Network security analytical method for solving K maximum probability attack graph
A technology of network security analysis and maximum probability, which is applied in the field of network security analysis for solving the K maximum probability attack graph. The problem of monotonous non-increasing multiplication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
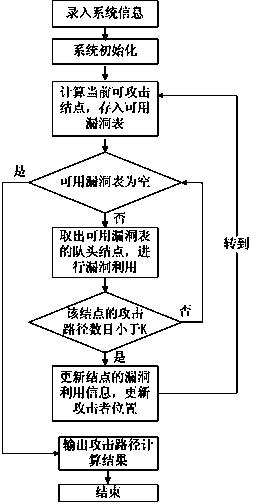
[0040] In order to make the technical means, creative features and objectives of the present invention easy to understand, the present invention will be further elaborated below in conjunction with specific examples
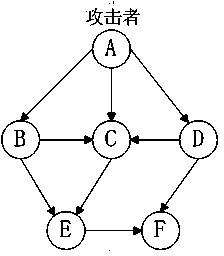
[0041] The network topology diagram of the present invention is as figure 2 As shown, node A represents the attacker, node B, node C, node D, node E and node F represent nodes in a given computer network system, and A can access node B, node C Like node D, the connection lines between node B, node C, node D, node E and node F represent the connection relationship between nodes.
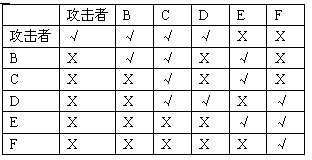
[0042] The access relationship between each node in the present invention is as follows: image 3 As shown, starting from the second line, each line represents the set of nodes that a node can access, "√" means that it can be directly accessed, and "X" means that it cannot be directly accessed. The attacker itself, node B, node C and node D, but cannot access node E and node F. The a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com