Knowledge sharing method of information operation and maintenance service based on big data trusted computing
A technology of trusted computing and knowledge sharing, applied in the field of information sharing, can solve the problems of poor timeliness and security of knowledge sharing in information operation and maintenance services, and the inability to safely and quickly realize shared information storage and release of shared information, achieving convenience The effect of barrier-free sharing, fast verification, and user privacy guarantee
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
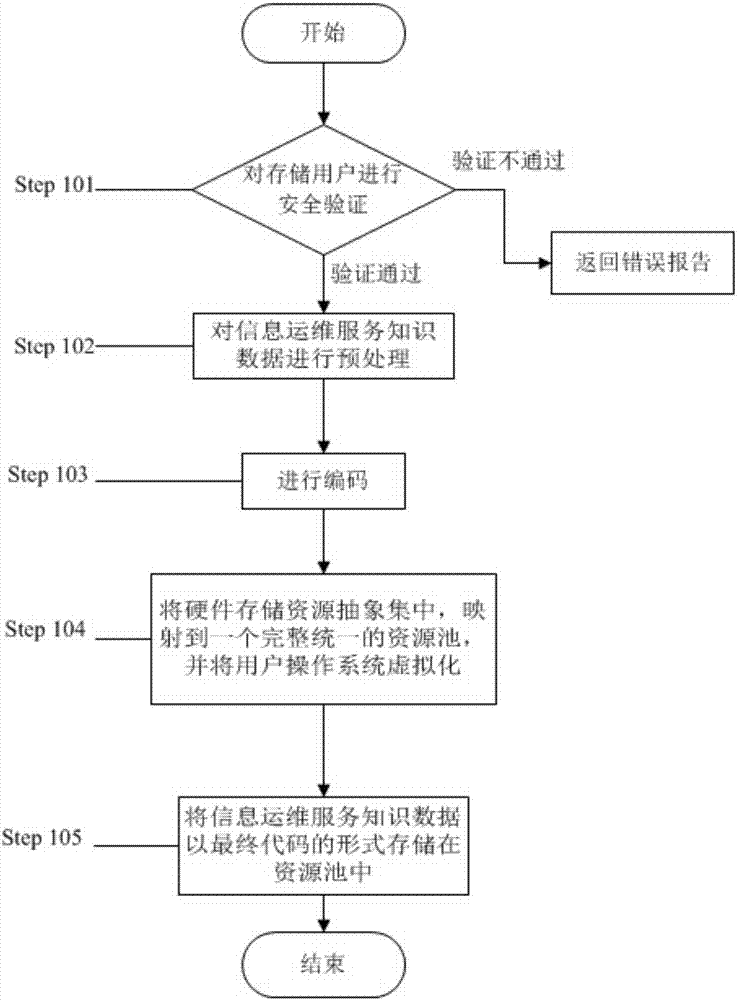
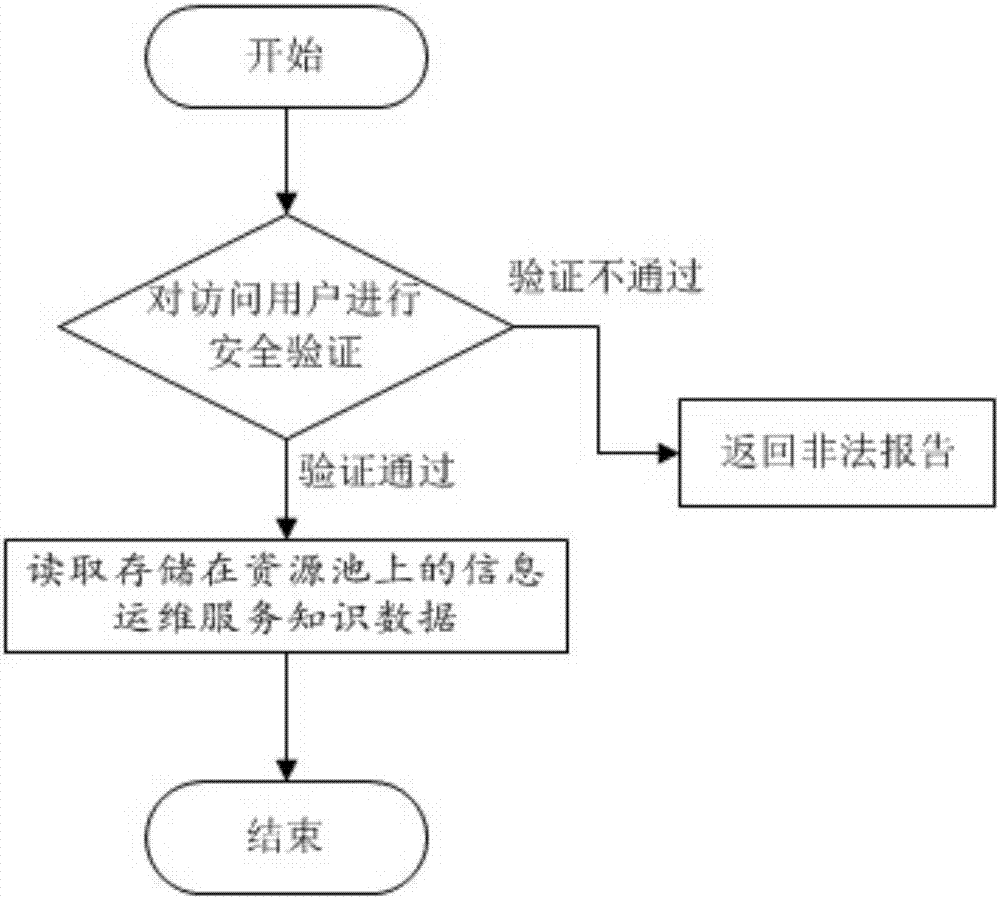
[0056] see figure 1 , figure 2 , this embodiment is based on big data trusted computing information operation and maintenance service knowledge sharing method, including information operation and maintenance service knowledge security storage and information operation and maintenance service knowledge security access;
[0057] The secure storage of information operation and maintenance service knowledge includes the following steps:
[0058] Step 101: when the storage user submits a storage request for information operation and maintenance service knowledge, perform security verification on the identity of the storage user;
[0059] Step 102 preprocesses the information operation and maintenance service knowledge data, and divides the information operation and maintenance service knowledge into two types of data: basic knowledge and business knowledge. The basic knowledge includes text and images that can reflect the basic situation of the information operation and maintenan...
Embodiment 2
[0073] see figure 1 , figure 2 , this embodiment is based on big data trusted computing information operation and maintenance service knowledge sharing method, including information operation and maintenance service knowledge security storage and information operation and maintenance service knowledge security access;
[0074] The secure storage of information operation and maintenance service knowledge includes the following steps:
[0075] Step 101: when the storage user submits a storage request for information operation and maintenance service knowledge, perform security verification on the identity of the storage user;
[0076] Step 102 preprocesses the information operation and maintenance service knowledge data, and divides the information operation and maintenance service knowledge into two types of data: basic knowledge and business knowledge. The basic knowledge includes text and images that can reflect the basic situation of the information operation and maintenan...
Embodiment 3
[0106] see figure 1 , figure 2 , this embodiment is based on big data trusted computing information operation and maintenance service knowledge sharing method, including information operation and maintenance service knowledge security storage and information operation and maintenance service knowledge security access;
[0107] The secure storage of information operation and maintenance service knowledge includes the following steps:
[0108] Step 101: when the storage user submits a storage request for information operation and maintenance service knowledge, perform security verification on the identity of the storage user;
[0109] Step 102 preprocesses the information operation and maintenance service knowledge data, and divides the information operation and maintenance service knowledge into two types of data: basic knowledge and business knowledge. The basic knowledge includes text and images that can reflect the basic situation of the information operation and maintenance...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com