Service signature method and device compatible with Android application
A service provider and Android technology, applied in the computer field, can solve problems such as the inability to retain user data, the stripping of digital signatures of developers or distributors, and the small namespace of signature file names, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
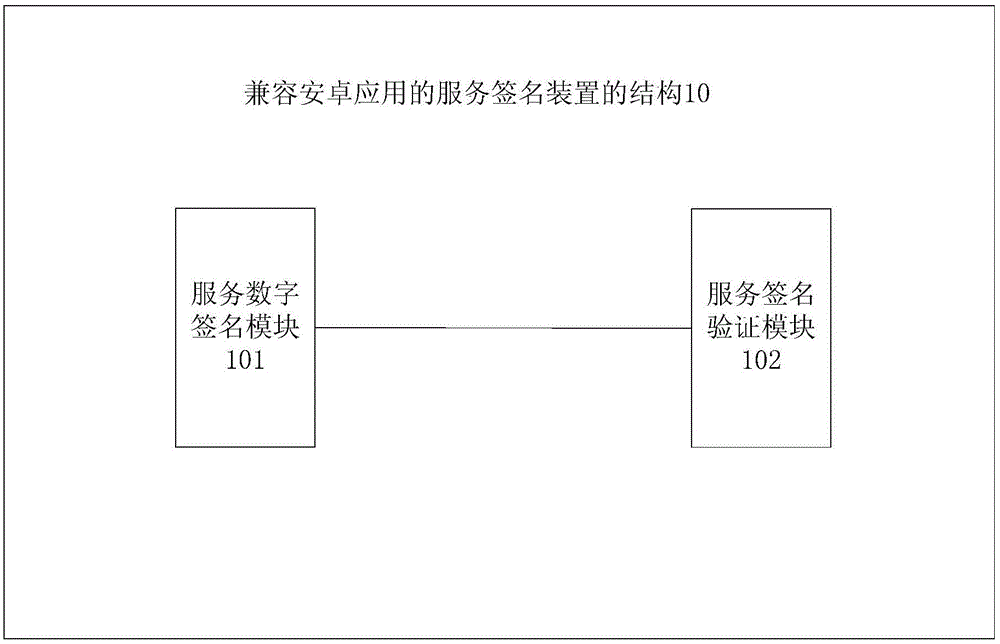
Image
Examples
Embodiment 1
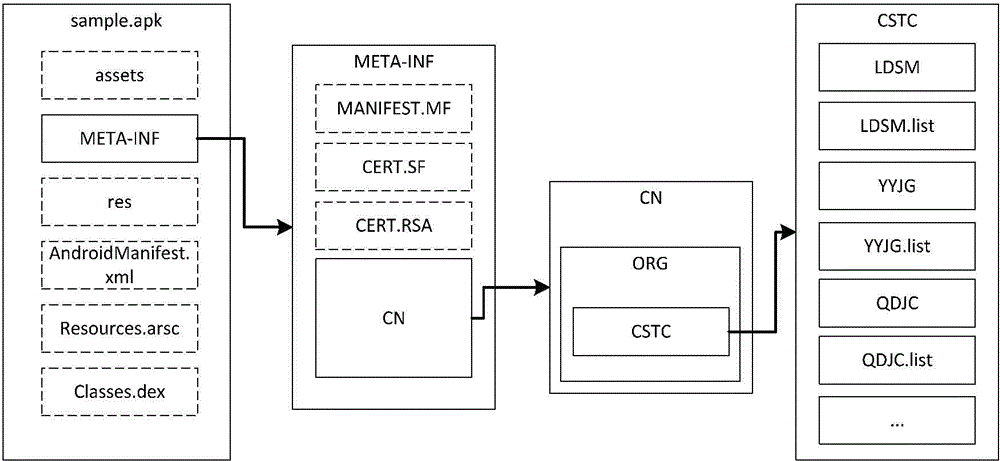
[0071] Assume that the private key of a business of the server is prikey, the business certificate is cert, the domain name of the server is www.cstc.org.cn, the business name of the service is "Application Reinforcement", the corresponding pinyin abbreviation is YYJG, and the application package sample to be signed The structure of the .apk is as follows:
[0072] sample.apk
[0073]
[0074]
[0075] Among them, there are three files AndroidManifest.xml, resources.arsc, classes.dex and three directories in the root directory of the application package sample.apk: assets, META-INF, res, and four files MANIFEST.MF in the directory META-INF , CERT.SF, CERT.RSA, others.plus, there is a file resource.xml in the directory res.
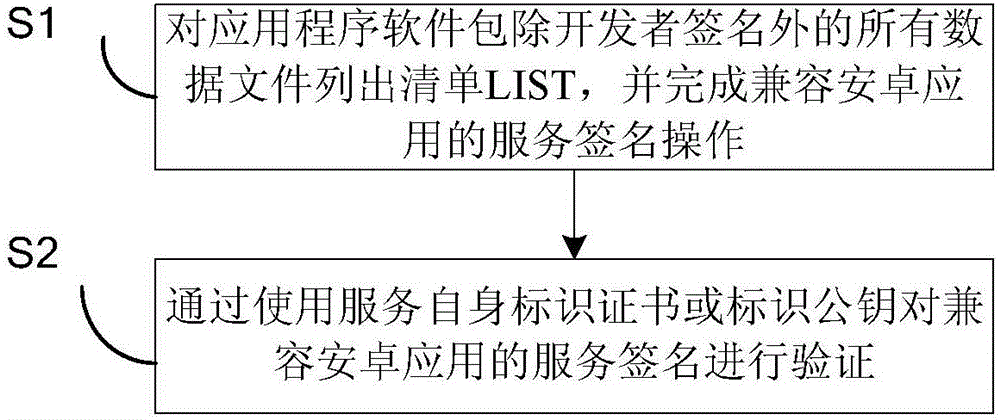
[0076] Specifically, the process of service signing is as follows: First, enumerate all files in the apk application package except the developer’s signature file, that is, .MF file, .SF file, and .RSA file, and obtain the list of data files to be d...
Embodiment 2
[0090] After using Example 1 to process the service signature of the application, it is assumed that the application package has been tampered with after it is released, and a file bug.file is added to the asset directory. It is assumed that the channel monitoring business verifies its service signature. The verification process is: channel monitoring The business service signature verification module parses the application package apk file, finds the corresponding service signature file storage directory META-INF / CN / ORG / CSTC / WWW / , and finds the summary file list QDJC.list from this directory; secondly, enumerates For all files outside the META-INF directory in the application package, check whether there are files other than the content of the summary file list in the enumerated files. Because the application has been tampered with, a file bug.file has been added to the asset directory, and the service signature verification failed;
Embodiment 3
[0092] After using Example 1 to process the service signature of the application, assuming that the application package has been tampered with after it is released, a file bug.file is added to the META-INF directory, assuming that the channel monitoring service verifies its service signature, and the verification process is as follows: The service signature verification module of the channel monitoring business analyzes the application package apk file, finds the corresponding service signature file storage directory META-INF / CN / ORG / CSTC / WWW / , and finds the summary file list QDJC.list from this directory; first, Enumerate all files outside the META-INF directory in the application package, check whether there are any files other than the contents of the summary file list in the enumerated files, and no such files are found here; secondly, read the files listed in the list file Summarize all data files, and form a string MSG of all data file summary information; secondly, read t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com