Method for finding back terminal, terminal and computer-readable storage medium
A storage medium and computer technology, applied in telephone communication, electrical components, branch office equipment, etc., can solve problems such as terminal loss and difficulty in finding it
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
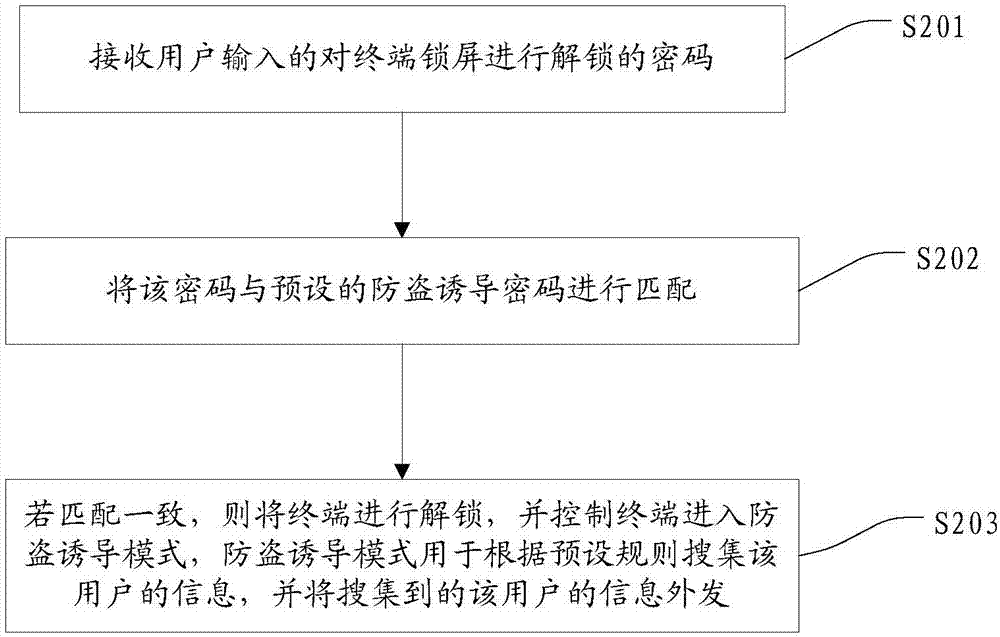
[0058] This embodiment provides a method for retrieving a terminal, see figure 2 , figure 2 A flowchart of a method for retrieving a terminal provided in this embodiment, the method for retrieving a terminal includes the following steps:
[0059] S201: Receive a password input by a user to unlock the terminal lock screen;
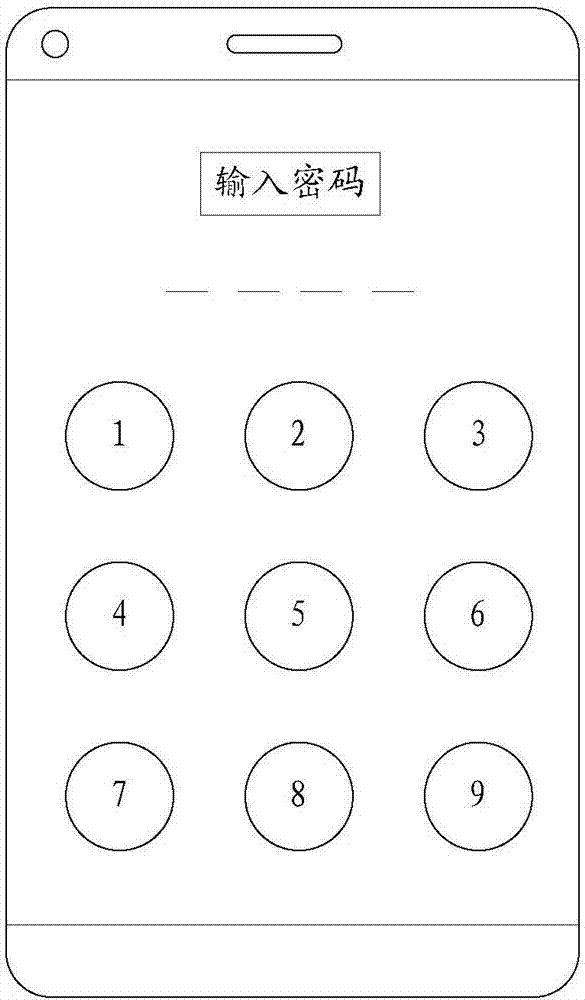
[0060] The password for unlocking the terminal lock screen can be in the form of entering a digital password, see image 3 , image 3 A schematic diagram of a terminal screen lock interface provided in this embodiment, image 3 , you need to enter a digital password to unlock;
[0061] The password for unlocking the terminal lock screen can also be in the form of a drawn pattern password, see Figure 4 , Figure 4 A schematic diagram of another terminal screen lock interface provided in this embodiment, Figure 4 , you need to draw a pattern password to unlock.
[0062] In one embodiment, after receiving the password input by the user to unlock th...
no. 2 example
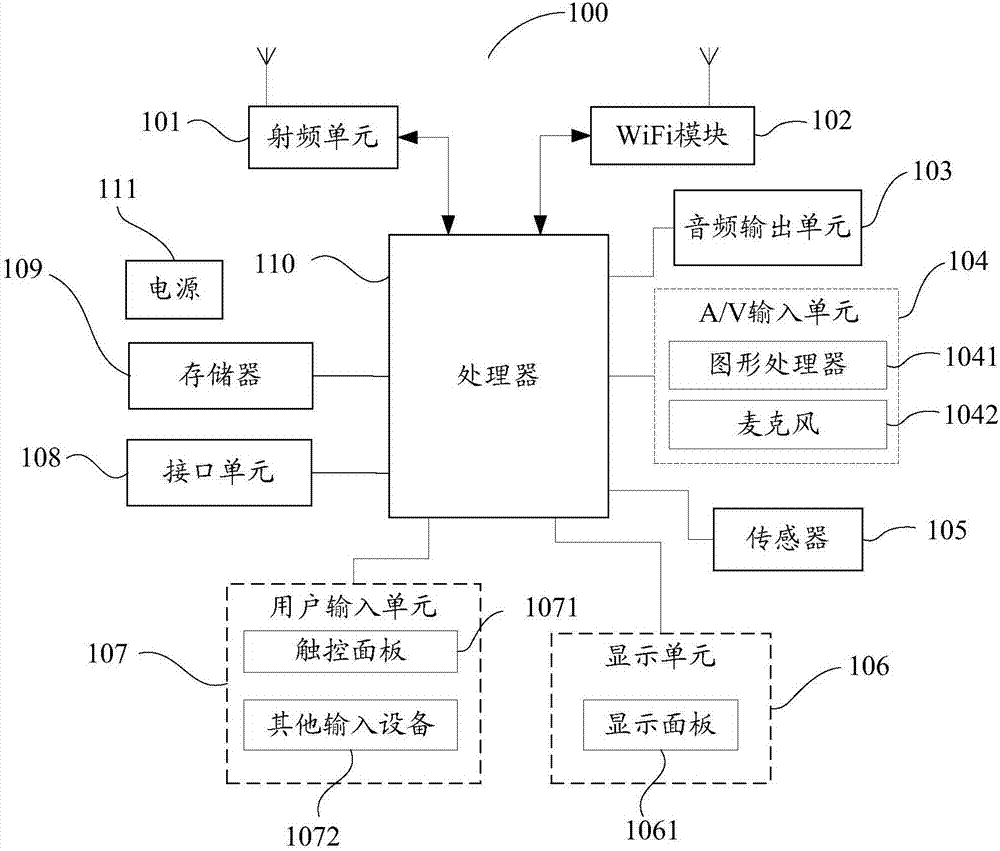
[0089] This embodiment provides a terminal, see Figure 5 , Figure 5 A schematic diagram of a terminal provided in this embodiment, the terminal includes a memory 501 and a processor 502;
[0090] The processor 502 is configured to execute the terminal retrieval program stored in the memory 501 to realize the following steps:
[0091] Receive the password entered by the user to unlock the terminal lock screen;
[0092] Match the password with the preset anti-theft inducement password;
[0093] If the matches are consistent, the terminal is unlocked, and the terminal is controlled to enter the anti-theft induction mode. The anti-theft induction mode is used to collect the user's information according to preset rules, and send the collected information of the user out.
[0094] The password for unlocking the terminal lock screen can be in the form of entering a digital password, see image 3 , image 3 A schematic diagram of a terminal screen lock interface provided in thi...
no. 3 example
[0121] This embodiment provides a computer-readable storage medium, where the computer-readable storage medium stores one or more programs, and the one or more programs can be executed by one or more processors to implement the following steps:
[0122] Receive the password entered by the user to unlock the terminal lock screen;
[0123] Match the password with the preset anti-theft inducement password;
[0124] If the matches are consistent, the terminal is unlocked, and the terminal is controlled to enter the anti-theft induction mode. The anti-theft induction mode is used to collect the user's information according to preset rules, and send the collected information of the user out.
[0125] The password for unlocking the terminal lock screen can be in the form of entering a digital password, see image 3 , image 3 A schematic diagram of a terminal screen lock interface provided in this embodiment, image 3 , you need to enter a digital password to unlock;
[0126] The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com