Method for defensing zero power consumption attack on code device
A zero-value power consumption attack and device technology, applied in the direction of encryption device with shift register/memory, etc., can solve the problems of reducing area and computational complexity, the effect is not obvious, and the computational complexity is large, and achieves good resistance. The effect of zero-value power attack performance, area overhead, and circuit speed reasonable
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
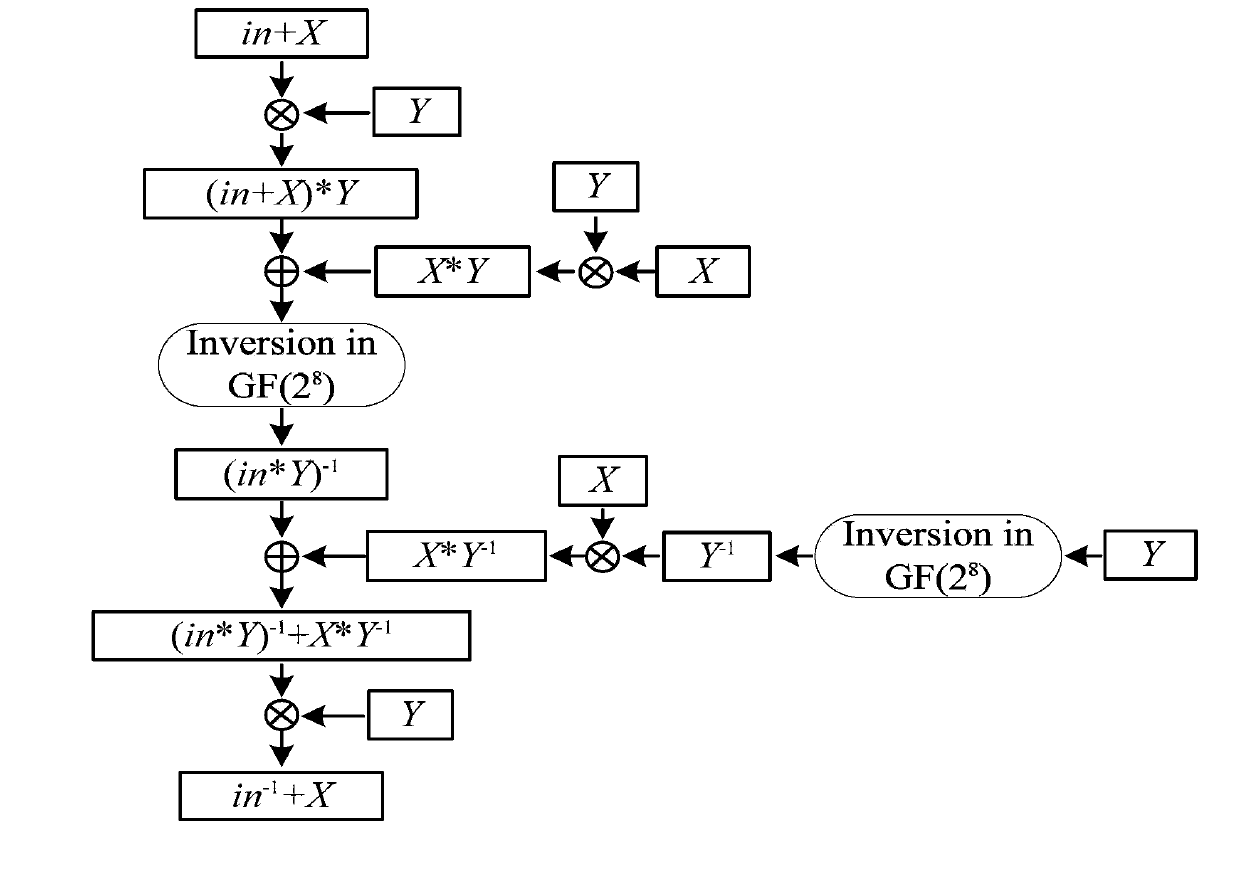
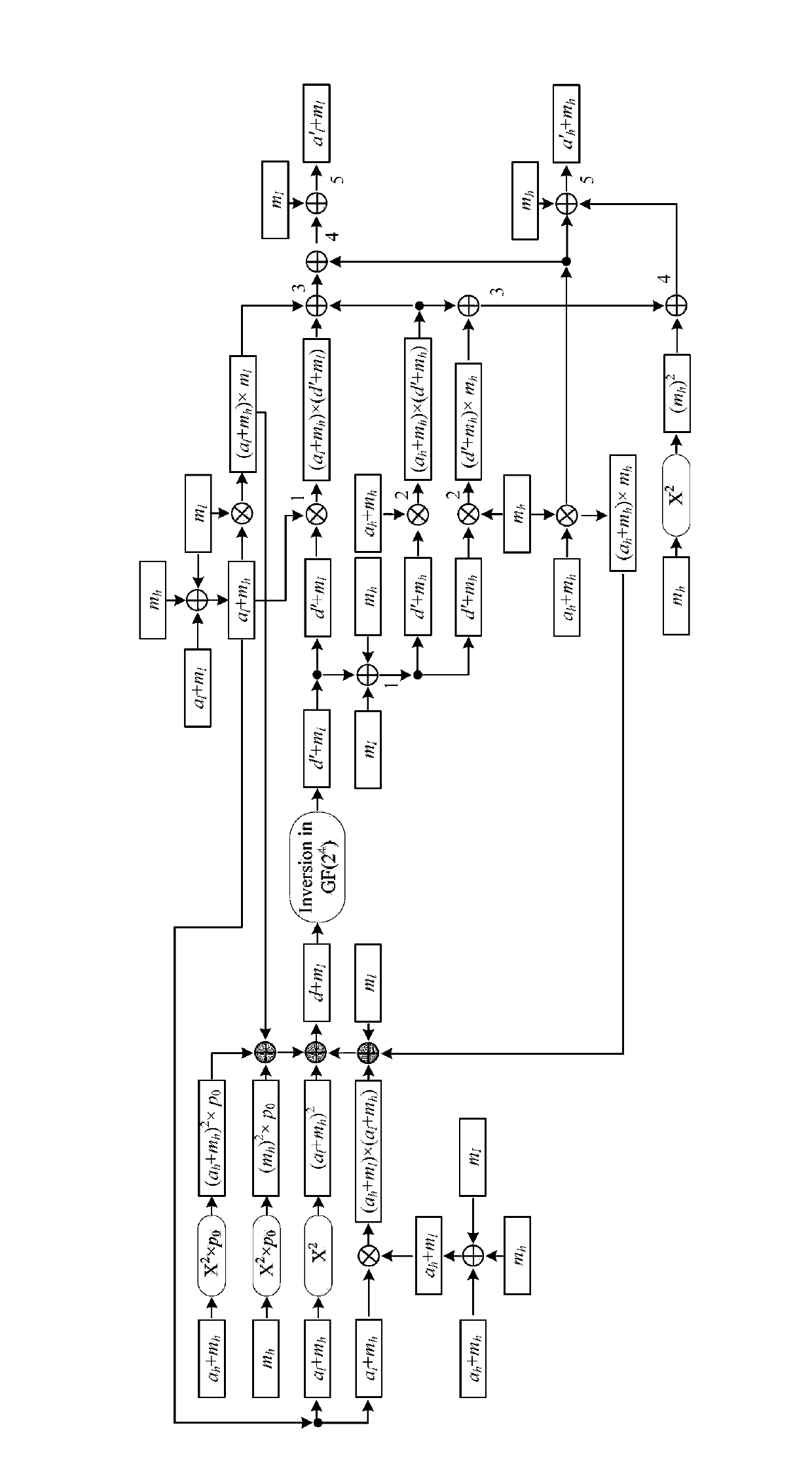
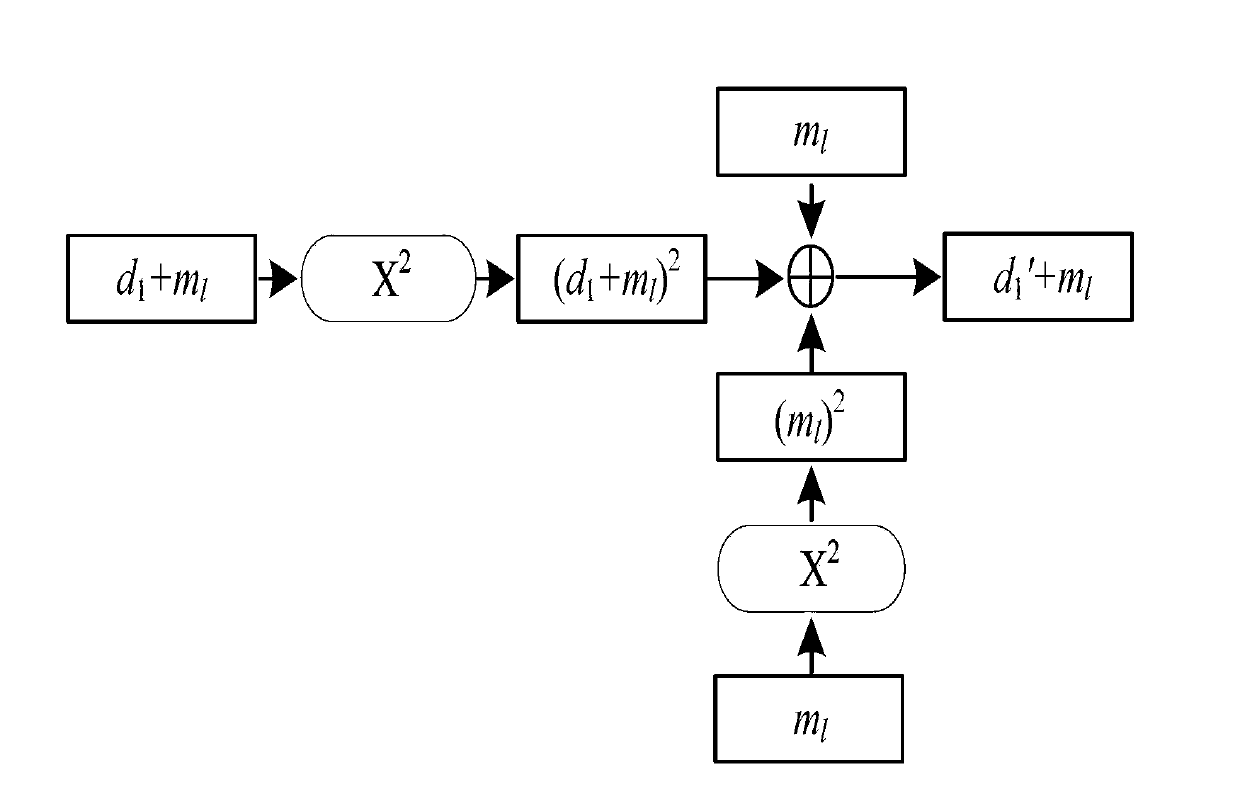
[0058] A method for defending against zero-value power consumption attacks on a cryptographic device, characterized in that GF(2 8 ) The inverse operation on the finite field uses GF(2 8 ) field additive masking inversion operation replacement, the specific process is as follows:
[0059] First in GF(2 8 ) on the finite field to perform the inverse operation, and use the superscript -1 to represent the inverse operation, specifically:
[0060] GF(2 8 ) signal data y on the domain is defined as {y 7 ,y 6 ,y 5 ,y 4 ,y 3 ,y 2 ,y 1 ,y 0}, where y i (0≤i≤7) is converted from decimal y to 8-bit binary coefficient corresponding to the i-th bit;
[0061] GF(2 4 ) signal data a on the domain is defined as {a 3 ,a 2 ,a 1 ,a 0}, where a i (0≤i≤3) is the coefficient corresponding to the i-th bit when the decimal a is converted into a 4-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com