A physical layer security optimization method based on SDP in multi-eavesdropping user cognitive network
A technology of physical layer security and optimization methods, applied in the field of physical layer security, can solve problems such as poor performance and high computational complexity, and achieve the effects of good security, low complexity, and high confidentiality rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
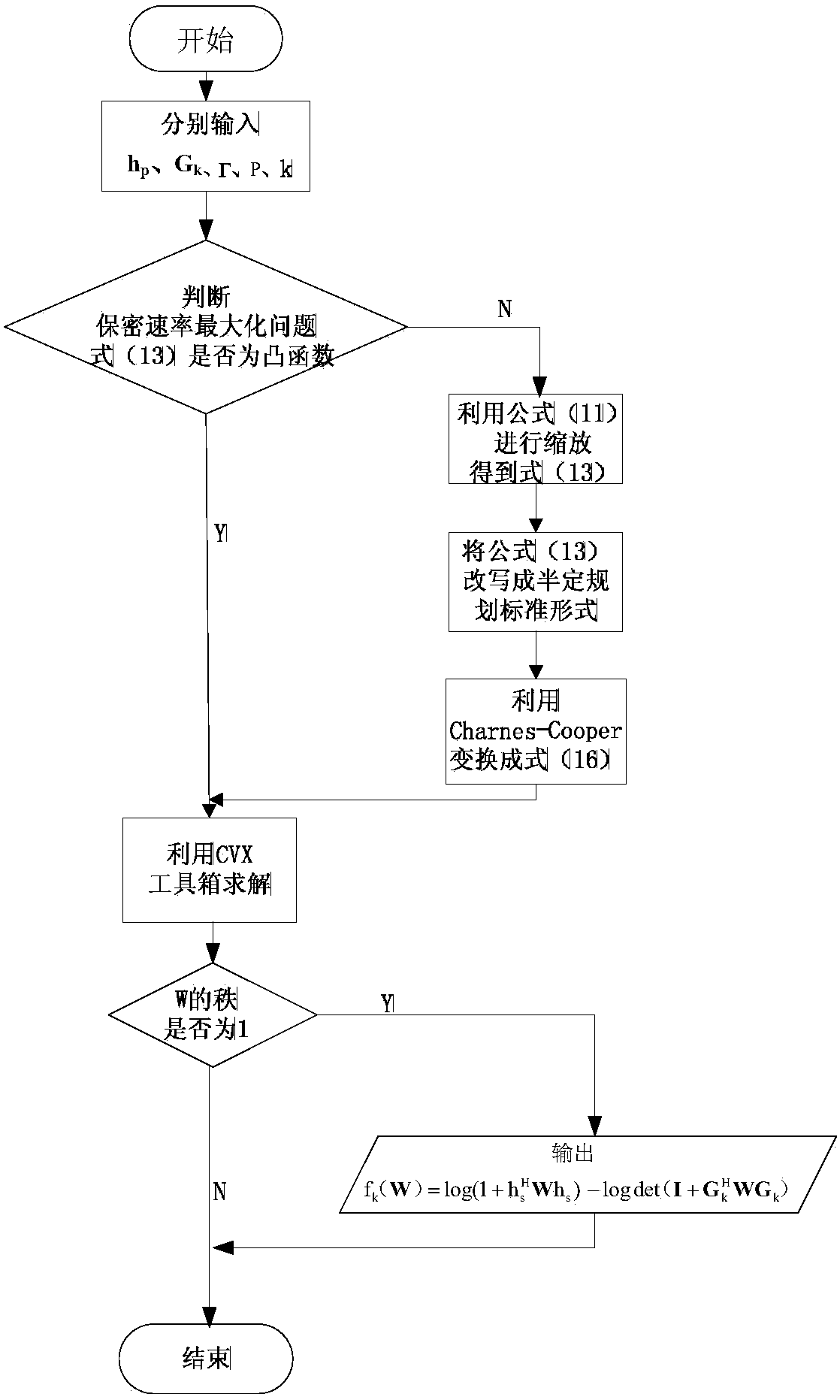
[0037] The present invention will be further explained below in conjunction with the drawings:
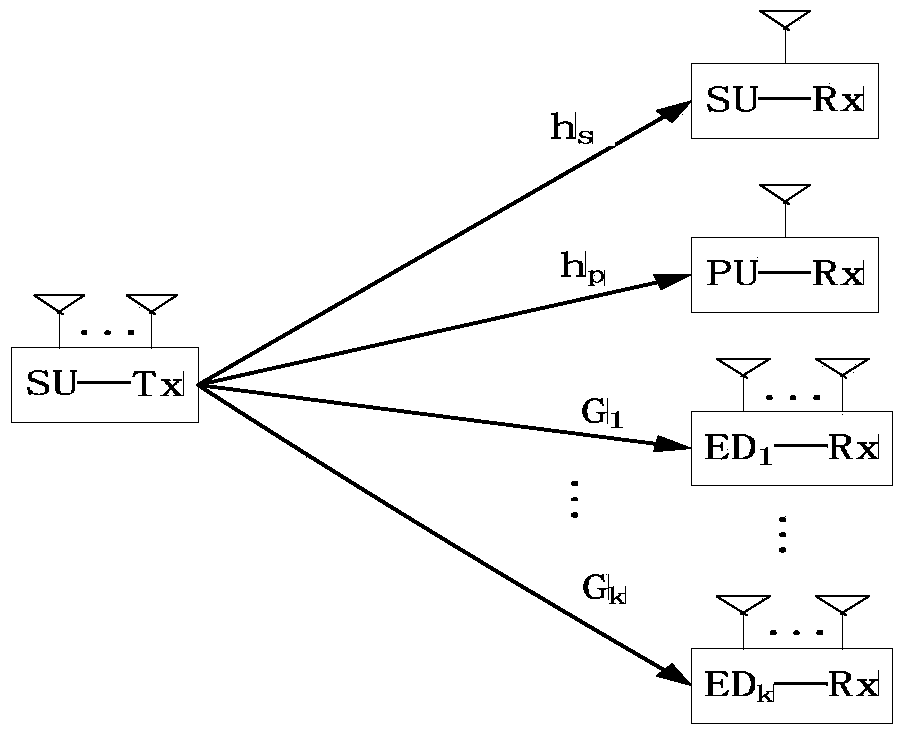
[0038] figure 1 Step 1. The system of this scheme is a multiple input single output (MISO) model under multiple multi-antenna eavesdropping users. By one with N t Antenna secondary user transmitter (SU-Tx), a single antenna secondary user receiver SU-Rx, a single antenna primary user receiver PU-Rx and K have N e Antenna eavesdropping on users (ED-Rx).
[0039] Step two, For the sending signal of the secondary user’s sender, according to figure 1 , The received signals of the secondary user SU-Rx, the primary user PU-Rx and the k-th eavesdropping user ED-Rx are:
[0040]
[0041]
[0042]
[0043] Where h s , Respectively represent the channel gain from the secondary user's transmitter to the secondary user and the primary user's receiver; Represents the channel matrix from the sending end of the secondary user to the eavesdropping end. They are the additive white Gaussian noise at th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com