A note encryption method and terminal
An encryption method and technology for sticky notes, applied in the direction of digital data protection, etc., can solve the problem of automatic encryption of sticky notes, etc., and achieve the effect of improving user experience and reducing user operations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
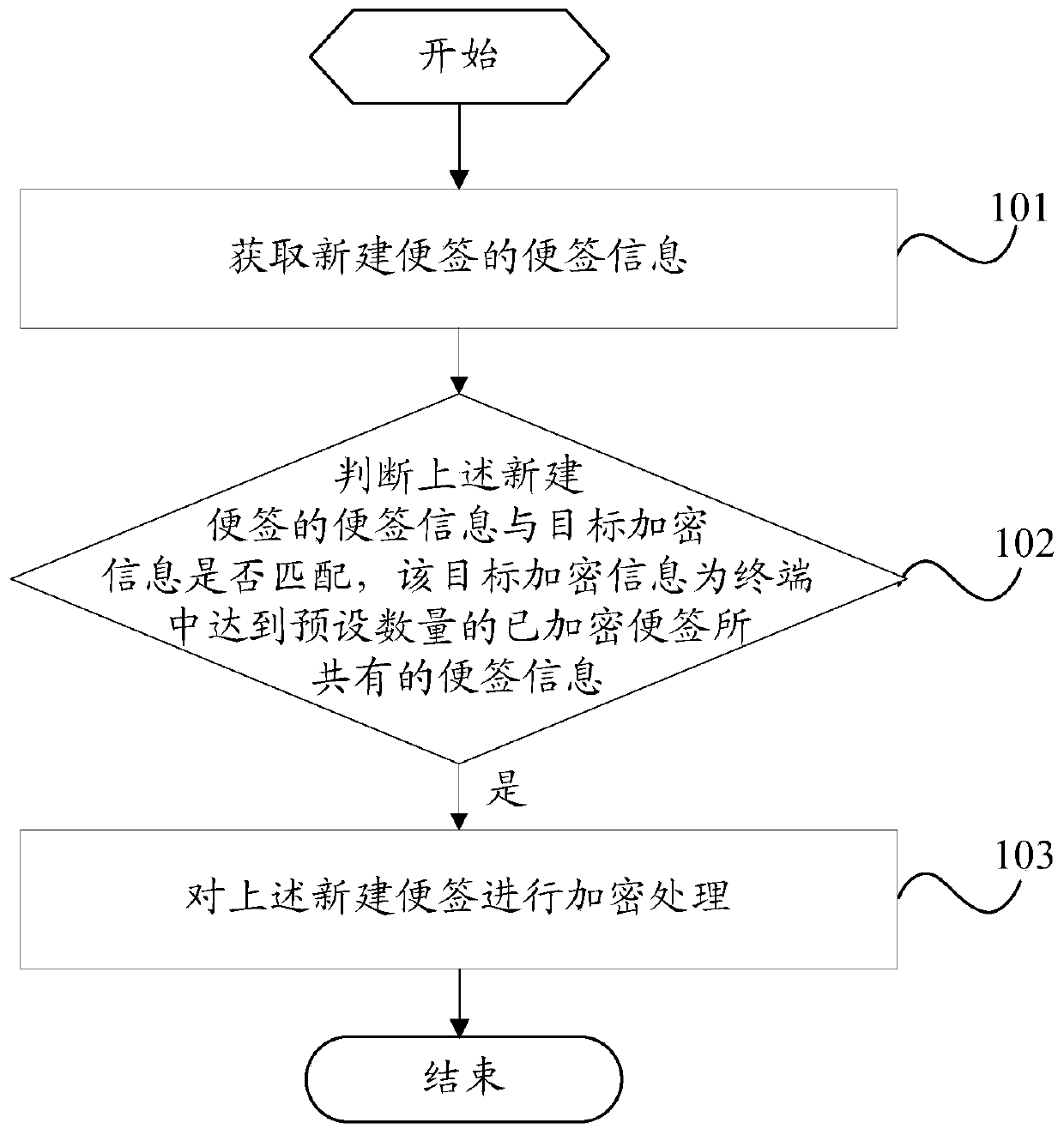
[0023] Such as figure 1 As shown, the embodiment of the present invention provides a note encryption method applied to a terminal, including:
[0024] Step 101: Obtain the note information of the newly created note.
[0025] The note information here may specifically be note type or note content.
[0026] In a specific embodiment of the present invention, if the user turns on the automatic encryption function, after the user creates a new note, the note information of the newly created note will be obtained, so that the new note will be automatically encrypted according to the note information of the newly created note .
[0027] Step 102: Determine whether the note information of the above-mentioned newly created note matches the target encrypted information, which is the note information shared by the preset number of encrypted notes in the terminal.
[0028] Here, the above note information may include keywords or note types. The encrypted note can be specifically the n...
no. 2 example
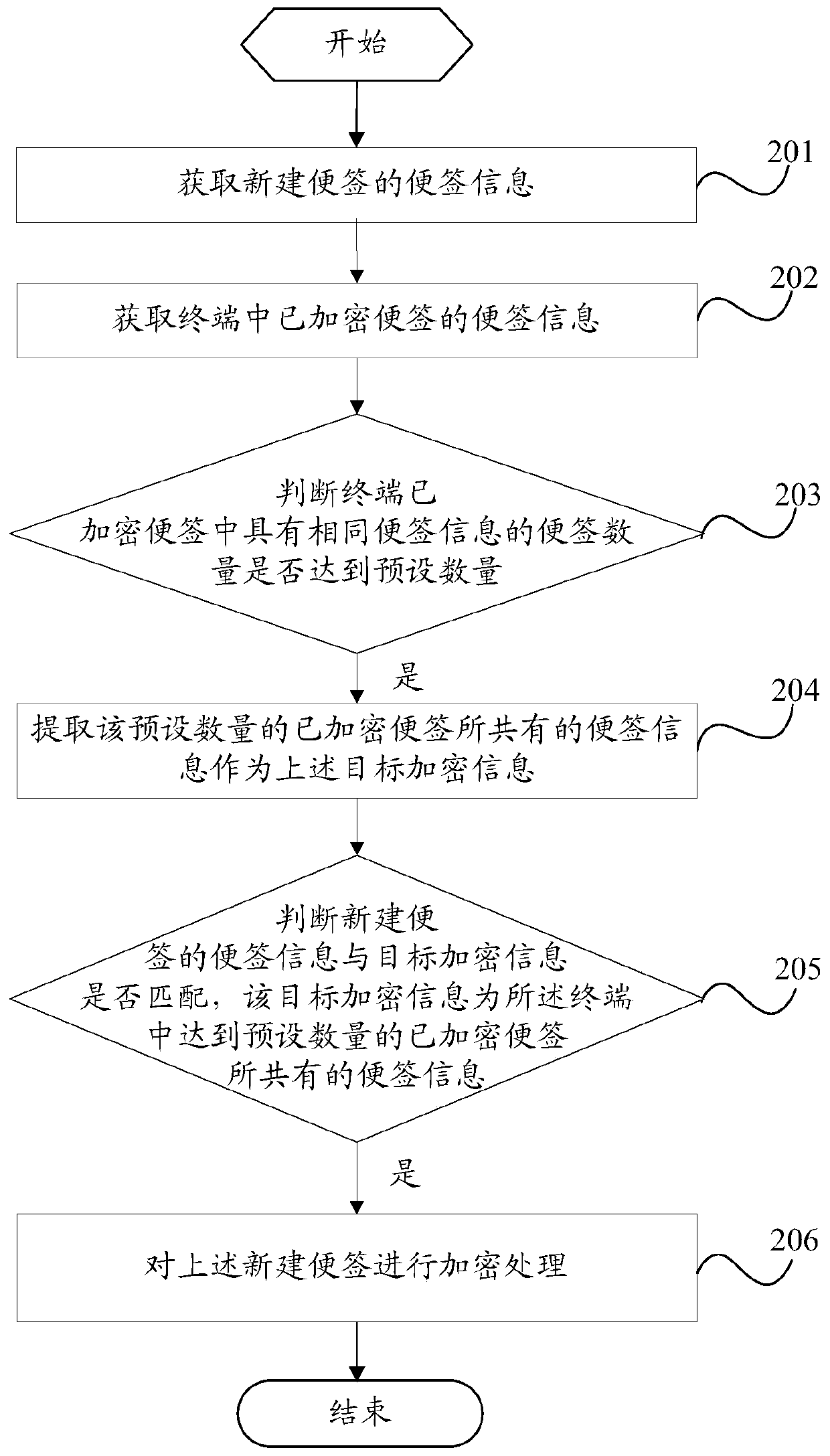
[0041] Such as figure 2 As shown, the embodiment of the present invention provides a note encryption method applied to a terminal, including:
[0042] Step 201: Obtain the note information of the newly created note.
[0043] This step is the same as step 101 in the above-mentioned first embodiment, and will not be repeated here.
[0044] Step 202: Obtain the note information of the encrypted note in the terminal.
[0045] The note information here may include note type and note content.
[0046] Step 203: Judging whether the number of notes with the same note information in the encrypted notes of the terminal reaches a preset number.
[0047] Step 204: If the preset number is reached, extract the note information shared by the preset number of encrypted notes as the target encrypted information.
[0048] When the number of identical note information is greater than or equal to the preset number, it indicates that the note information is common information of encrypted not...
no. 3 example
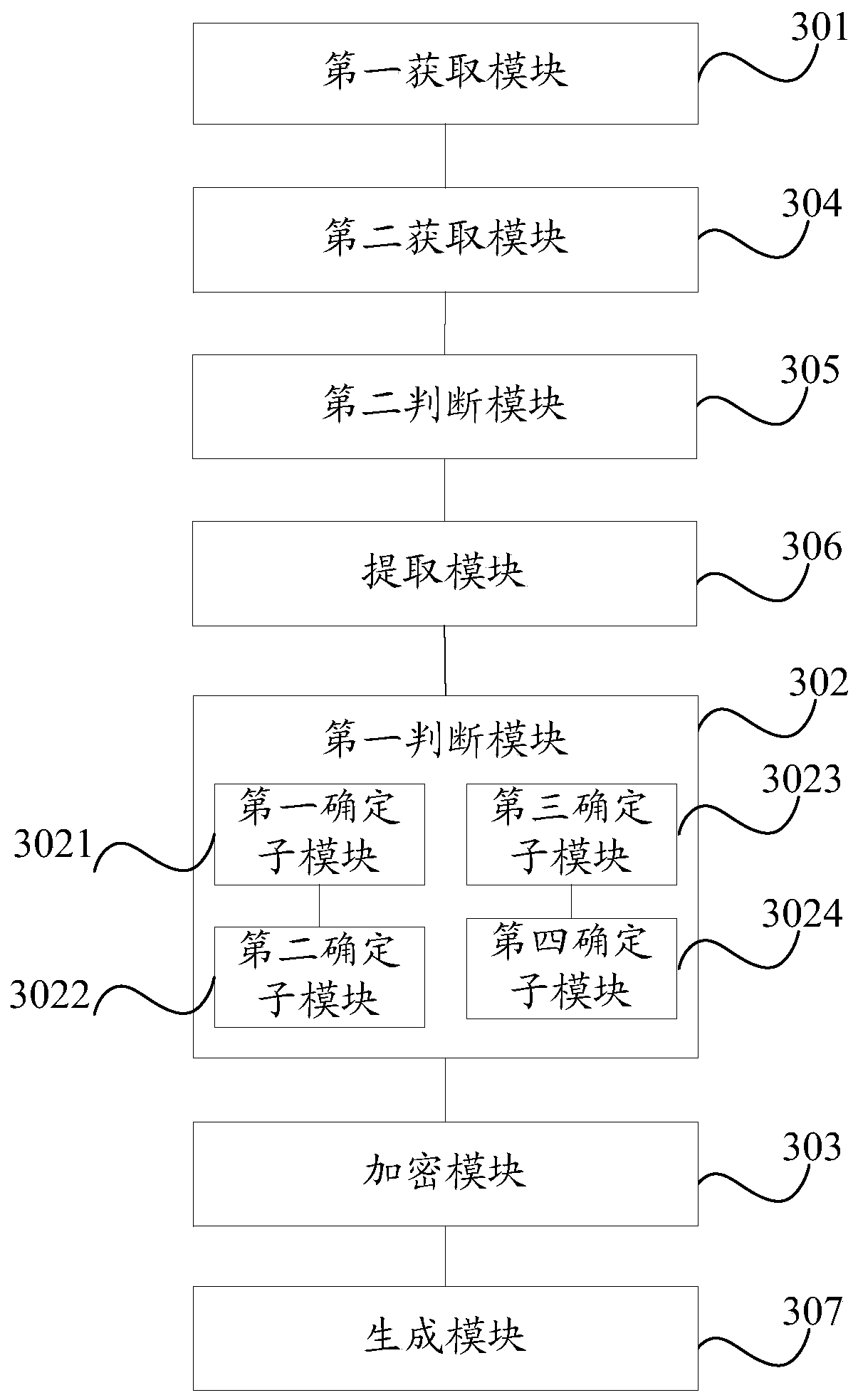
[0059] like image 3 As shown, the embodiment of the present invention also provides a terminal, including:
[0060] The first obtaining module 301 is used to obtain the note information of the newly created note;
[0061] The first judging module 302 is used to judge whether the note information of the newly-created note matches the target encrypted information, and the target encrypted information is the note information shared by the encrypted notes reaching a preset number in the terminal;
[0062] The encryption module 303 is configured to perform encryption processing on the newly created note if the note information of the newly created note matches the target encrypted information.
[0063] The terminal of the embodiment of the present invention also includes:
[0064] The second obtaining module 304 is used to obtain the note information of the encrypted note in the terminal;
[0065] The second judging module 305 is used to judge whether the number of notes with t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com