Hevc Video Data Hiding Method in Encrypted Domain Based on Residual Coefficient Modulation
A technology of video data and residual coefficients, which is used in digital video signal modification, image communication, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
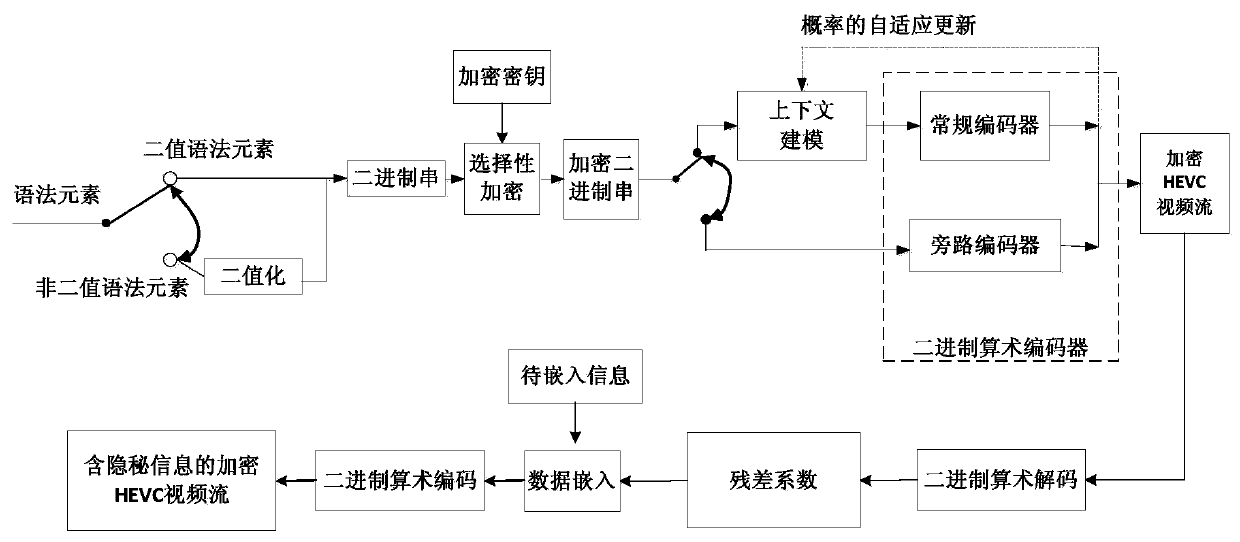
[0108] This embodiment proposes a method for hiding HEVC video data in an encrypted domain based on residual coefficient modulation, which includes three parts: HEVC video encryption, HEVC video data hiding in the encrypted domain, and secret data extraction.
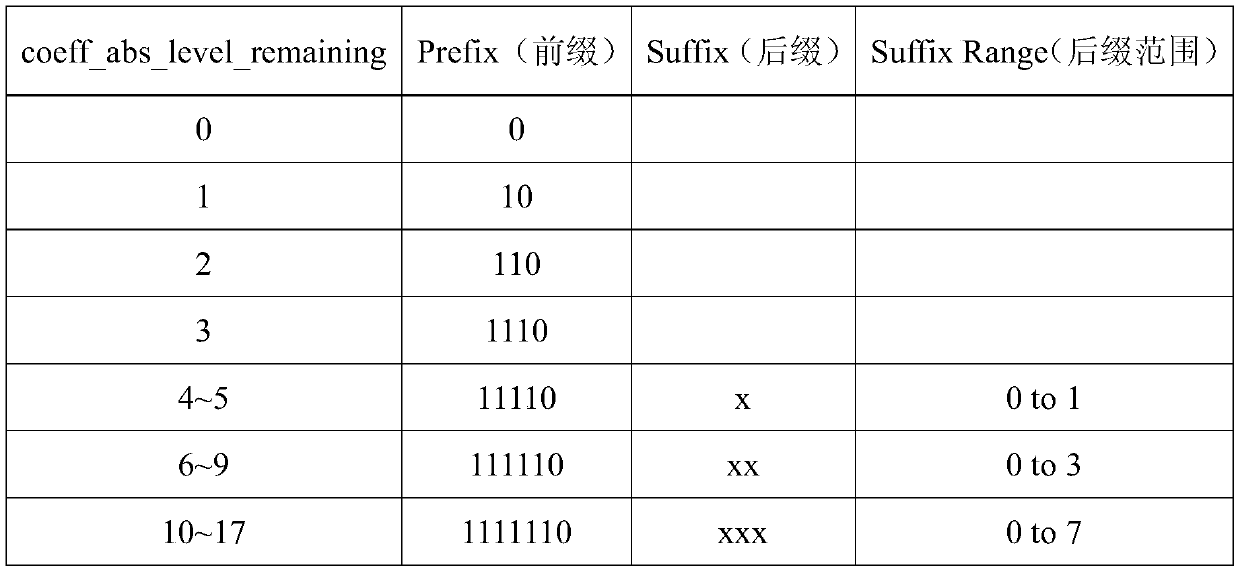
[0109] In this specific embodiment, in order to reduce the computational complexity, keep the code rate of the encrypted HEVC video code stream unchanged, and have high perceptual security, the method of the present invention selects the motion vector difference (MVD) symbol The CABAC binary string (bin string) and the CABAC binary string of the quantized residual coefficient sign are encrypted, such as Figure 1a As shown, the HEVC video encryption process is as follows: For the original HEVC video, for all macroblocks whose prediction mode is inter prediction mode and whose motion vector difference is not 0, use the binary pseudo-random sequence pair generated by the first key The CABAC binary string of the motion vect...
Embodiment 2
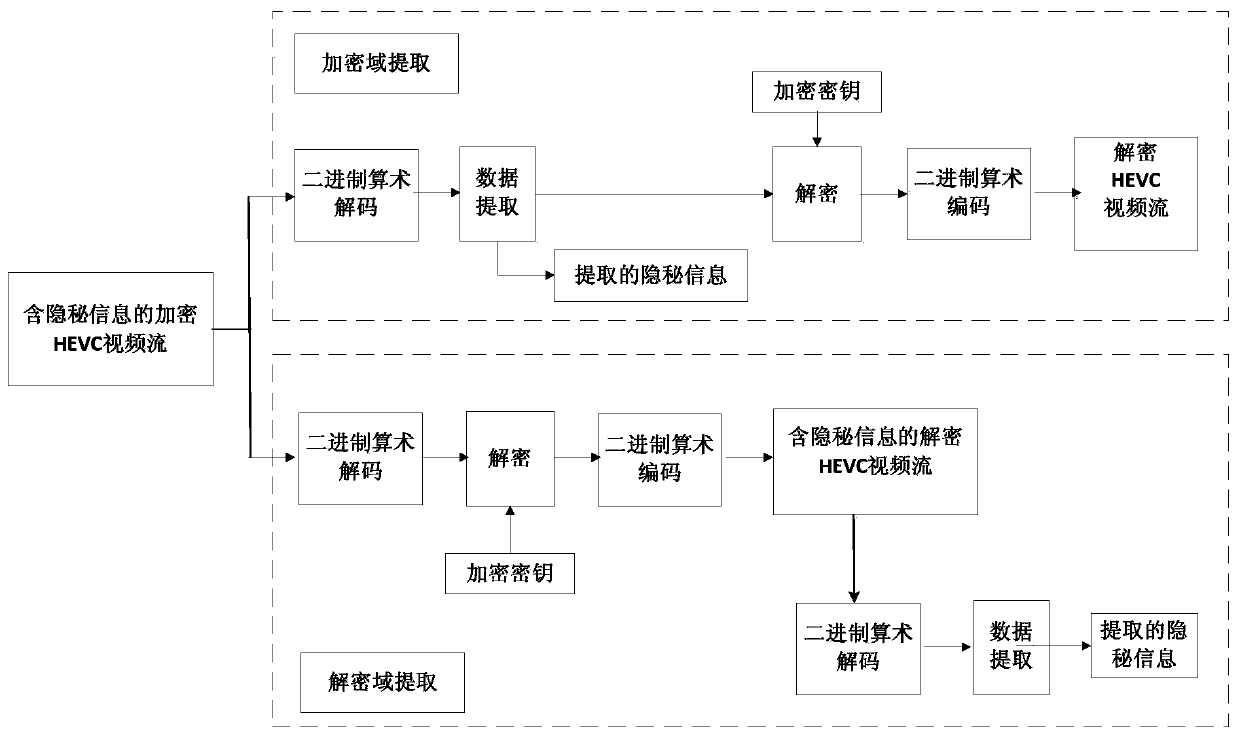
[0190] A method for hiding HEVC video data in an encrypted domain based on residual coefficient modulation proposed in this embodiment includes three parts: HEVC video encryption, HEVC video data hiding in the encrypted domain, and secret data extraction, wherein HEVC video encryption and HEVC in the encrypted domain The two parts of video data hiding are the same as the HEVC video encryption in the first embodiment and the two parts of the HEVC video data hiding in the encrypted domain are correspondingly the same, but the secret data extraction part of this embodiment is different from the secret data extraction of the first embodiment. The secret data extraction of the above is completed in the encrypted domain, and the secret data extraction in this embodiment is completed in the decrypted domain. In some cases, the user needs to decrypt the encrypted video first, and then extract the secret information from the decrypted video. ) authorized users receive encrypted videos ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com