Telnet proxy forwarding mechanism
A mechanism and thread technology, applied in the field of Telnet proxy forwarding mechanism, can solve problems such as potential safety hazards, and achieve the effect of improving the level of internal risk control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
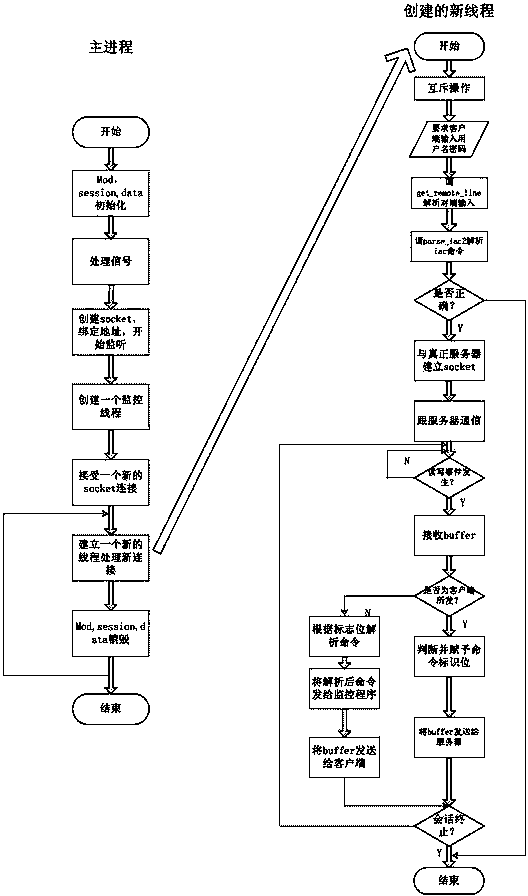
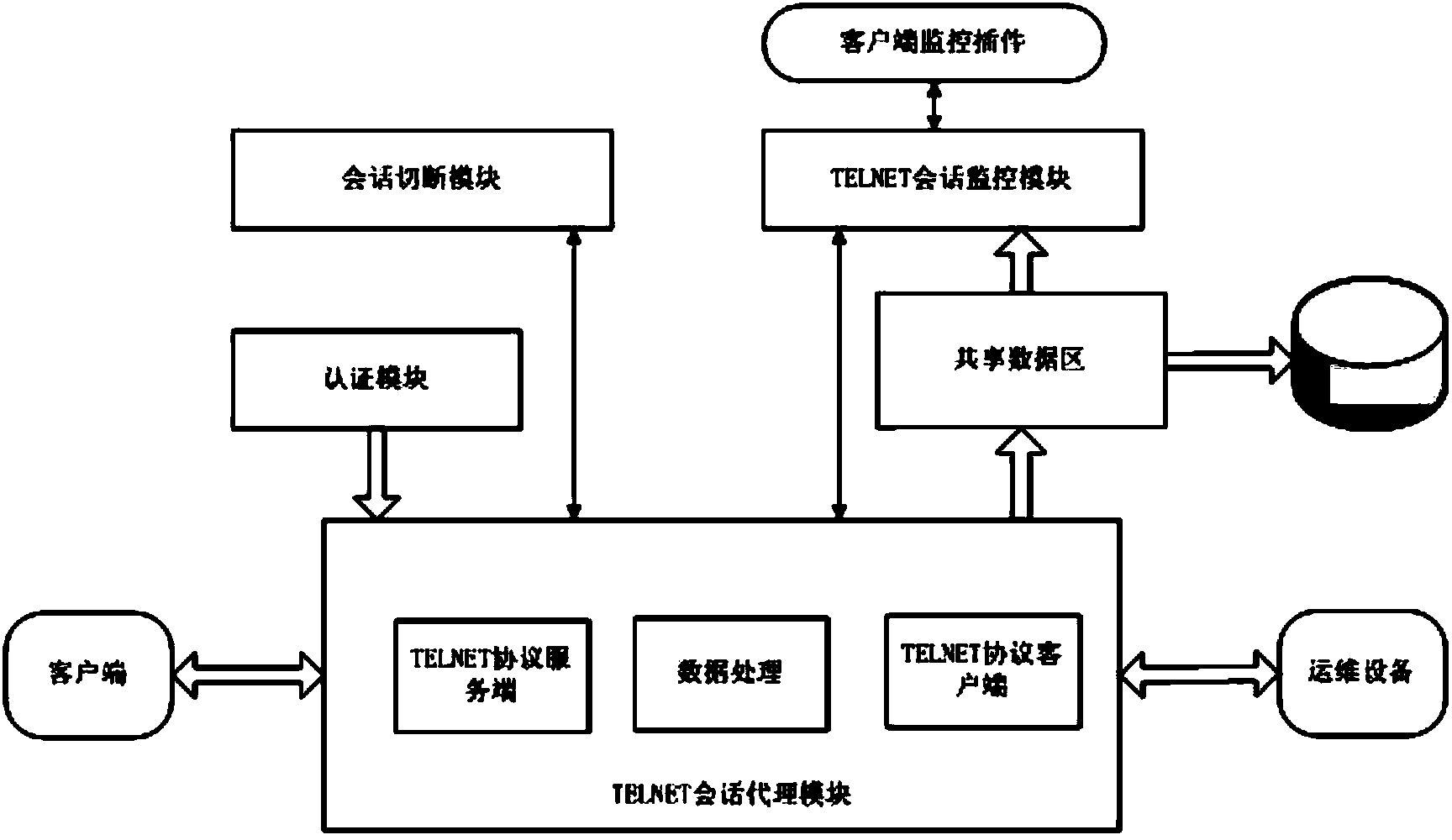
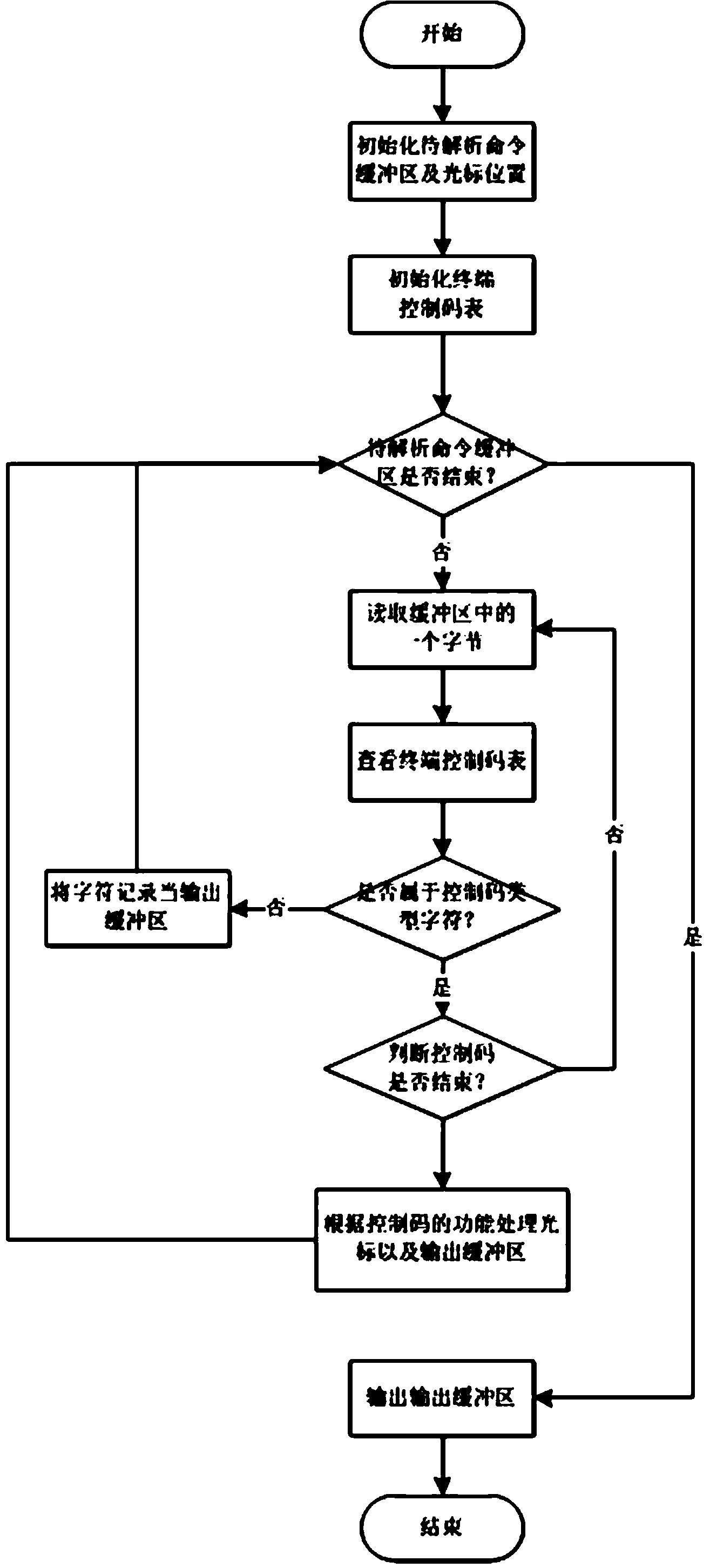
[0031] Embodiment 1: Telnet is a kind of simpler remote login agreement, and its whole process does not need encryption, but application is quite extensive, can work between any host computer or any terminal, and this among them is to come by NVT (network virtual terminal) accomplish. NVT is a virtual device, and the two connected parties, that is, the client and the server, must convert their physical terminals to and from the NVT.
[0032] The term NVT ACSII stands for 7-bit ACSII character set. Each 7-bit character is sent in 8-bit format with the most significant bit being 0. During Telnet communication, the byte 0xff is sent, which is called IAC (interpreted as a command).
[0033] During a Telnet connection, the first information exchanged between the two parties is the option negotiation data. Option negotiation is symmetric, which means that any party can actively send an option negotiation request to the other party. For any given option, either side of the connec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com