Method for realizing protection switching based on TRILL (transparent interconnection of lots of link) network, TOR (top of rack) switchboard and system
A technology for network implementation and protection switching, which is applied in the field of communication technology and can solve problems such as delay and packet loss sensitivity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0037] An embodiment of the present invention provides a method for implementing protection switching based on a TRILL network, such as figure 1 shown, including:
[0038] 101. TOR switch protection group information.
[0039] Wherein, the protection group information may include information of a first link connected between the TOR switch and the first COR switch and information of a second link connected between the TOR switch and the second COR switch. The acquisition of protection group information may be storing the protection group information in the TOR switch through static configuration, and the TOR switch obtains the pre-stored protection group information, or it may be that the TOR switch obtains the protection group information from the link generated by the TRILL protocol. Obtain two link information from a link state database (Link State Data Base, hereinafter referred to as LSDB) as protection group information, and the two links are links between the TOR switc...
Embodiment 2
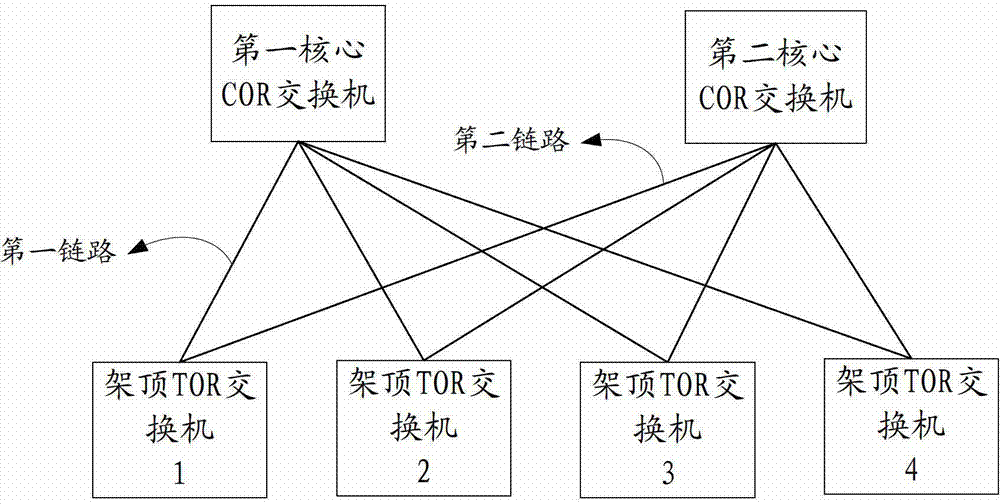
[0052] Embodiments of the present invention provide a method for implementing protection switching based on a TRILL network, which is applied to a TRILL network, such as figure 2 As shown, the TRILL network includes multiple TOR switches and multiple COR switches, wherein each TOR switch is physically connected to the COR switch. The TRILL protocol is adopted in the TRILL network, and the TRILL protocol includes the protocol specification of the data plane and the protocol specification of the control plane. In the protocol specification of the control plane, TRILL introduces IS-IS as an addressing protocol, which runs between TOR switches and COR switches in all TRILL networks. IS-IS is a routing protocol based on the link state. In the TRILL network, each TOR switch will generate a link state protocol data unit (Link State Protocol Data Unit, hereinafter referred to as LSPDUDU), this LSPDU contains the generated LSPDU All link information of the TOR switch. Each TOR switc...
Embodiment 3
[0081] An embodiment of the present invention provides a top-of-rack switch TOR switch, such as Figure 5 As shown, it includes: an acquiring unit 31 , a first establishing unit 32 , and a first switching unit 33 .
[0082] The acquiring unit 31 is configured to acquire protection group information, where the protection group information includes the first link information connected between the TOR switch and the first core COR switch and the second link information connected between the TOR switch and the second COR switch. link information, and transmit the protection group information to the first establishment unit 32, and its specific implementation method is the same as image 3 The above step 201 is the same and will not be repeated here.
[0083]Wherein, the first link information includes Nickname of the first COR switch, and the second link information includes Nickname of the second COR switch. If the TOR switch and the first COR switch are non-directly connected ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com