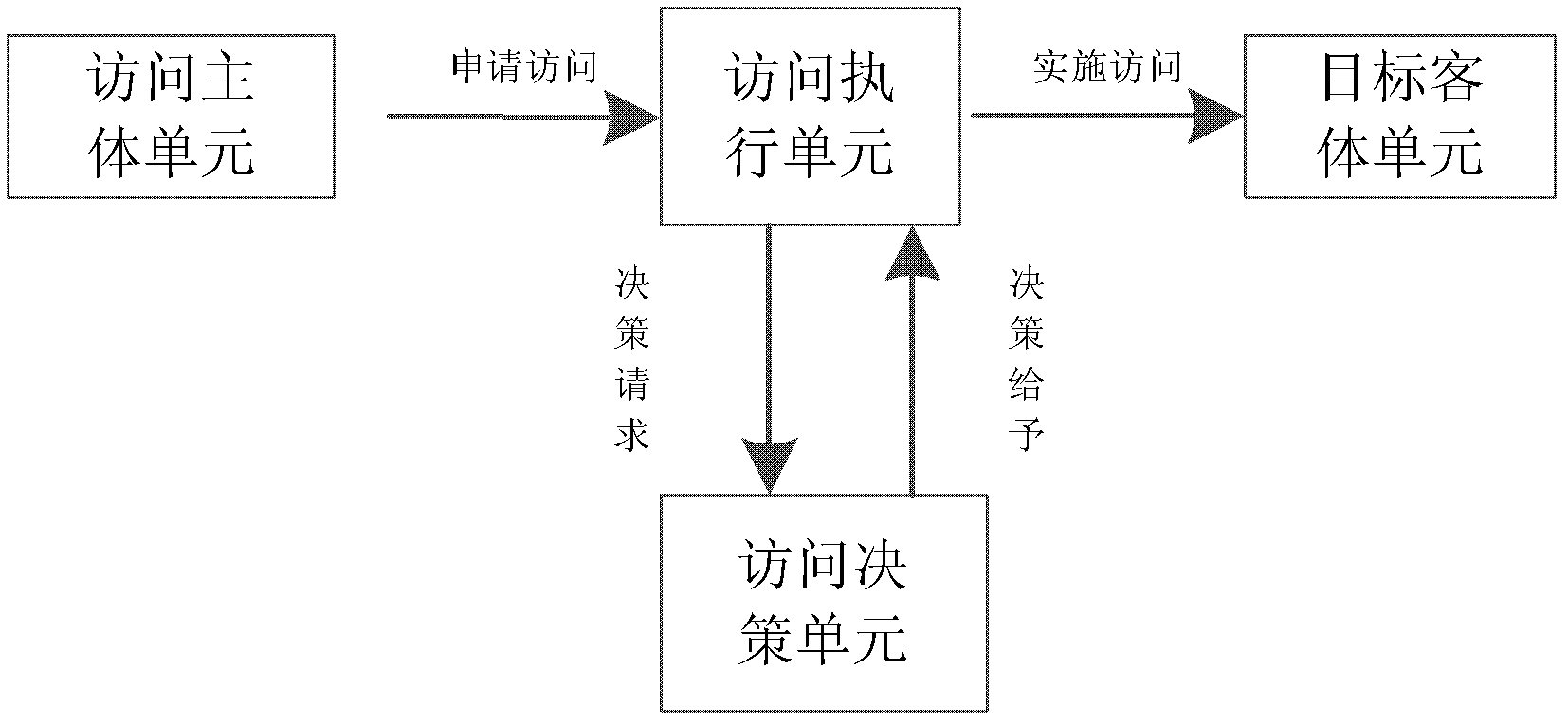
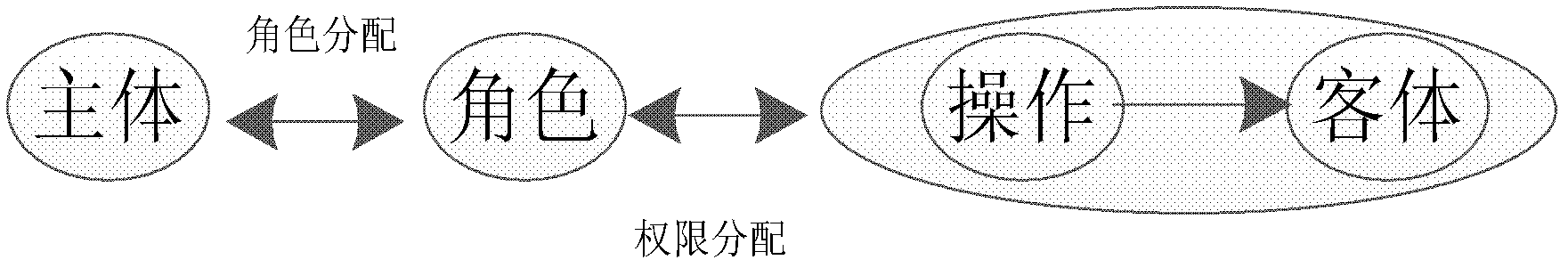
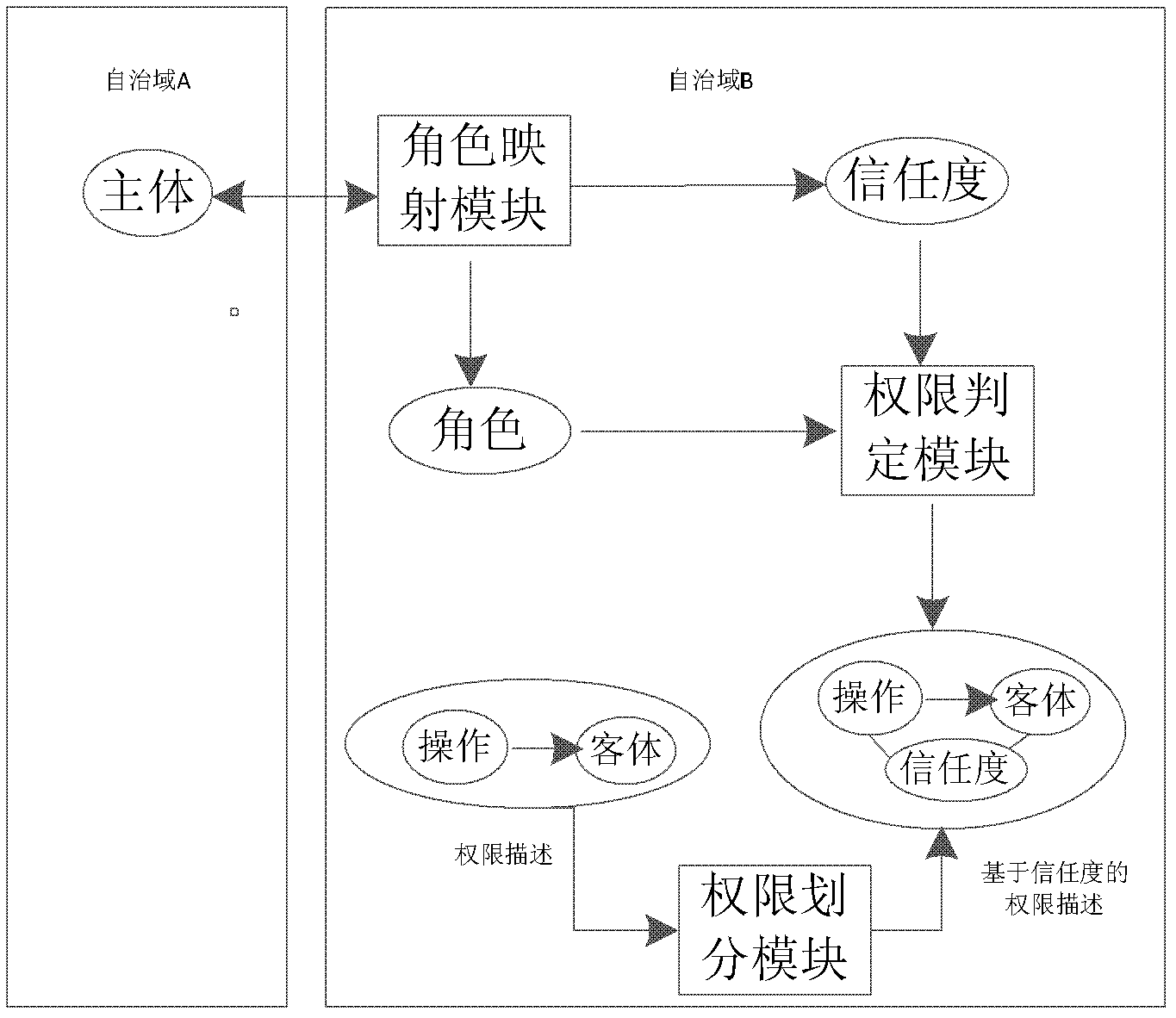
Trust-based access control method and system thereof
A technology of access control and trust, applied in transmission systems, electrical components, etc., can solve the problem that the RBAC model cannot be applied to a distributed collaborative development environment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0124] The present invention will be further described below in conjunction with specific embodiments and accompanying drawings.
[0125] There are two universities H and G, each with a set of course information system for the school, university H has three roles RoleSet H = {teacher, full-time student, part-time student}, university G has two roles RoleSet G = {teacher, student}, and:
[0126] In the role access control implementation scheme of school H:
[0127] ●Teachers have the authority to start courses, view student information, and score;
[0128] ●Full-time students have the authority to choose courses across majors, choose courses in this major, evaluate courses, and study online courses;
[0129] ●Part-time students have the right to choose courses, evaluate courses, and study online courses.
[0130] In the role access control implementation scheme of school G:
[0131] ●Teachers have the authority to start courses, view student information, and score;
[013...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com