Method, device and system for access control
An access control and access right technology, applied in the field of communications, can solve problems affecting other normal user experience, network security threats, etc., to prevent malicious attacks and improve service quality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
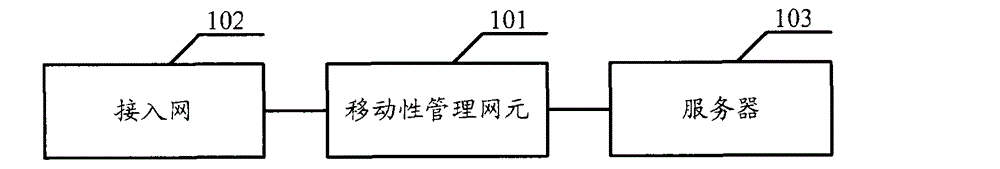
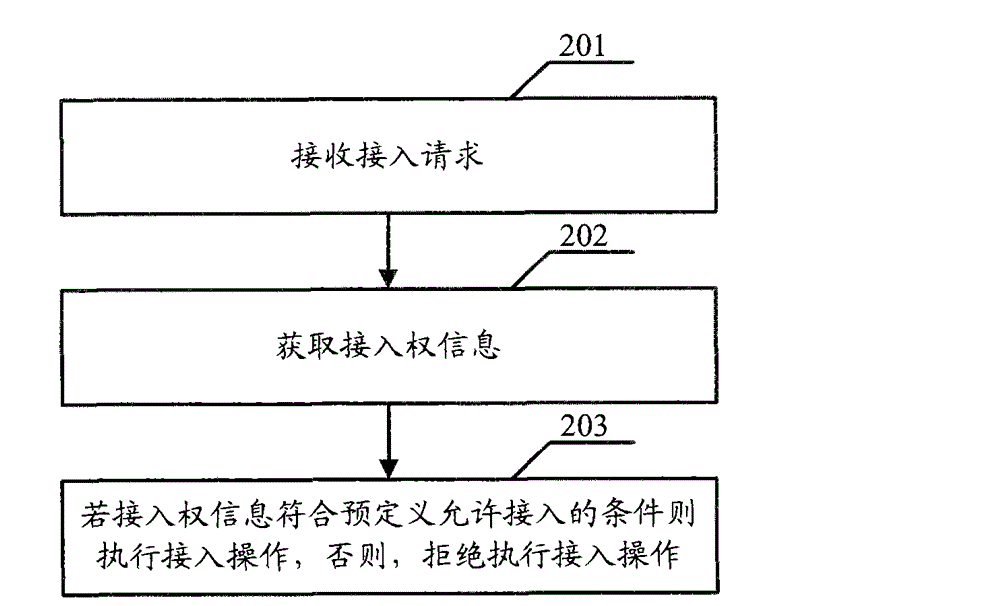
[0036] Embodiment 1. The embodiment of the present invention provides an access control method. The execution subject of the technical solution of this embodiment may be a mobility management network element, or may be an access network element. Can include the following steps:
[0037] Step 201: receiving an access request;
[0038] Step 202: Obtain the access right information of the user equipment of the above access request or the group or access point name to which the user equipment belongs;
[0039] The above access right information includes: the number of access times per unit time of the user equipment or the group where the user equipment is located, the total number of access times of the user equipment or the group where the user equipment is located (it can be the total number of access times on a certain network device , such as a mobility management network element or an access network element), at least one of the number of access times per unit time under a ...
Embodiment 2
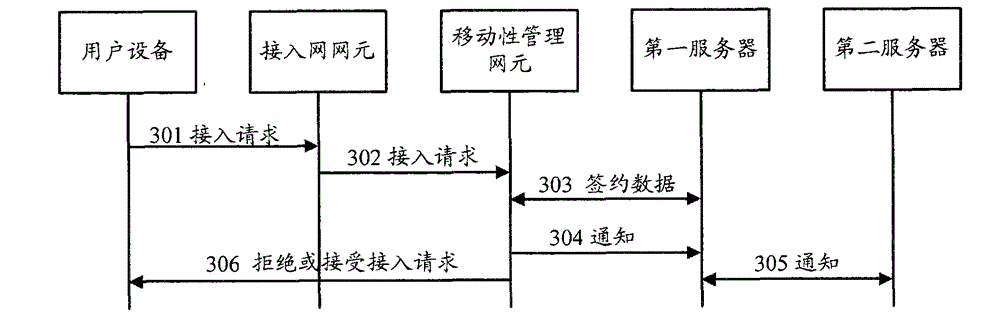
[0052] Embodiment 2. In this embodiment, the embodiment of the present invention will be further described by taking the statistics of the access right information of the user equipment by the mobility management network element as an example. In this embodiment, both the first server and the second server can be used as a server for storing user subscription data, and the second server can also be used as a server for troubleshooting illegal causes of illegal APNs or illegal users or illegal groups. Of course, the functions of the first server and the second server can also be integrated. If the functions are integrated, the messages between the first server and the second server belong to the message interaction within the device. In this embodiment, the first or second server stores the traffic model of the UE or the group. The traffic model in the present invention refers to the model in which the UE or the UE in the group initiates an access process to access the network, ...
Embodiment 3
[0064] Embodiment 3. In this embodiment, the embodiment of the present invention will be further described by taking the statistics of access information under a certain APN as an example. In this embodiment, the traffic model of a certain APN is stored in the HSS or the MTC Server, or the traffic model of a certain APN is statically configured by the mobility management network element, for example, the number of accesses under a certain APN is allowed per unit time, or The total number of times a device is allowed to access a certain APN. The mobility management network element counts the access situation under a certain APN, such as the number of accesses under a certain APN per unit time, or the total number of accesses to the APN on a certain mobility management network element Access conditions such as the number of times, the mobility management network element accepts or rejects the access request for a certain APN according to the traffic model of the APN; Figure 4 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com