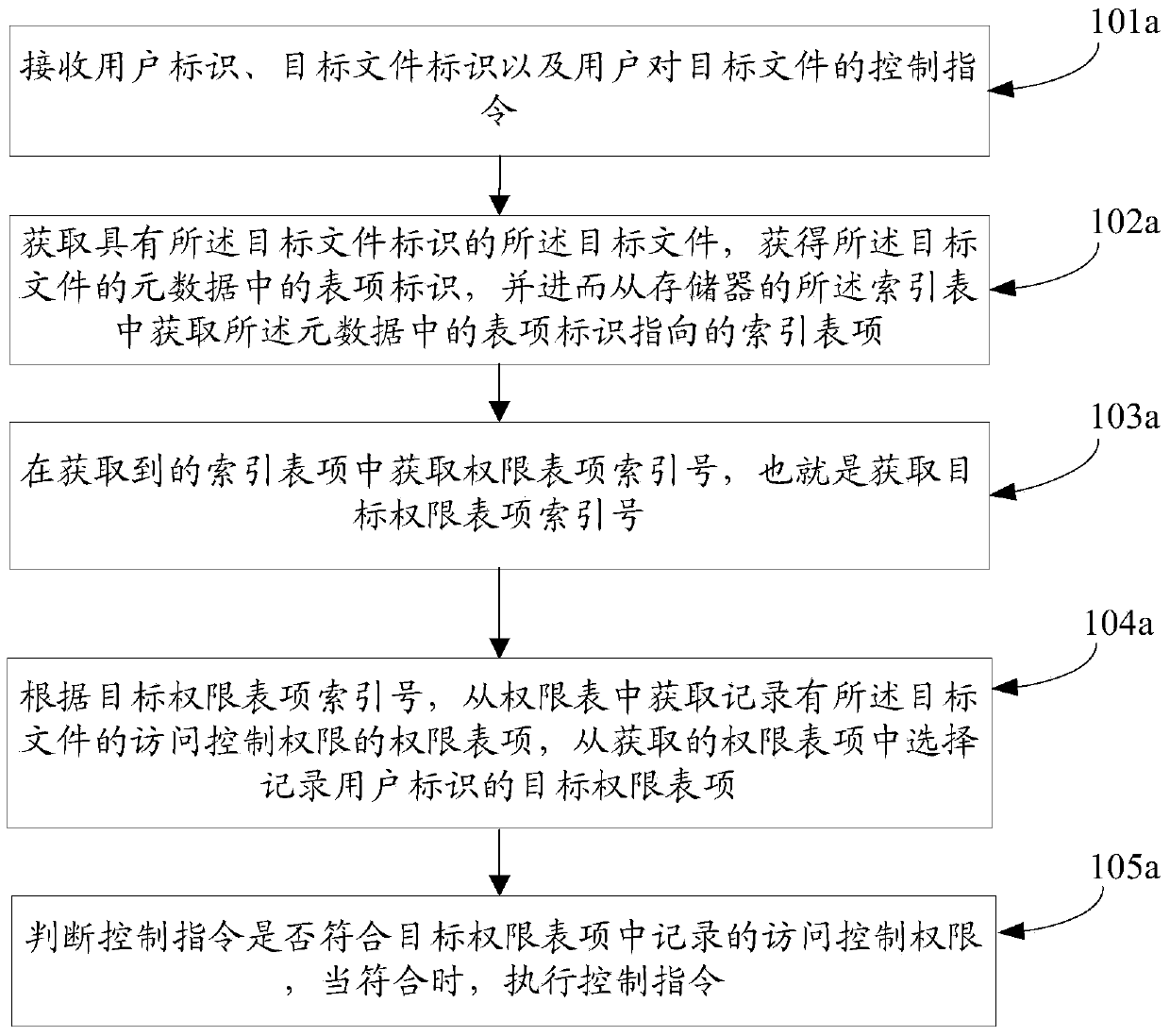
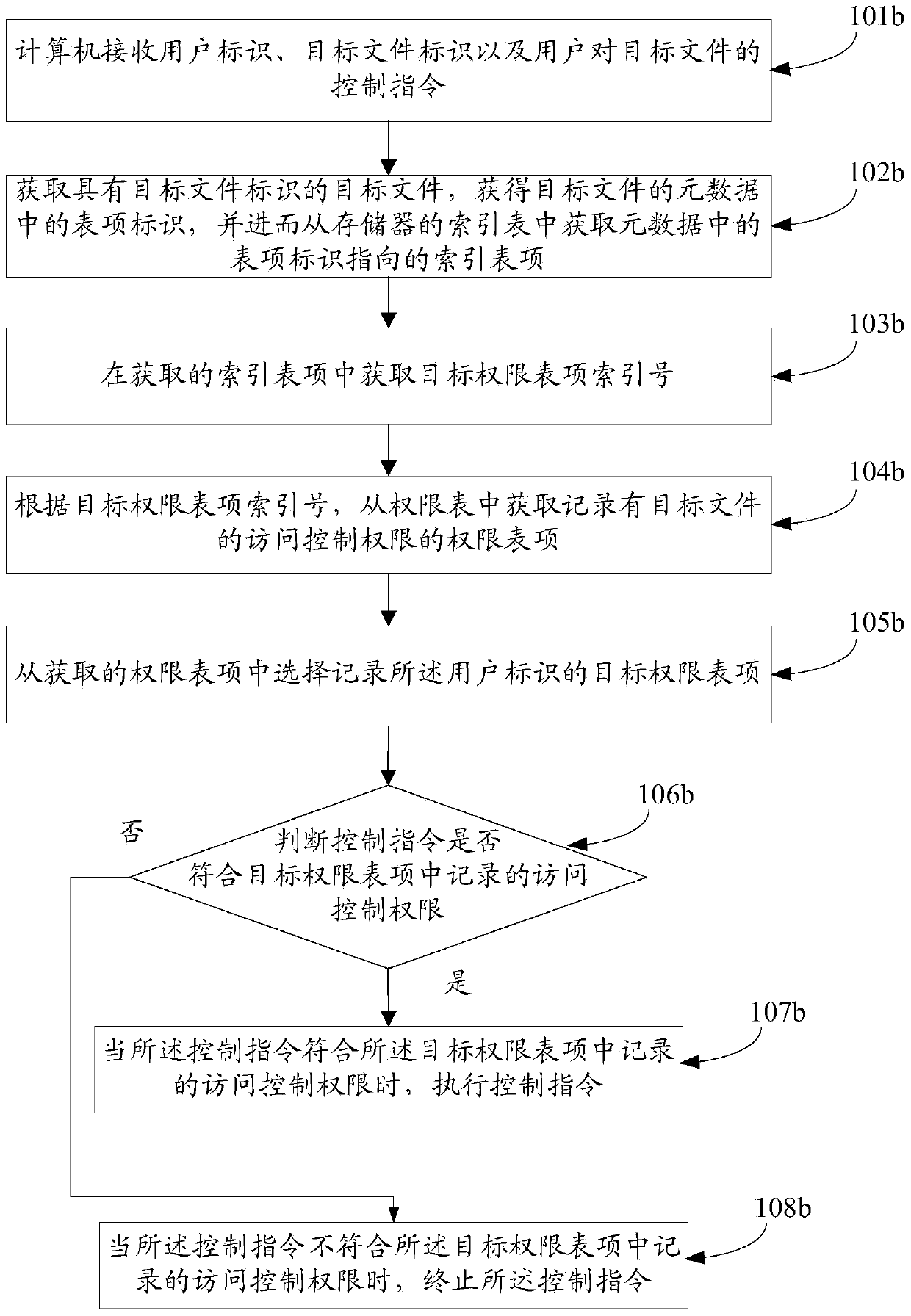
Access control right management method and device
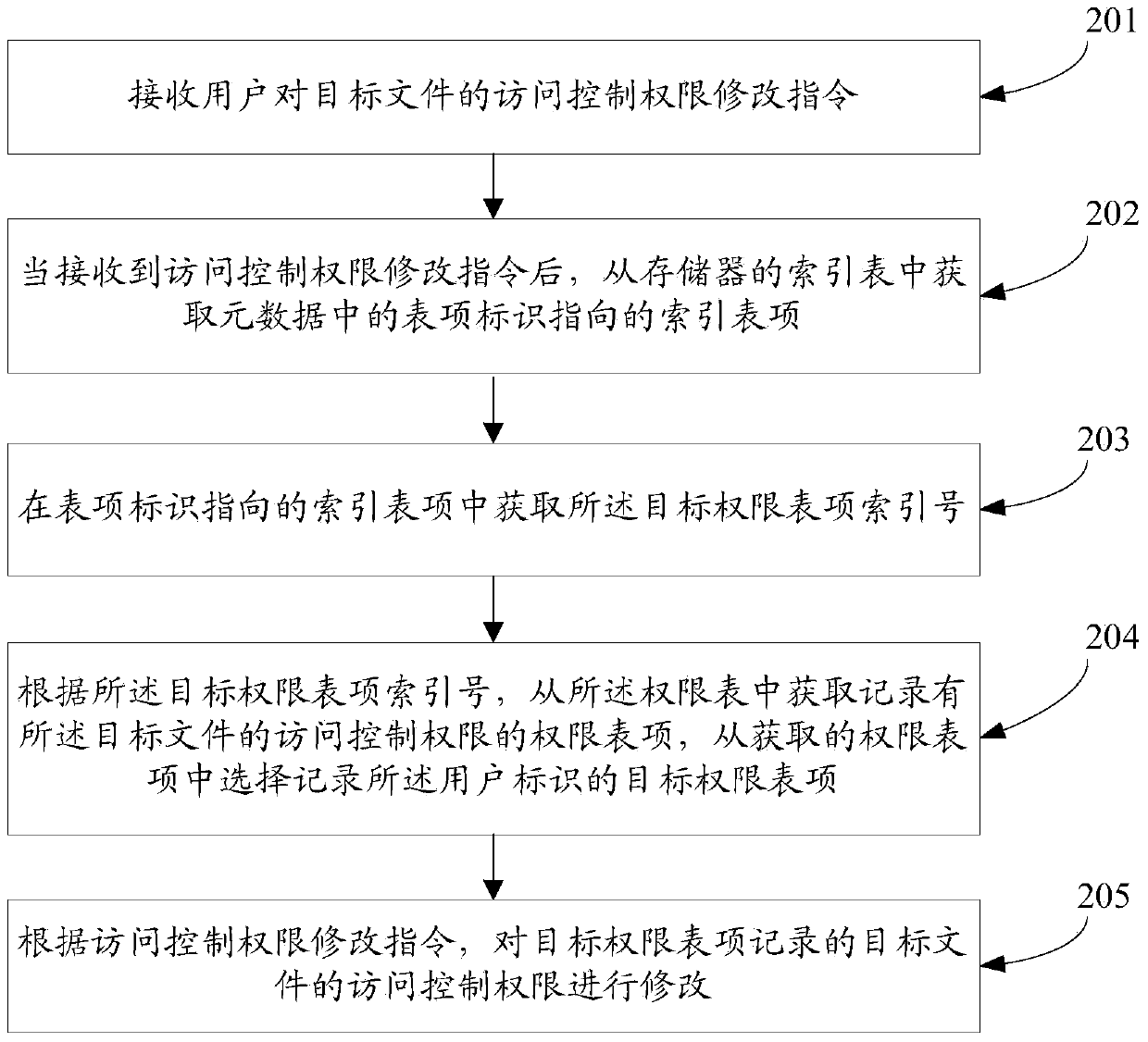
ActiveCN103620616AReduce complexityIncrease speedDigital data protectionFile system administrationRights managementComputer file
This invention discloses an access control right management method and a device, relating to the computer filed, providing convenience to management for large quantity of access control right information and improving operation efficiency of the system. The access control right management method comprises: acquiring index table entries in the index table when the control order for the target file from the user is obtained; acquiring the ?table entry index number in the obtained index table; acquiring the access table entry recording the target files from the right table according to the ?table entry index number, and selectively recording the target right table entries of the user identifications from the obtained right table entries; and determining whether the control order meet the access control right in the target right table entries, if yes processing the control order. The invention is mainly applied in the computer access control management.
Owner:HUAWEI TECH CO LTD
IPTV access control, personalized advertisement, personalized electronic program guide providing method and system using fingerprint scanner equipped set-top box
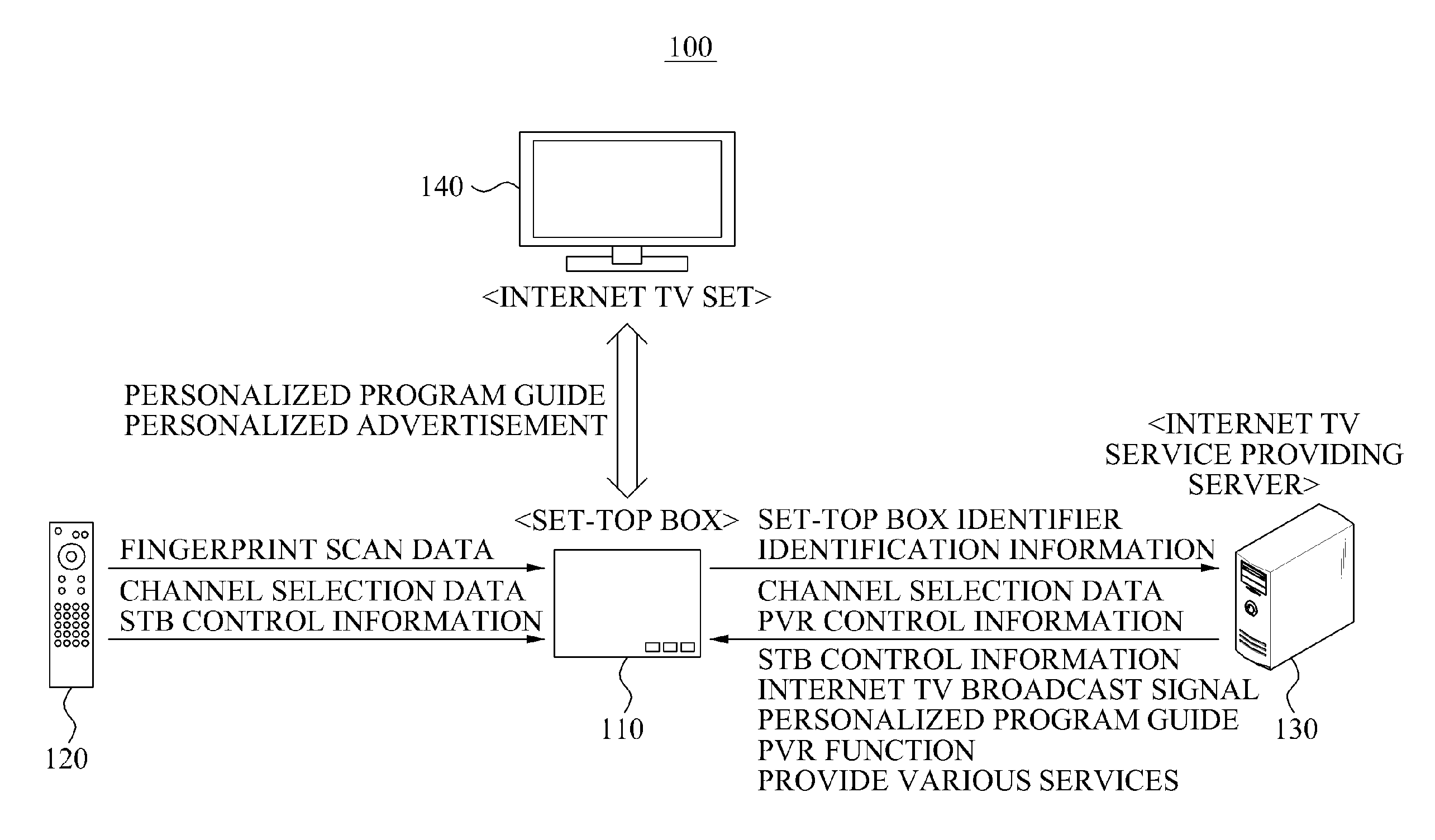
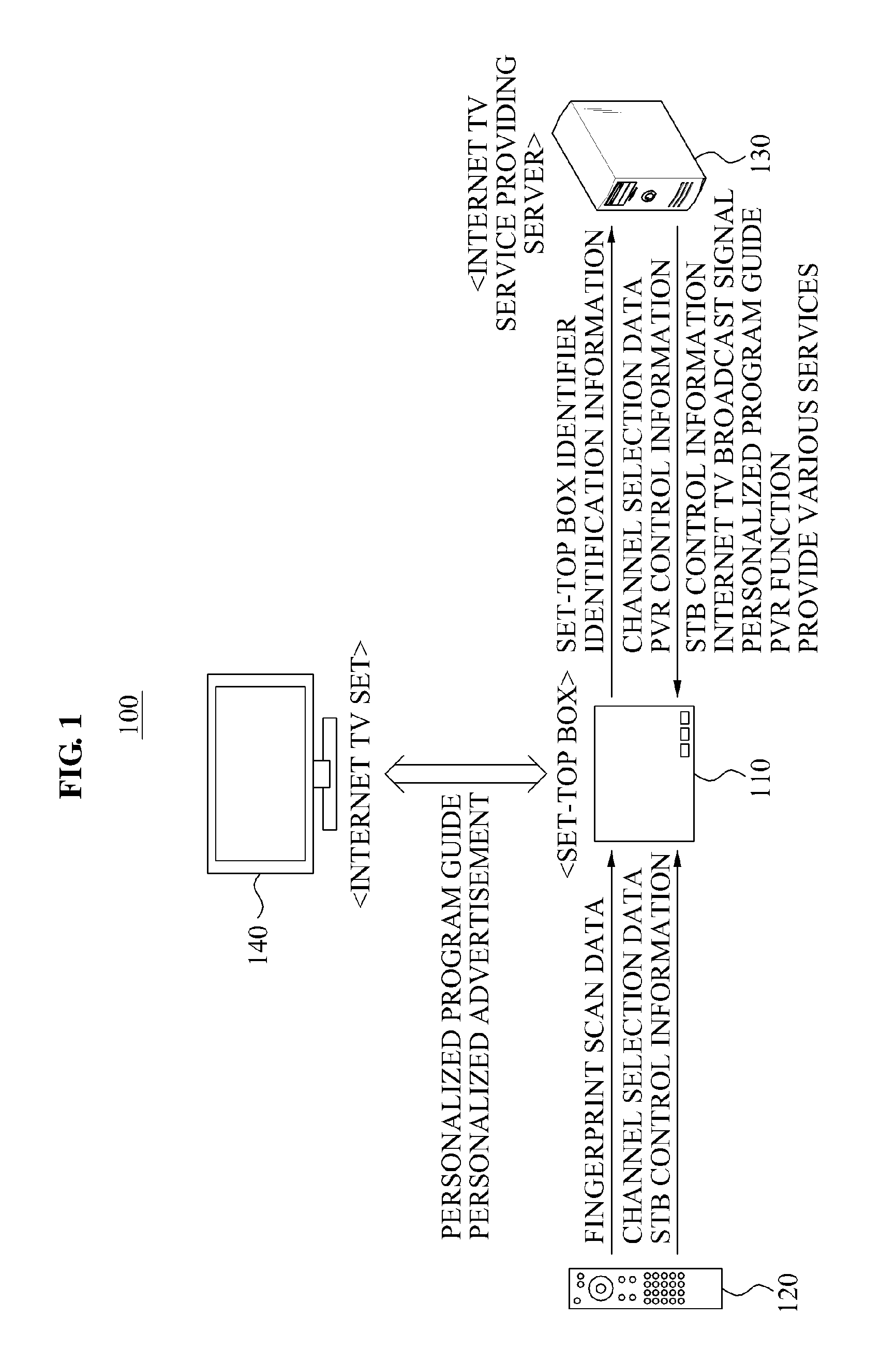
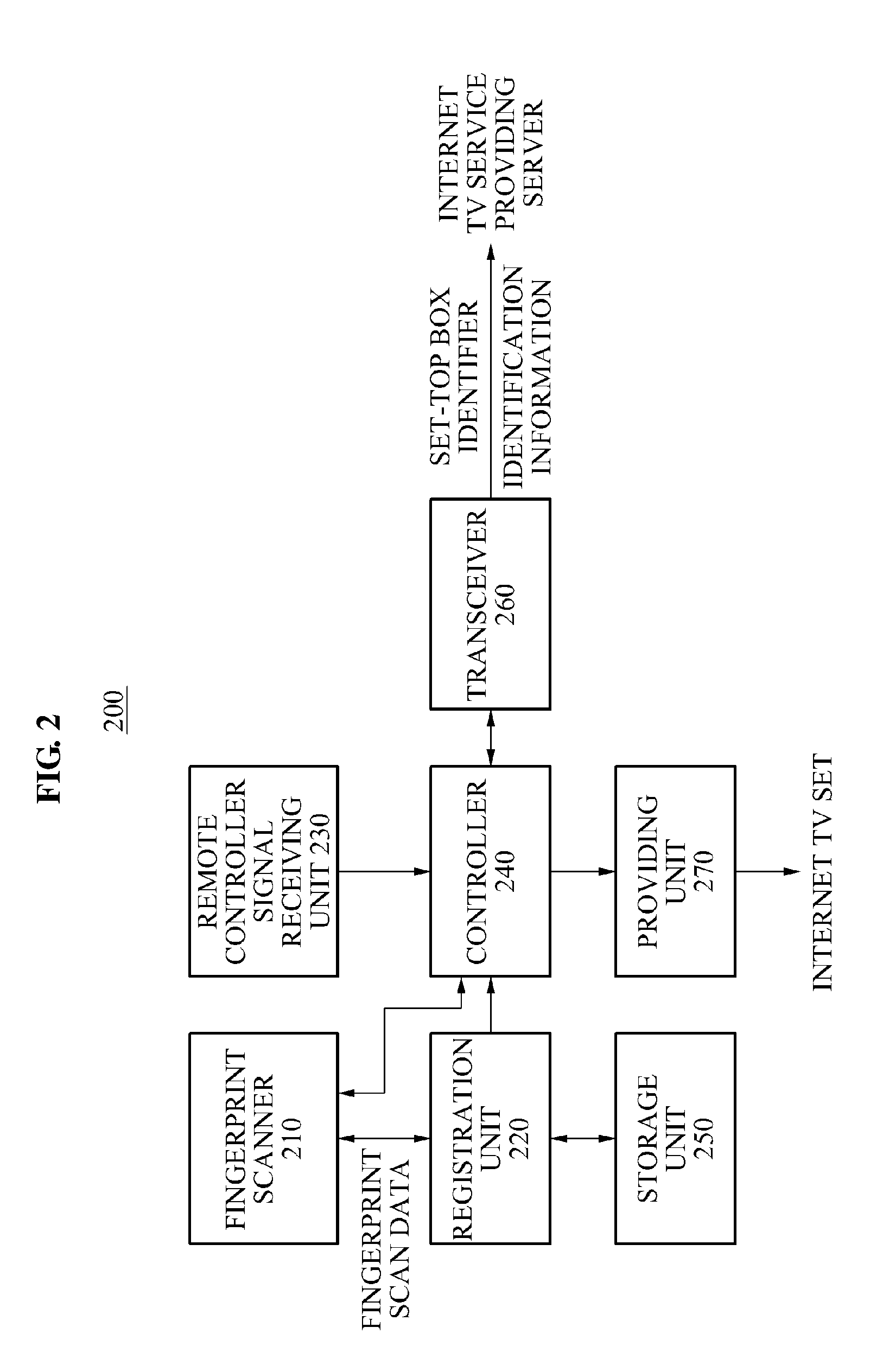
InactiveUS20110113441A1Easy to identifyGood choiceTelevision system detailsAnalogue secracy/subscription systemsPersonalizationThe Internet
Provided is a personalized program providing method and system. The personalized program providing system may provide a view restriction, a personalized advertisement, or a personalized program guide using a set-top box including a fingerprint scanner. The personalized program providing system includes a set-top box to scan a fingerprint using a fingerprint scanner to identify identification information associated with a user and to transmit the identified identification information to an Internet TV service providing server, an Internet TV service providing server to transmit a personalized program guide corresponding to the transmitted identification information to the set-top box, and an Internet TV set to provide the transmitted personalized program guide.
Owner:ELECTRONICS & TELECOMM RES INST
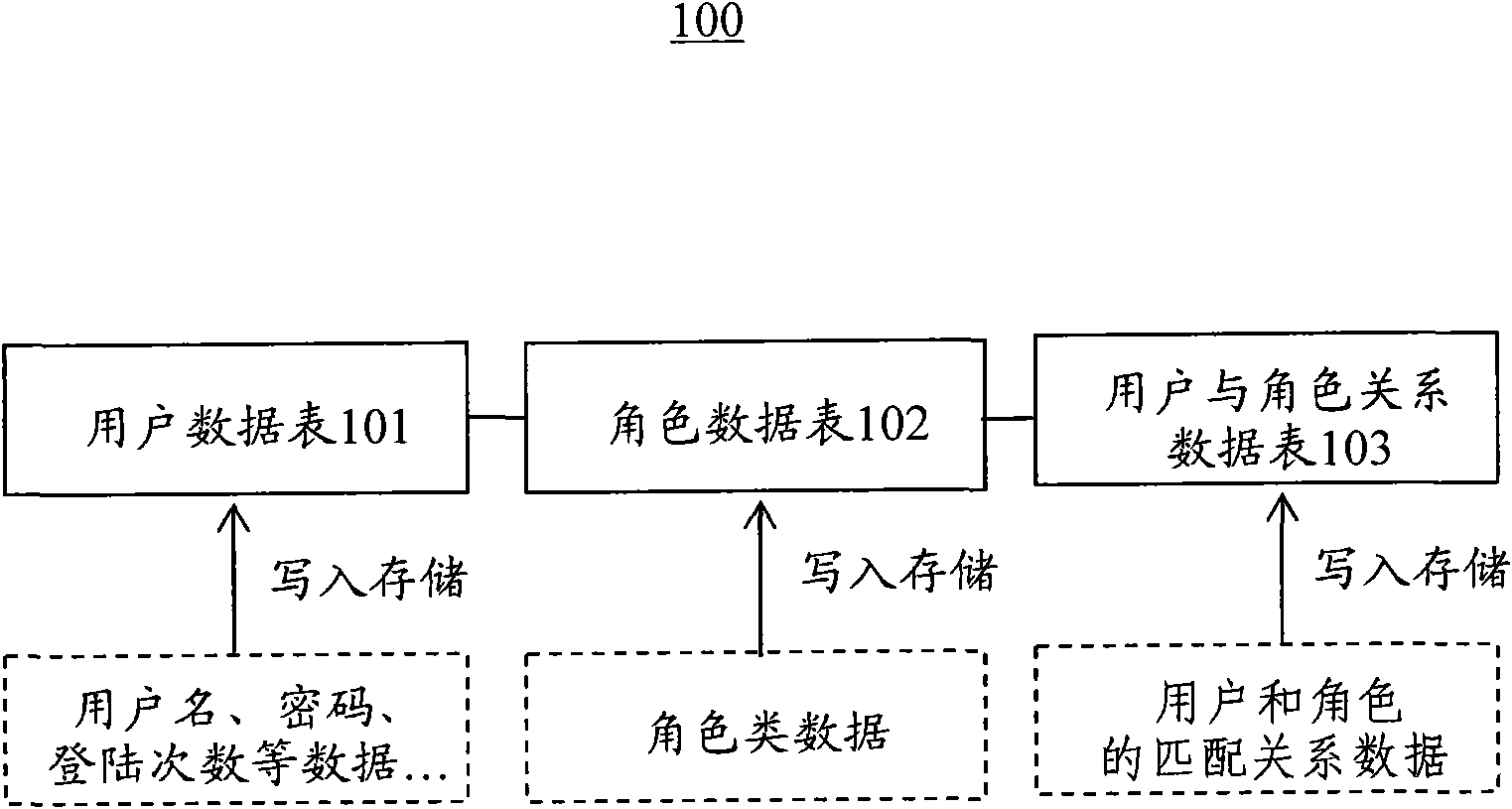
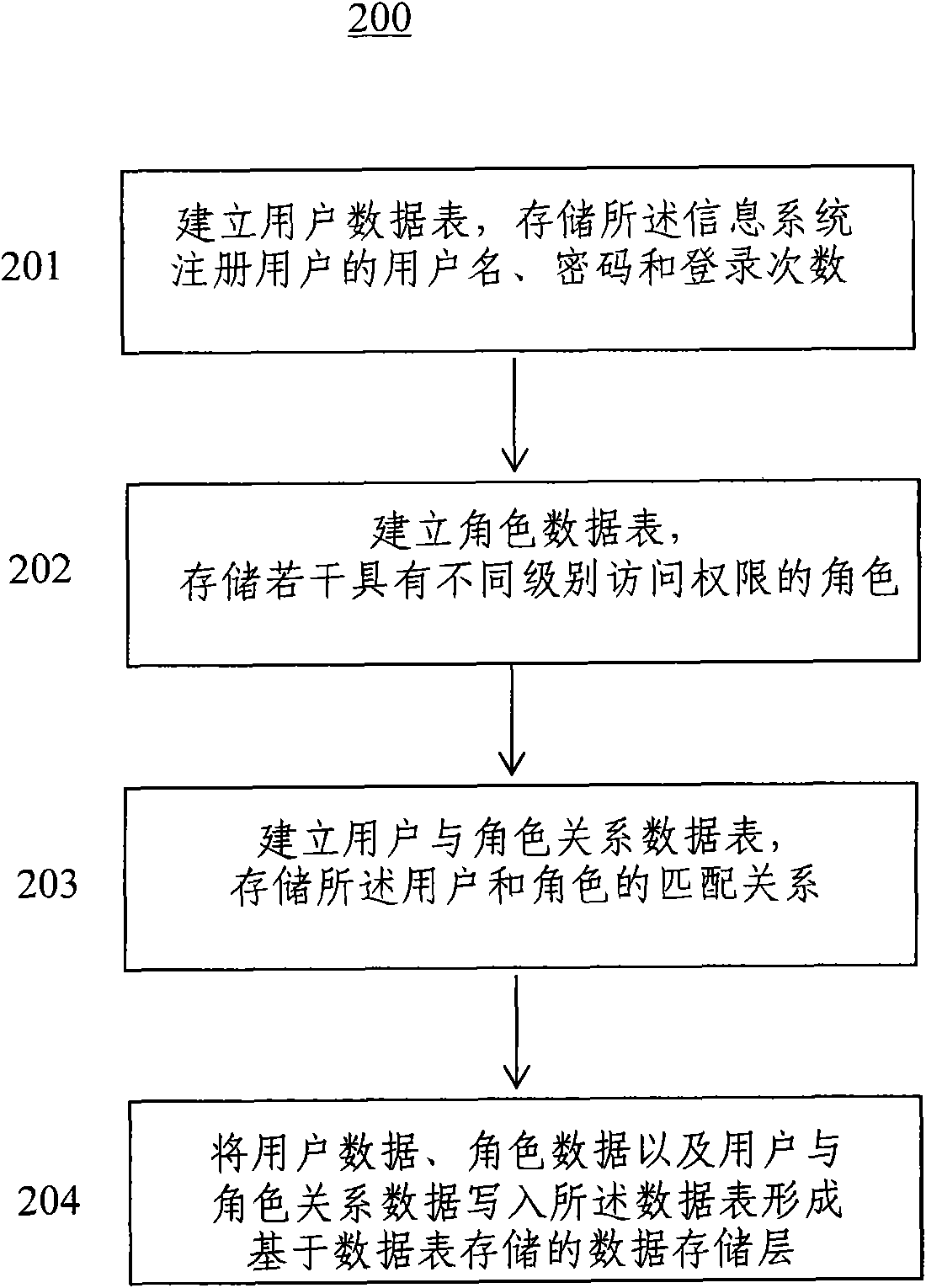
Role access control-based information system data storage layer and building method
InactiveCN102004868AAchieve matchingImplement modificationDigital data authenticationSpecial data processing applicationsPasswordRole-based access control
The invention discloses a role access control-based information system data storage layer and a building method. User name, password and login times of information system registered users are stored through a user data table; a plurality of roles with access authorities of different levels are stored through a role data table; and a matching relationship between the users and the roles is stored through a user and role relationship data table. The data tables of the data storage layer are called by an information system to realize modification of system user information and matching between the users and the roles and further fulfill the purpose of endowing and controlling the access authorities of the users.
Owner:SANDA UNIVERSITY
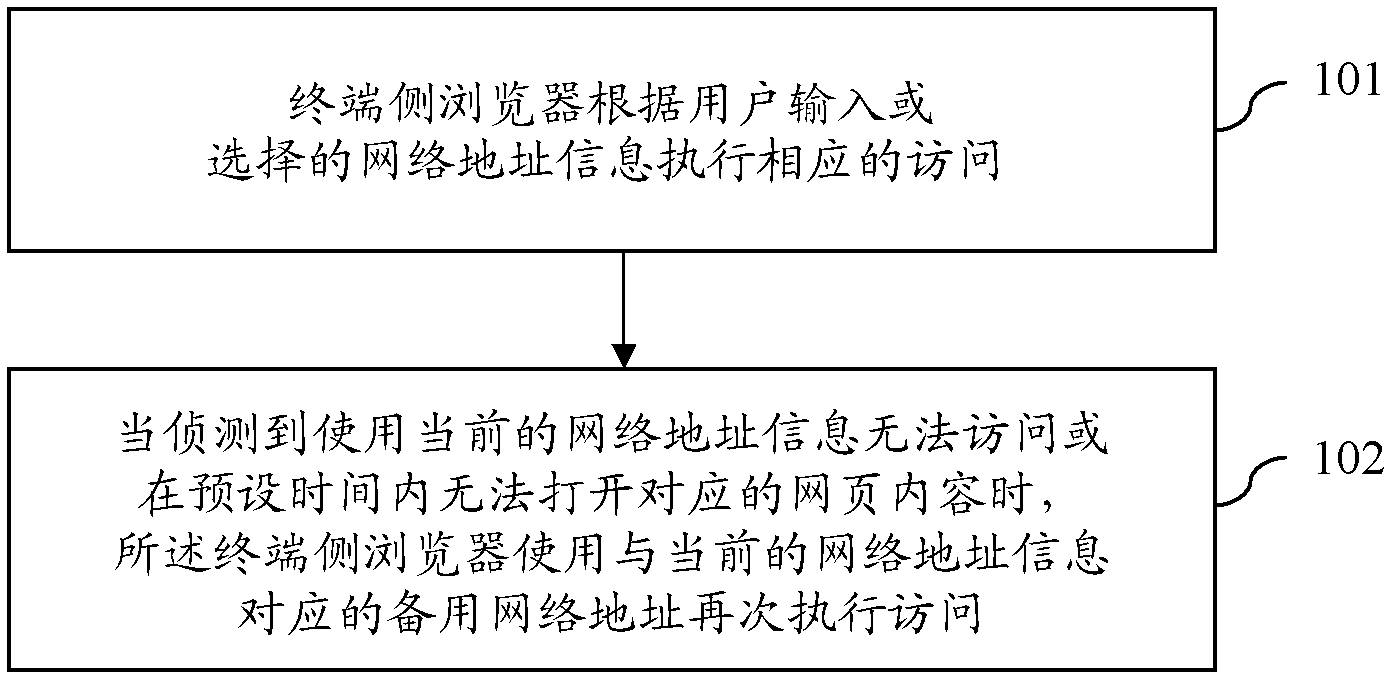
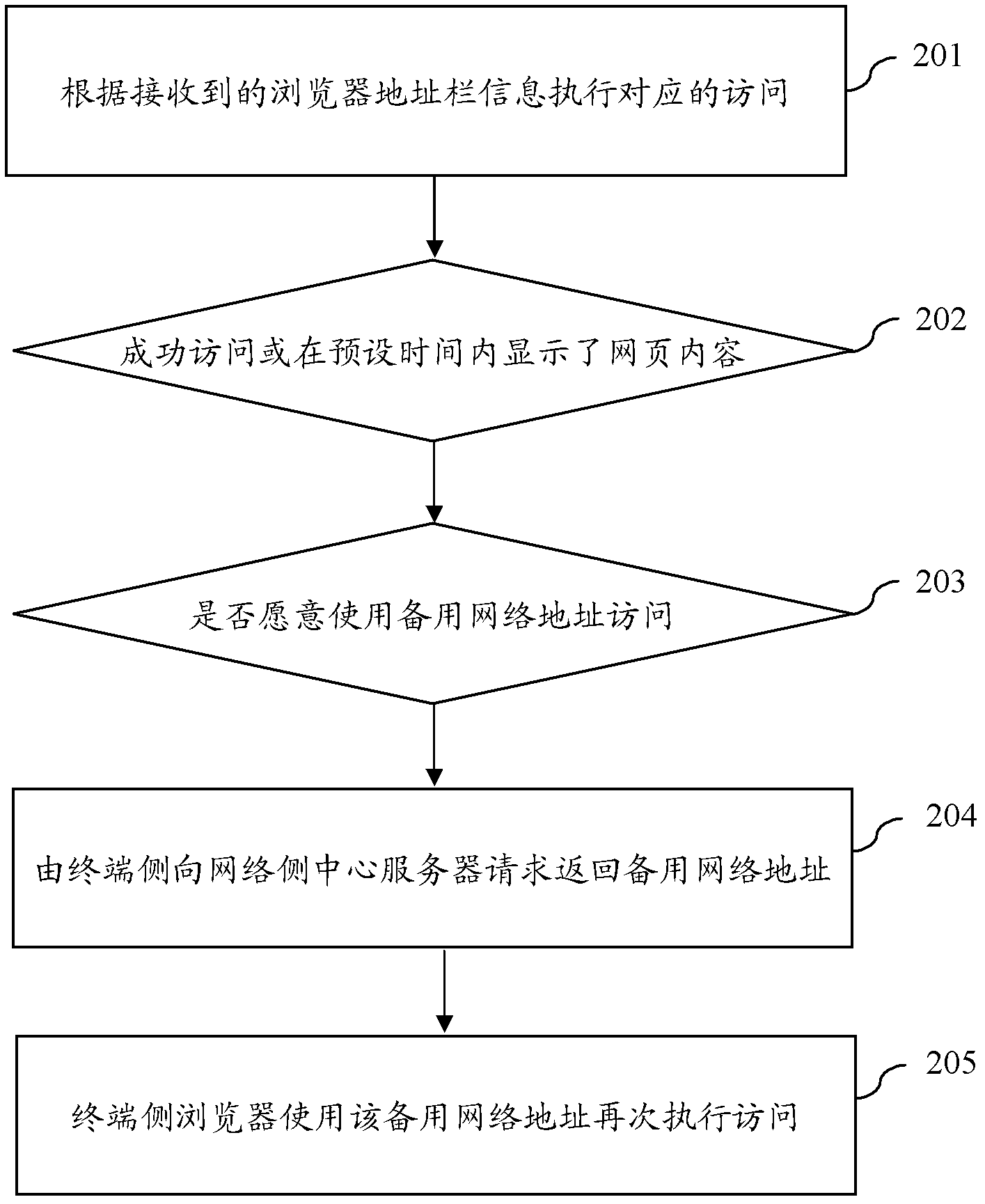
Method and system for browser access control
InactiveCN102214223AAchieve accessAvoid access to failed resultsTransmissionSpecial data processing applicationsUser inputNetwork addressing
The invention provides a method and a system for browser access control. A terminal side browser, according to network address information input or selected by users, executes corresponding access; and when the situation is detected that access cannot be realized by using current network address information or corresponding webpage content cannot be opened, the terminal side browser uses a backup network address corresponding to the current network address information to execute access once again. By the method provided by the invention, a browser is guided to help users use the backup network address to execute access once again when the browser cannot be accessed normally and the webpage fails to be opened on time, thus the situation is avoided that only an access failure-related result, which is completely useless for users, is returned when the current network address cannot be accessed, instead, the access of users is implemented in other ways as much as possible or more information is offered to users.
Owner:QIZHI SOFTWARE (BEIJING) CO LTD
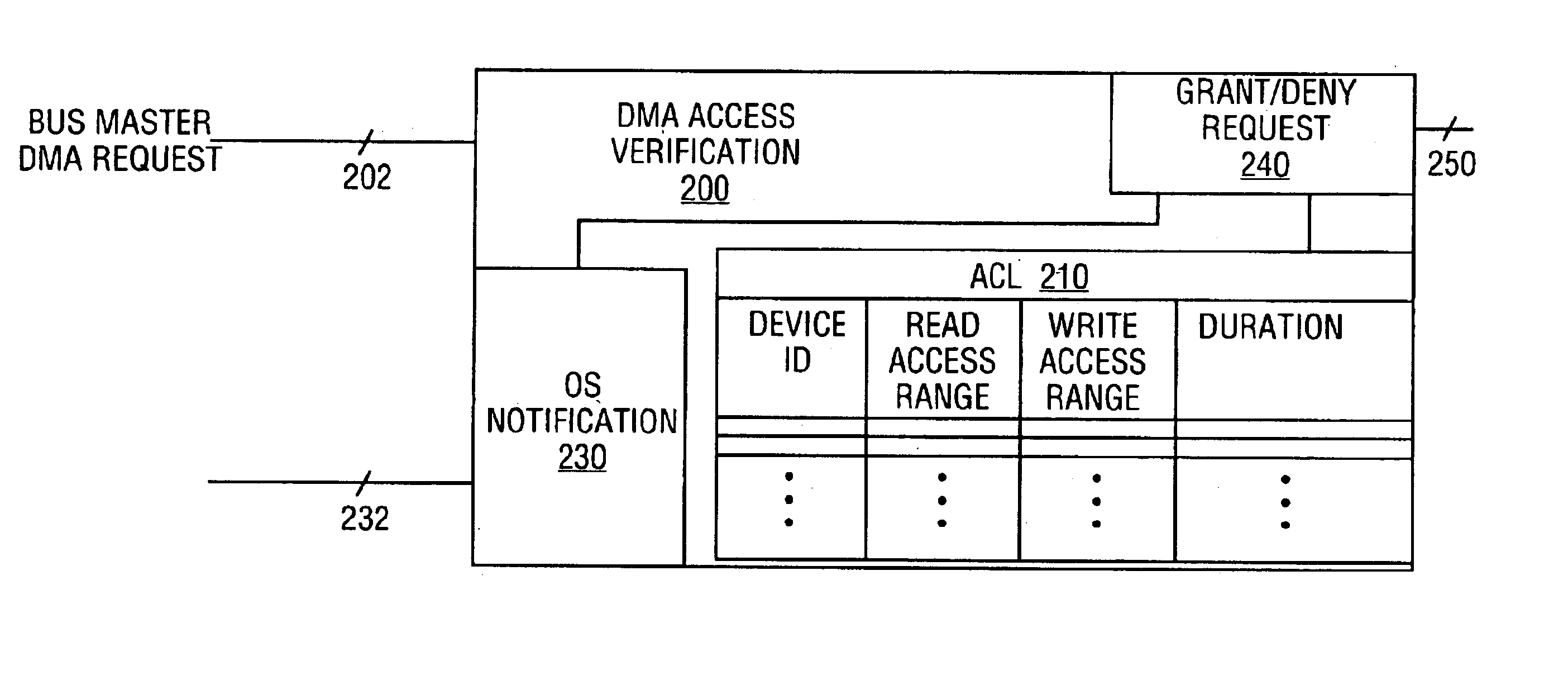
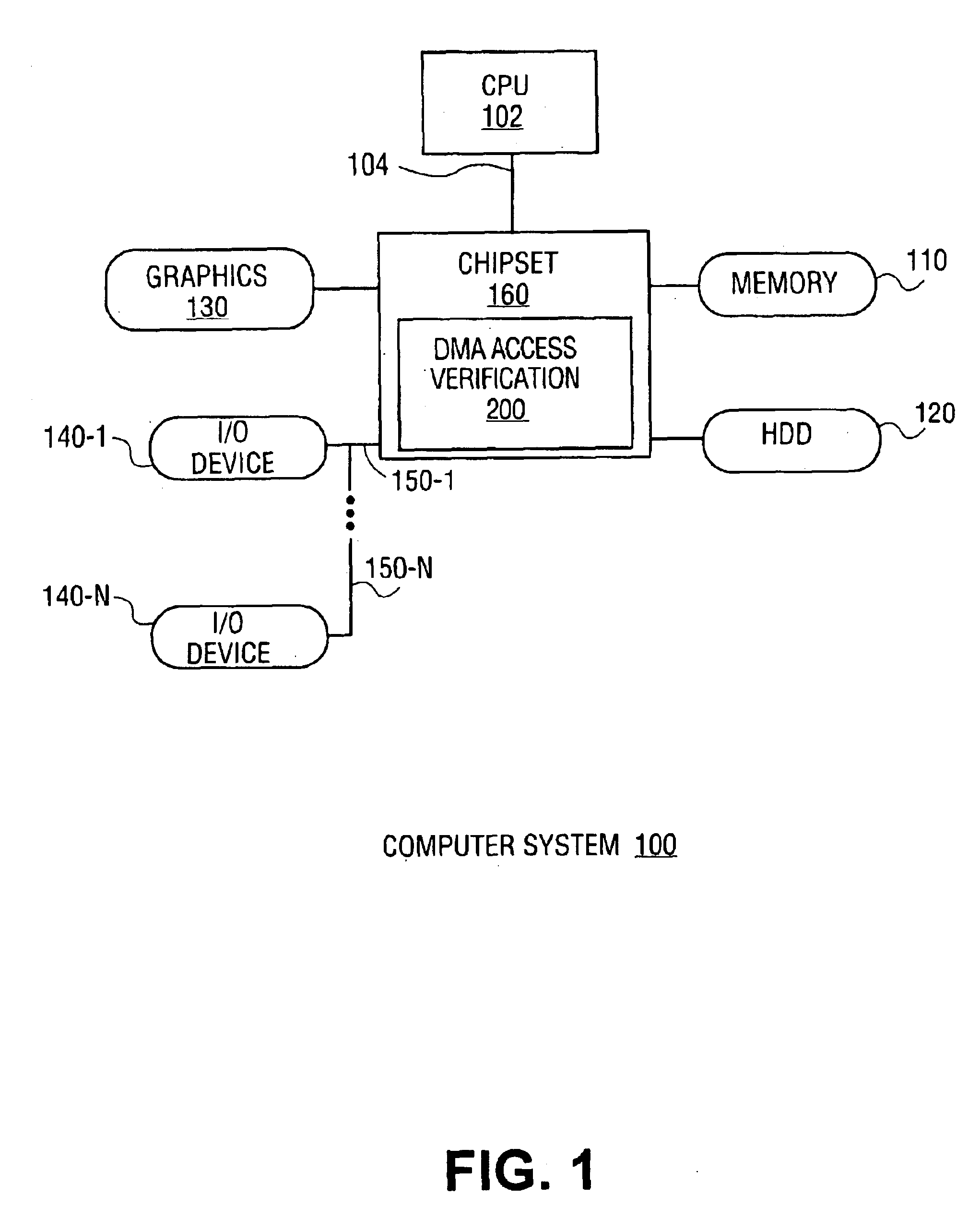
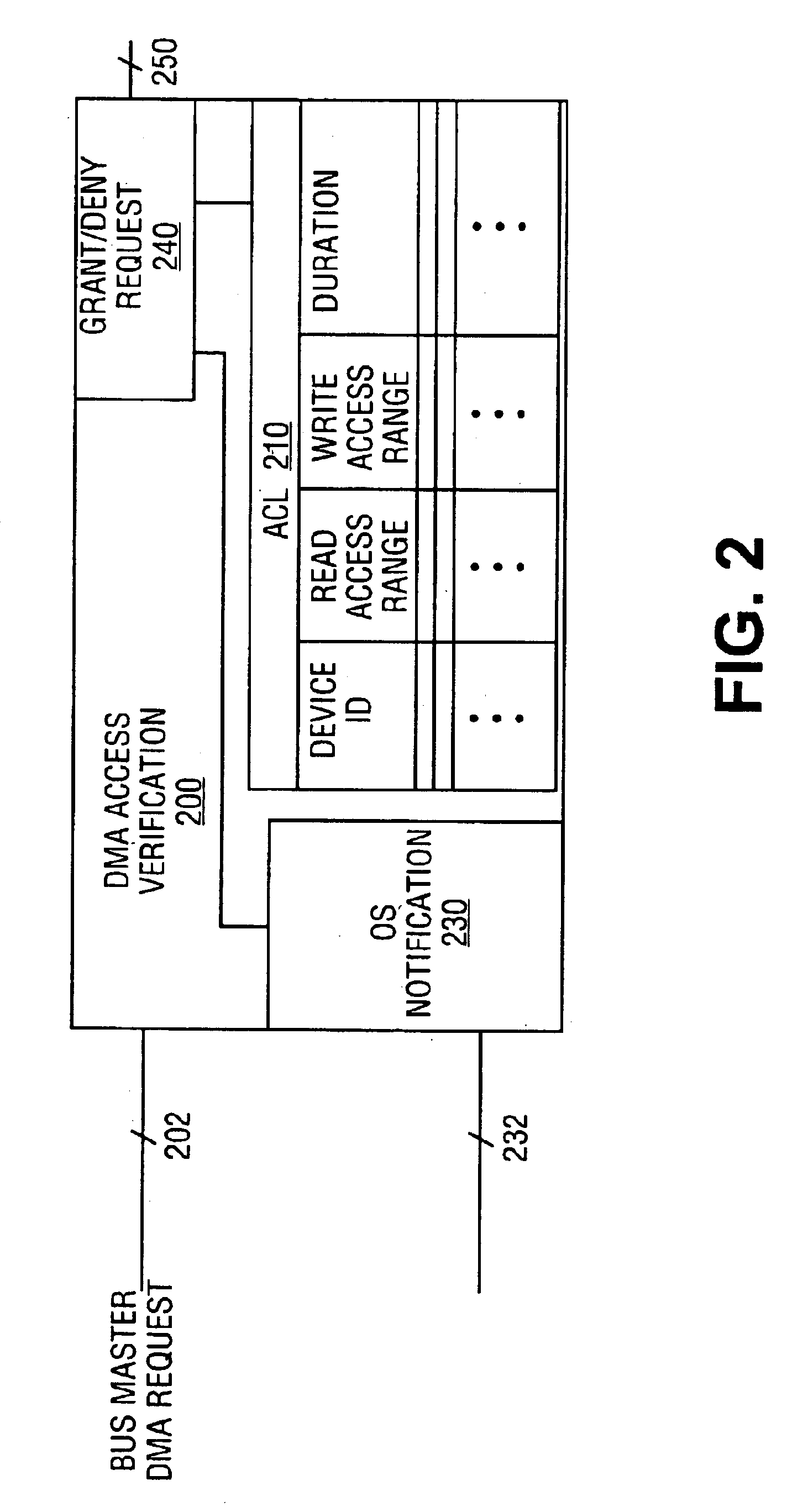
Apparatus and method of memory access control for bus masters
ActiveUS6922740B2Digital computer detailsElectric digital data processingDirect memory accessOperational system
A method and apparatus of memory access control for bus masters are described. In one embodiment, the method includes the receipt of a direct memory access (DMA) request from a device. Once the DMA request is received, DMA access rights of the device are determined according to an access control list (ACL). Once determined, the device is granted DMA access according to the determined memory access rights of the device. In other words, if a DMA request coincides with DMA access rights assigned to the device, the DMA request is executed. Otherwise, the operating system may be notified of an unauthorized DMA request.
Owner:TAHOE RES LTD
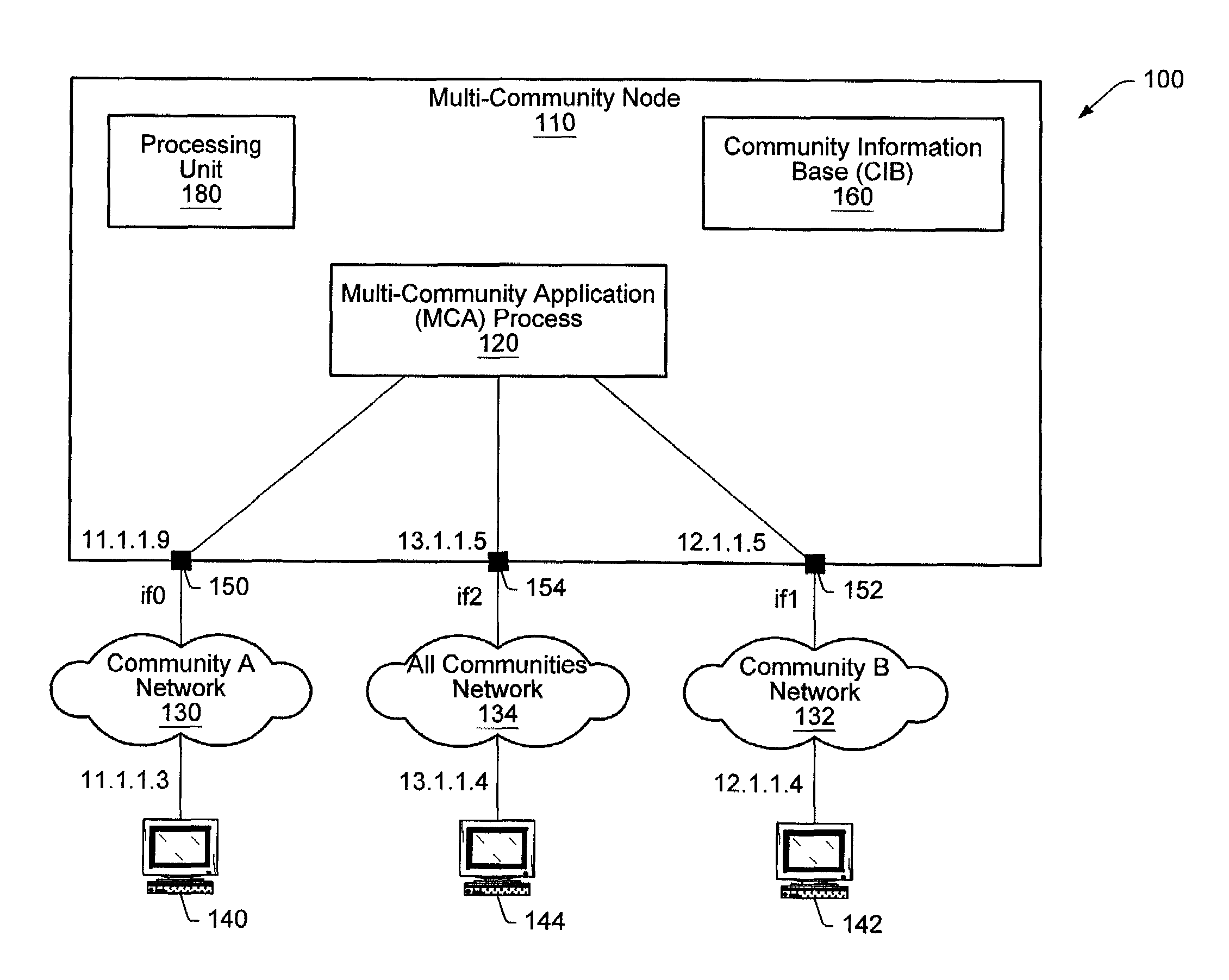
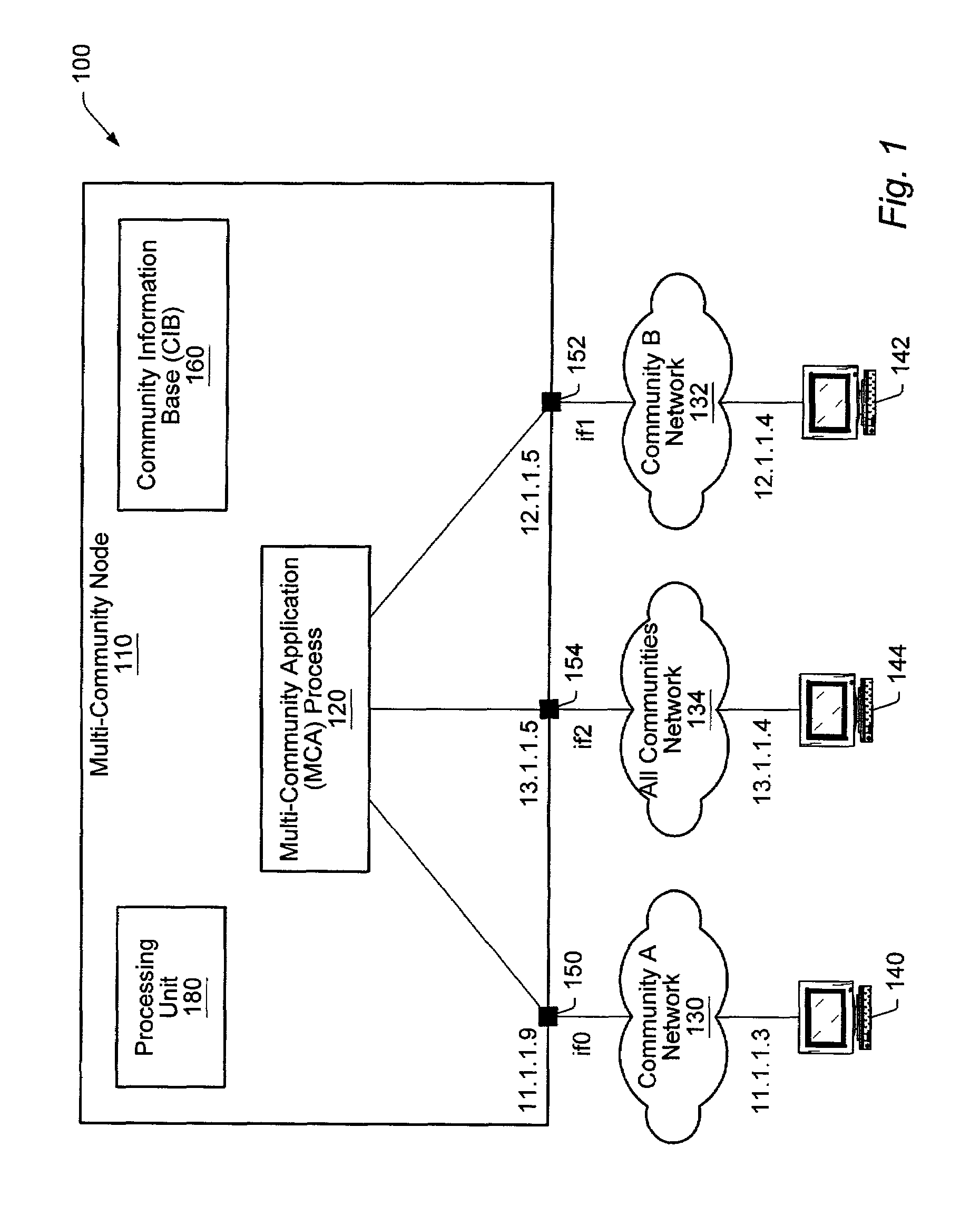
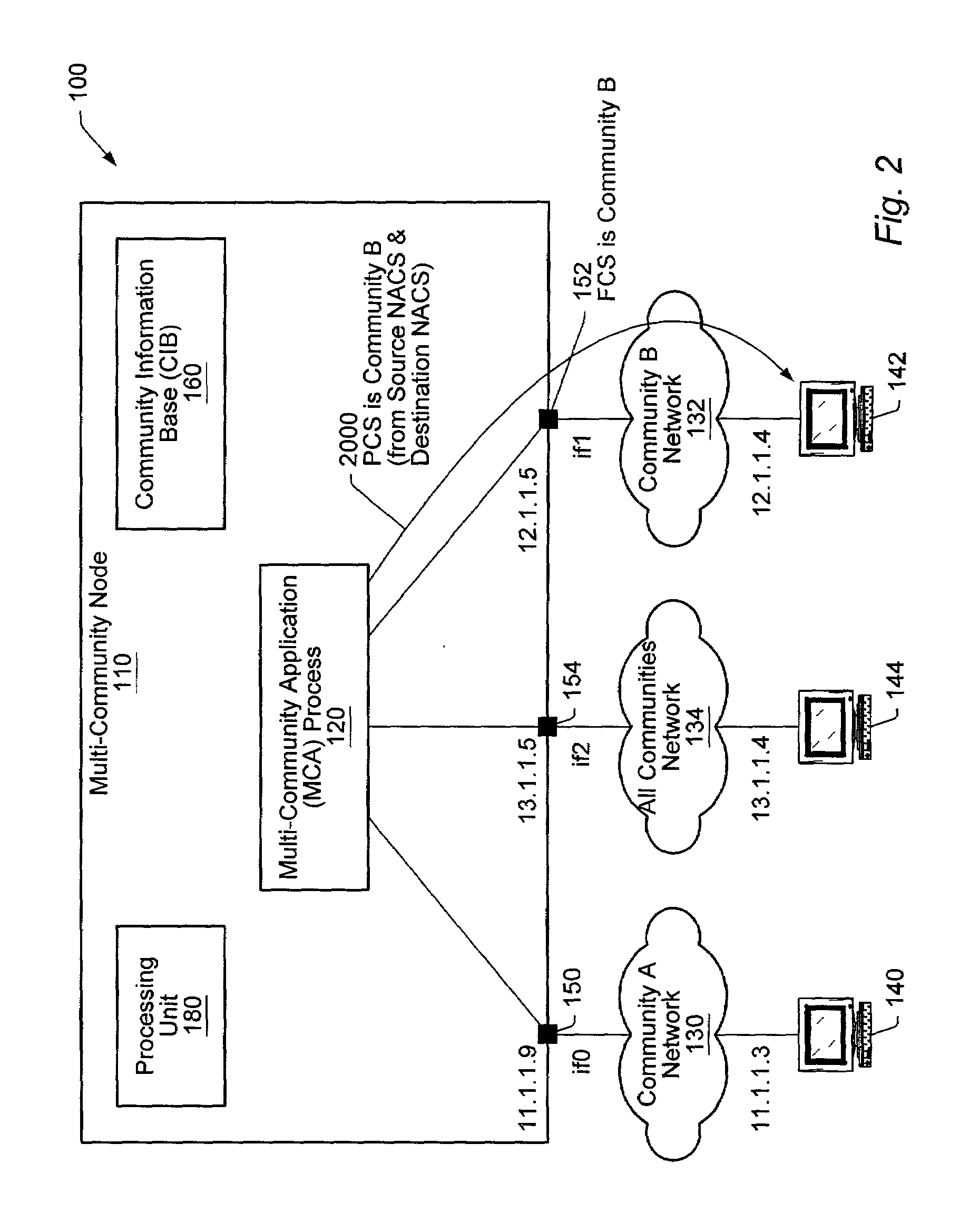
Community access control in a multi-community node
ActiveUS7447782B2Keep full controlMultiple digital computer combinationsTransmissionProcess informationWorld Wide Web
A method and mechanism of enforcing community access control in a computer network, wherein access to objects by users and processes is controlled. A Multi-Community Node (MCN) processes information for users in multiple communities and must enforce a community separation policy. The enforcement method and mechanism use a database of associations of sets of communities corresponding to users, processes, and system objects. Upon receiving a request for access to an object by a user, the MCN permits access if a user community set (UCS) of the user is a superset of an object community set (OCS) of the object; otherwise, access is denied. Upon receiving a request for access to an object by a process, the MCN permits access if an application process community set (ACS) of the process is a superset the OCS of the object; otherwise, access is denied.
Owner:ORACLE INT CORP
Cloud voiceprint recognition system and method for community access control
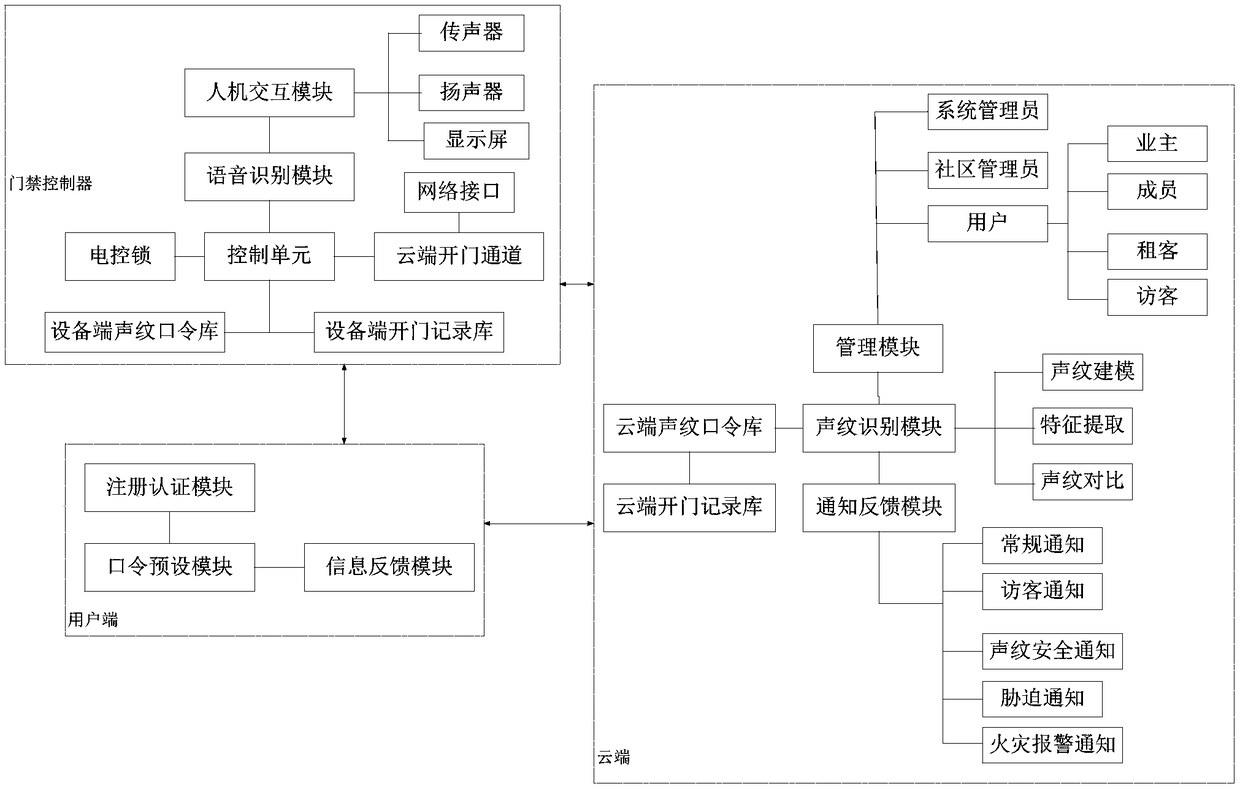
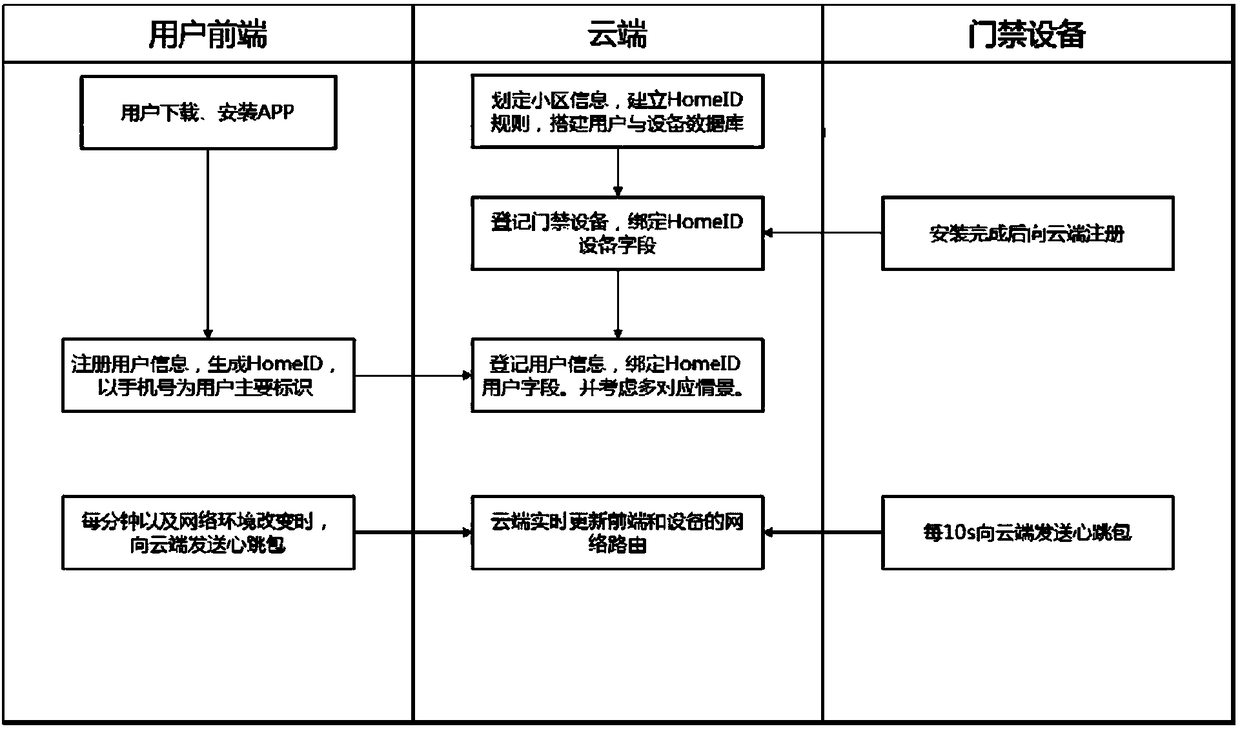
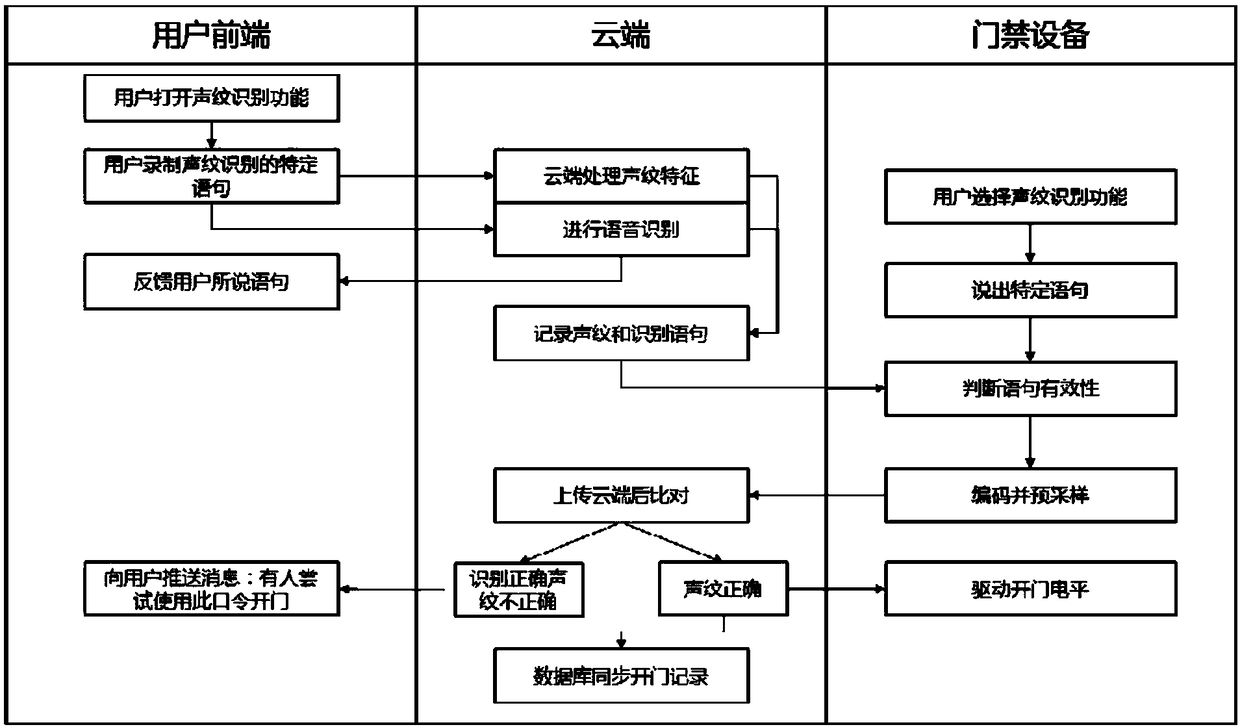
ActiveCN108320752ASmooth trafficSmooth access controlData processing applicationsSpeech analysisUser inputPassword
The invention provides a cloud voiceprint recognition system and method for community access control. The method is characterized in that a user inputs a preset voiceprint password through a user terminal, and after successful voice recognition, the preset voiceprint password is transmitted to a cloud server for processing and storage; and then, the user can speak out a check voiceprint password at an access controller, and the access controller carries out voice recognition and voiceprint acquisition, and then, transmits the check voiceprint password to the cloud end for voiceprint modeling processing and comparison, and recognition is carried out by utilizing powerful computation ability of the cloud end. When the preset voiceprint password and the check voiceprint password are collected, voice recognition is carried out to improve recognition efficiency; and legality of the voiceprint is verified through asymmetric error rate, so that the user can pass through the access control more smoothly, and each opening action and record can be obtained. The method and system provide basis for deploying a voiceprint recognition system in a community in a large area, so that user learningcost is low, construction-side installation cost is low and operation-side maintenance cost is low, and passage convenience and passage efficiency of community access control can be improved effectively.
Owner:青岛易方德物联科技有限公司
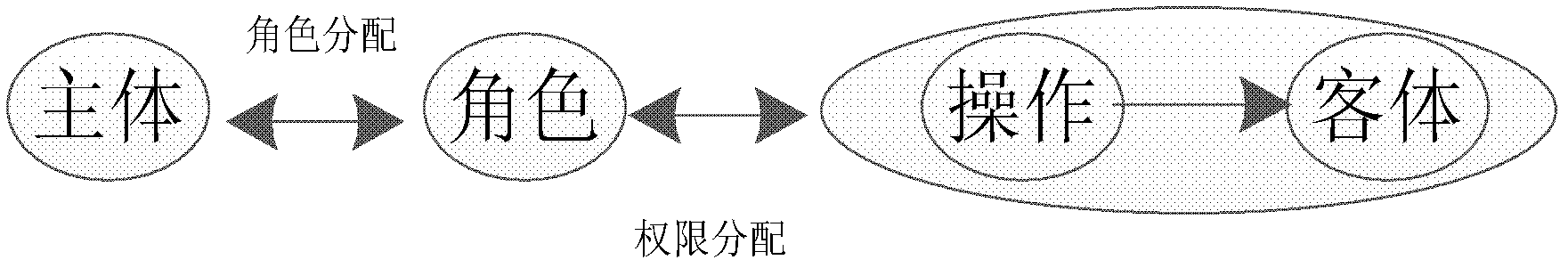
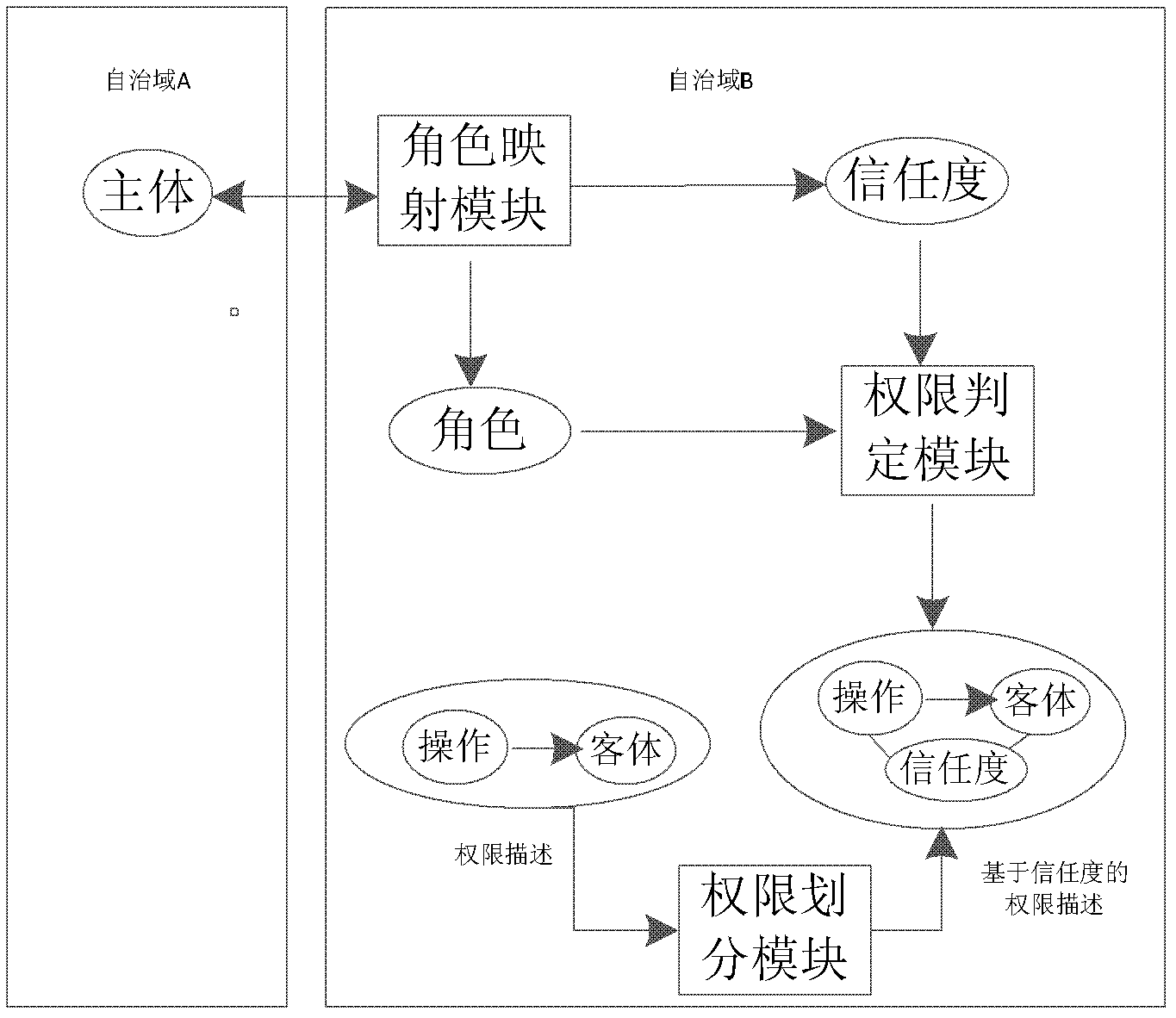
Trust-based access control method and system thereof
The invention discloses a trust-based access control method and a system thereof, belonging to the field of computer access control. The trust-based access control method comprises the following steps: 1), establishing a role-trust describing model; 2), for each role r in an autonomous domain B, determining a mapping relationship of a role in another autonomous domain A to the role r, and making mapping of the role in the A to the role in the B meet the mapping relationship; 3), according to the mapping relationship, dividing an authority set of the role r into different authority subsets, and correlating the divided subsets to corresponding trust values; 4), when of a main role in the A accesses resources in the B, analyzing information of the accessing main role first and then mapping the information of the accessing main role to the role in the autonomous domain B, and obtaining a trust value; and 5) according to the role information and the trust value of the accessing main role, determining a resource accessing authority of a current access request by the autonomous domain B. The trust-based access control method and the trust-based access control system effectively compensate for a defect that the conventional role access control cannot adapt to a distributed cooperative development environment.
Owner:山东经伟晟睿数据技术有限公司
Computer file control through file tagging
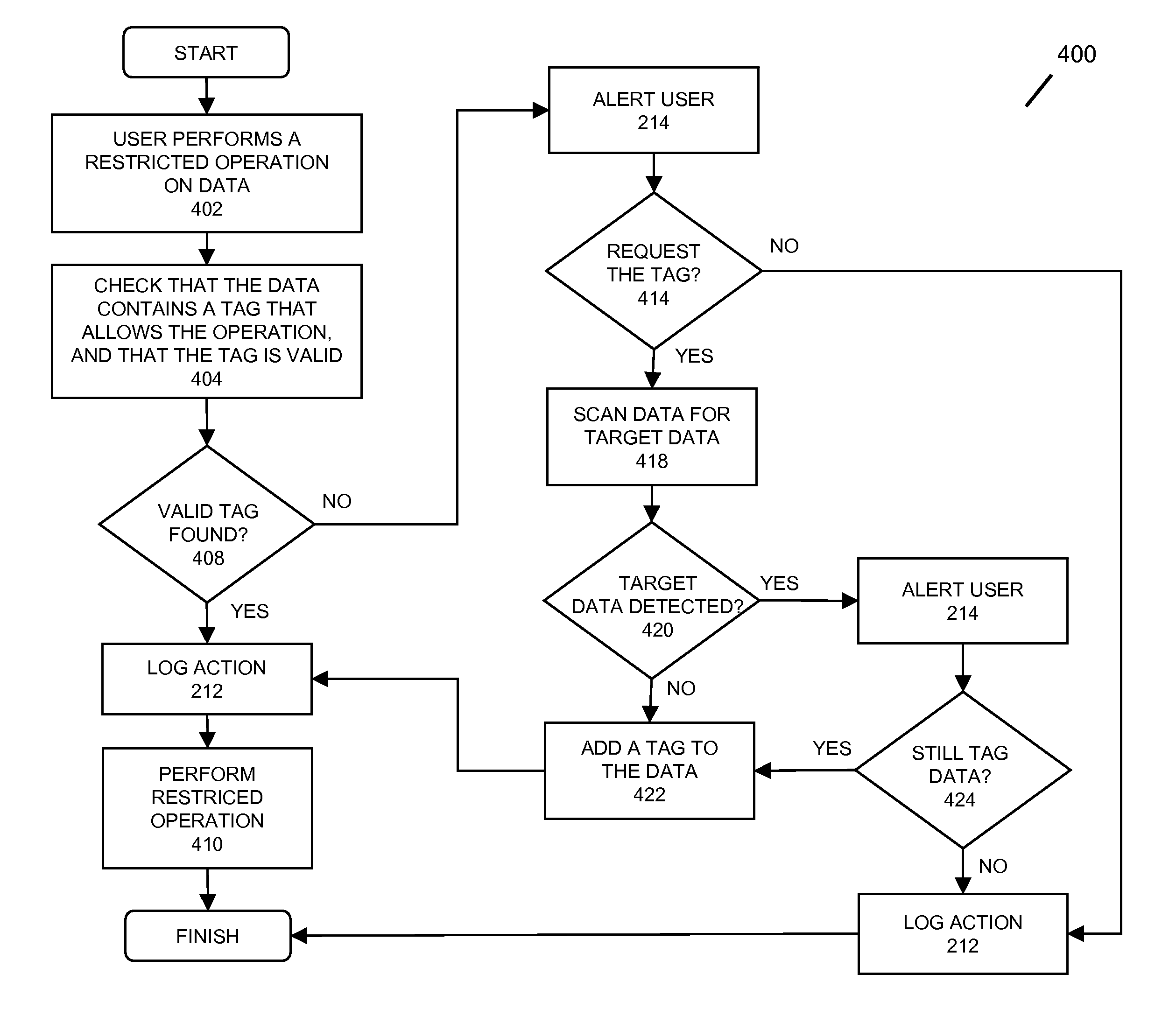
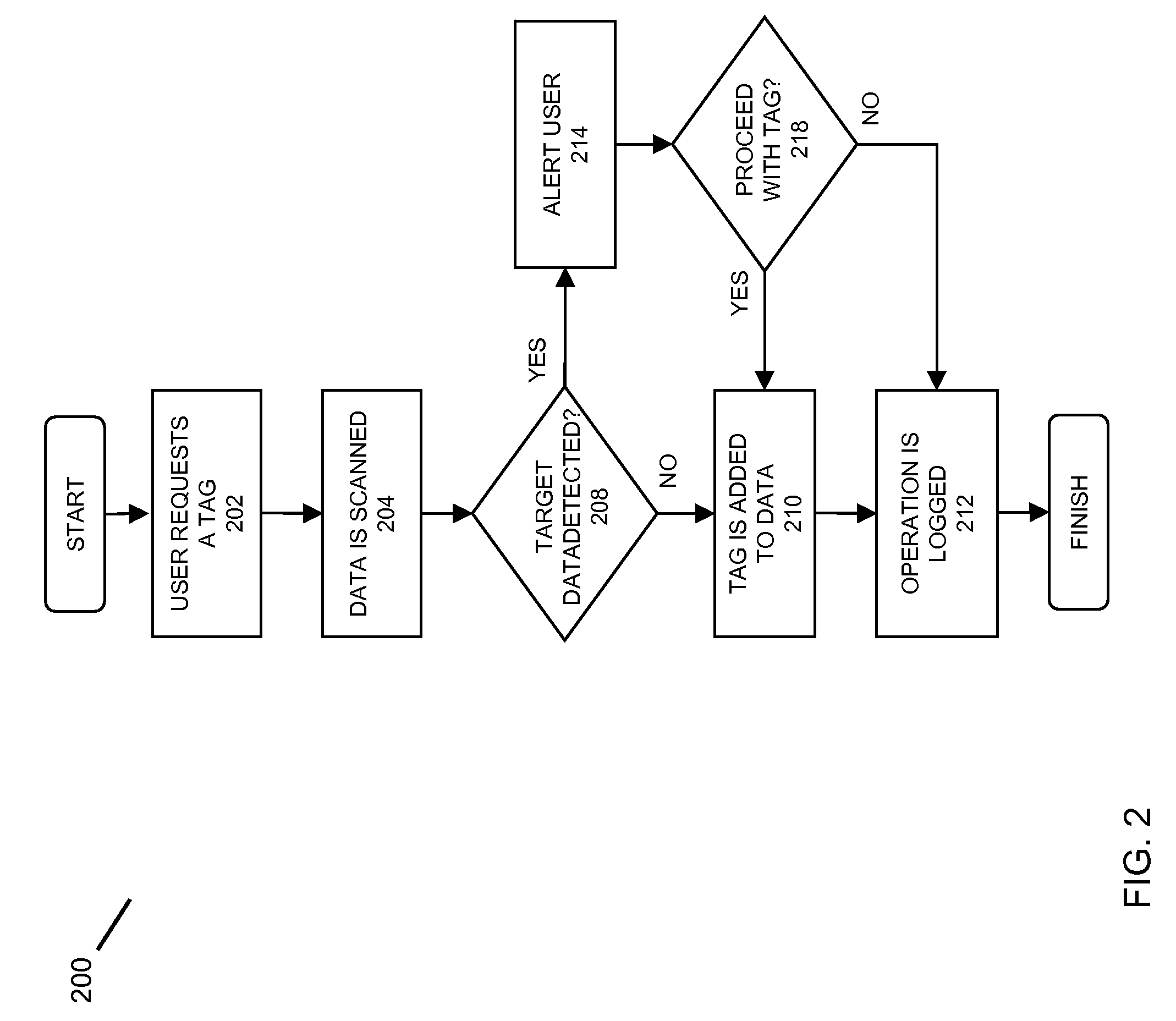
ActiveUS8286255B2Digital data processing detailsUnauthorized memory use protectionComputer fileComputer access control
In embodiments of the present invention improved capabilities are described for providing data protection through the detection of tags associated with data or a file. In embodiments the present invention may provide for a step A, where data may be scanned that is intended to be communicated from the client computing facility. In response to step A, at step B, restricted data may be identified by identifying an absence of a tag associated with the data. And finally, in response to step B, at step C, an interruption to the intended communication may be caused.
Owner:SOPHOS
Role access control system and method based on block chain smart contract
ActiveCN110348202ANot easy to tamper withWith traceability functionDigital data protectionDigital data authenticationRole-based access controlControl system
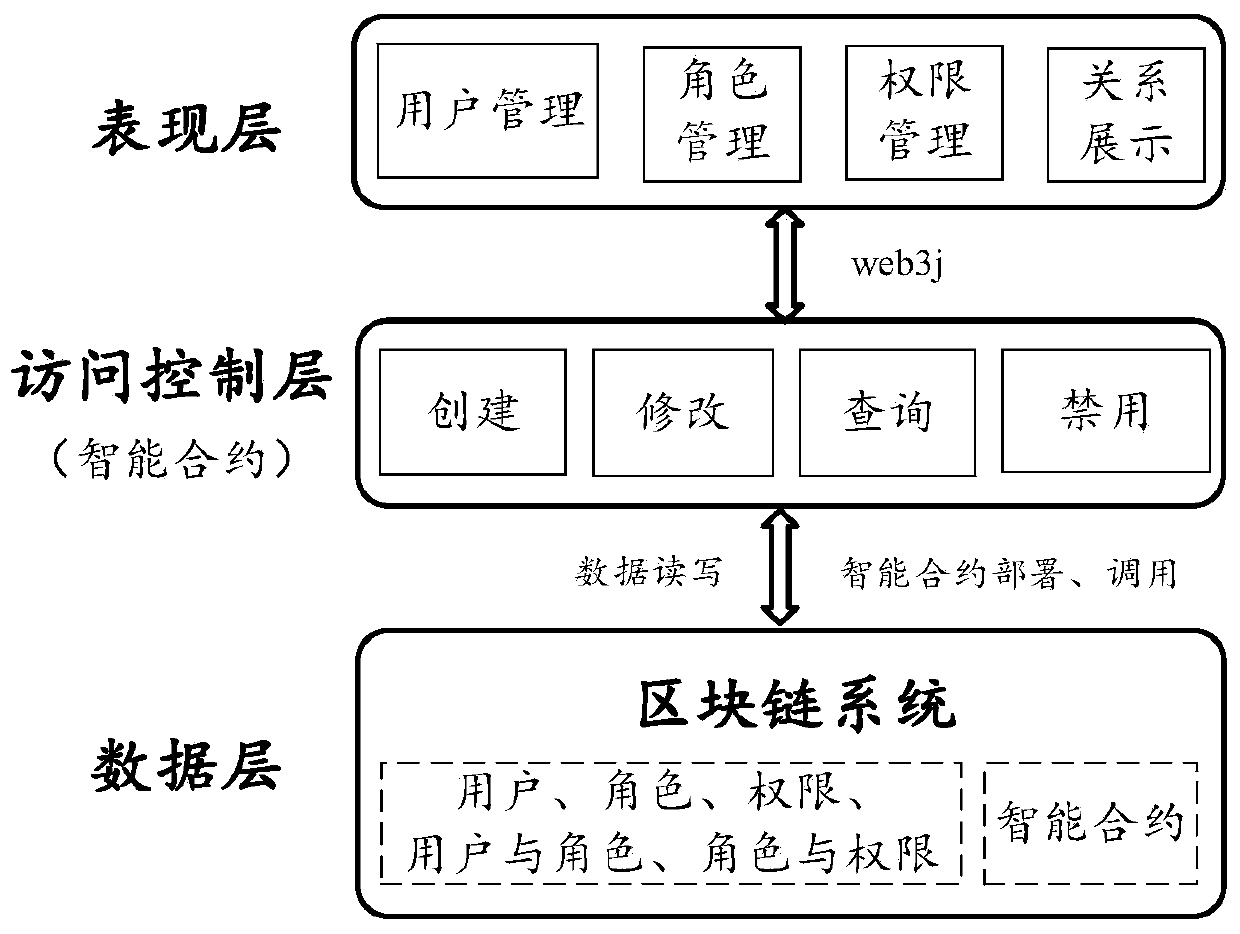
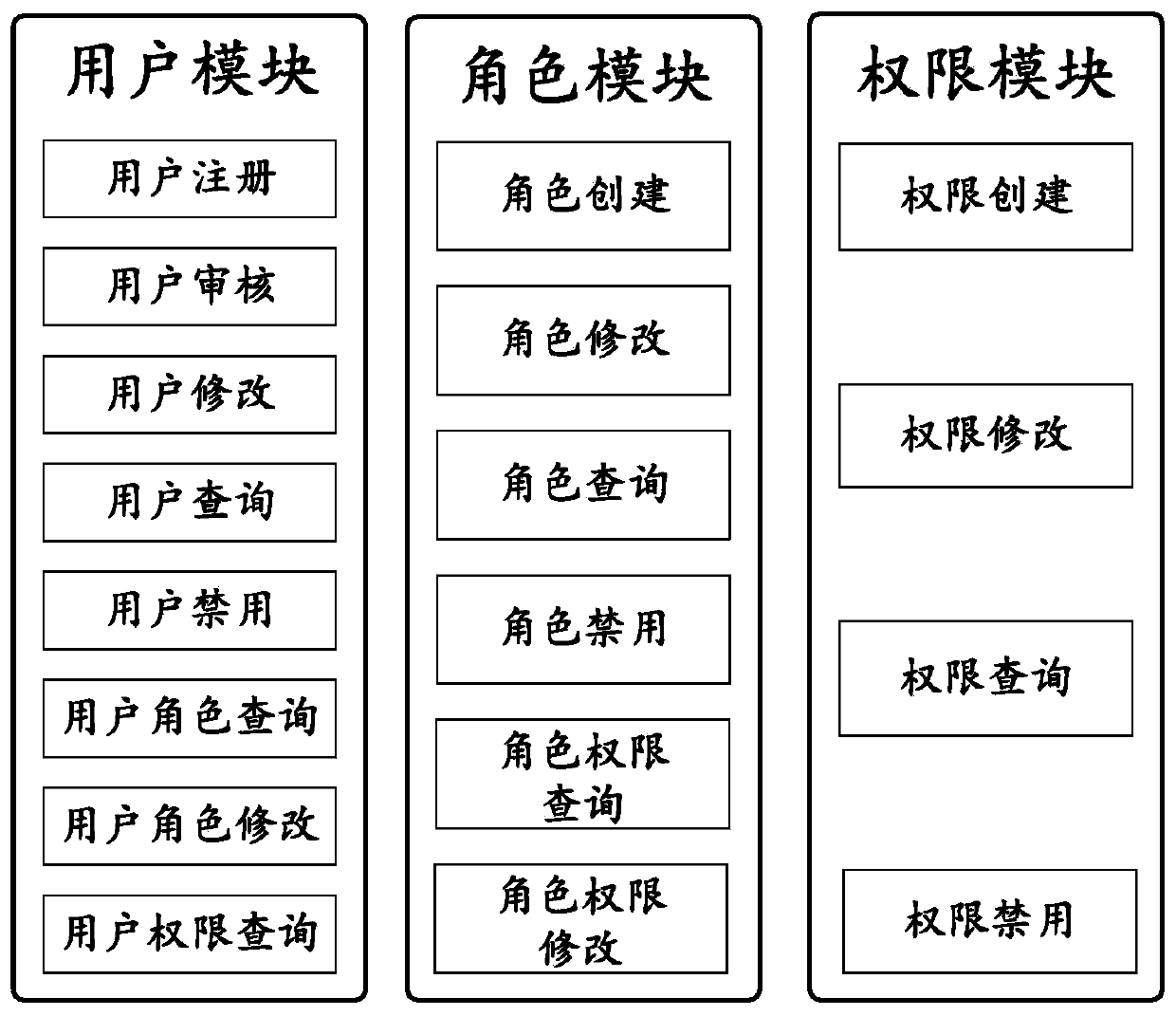
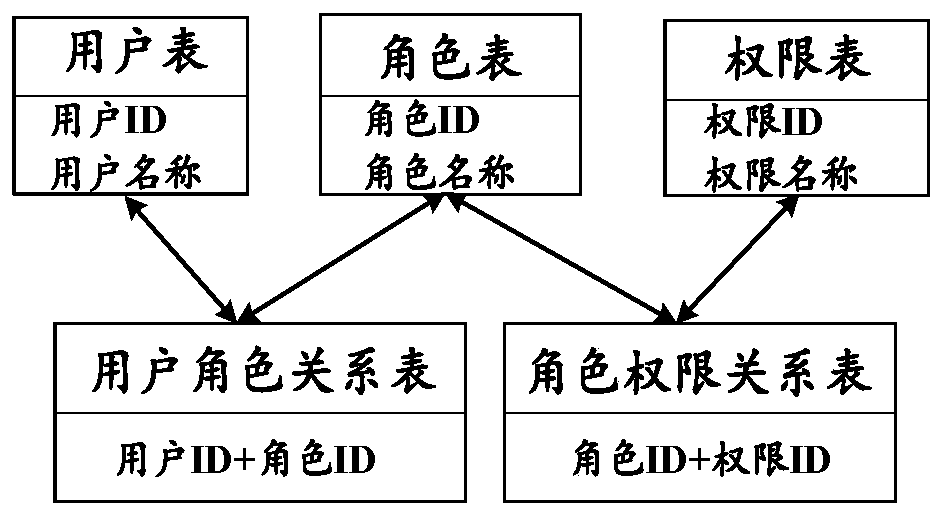
The invention provides a role access control system based on a block chain smart contract. According to RBAC rule setting, the role access control system based on the block chain smart contract is logically divided into a data layer, an access control layer and a presentation layer, and the role access control system based on the block chain smart contract is divided into a user module, a role module and an authority module according to function modules. The invention further provides a role access control method. Contract deployment, administrator initialization and role and authority configuration need to be completed before the access control system is used; and then, the user can perform login, a manager can do works such as audit and role distribution. The role access control method comprises the following steps: 1, deploying an intelligent contract of a role access control system based on a block chain intelligent contract in a block chain system; 2, configuring permission and roles; 3, the user registering an account; 4, auditing user registration; 5, the administrator allocating roles to the users; and 6, the user logging in and accesses the system by using the secret key.
Owner:BEIJING WUZI UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com