Certificate-based vehicle identification method for use in internet of vehicles
A vehicle identity and authentication method technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve the problems of increasing authentication overhead and increasing vehicle storage overhead, and achieve the effect of preventing further attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with the accompanying drawings and specific examples of implementation.
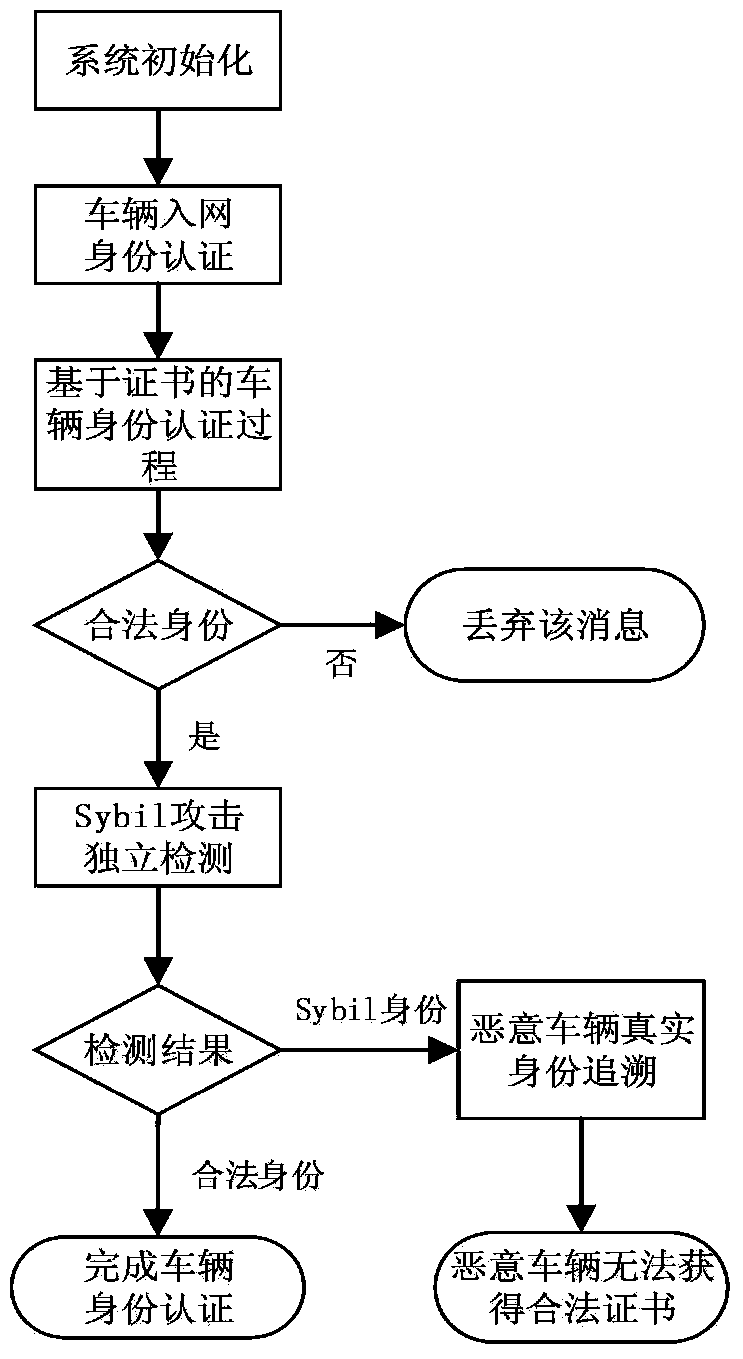
[0025] figure 1 It is a flow chart of the method of the present invention, comprising the following steps:
[0026] (1) Vehicle identity authentication system entity initialization
[0027] (1.1) Authentication Authority (TA) initialization
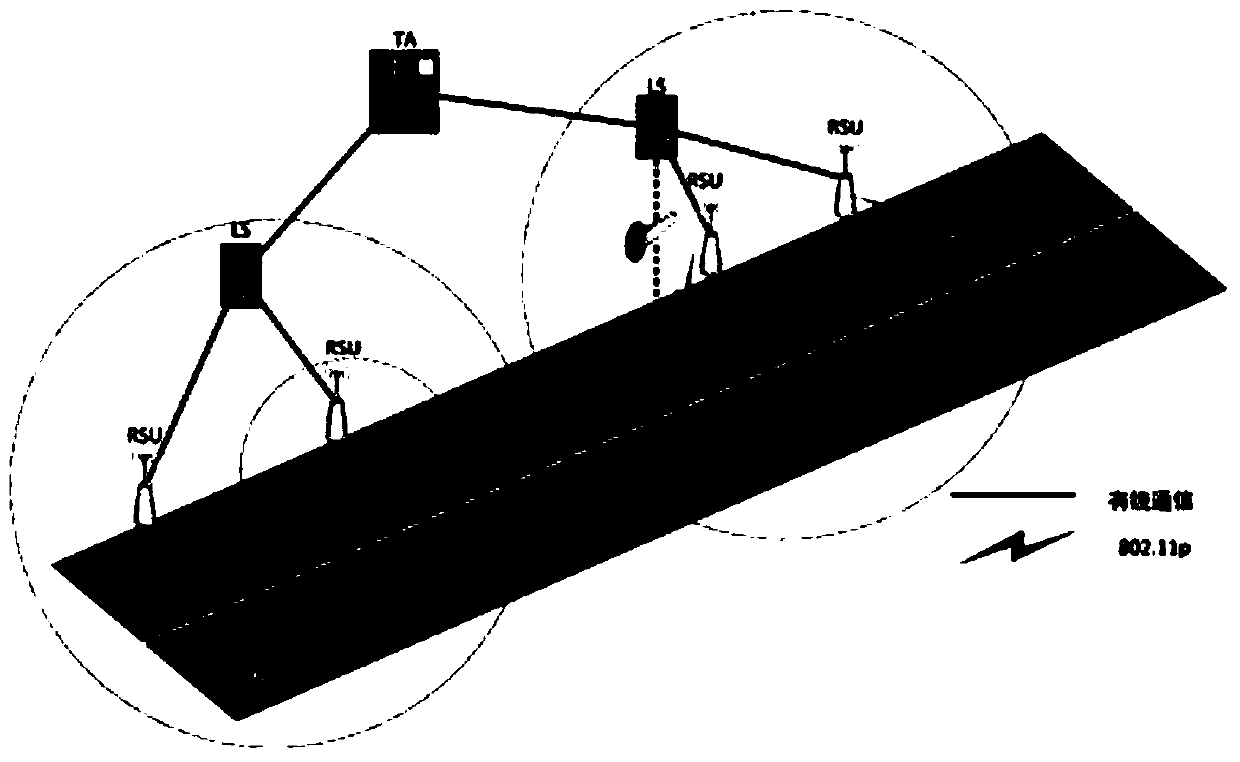
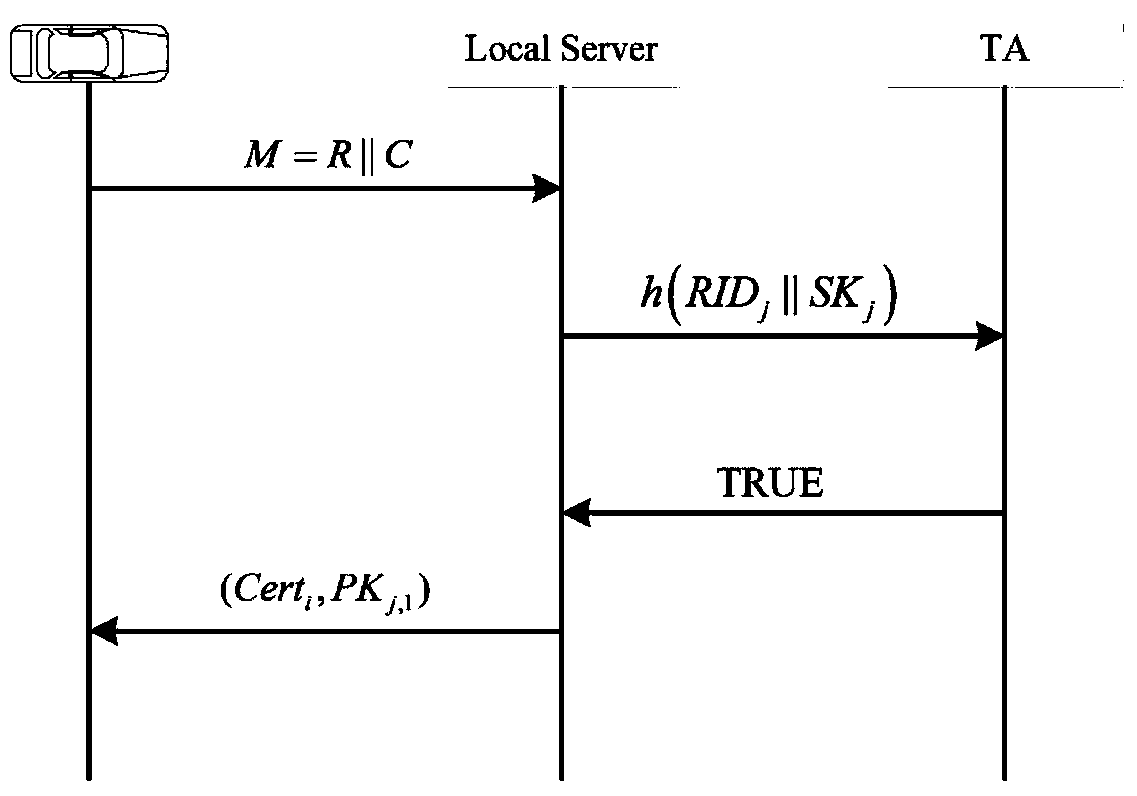
[0028] TA configures the parameters required for the signature in the vehicle identity authentication system, and the system parameters are (q, U, U’, G, G’, G T ,e,p,p',Enc(),event,h); where TA randomly selects is the private key, and calculate U=up∈G and U′=up′∈G′; G and G′ are two additive cyclic groups, G T is a multiplicative cyclic group; p and p' are the generators of G and G' respectively, and ψ(p')=p, that is, G and G' are isomorphic; e is an effective bilinear pairing mapping: e:G ×G′→G T ;Enc() is a secure symmetric encryption algorithm; event is a system event; h is a hash...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com