A security audit system and audit method for an in-memory database
A technology of security auditing and database, which is applied to the security audit system and audit field of memory database, which can solve the problems of lack of audit system, memory database without audit ability, and memory database audit system, etc., and achieve the effect of solving audit problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
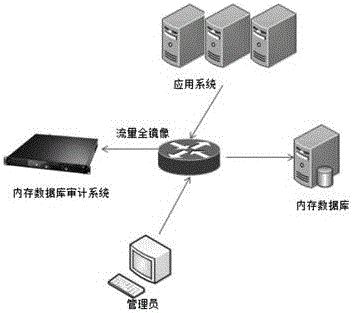
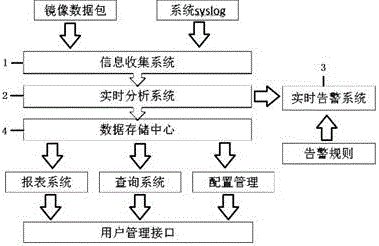
[0022] see Figure 1-3 , a security audit system for an in-memory database, comprising an information collection system 1, a real-time analysis system 2, a real-time alarm system 3 and a data storage center 4;
[0023] The information collection system 1 captures the image data packets and the system syslog between the application system and the memory database;
[0024] The real-time analysis system 2 performs real-time data analysis, and judges whether to give an alarm;
[0025] The real-time warning system 3 performs real-time warning;
[0026] The data storage center 4 records the corresponding operation information;
[0027] The in-memory database audit system adopts the mode of bypass mirroring data flow, and directly mirrors the data communication packets between the application system and the in-memory database on the switch, so that all traffic information and communication data can be obtained without affecting normal business. real time monitoring.
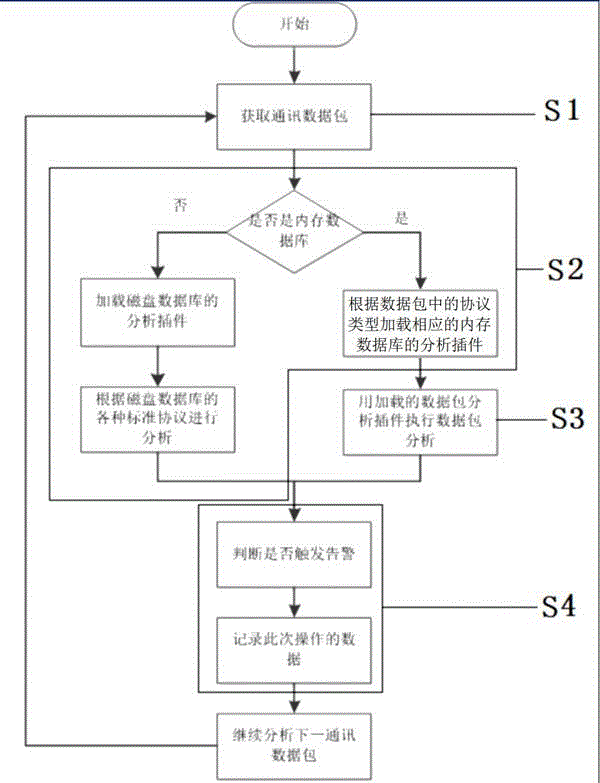
[0028] A se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com