A Memory Integrity Protection Method Based on Write Counter
A technology of integrity protection and counter, applied in the direction of digital data protection, etc., can solve the problems of large time delay and long verification path of tree mechanism, and achieve the effect of low verification overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with the drawings.
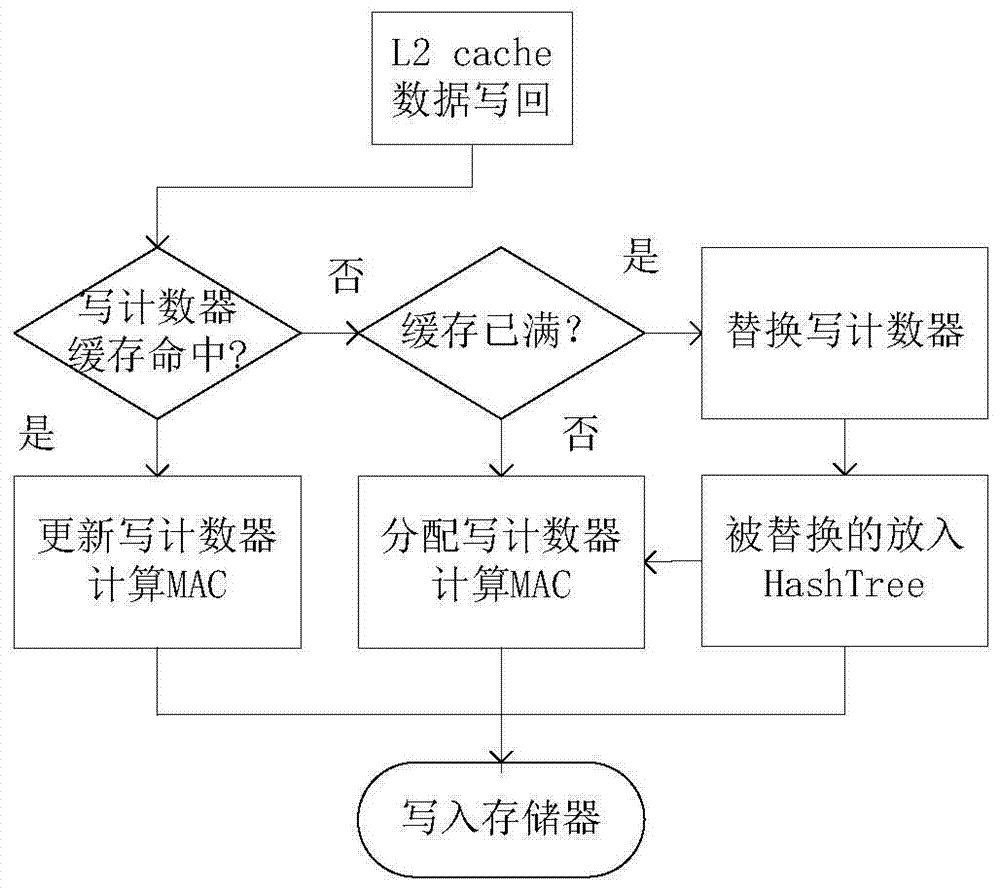
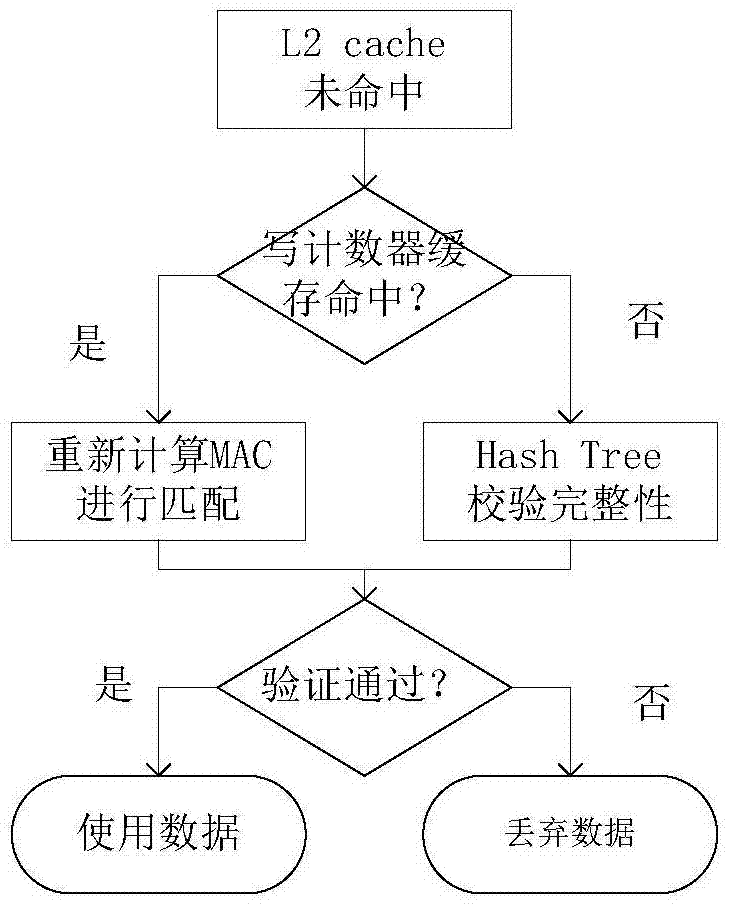
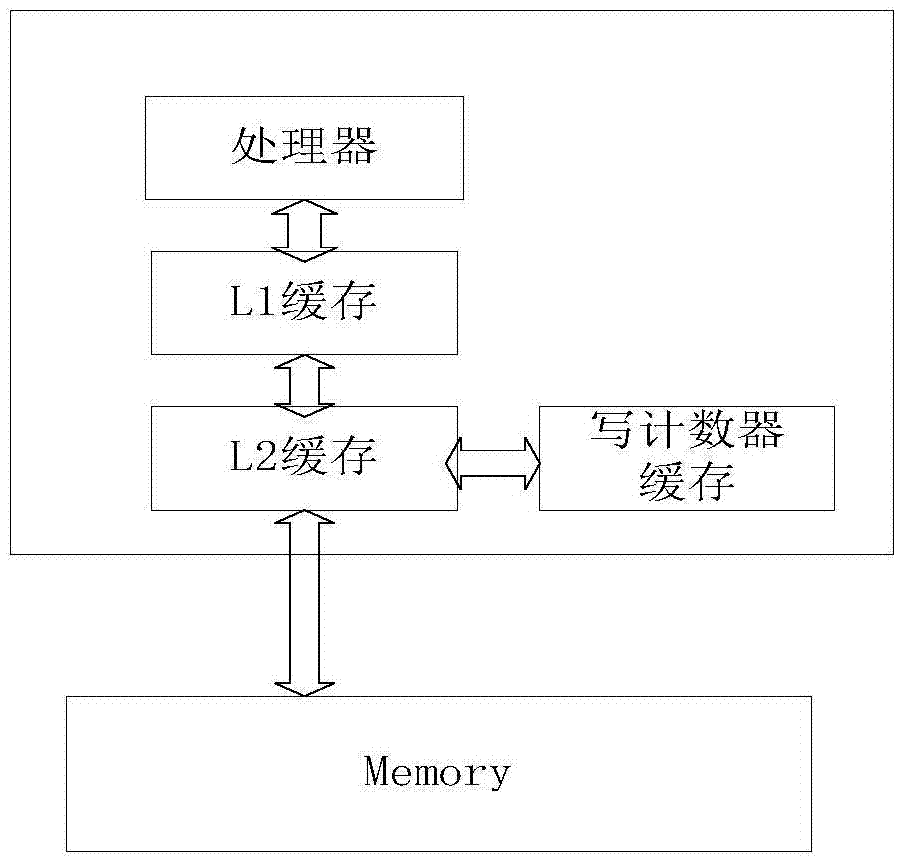
[0029] The invention relates to the field of memory integrity verification, in particular to a memory integrity protection method based on a write counter. Currently, tree structures are mainly used in terms of memory integrity, such as Merkle Tree, PAT, and TEC-Tree to protect memory. When data is updated, it is necessary to recurse from the leaf node to the root node, and the delay is very large. The present invention adopts different integrity verification mechanisms for the data on the memory. One type of data block has a write counter, which is used to record the number of times the processor writes to the memory block at this address. When writing data, the memory block address, write counter and data content are connected and then the MAC function is calculated to obtain the corresponding authentication tag for completeness Sexual verification; some data blocks do not have a w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com