Method, device and system for assigning permissions
A permission configuration and permission technology, applied in the field of network communication, can solve the problems of cumbersome operation of UPnP device reconfiguration, different access permission configuration information, etc., and achieve the effect of simplifying the reconfiguration process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
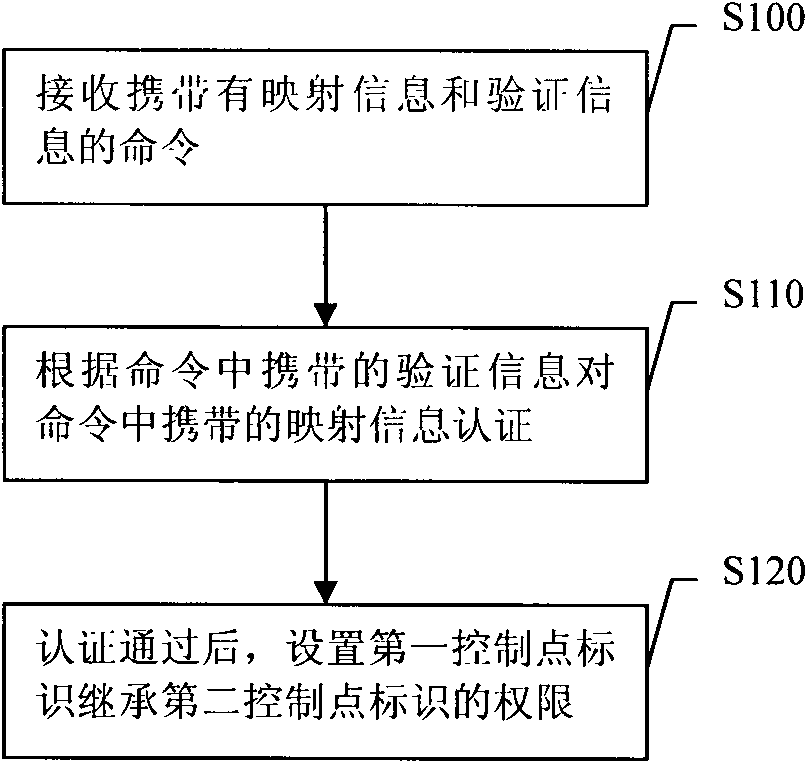
[0040] Embodiment 1, a rights configuration method. The flow of the method is attached figure 1 shown.
[0041] figure 1 , S100. Receive a command carrying mapping information and verification information.
[0042] The command carrying the mapping information and verification information in S100 may be sent from the control point.
[0043] The mapping information in S100 includes the first control point identifier and the second control point identifier of the same control point, that is, the first control point identifier and the second control point identifier are two different identifiers of the same control point, and Not two identities for different control points. A specific example of mapping information is: the first control point identifier may be a new identifier of a control point, and the new identifier of a control point may be called a new control point identifier; the second control point identifier may be an old identifier of the control point, and the The...
Embodiment 2
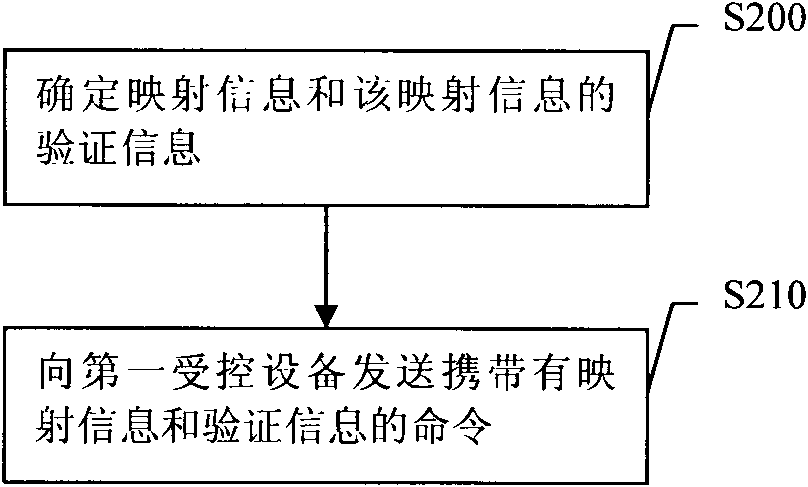
[0063] Embodiment 2, a rights configuration method. The flow of the method is attached figure 2 shown.
[0064] figure 2 , S200. Determine mapping information and verification information of the mapping information.
[0065] The mapping information in S200 includes the first control point identifier and the second control point identifier of the same control point, and the verification information includes signature information of the above mapping information.
[0066] In S200, the two self-signed certificates generated by a control point can be used as the first control point identifier and the second control point identifier, or the two self-signed certificates generated by a predetermined algorithm for a control point can be calculated separately The obtained values are used as the first control point identifier and the second control point identifier. This embodiment does not limit the specific implementation manner of determining the mapping information.
[0067...
Embodiment 3
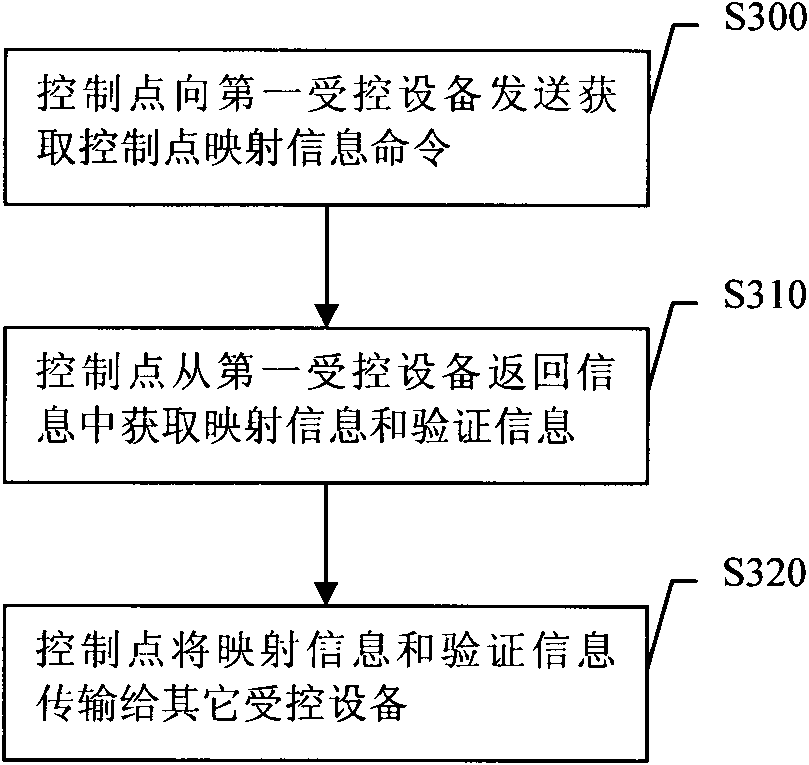
[0076] Embodiment 3, a rights configuration method. The following describes this embodiment by taking the execution subject as a control point as an example. The flow of the method is attached image 3 shown.
[0077] image 3 In S300, the control point sends a command to acquire control point mapping information to the first controlled device. The control point that invokes the command to acquire control point mapping information should have corresponding authority, for example, the control point has public authority for the first controlled device. The permission of the control point to call the command to obtain the mapping information of the control point can be set according to actual needs. In this embodiment, the specific authority that the control point that sends the command to obtain the mapping information of the control point should have is not limited.
[0078] The acquire control point mapping information command sent in S300 may acquire the mapping informat...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap