Risk identification method and equipment
A risk identification and risk technology, applied in the field of network information security, can solve problems such as the reduction of communication software security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
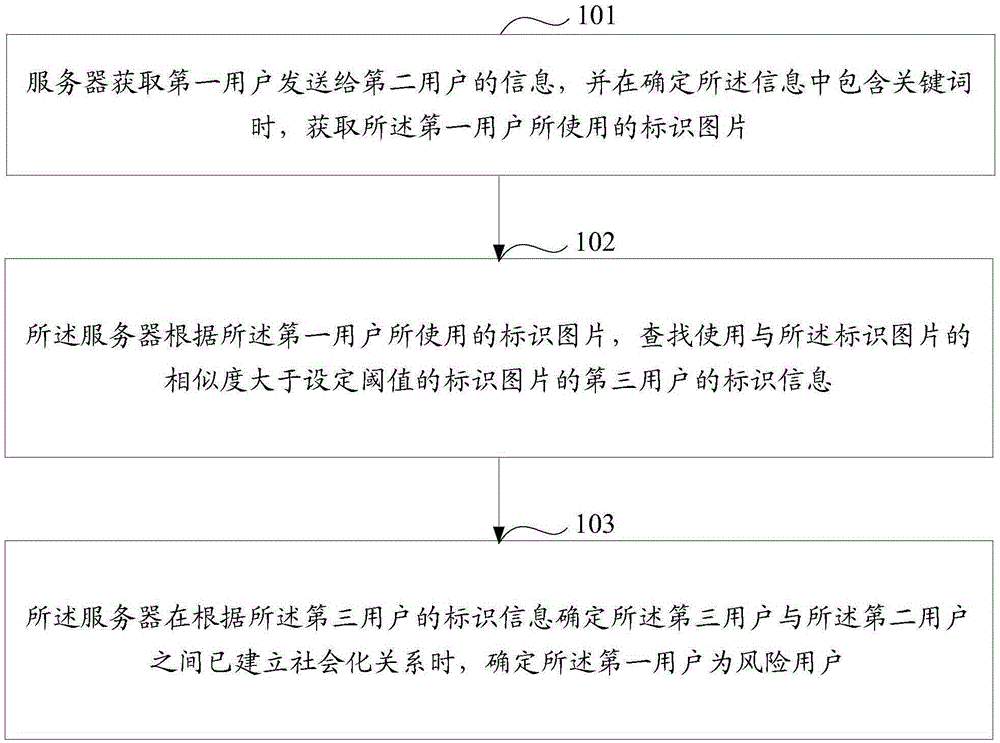
[0027] In order to achieve the purpose of this application, the embodiment of this application provides a risk identification method and device, the server obtains the information sent by the first user to the second user, and when it is determined that the information contains keywords, obtains the An identification picture used by the first user; according to the identification picture used by the first user, search for identification information of a third user who uses an identification picture whose similarity with the identification picture is greater than a set threshold; When the identification information of the third user determines that a social relationship has been established between the third user and the second user, it is determined that the first user is a risk user.
[0028] Through the method described in the embodiment of this application, when the server finds that some keywords appear in the communication content of both parties, it triggers the identific...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com