Method for decrypting WeChat encrypted data based on binary system
An encrypted data, binary technology, used in digital data protection, electrical digital data processing, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in further detail below with reference to the accompanying drawings and examples.
[0014] A method based on binary decryption of WeChat encrypted data, taking an Android phone as an example:
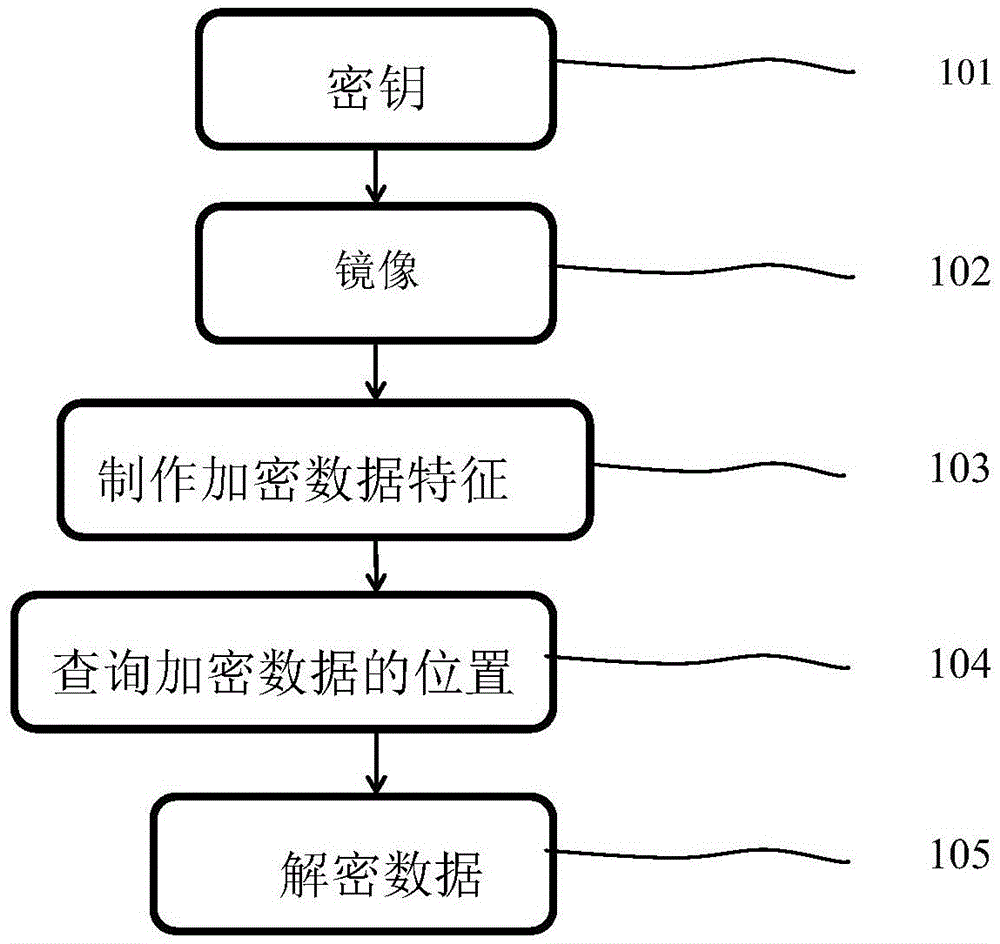
[0015] 101 Obtain the unique imei number and WeChat uid of the Android device, and calculate the key; 102 Make an image file of the Android device; 103 Use the WeChat encryption algorithm to encrypt the file identification to generate a unique and exclusive data feature; 104 Use the encrypted data feature to make in 102 In the free area of the image file, retrieve the content consistent with the data characteristics produced by 103 and obtain its address, if there is, execute 105, if not, end; 105 uses the WeChat algorithm to decrypt the data encrypted by 103.
[0016] The specific method of 101 is as follows: You can directly obtain the uniqu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com