Method and system for controlling user access
An access control and access control strategy technology, applied in the field of network communication, can solve problems such as increased failure rate, implementation trouble, double login, etc., to achieve the effect of reducing pressure, simple configuration, and avoiding trouble
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
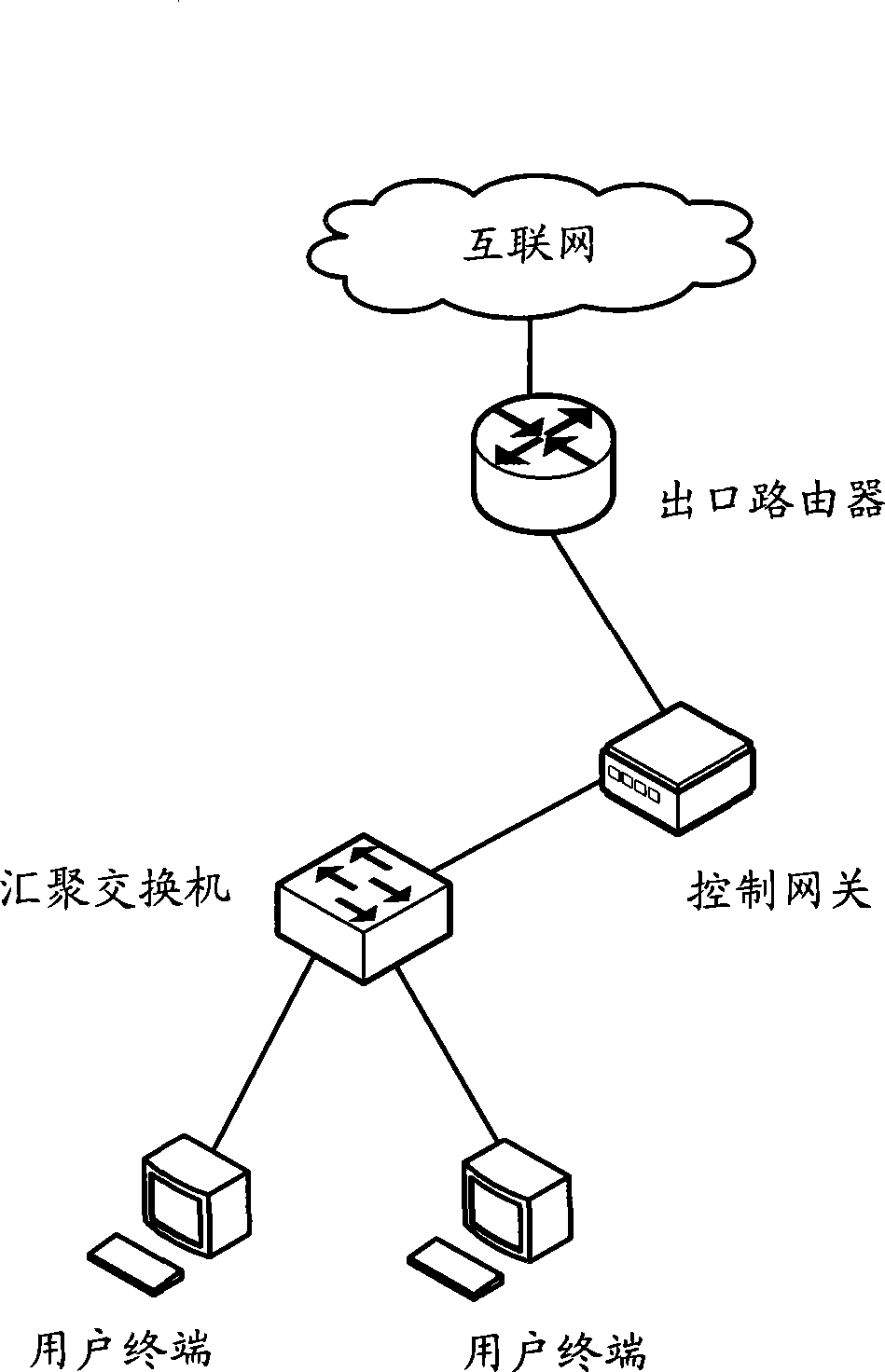
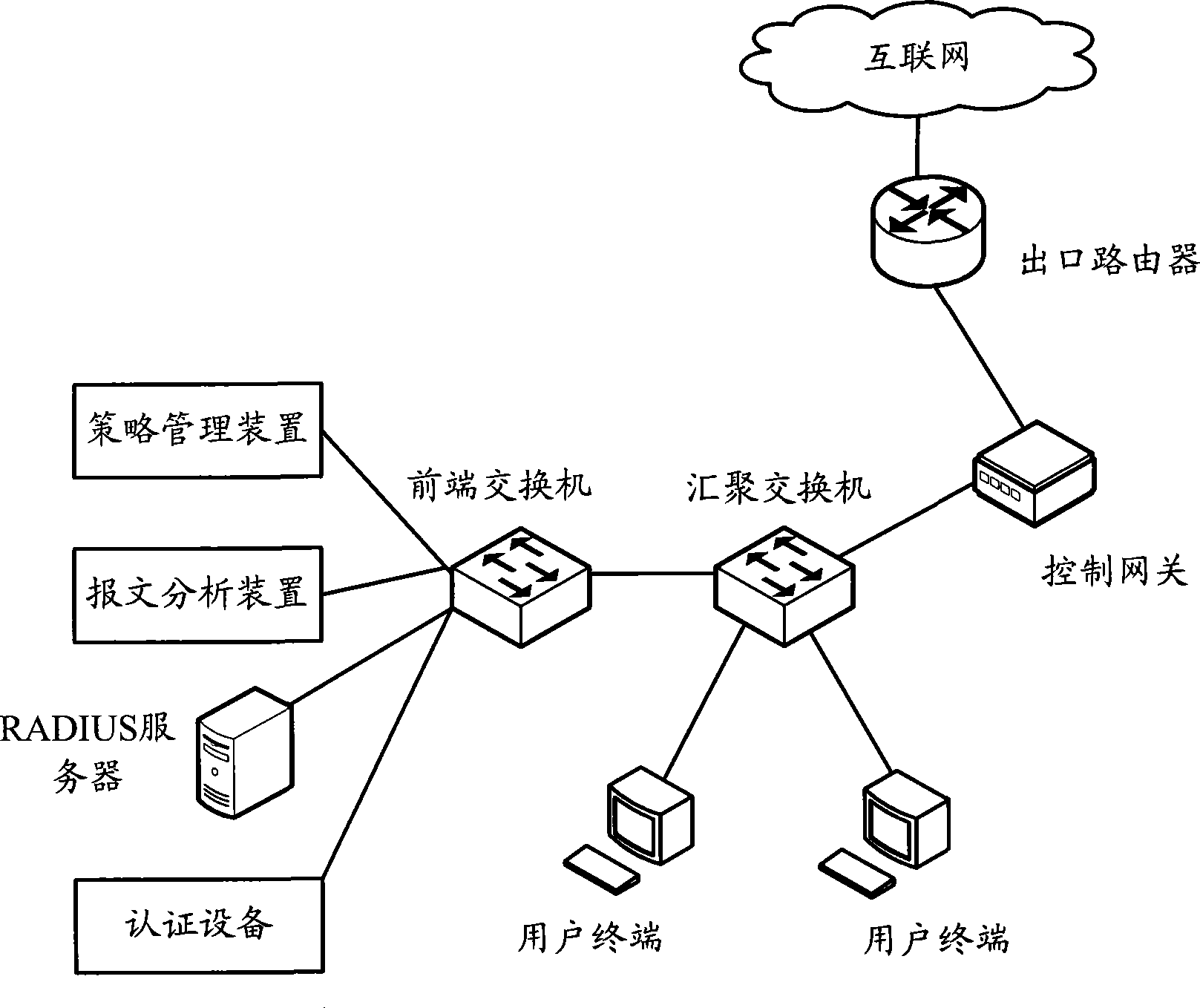
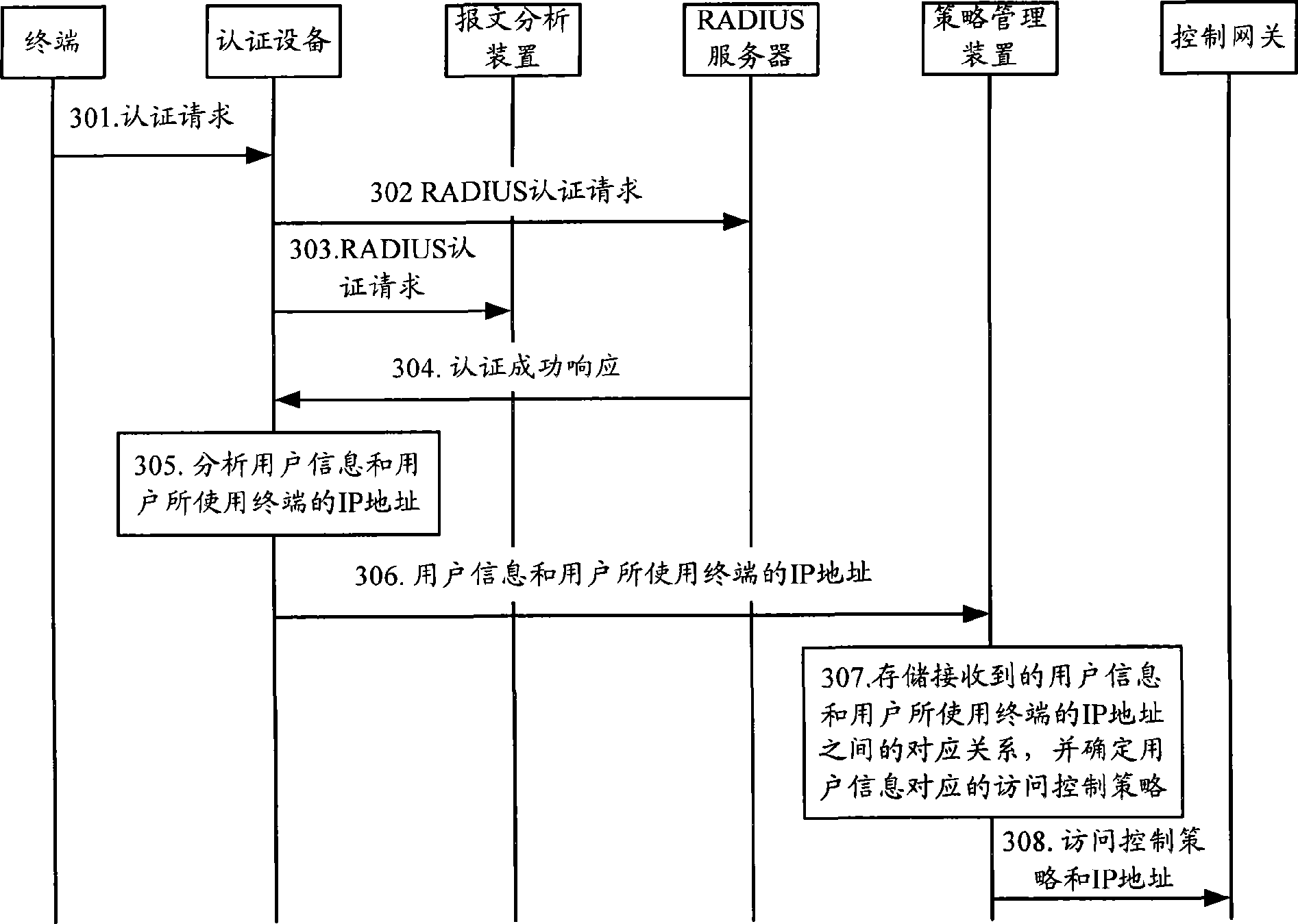
[0024] Embodiment one: for such as figure 2 In the networking structure of the Remote Authentication Dial In User Service (RADIUS) shown in FIG. Correspondence with access control policies. The implementation process of this method can be as follows image 3 shown, including the following steps:
[0025] Step 301: the user sends an authentication request to the authentication device through the terminal used.
[0026] The authentication request sent by the terminal in this step may be an 802.1X authentication request or a portal (Portal) authentication request, and the authentication request may include user information and IP address information of the terminal. For example, the user can enter user information such as user name, login ID, or user password through the Portal page pushed by the authentication device.
[0027] Alternatively, the authentication request only includes user information and the MAC address information of the terminal, and the authentication devi...
Embodiment 2
[0042] Embodiment two: for Figure 4 In the domain login authentication network structure shown, a packet analysis device and a policy management device are also set in the network. Wherein, the corresponding relationship between user information and access control policies is pre-configured in the policy management device. The implementation process of this method can be as follows Figure 5 shown, including the following steps:
[0043] Step 501: the user sends a domain login request including user information and terminal IP address information to the domain controller through the terminal used.
[0044] Step 502: After receiving the domain login request, the domain controller uses the user information in the domain login request to perform authentication, and the domain login request is redirected to the packet analysis device by the front-end switch.
[0045] A mirror port can be pre-configured on the front-end switch connected to the domain controller and the message ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com