System and Method of Preventing Hijacking of Security Systems and Components
A component, event technology, applied in the field of systems and methods for preventing the hijacking of security systems and components, capable of addressing issues such as breach of prior contracts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
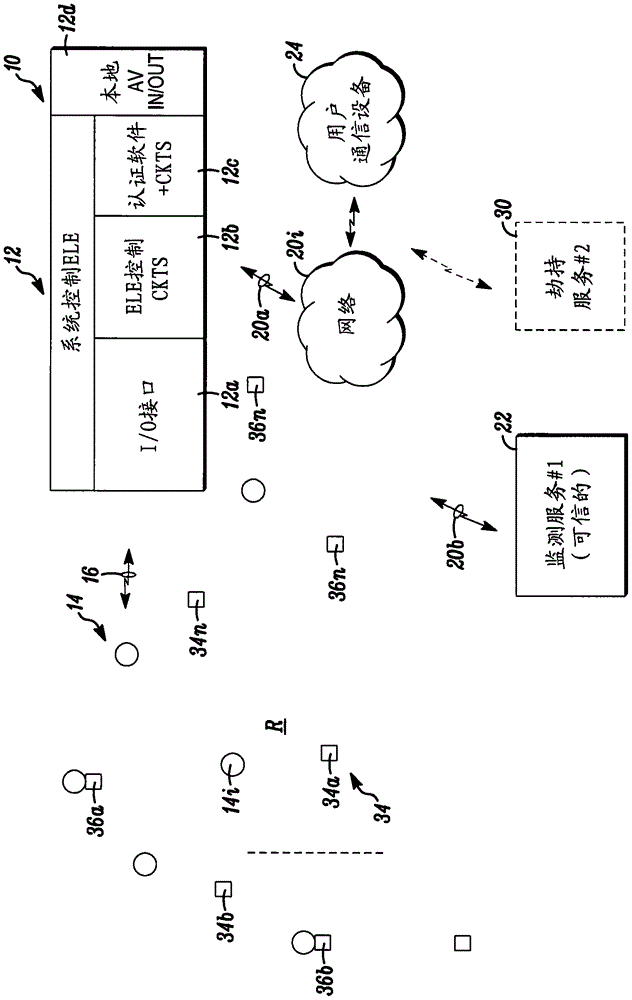
[0006] While the disclosed embodiments may take many different forms, specific embodiments thereof are shown in the drawings and are to be considered in this disclosure as illustrative of its principles and as the best mode for practicing those principles and not as intended. Specific embodiments are described in detail herein with the understanding that the application or claims are limited to the specific embodiments illustrated.
[0007] In one aspect, a decentralized component of the above mentioned primarily centralized system architecture for the purpose of preventing the above mentioned unauthorized hijacking. More generally, it provides added protection against man-in-the-middle network attacks.
[0008] In disclosed embodiments, decentralization of components is accomplished by designing 'watchdog' agents into components of the security system, especially those located at the edge of the network underlying the system architecture (e.g., sensors, device control point,...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap