Security policy online detection system facing to terminal computers
A terminal computer and computer technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as high internal complexity, reduced network security defense capabilities, and lengthy management cycles, so as to reduce the requirements for professional technical knowledge and reduce unique Command input, the effect of improving the overall safety performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
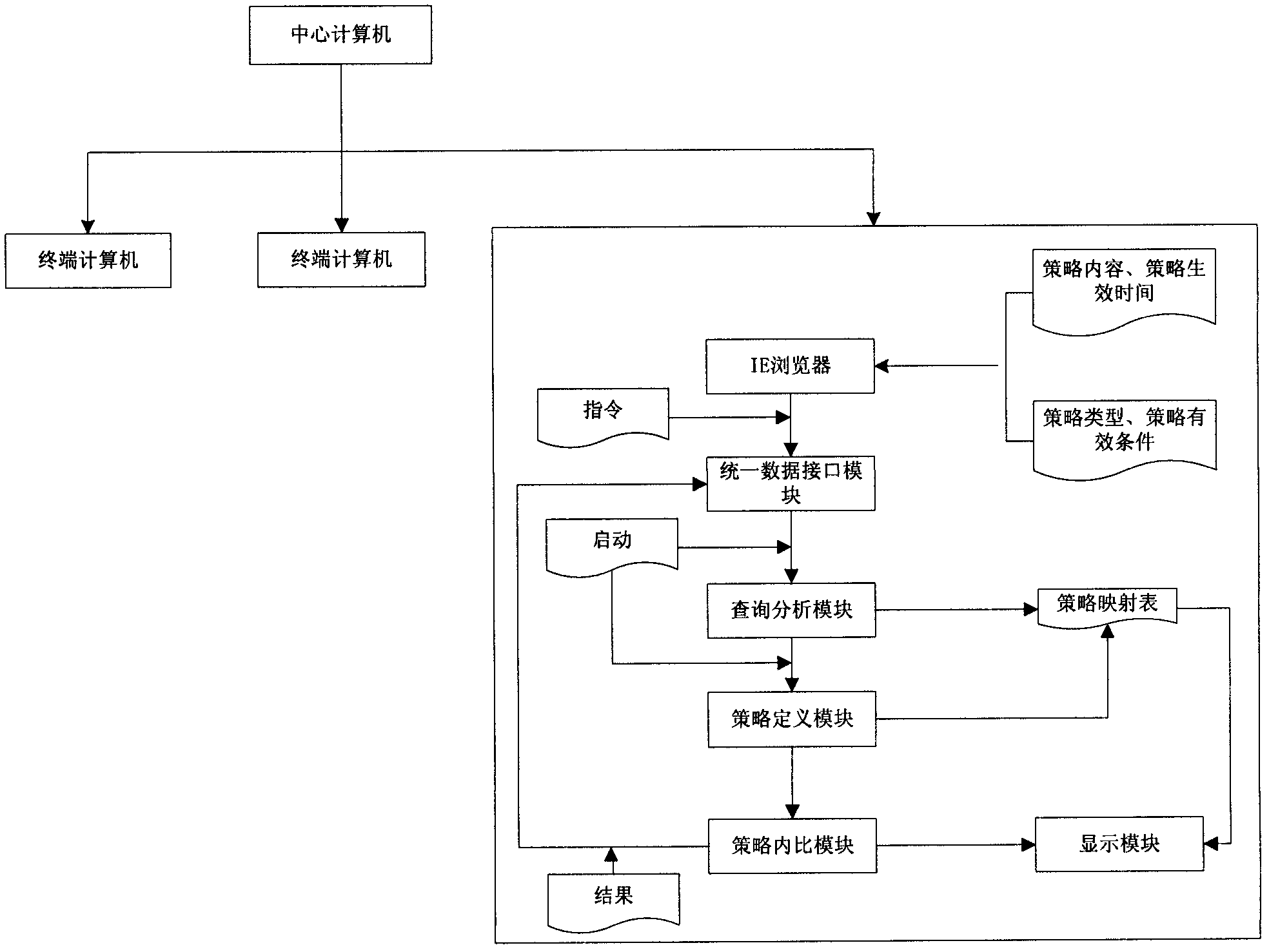
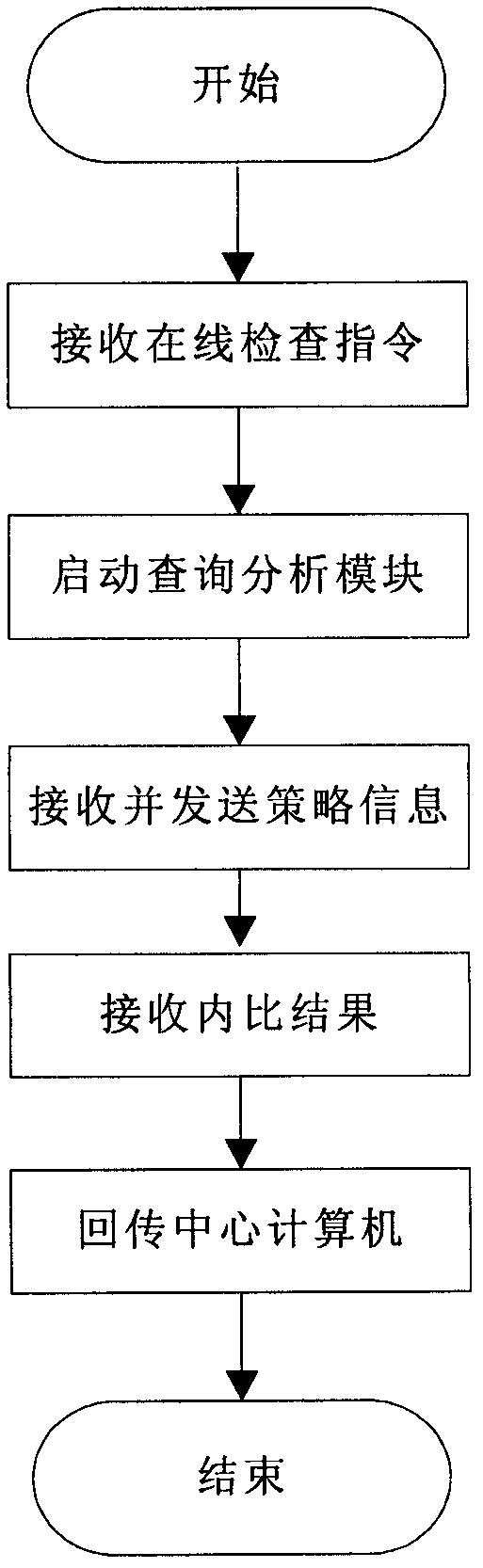
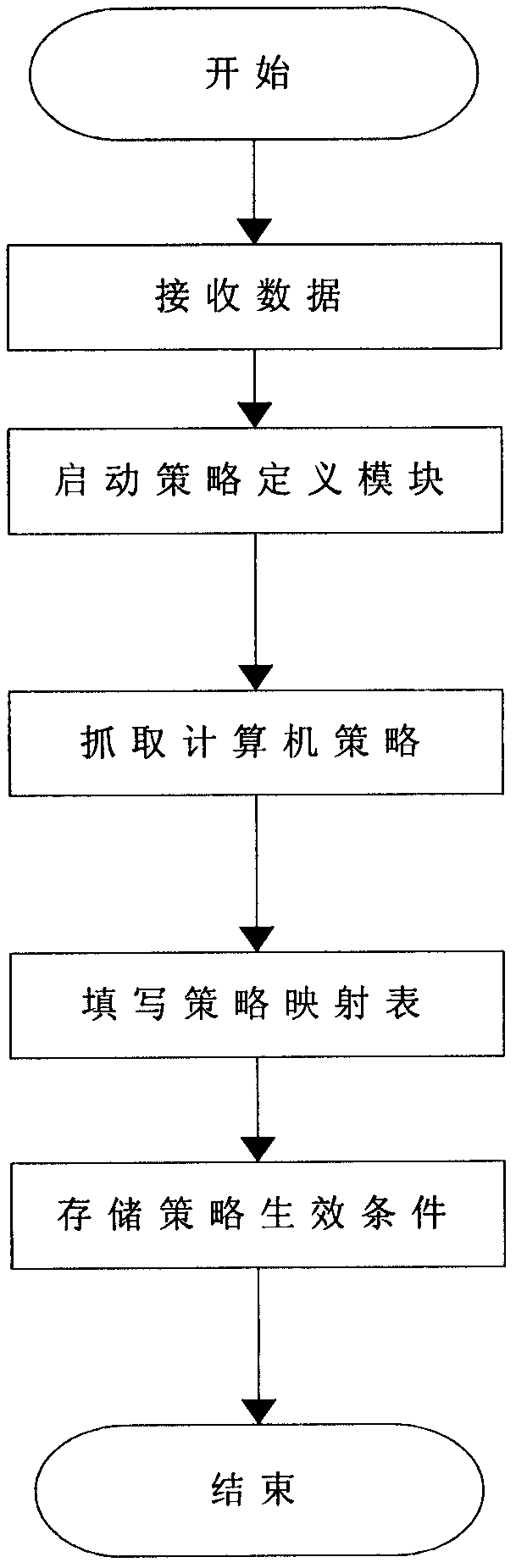
[0026] The implementation process of the system of the present invention will be described in detail below in conjunction with the accompanying drawings. This system conducts centralized inspection on all terminal computers online on a central computer, and all computers are connected through a network; the system includes an online inspection tool and a packaging module, and the packaging module packs the online inspection tool into a CAB form and Stored on the central computer, the central computer embeds the CAB into the IE browser (can adopt com technology to realize embedding), and the terminal computer downloads the CAB from the central computer through the IE browser and automatically installs it; the online inspection tool includes a policy definition module, Unified data interface module, query analysis module, strategy internal comparison module and display module;
[0027] The system of the present invention can realize two situations of online centralized inspectio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com