Role access control-based information system data storage layer and building method
A technology of role access control and data storage layer, which is applied in digital data authentication, electronic digital data processing, special data processing applications, etc., and can solve problems such as leaks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
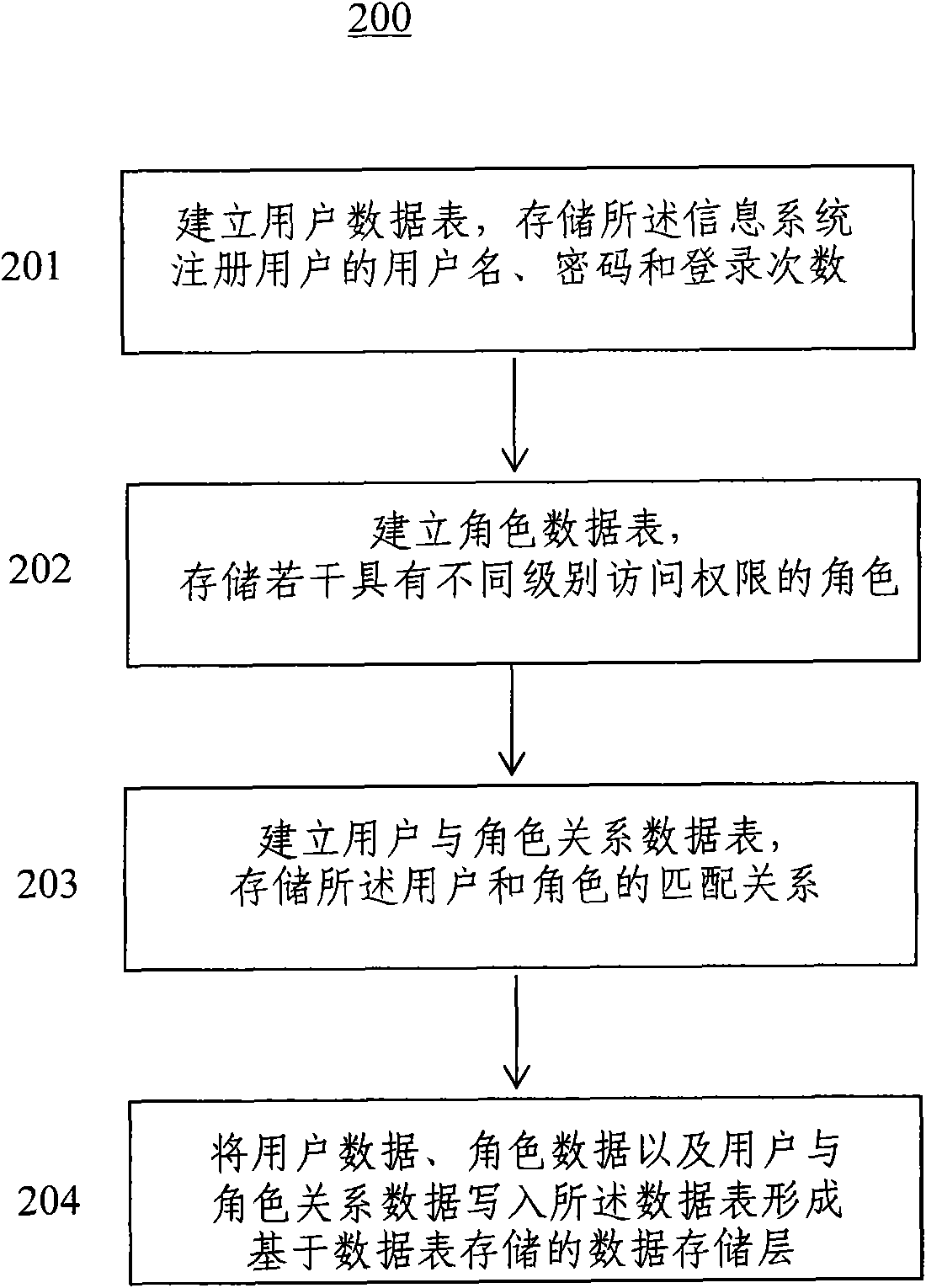
[0024] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments, and will be described by applying the present invention to a graduate management system.
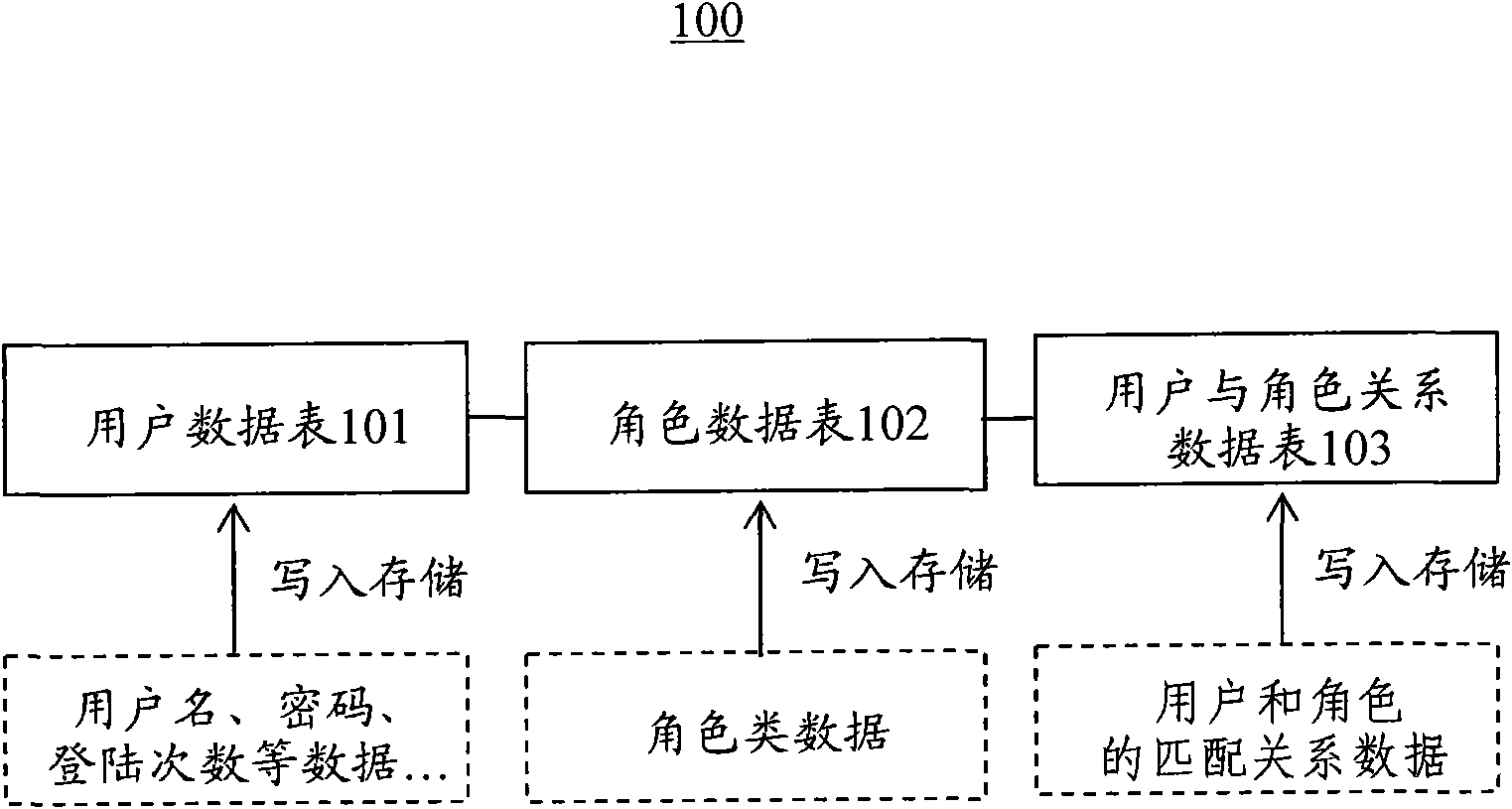
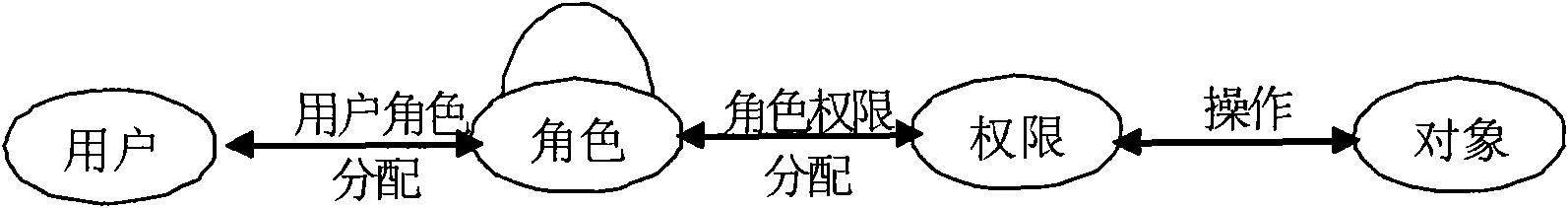
[0025] refer to figure 1 , figure 1 An information system data storage layer 100 based on role access control is shown, including a user data table 101, a role data table 102, and a user-role relationship data table 103, which will be introduced in sequence below:
[0026] The user data table 101 is used to store the user name, password, login times and student number or job number of the registered user of the information system, as shown in Table 1. The user data table 101 is used to implement user registration, user addition, and user deletion of the information system, and the number of user logins stored in the user data table 101 is incremented by one each time the user logs into the information system once.
[0027] Table 1 - User...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com