Method and device for sending contact information
A technology for contacting information and equipment, applied in the field of communication, which can solve problems such as time-consuming and complex
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
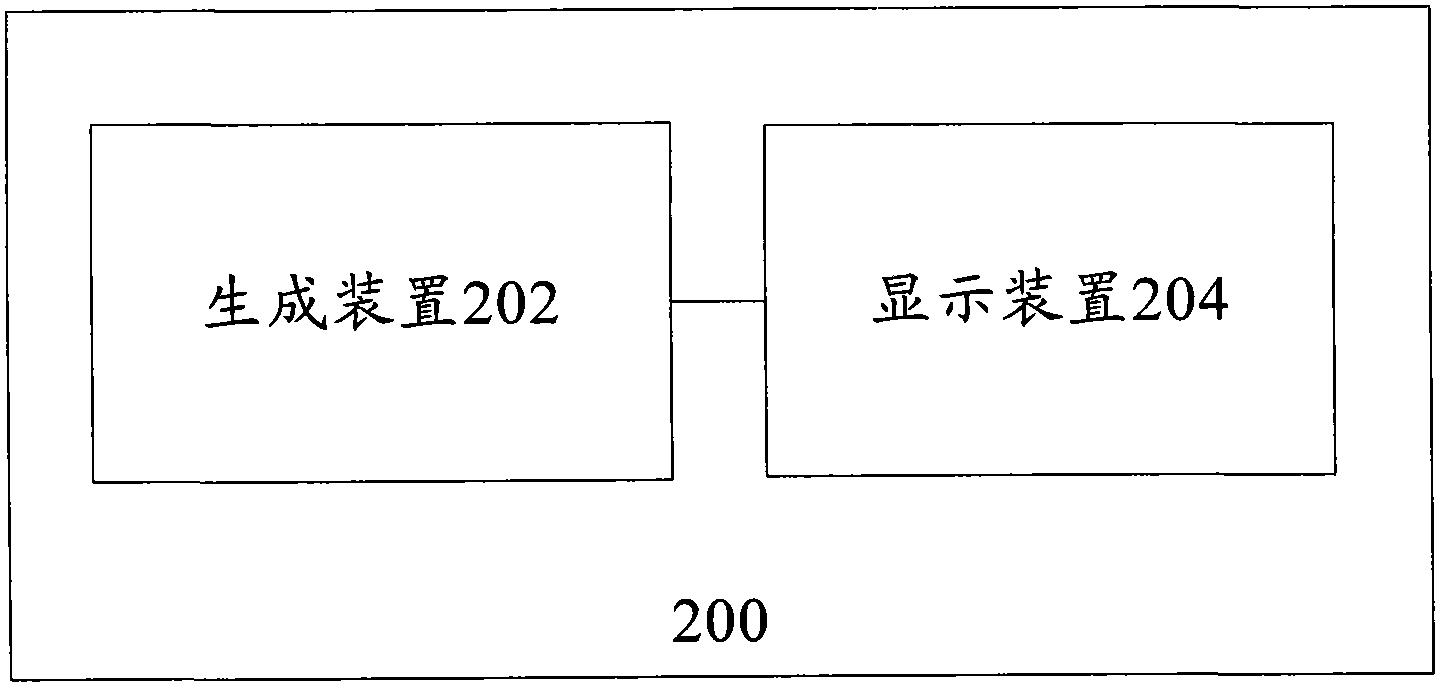
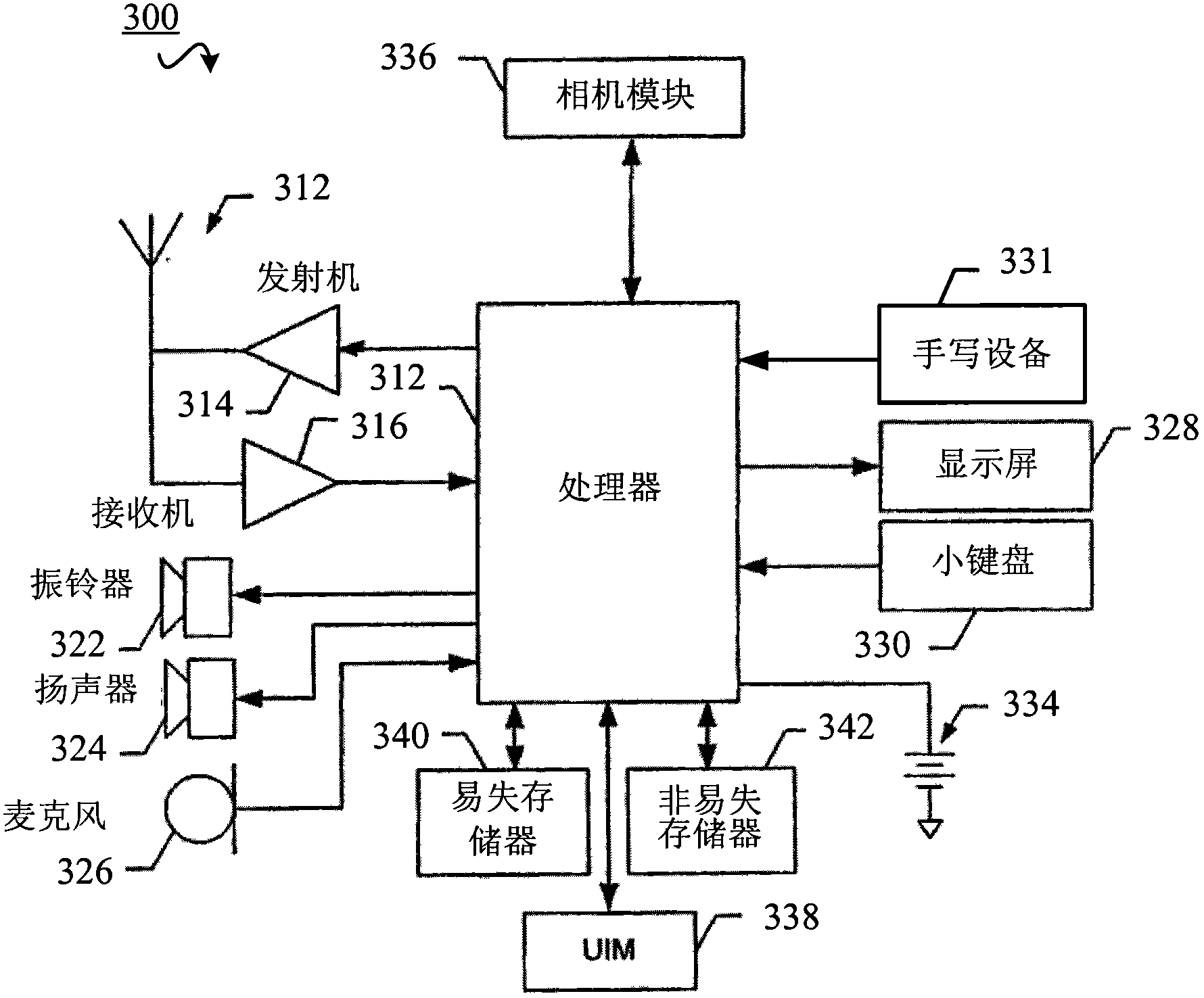
Image
Examples
Embodiment Construction
[0010] The principle and spirit of the present invention will be described below with reference to several exemplary embodiments. It should be understood that these embodiments are given only to enable those skilled in the art to better understand and implement the present invention, but not to limit the scope of the present invention in any way.
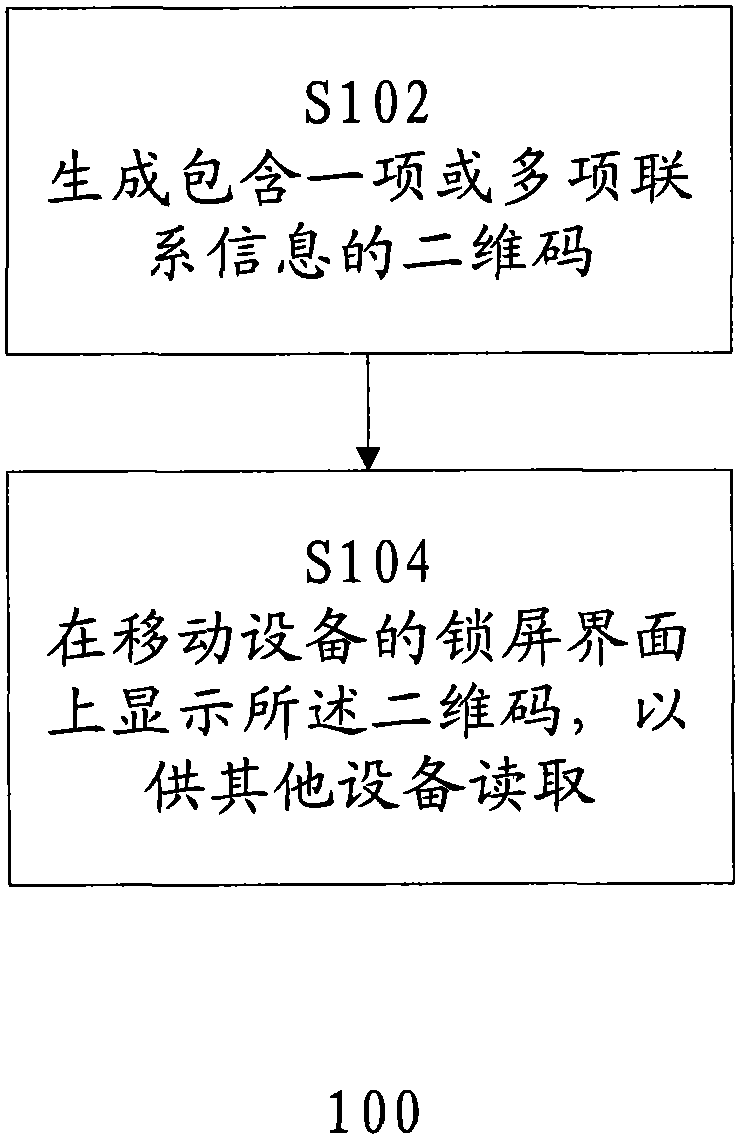
[0011] Refer below figure 1 , which shows a flowchart of a method 100 for sending contact information according to an embodiment of the present invention.
[0012] In step S102, a two-dimensional code containing one or more pieces of contact information is generated.
[0013] A two-dimensional code generally refers to a two-dimensional pattern that uses a black and white (or two other colors) pattern to represent binary data and is scanned by a device to obtain the information contained therein. Using QR codes can conveniently and reliably transmit various types of information.
[0014] In one embodiment, the contact information ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com