Vehicle remote monitoring warning system
A remote monitoring and alarm system technology, applied in vehicle parts, anti-theft vehicle accessories, transportation and packaging, etc., can solve the problem of inability to real-time remote anti-theft monitoring, and achieve the effect of satisfying anti-theft needs and efficient application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
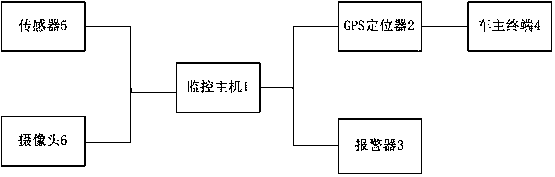
[0020] see figure 1 , a vehicle remote monitoring alarm system, comprising: a monitoring host 1, a GPS locator 2, an alarm 3, a vehicle owner terminal 4, a plurality of sensors 5 and a plurality of cameras 6; the cameras 6 are dispersedly arranged on a vehicle shell, It is used to collect image information around the vehicle; and the collected image information is sent to the monitoring host 1; the GPS locator 2 is installed inside the vehicle, and is used to obtain the acquired image information after receiving an alarm command from the monitoring host 1. The vehicle positioning data is sent to the vehicle owner terminal 4; the sensor 5 is used to collect intrusion information, and the intrusion information is sent to the monitoring host 1; the monitoring host 1 is installed inside the vehicle and is used to monitor the images respectively Information and intrusion information are judged, if judge vehicle is invaded according to described image information and intrusion infor...
Embodiment 2
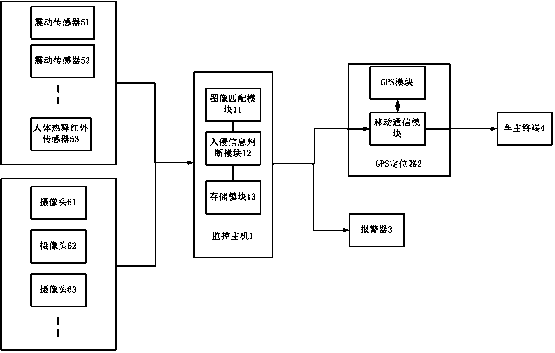
[0023] see figure 2 , a vehicle remote monitoring alarm system, including: a monitoring host 1, a GPS locator 2, an alarm 3, a vehicle owner terminal 4, multiple sensors 51, 52, 53... and multiple cameras 61, 62, 63.. .; The cameras 61, 62, 63... are dispersedly arranged on the outer shell of the vehicle, and are used to collect image information around the vehicle; and send the collected image information to the monitoring host 1; the GPS locator 2, Installed inside the vehicle, it is used to send the obtained vehicle positioning data to the vehicle owner terminal 4 after receiving an alarm command from the monitoring host 1; the sensors 51, 52, 53... are used to collect intrusion information, and send The intrusion information is sent to the monitoring host 1; the monitoring host 1 is installed inside the vehicle and is used to judge the image information and the intrusion information respectively. If it is judged that the vehicle has been invaded according to the image inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com