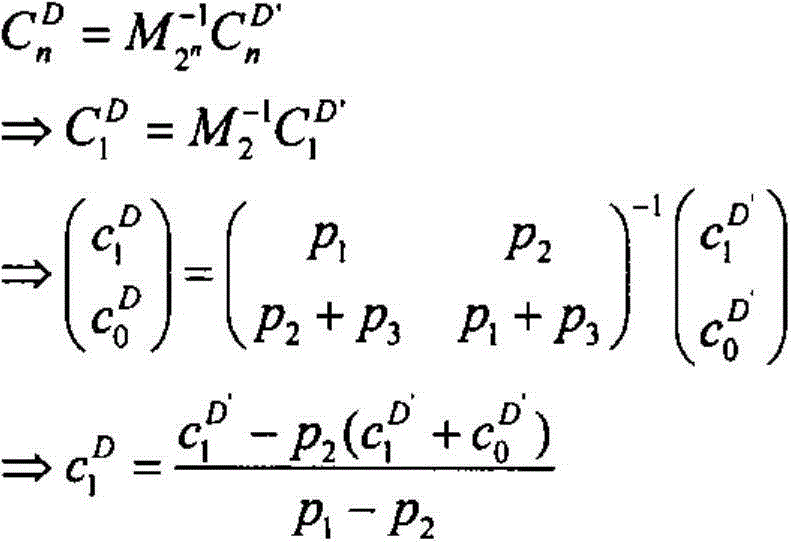Privacy protection associated rule data digging method based on multi-parameter interference
A privacy protection and data mining technology, applied in electrical digital data processing, special data processing applications, instruments, etc., can solve the problems of leakage of privacy, low efficiency of running time, and low degree of privacy protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment
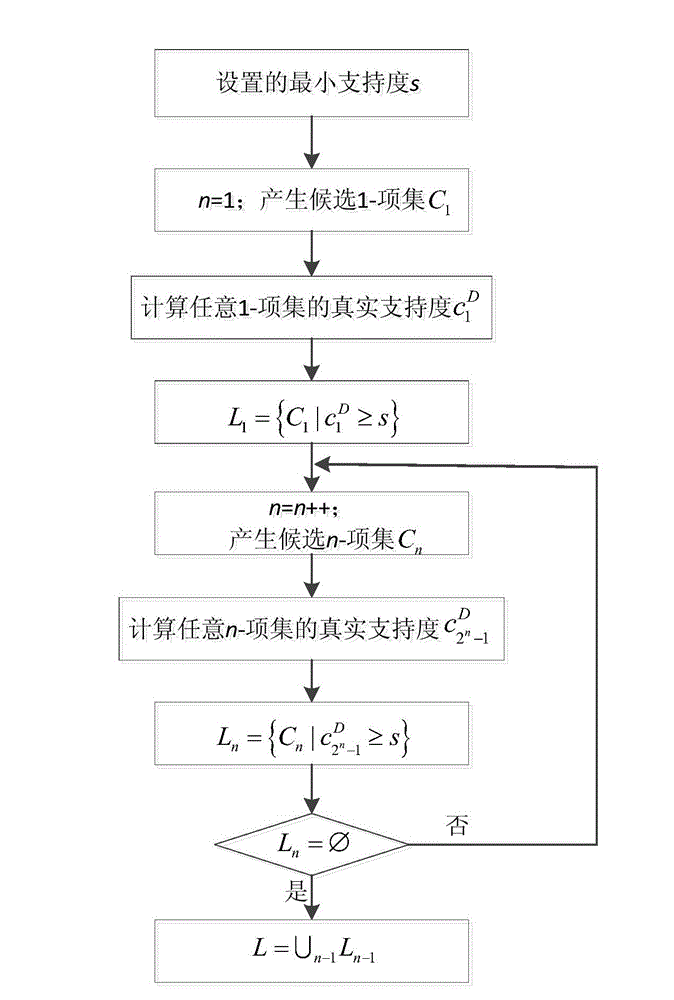
[0079] As shown in Table 1, the original dataset consists of 3 items and 10 data records, and the minimum support threshold is set to 2.
[0080] Table 1 Raw data set
[0081] ID
A
B
C
1
1
1
0
2
0
1
0
3
0
1
1
4
1
1
0
5
1
0
1
6
0
1
1
7
1
0
1
8
1
1
1
9
1
1
1
10
1
0
1
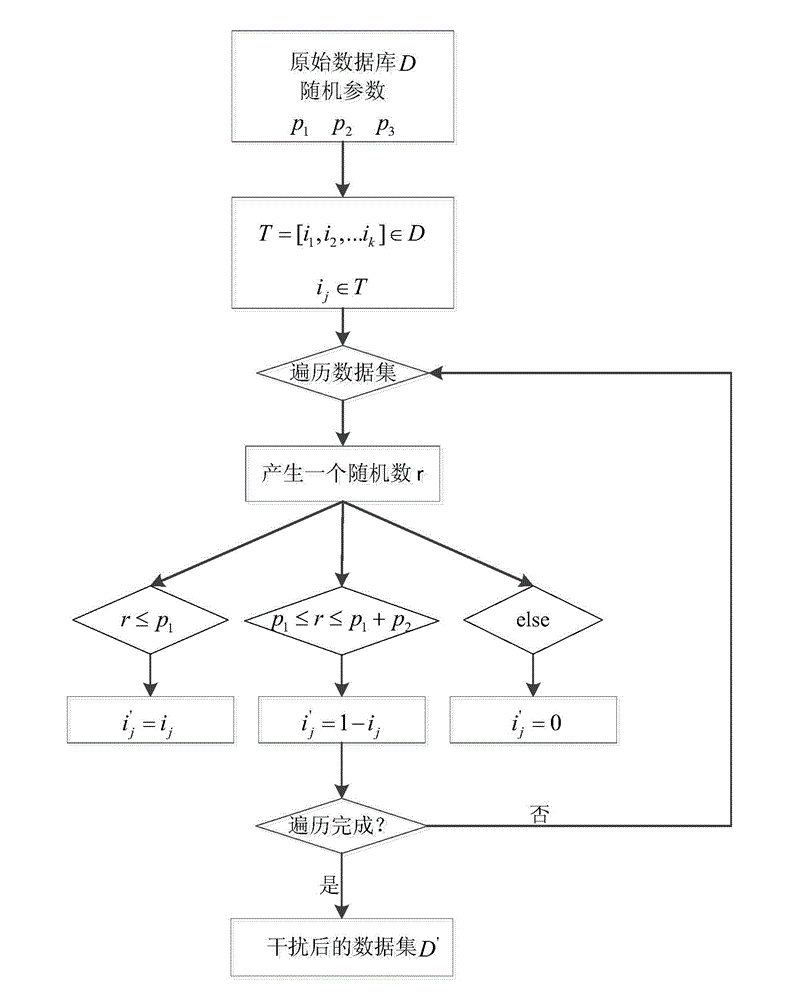
[0082] The specific execution steps are as follows:
[0083] (1) Set the three interference parameters as p 1 =0.4,p 2 =0.3,p 3 =0.3, for any item t∈{0, 1} in the original dataset, let f 1 =t,f 2 =1-t, f 3 =0, define a function f(t), the function value is with probability p j value is f j, j=1, 2, 3, random disturbance is performed on the original database, and the disturbed data set D′ is obtained, as shown in Table 2;
[0084] Table 2 Dataset D′ after interference
[0085] ID
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com