Voice unlocking system and method
A voice unlocking and unlocking technology, applied in voice analysis, voice recognition, instruments, etc., can solve the problems of inconvenient operation, poor safety and convenience of unlocking operation, questioning of safety of unlocking operation, etc. The effect of convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The implementation of the present invention will be described in detail below in conjunction with the accompanying drawings and examples, so that the implementation process of how to apply technical means to solve technical problems and achieve technical effects in the present invention can be fully understood and implemented accordingly.
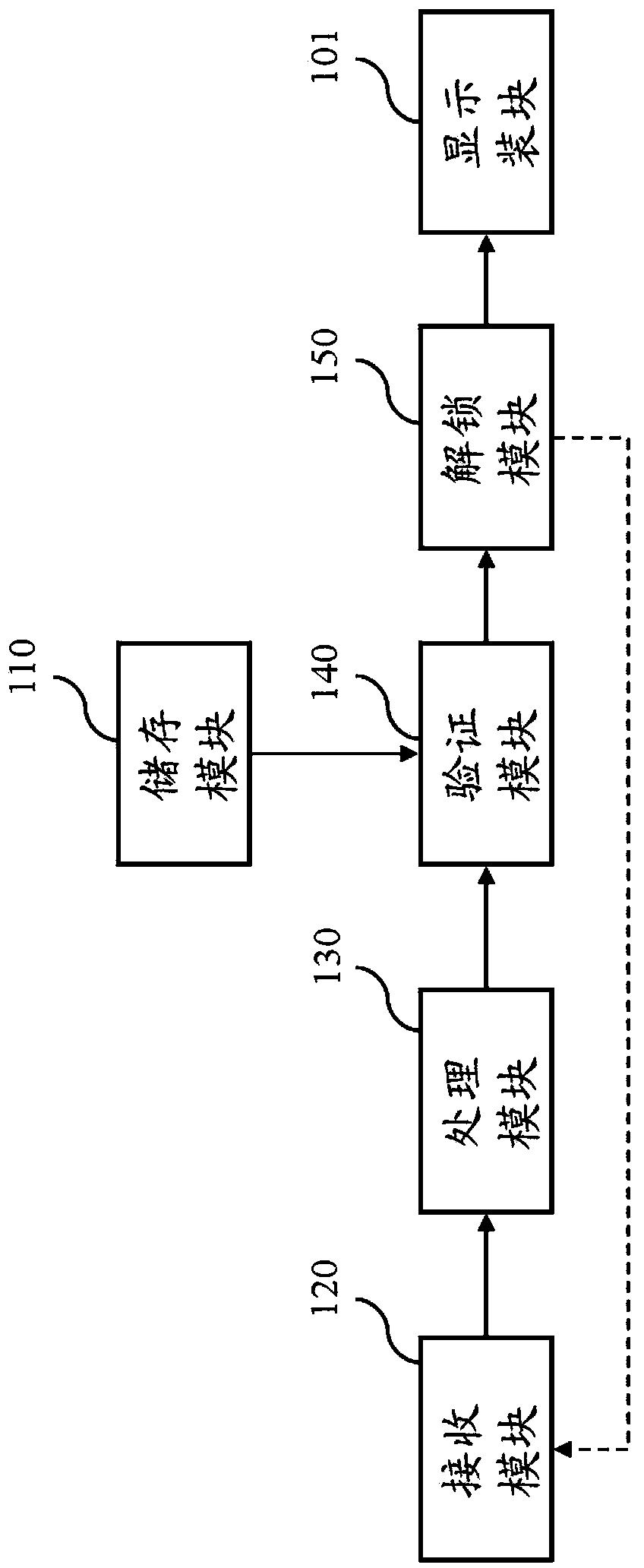
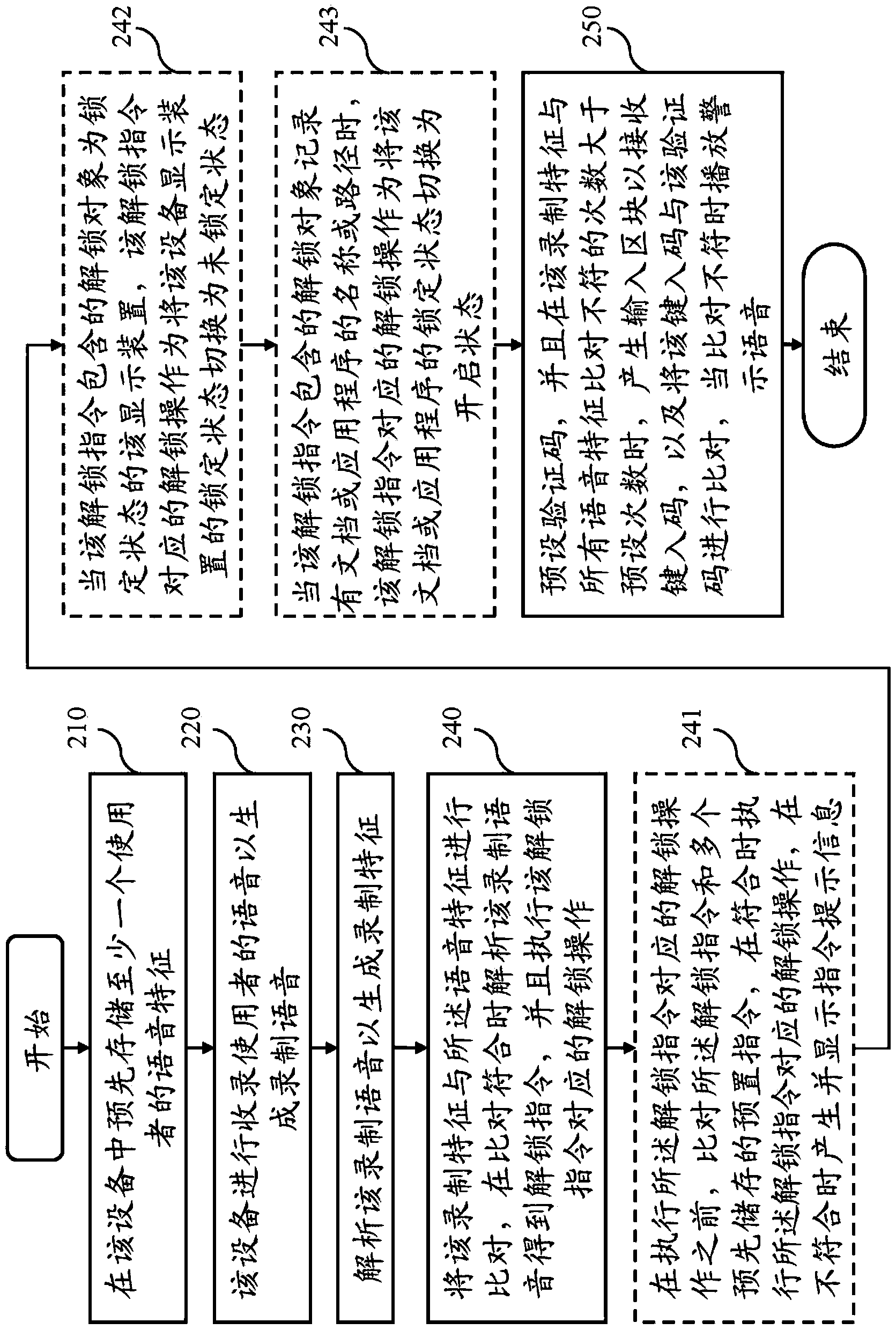
[0039] Before explaining the voice unlocking system and method disclosed in the present invention, the terms defined in the present invention will be described first. The voice features and recording features in the present invention refer to the features extracted after analyzing the voice signal. Such as: volume, pitch, timbre, etc., where the voice characteristics are pre-stored in the device, and the voice characteristics of different users can also be stored; the recording characteristics are generated by analyzing the recorded voice, and the generation method of the characteristics In the same way as the voice feature is generat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com