Computer-implemented system and method for selecting safe paths using network scoring
A security path and computer technology, applied in the field of network security, can solve problems such as hijacking and data snooping
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
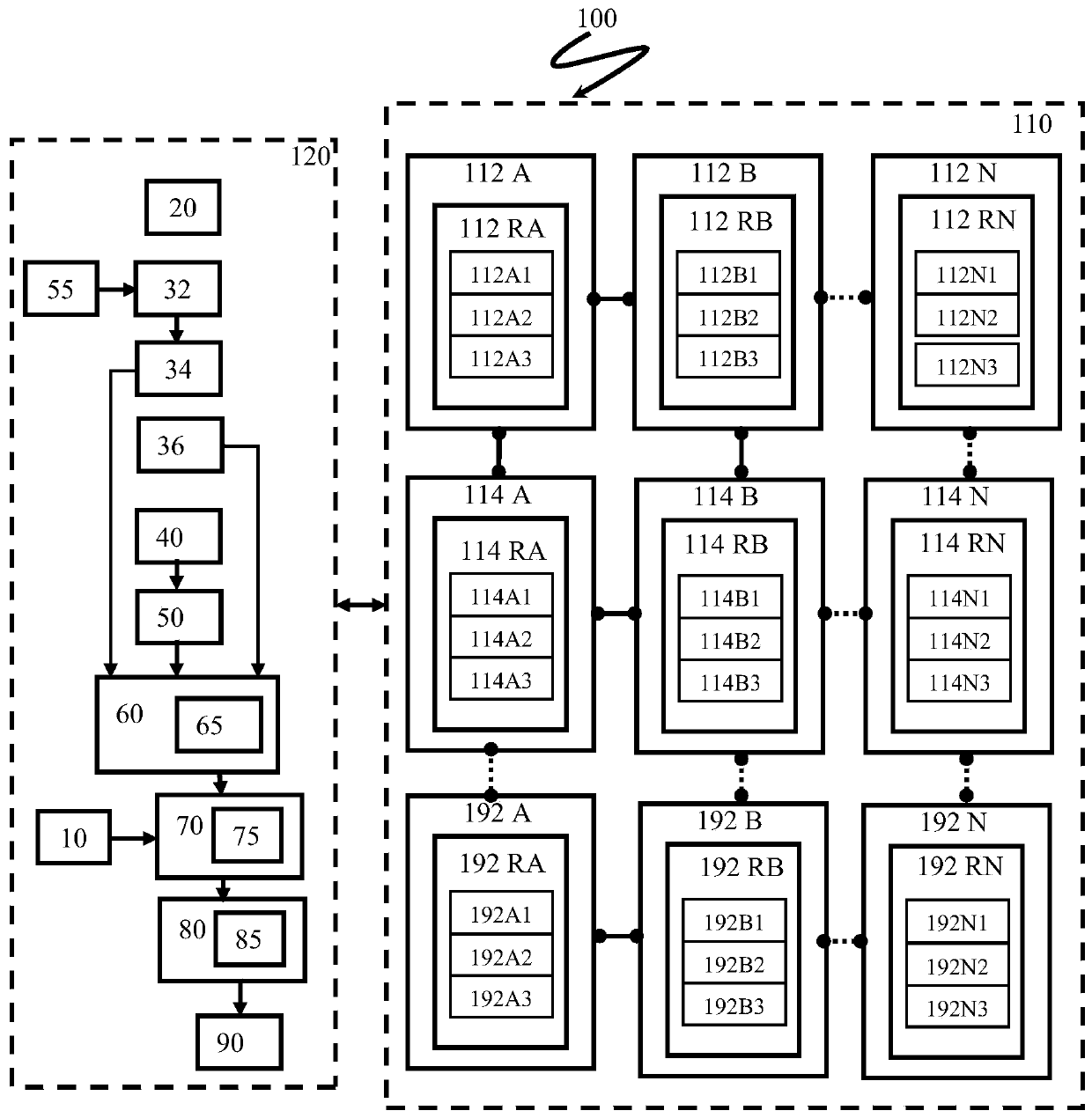
[0016] Referring now to the solution shown in the accompanying drawings, a computer-implemented system and method using network scoring to ensure route selection security will be described. This solution does not limit the scope and scope of this application. The description deals only with examples, preferred schemes of the disclosed systems and their suggested applications.
[0017] Referring to the non-limiting scenarios in the following description, the system and various features and advantages thereof are illustrated. Well-known parameters and processing techniques are omitted from the description to avoid obscuring the protocols herein. The examples used herein are only intended to facilitate the understanding of possible implementations of the solutions herein, so as to enable those skilled in the art to implement the solutions herein. As such, these examples should not be construed as limiting the scope of the protocols herein.
[0018] overview
[0019] Definitio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com