Method and device for storing ciphertext
A ciphertext and key technology, applied in computer security devices, digital data protection, internal/peripheral computer component protection, etc., can solve problems such as data cannot be decrypted
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
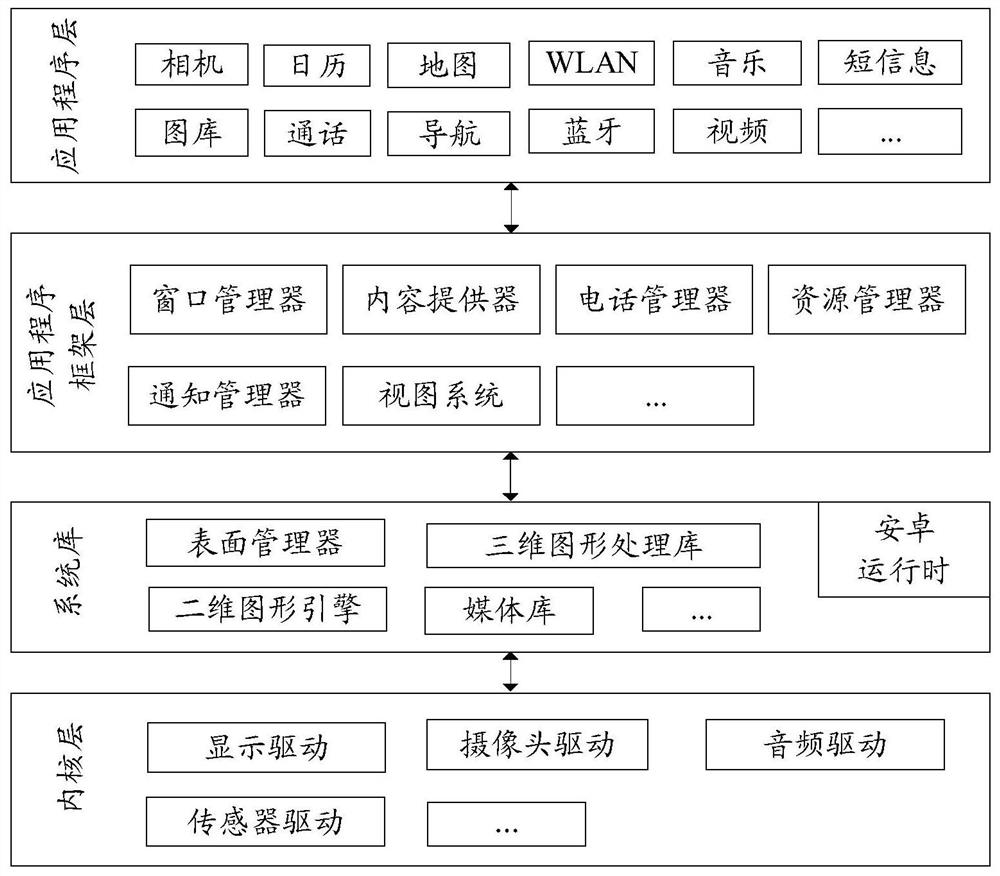
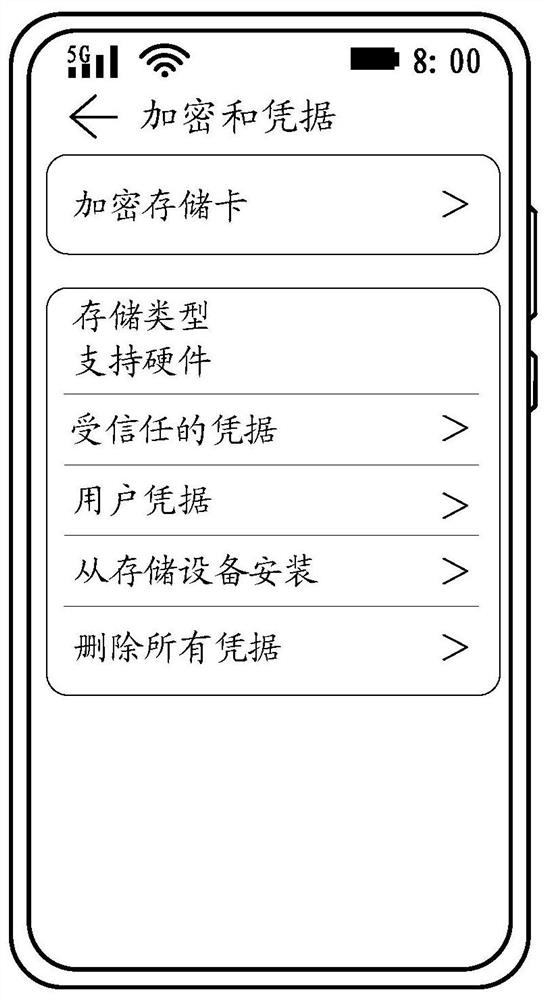
[0054] The technical solutions in the embodiments of the present application will be described below with reference to the accompanying drawings.
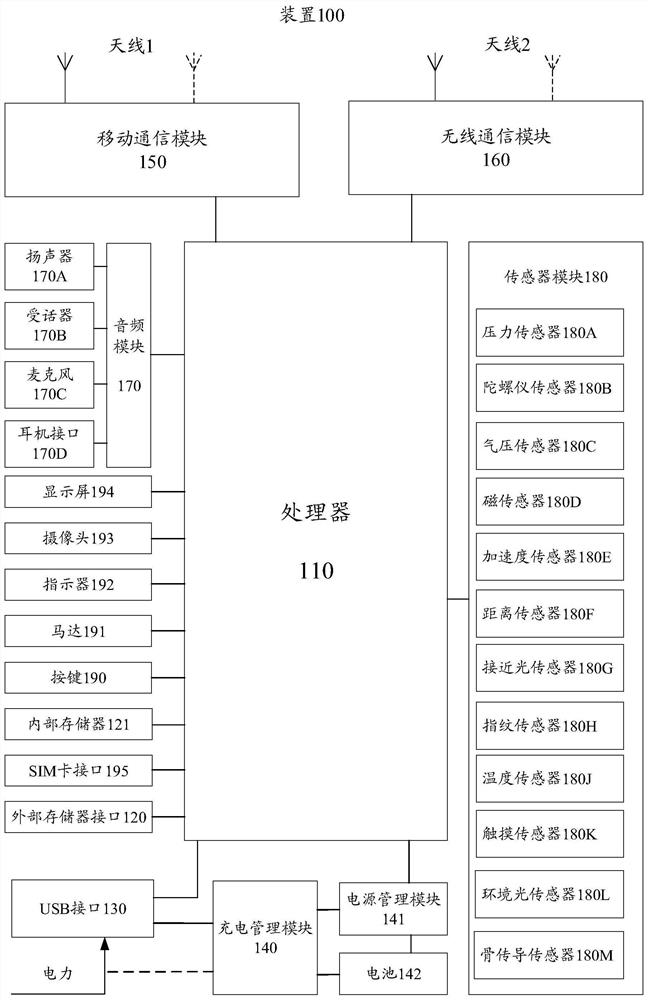
[0055] figure 1 A hardware system suitable for the apparatus of the present application is shown.
[0056] The device 100 can be a mobile phone, a smart screen, a tablet computer, a wearable electronic device, an in-vehicle electronic device, an augmented reality (AR) device, a virtual reality (VR) device, a notebook computer, an ultra-mobile personal computer (ultra mobile computer) - mobile personal computer, UMPC), netbook, personal digital assistant (personal digital assistant, PDA), projector, etc. The embodiment of the present application does not impose any limitation on the specific type of the device 100.
[0057] The device 100 may include a processor 110, an external memory interface 120, an internal memory 121, a universal serial bus (USB) interface 130, a charging management module 140, a power management module 141, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com