Access control right management method and device
A technology of access control authority and management method, which is applied in the field of access control authority management method and device, and can solve the problems of large number of authority files, affecting system operation speed, unfavorable authority file management, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
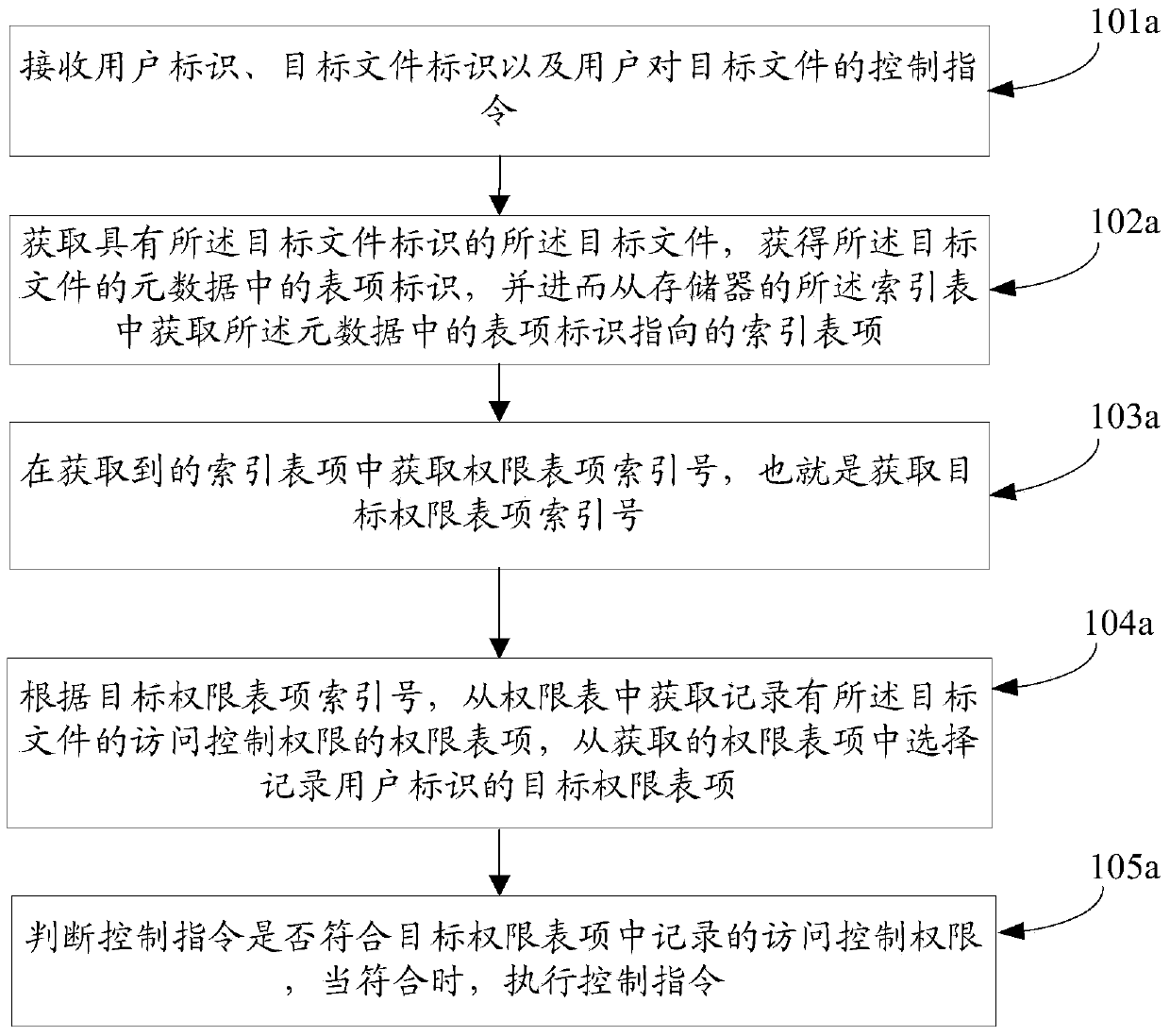
[0141] An embodiment of the present invention provides a method for access control authority management. To implement the method, an index table and an authority table are stored in the memory of the computer system. This memory can be the same memory as the memory storing files, or can be Not the same memory.
[0142] The index table is composed of multiple index entries, and each index entry records an entry identifier and at least one permission entry index number. Each permission entry index number maps to a permission entry in the permission table. Since the mapping relationship is one-to-one correspondence, the corresponding permission entry can be read through a permission entry index number.
[0143] Wherein, for each newly generated file in the computer, the above entry identifier is generated by default in the metadata of the file, and the entry identifier points to an index entry corresponding to the file. For example, there is an entry identifier a in the metadat...
Embodiment 2
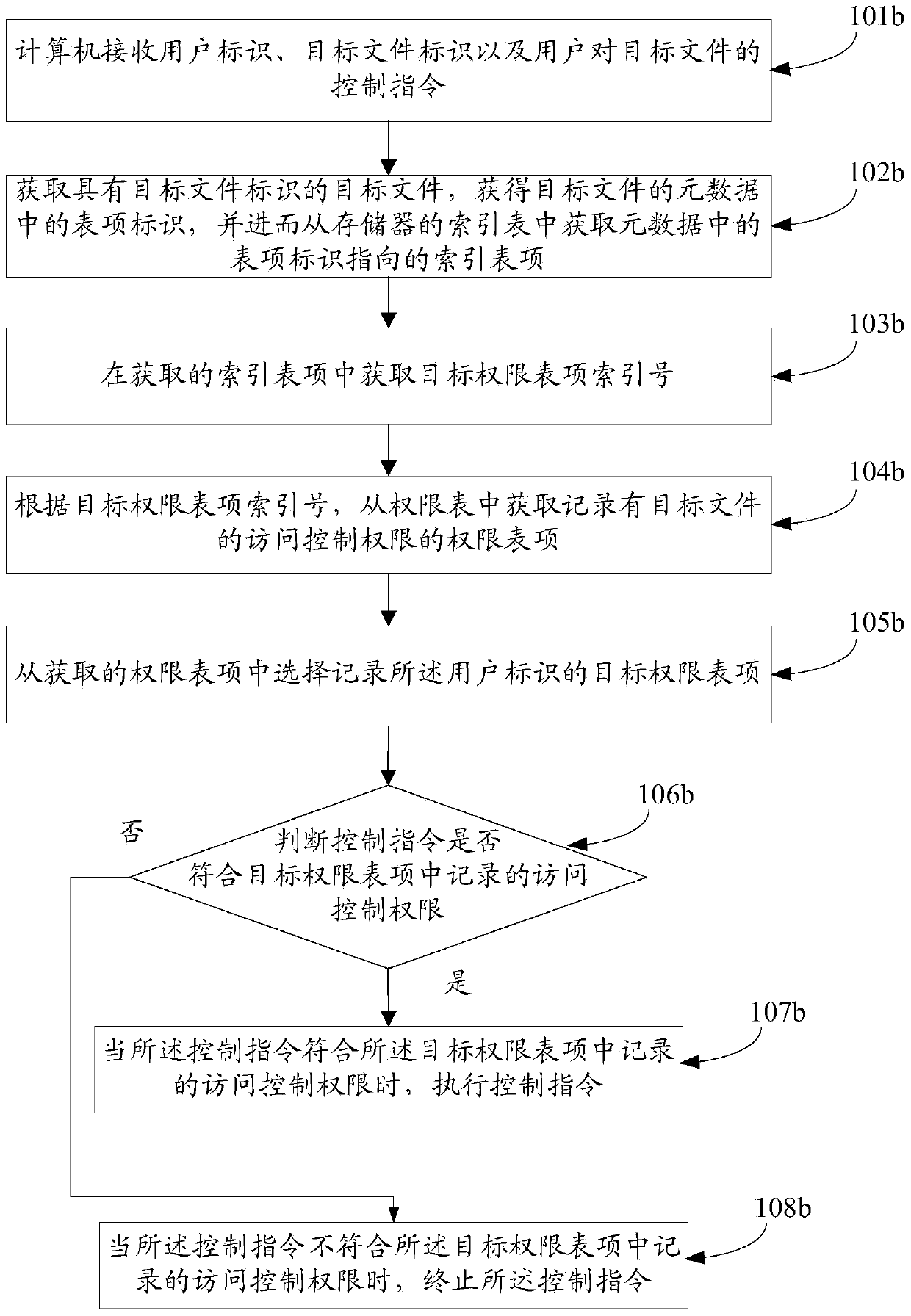
[0173] An embodiment of the present invention provides a method for managing access control rights, such as Figure 1b As shown, the method includes the following steps:
[0174] 101b. The computer receives the user identifier, the target file identifier, and the user's control instruction on the target file.
[0175] 102b. Obtain the target file with the target file identifier, obtain the entry identifier in the metadata of the target file, and then obtain the index entry pointed to by the entry identifier in the metadata from the index table of the memory.
[0176] 103b. Obtain the index number of the target permission entry from the obtained index entry.
[0177] 104b. According to the index number of the target permission entry, obtain the permission entry recording the access control permission of the target file from the permission table.
[0178] 105b. Select a target permission entry that records the user ID from the obtained permission entries.
[0179] 106b. Deter...
Embodiment 3
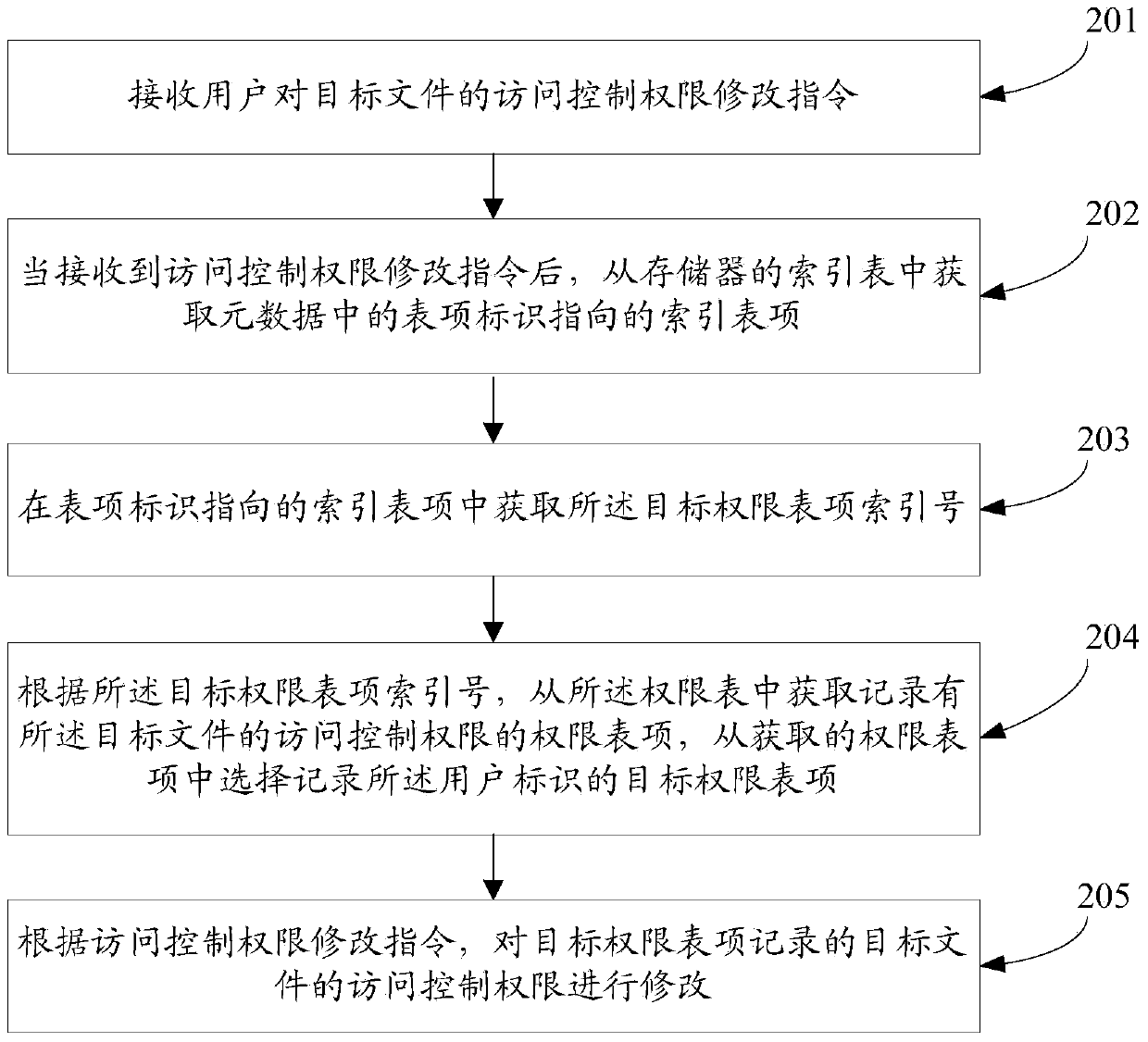
[0240] An embodiment of the present invention provides a device for managing access control rights, such as Figure 5 shown, including:
[0241] The receiving unit 51 is configured to receive a user identifier, a target file identifier, and a user's control instruction on the target file.
[0242] An index entry obtaining unit 52, configured to obtain the target file with the target file identifier, obtain the entry identifier in the metadata of the target file, and then obtain the metadata from the index table in the memory. The index entry pointed to by the entry identifier in the data.
[0243] A permission entry index number obtaining unit 53, configured to obtain a target permission entry index number from the index entry obtained by the index entry obtaining unit 52; the permission entry pointed to by the target permission entry index number is recorded with The access control permission of the target file.
[0244] A permission entry obtaining unit 54, configured to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com