Security auditing system and method for database, and server
A security audit and database technology, applied in the field of database security audit system, can solve the problems of information leakage, no audit rules design, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
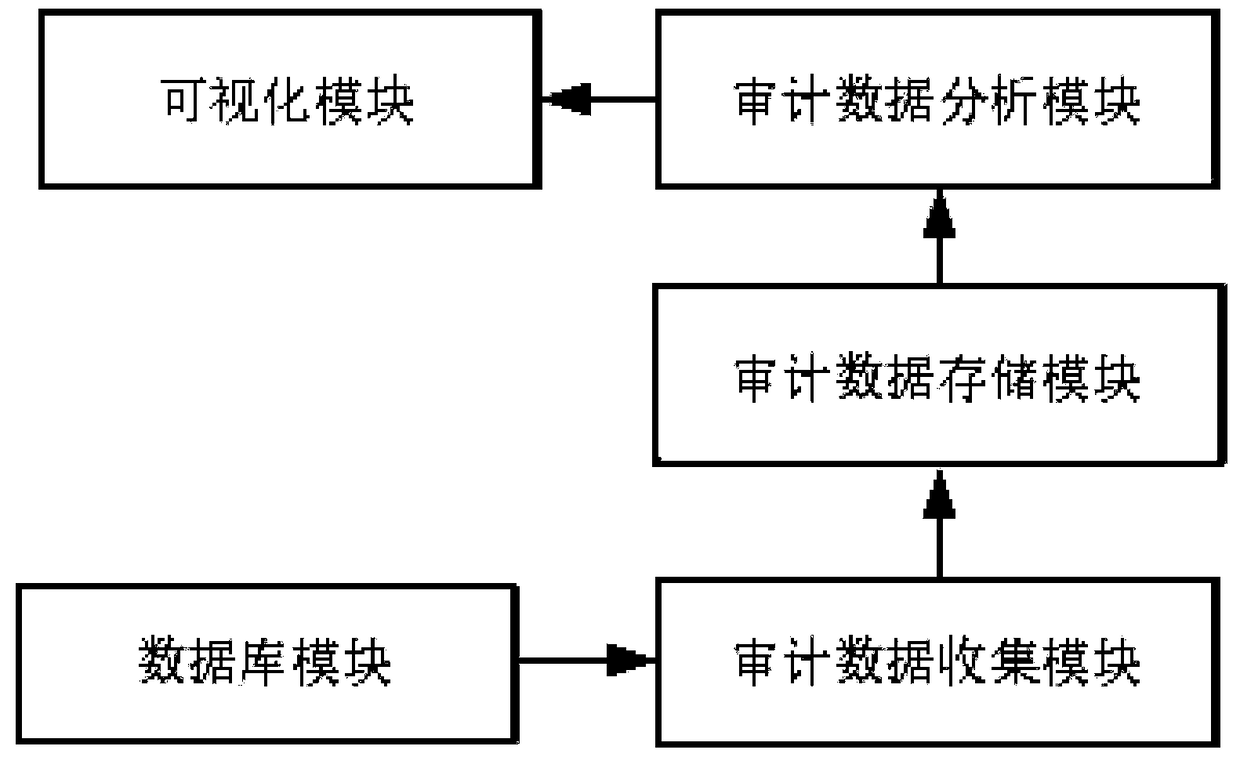
[0043] This embodiment provides a database security audit system, such as figure 1 As shown, the security audit system is installed in the database, and the security audit function is deployed to the existing database by changing the source code of the storage engine module in the existing database or through a plug-in; including the database module, audit data collection module , audit data storage module, audit data analysis module and visualization module;
[0044] The database module is built on the storage engine module of the existing database, and is used to process the data in the database according to the command request of the client, and store the operation log in the data processing process. At the same time, the data that needs to be stored stored on disk or other media;
[0045] The database module provided in this example is the storage engine part of the self-developed database. After receiving the command request from the client, it stores the data to be stor...
Embodiment 2
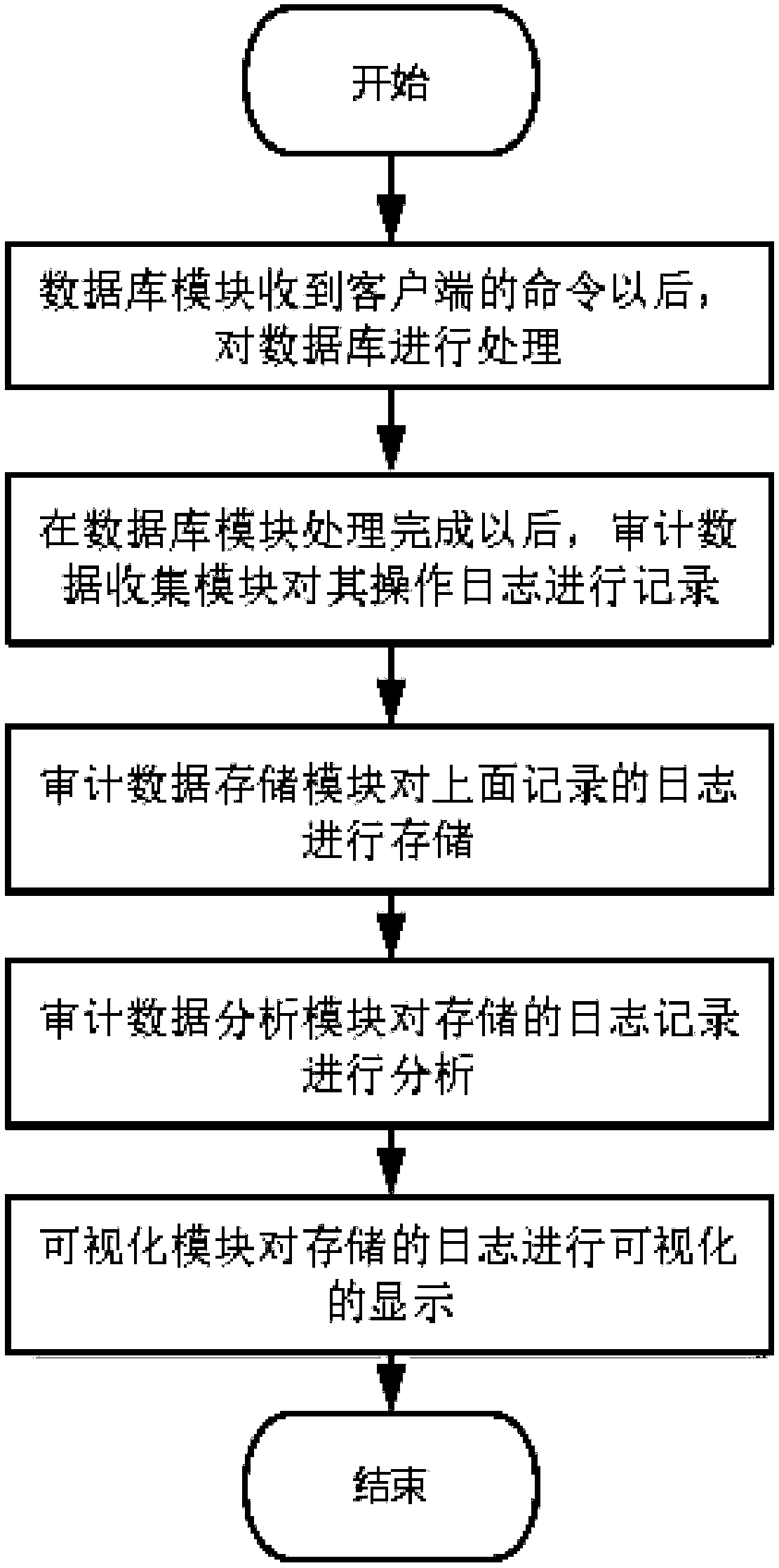
[0059] Corresponding to Embodiment 1, this embodiment provides a database security audit method, the method is applied to the database, such as figure 2 As shown, the method includes the following steps:
[0060] (1) Process the data in the database according to the client's command request, and store the operation log in the data processing process, and at the same time, store the data to be stored in the disk or other media;
[0061] (2) Collect and store the operation log of the database module, and format the collected operation log, convert it into a format that can be stored, and use it as the audit data of the security audit system;
[0062] (3) Change the underlying source code of Elasticsearch and use the open source search engine Elasticsearch storage format to classify and store the audit data collected and transformed by the audit data collection module, and index the audit log information according to time, database, and user keywords;
[0063] (4) Analyzing and...
Embodiment 3
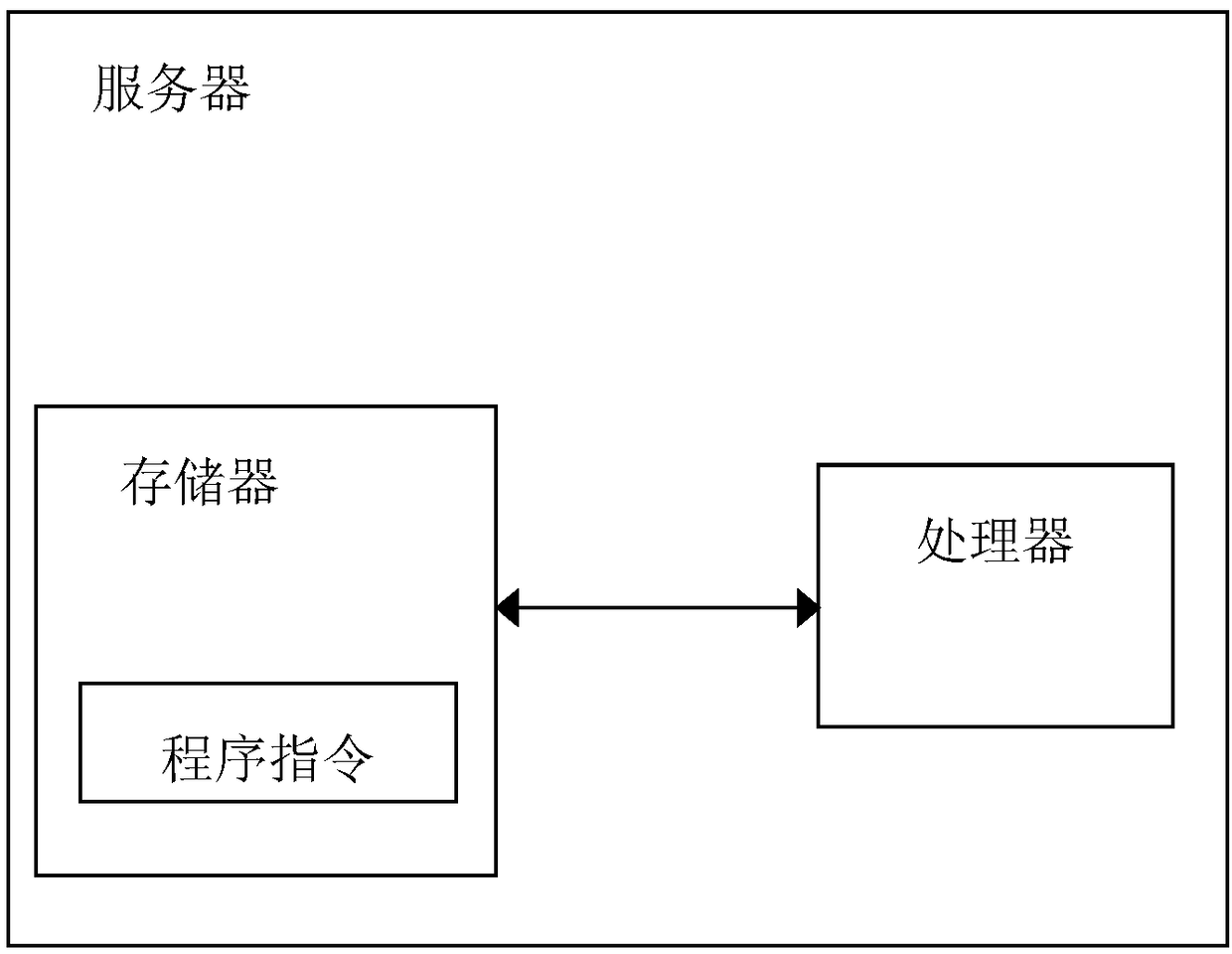
[0068] This embodiment provides a server, such as image 3 As shown, it includes a memory, a processor, and a computer program stored on the memory and operable on the processor, and the processor implements the following steps when executing the program:
[0069] (1) Process the data in the database according to the client's command request, and store the operation log in the data processing process, and at the same time, store the data to be stored in the disk or other media;
[0070] (2) Collect and store the operation log of the database module, and format the collected operation log, convert it into a format that can be stored, and use it as the audit data of the security audit system;
[0071] (3) Change the underlying source code of Elasticsearch and use the open source search engine Elasticsearch storage format to classify and store the audit data collected and transformed by the audit data collection module, and index the audit log information according to time, databas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com