Call processing method and device
A call processing and call status technology, applied in the field of communication, can solve the problems of low efficiency and limited application scope of malicious voice information, and achieve the effect of reducing the possibility of being harassed and being defrauded, wide application scope, and improving prevention awareness.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0024] The malicious voice information harassment in the embodiment of the present invention may include harassing calls and false calls, and may also include other forms of voice information that harass users.
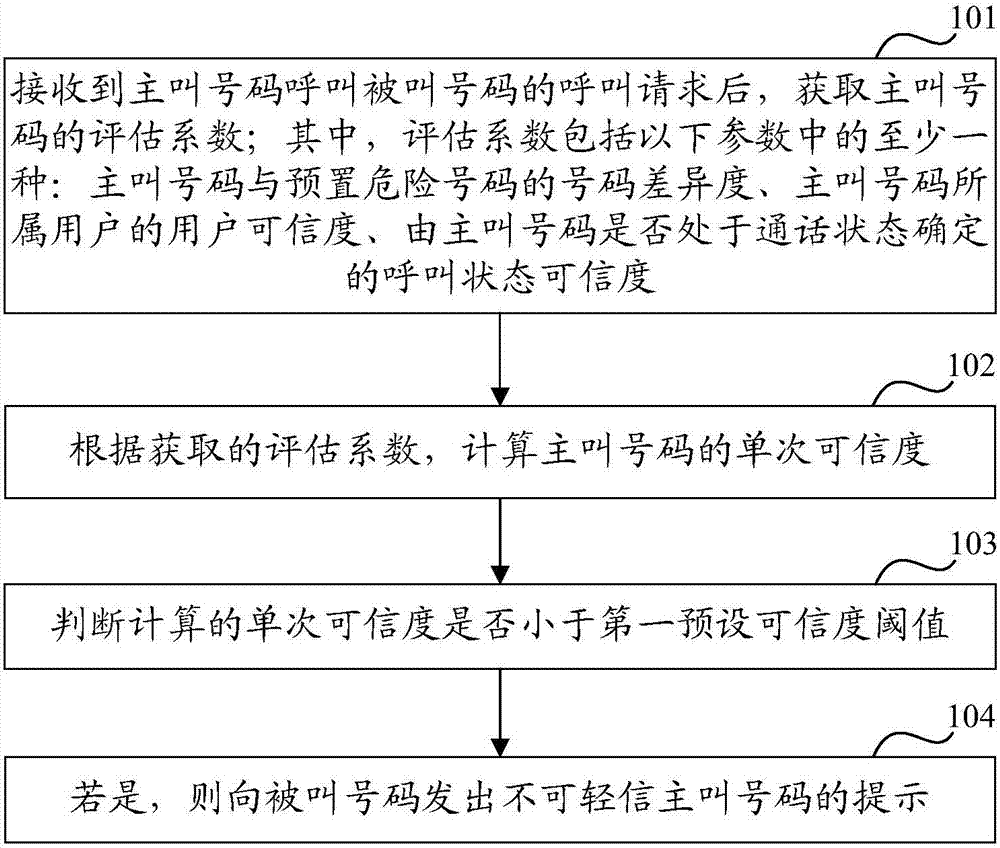
[0025] Such as figure 1 As shown, it is a schematic flowchart of the call processing method in Embodiment 1 of the present invention, and the call processing method may include the following steps:
[0026] Step 101: After receiving a call request from the calling number to call the called number, obtain the evaluation coefficient of the calling number; wherein, the evaluation coefficient includes at least one of the following parameters: the number difference between the calling number and the preset dangerous number , the user credibility of the user to which the calling number belongs, and the calling state credibility determined by whether the calling number is in a call state.
[0027] Step 102: Calculate the single reliability of the calling number according to...
Embodiment 2
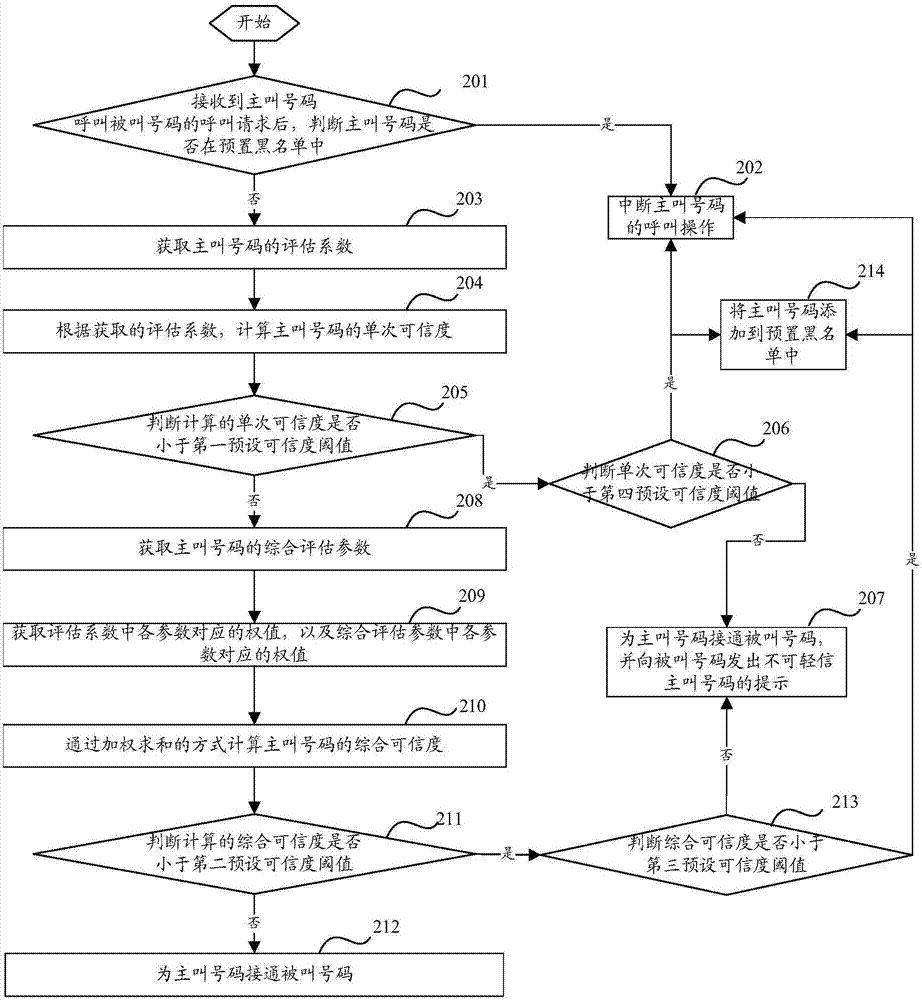
[0117] In order to further understand the call processing method provided by the embodiment of the present invention, a specific embodiment is used to describe it here, as figure 2 Shown is the schematic flow chart of this method, and this method comprises the following steps:
[0118] Step 201: After receiving a call request from the calling number to call the called number, determine whether the calling number is in the preset blacklist, if yes, go to step 202; if not, go to step 203.
[0119] Step 202: Interrupt the calling operation of the calling number.
[0120] Step 203: Obtain the evaluation coefficient of the calling number.
[0121] Step 204: Calculate the single reliability of the calling number according to the obtained evaluation coefficient.
[0122] Step 205: Judging whether the calculated single credibility is less than the first preset credibility threshold, if yes, go to step 206; if not, go to step 208:
[0123] Step 206: Determine whether the single rel...
Embodiment 3
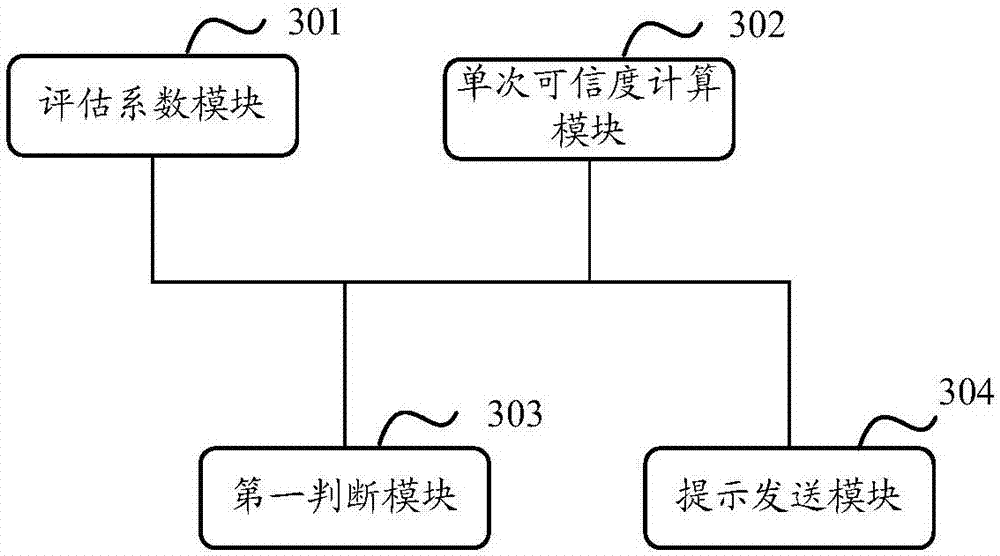
[0134] Based on the same inventive concept, the present invention also provides a call processing device, such as image 3 Shown is a schematic structural diagram of the device, including:
[0135] The evaluation coefficient module 301 is configured to obtain the evaluation coefficient of the calling number after receiving a call request from the calling number to the called number; wherein, the evaluation coefficient includes at least one of the following parameters: the calling number and the preset dangerous number The degree of number difference, the user credibility of the user to which the calling number belongs, and the credibility of the call state determined by whether the calling number is in a call state;
[0136] A single credibility calculation module 302, configured to calculate the single credibility of the calling number according to the obtained evaluation coefficient;
[0137] The first judging module 303 is used to judge whether the calculated single credib...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com