Encryption domain H.264/AVC video data hiding method based on MVD (Motion Vector Difference) codon mapping
A technology of video data and encryption domain, applied in the direction of digital video signal modification, electrical components, image communication, etc., can solve problems such as technical failure and loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
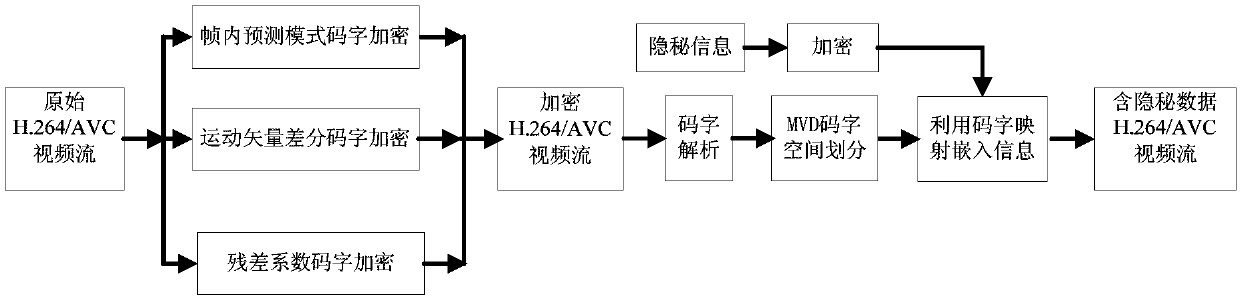
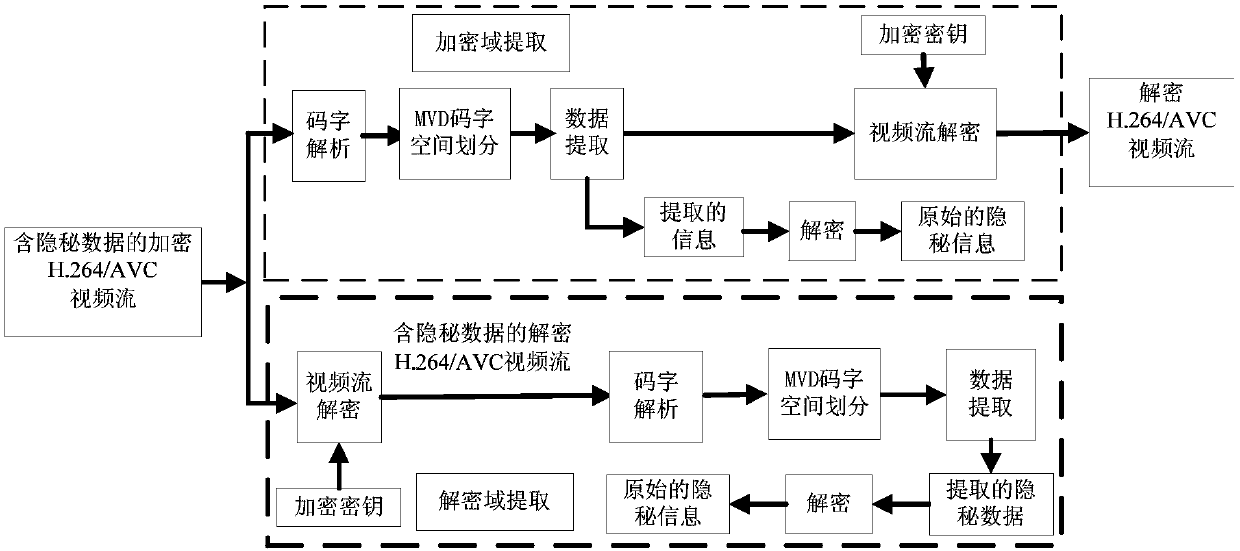
[0067] A method for hiding H.264 / AVC video data in encrypted domain based on MVD codeword mapping proposed in this embodiment, which includes H.264 / AVC video encryption, hidden information embedding in encrypted domain H.264 / AVC video, hidden information There are three parts to extract, among which, secret information extraction and video decryption are completely separable, and secret information can be extracted before video decryption or after video decryption.
[0068] In order to reduce the encryption complexity, keep the size of the encrypted domain H.264 / AVC video code stream obtained after encryption unchanged, and have high perceptual security, the method of the present invention selects the intra prediction mode (IPM), motion vector The difference (MVD) and residual coefficients are encrypted, that is, as Figure 1a As shown, the H.264 / AVC video encryption process is as follows: For all macroblocks whose prediction mode is Intra_4×4 prediction mode in the original H....
Embodiment 2
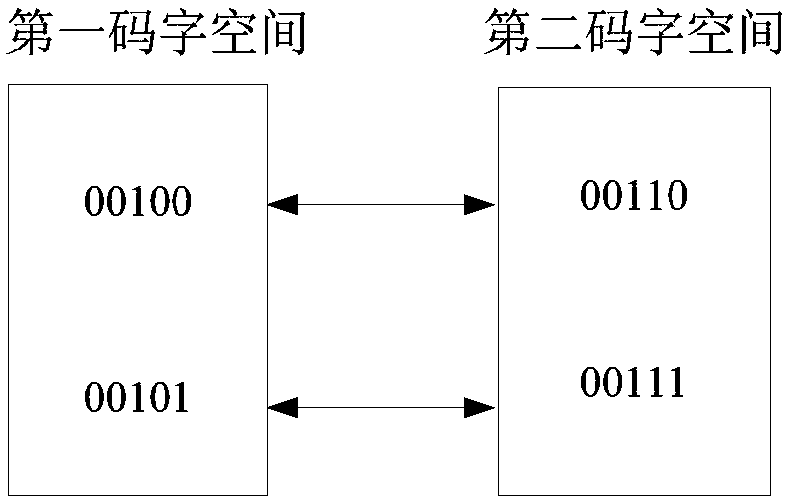
[0124] The encryption domain H.264 / AVC video data hiding method proposed in this embodiment is proposed on the basis of Embodiment 1 in order to further improve security. In order to prevent secret information from being extracted and leaked, encryption is first used in step ②_3. The binary pseudo-random sequence of the secret information encrypts the secret information to be embedded, and then re-uses the encrypted secret information as the secret information to be embedded, and then takes out the current information bits to be embedded; in this way, when extracting the secret data, it needs to extract The obtained secret information is decrypted, that is, in step ③_1e, the binary pseudo-random sequence of the encrypted secret information used in the H.264 / AVC video data hiding process of the encrypted domain is used to decrypt the extracted secret information; in step ③_2f, use In the H.264 / AVC video data hiding process in the encrypted domain, the binary pseudo-random sequen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com