RBAC (Role-Based policies Access Control) accessing control model based on organization
A technology of access control and organization, applied in the direction of instruments, digital data authentication, electronic digital data processing, etc., can solve the problems of inconvenient management and organization of objects and related operations, inability to facilitate hierarchical authorization, and inability to meet dynamic needs, etc., to meet the requirements of the system Authorization requirements, the effect of eliminating unauthorized authorization issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
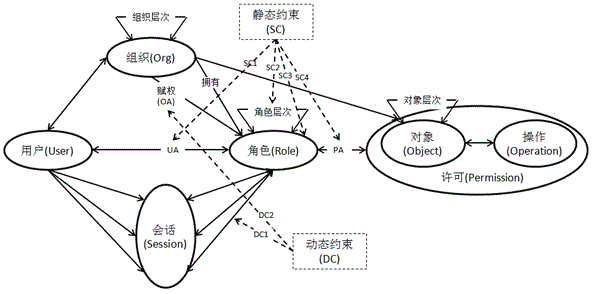
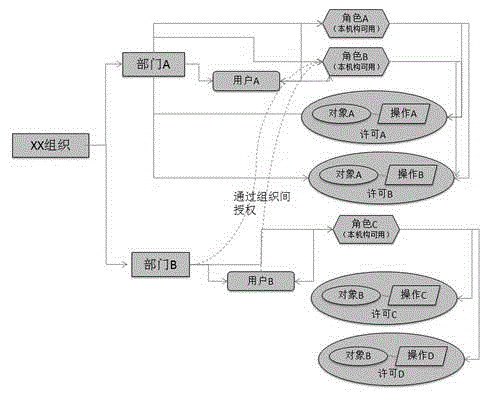
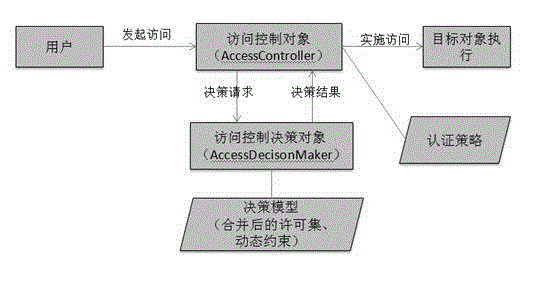
[0028] The technical solutions implemented by the present invention will be described clearly and completely in conjunction with the accompanying drawings of the present invention. The content of this description is only some examples of the present invention. In order to better describe the embodiments of the present invention, the following will combine figure 2 Go through the process of describing authorization.
[0029] figure 2 Suppose there are two departments under an organization-Department A and Department B. Department A has a user-user A, has two permissions-permission A and B (corresponding to operation A and operation B of object A respectively), and has two roles-role A and B (respectively has permission A and permission B) ; Department B has a user-user B, has two permissions-permissions C and D (corresponding to the operation C and operation D of object B), and has a role-role C (has permission C and permission D); at the same time the system The administrator...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com