A method and device for secure access control based on user
A security access control and user technology, applied in the field of network information security, can solve problems such as inability to associate intranet users with people, poor usability, and inconvenient security management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
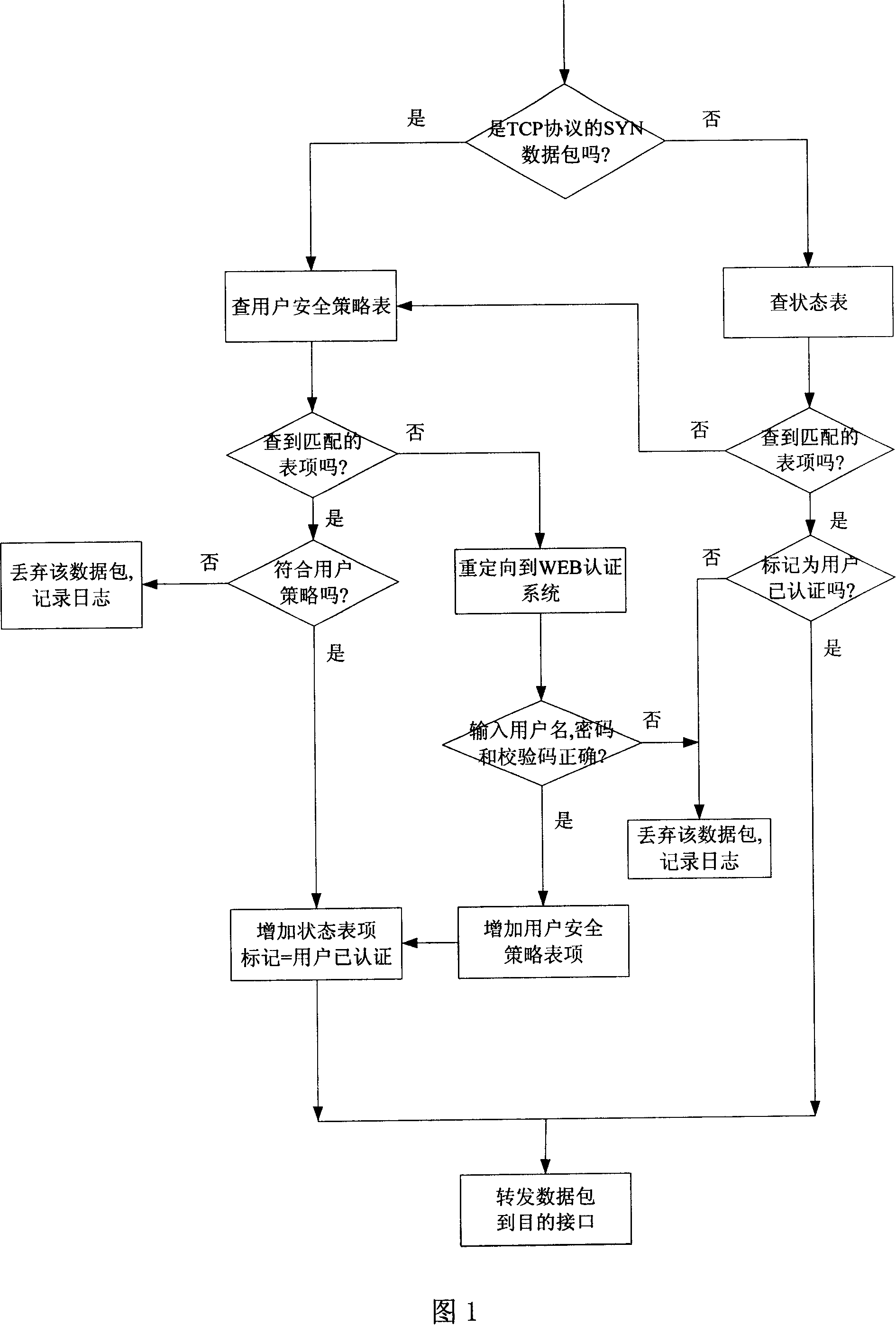
[0027] The technical scheme of the present invention will be described in further detail below in conjunction with accompanying drawing and embodiment:
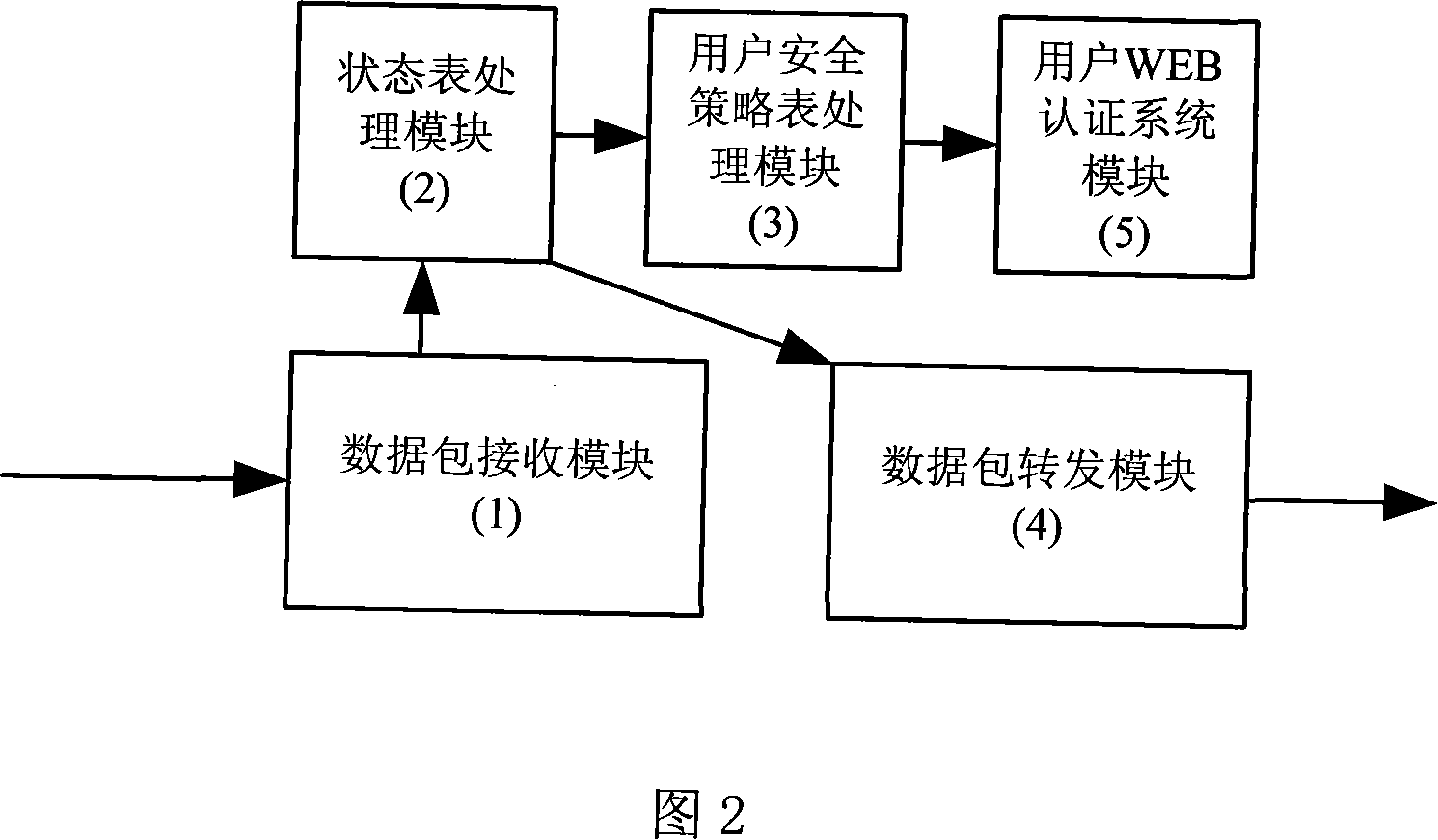
[0028] Referring to Figure 1, this method of user-based security access control is implemented through programming, and the software implemented by programming runs on an industrial control firewall platform with multiple network interfaces. This device is generally installed in series on the enterprise network The location connected to the public Internet, while protecting the outside from illegal intrusion, strictly controls the access rights of internal users' external access.
[0029] The steps of the method are divided into two processes of configuration and packet processing, wherein: the steps of the configuration process are:
[0030] [1] In the security rules, first add a user name and password for each intranet user, then directly configure the destination addresses and services that each user can access, and set th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com