A method and device for realizing secure communication
A technology for secure communication and access, applied in telephone communication, branch equipment, electrical components, etc., to avoid the risk of eavesdropping
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
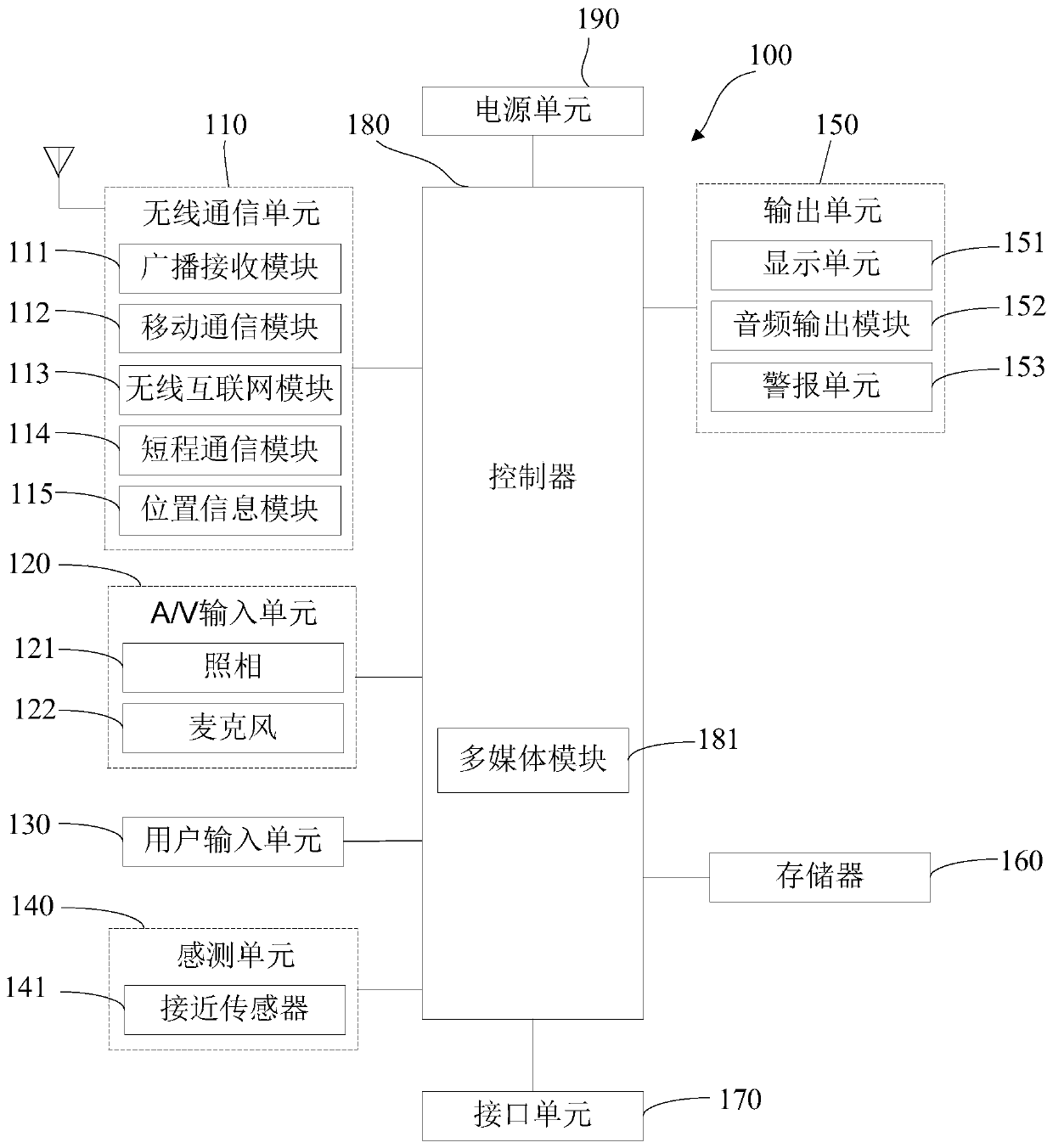
Image
Examples
example 1
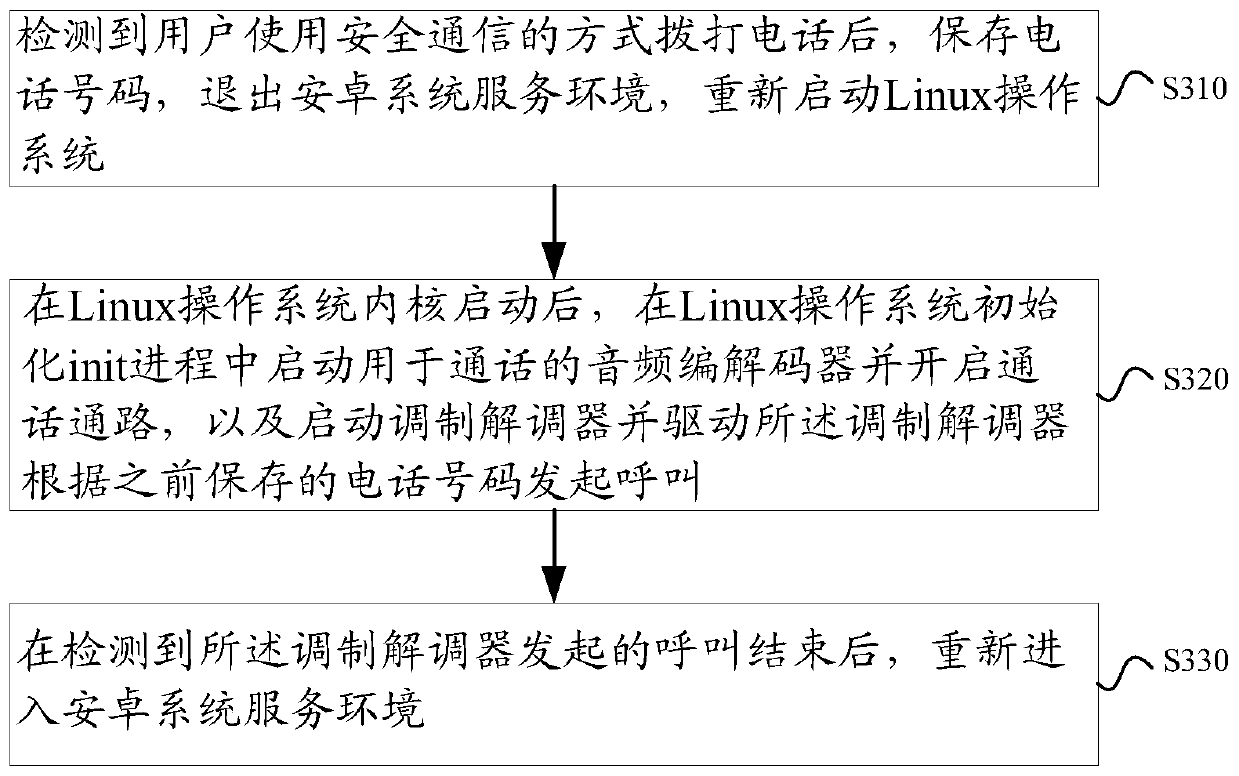
[0083] Such as Figure 5 As shown, Example 1 of the present invention provides a method for secure communication, including the following steps:
[0084] Step S501, the user instructs to make a call through a secure call method under the Android system service environment;
[0085] Wherein, on the calling interface under the service environment of the Android system, the option of a safe calling method is provided for the user to choose;
[0086] Step S502, saving the phone number, exiting the Android system service environment, and restarting the Linux operating system;
[0087] Step S503, start the Linux operating system kernel;
[0088] Step S504, use the ALSA tool to configure the sound card (audio codec);
[0089] Wherein, run custom code in the initialization init process of Linux operating system, described custom code is used for starting audio frequency codec and opening communication channel, and starts modem and drives described modem to initiate a call according...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com