A HEVC video encryption and decryption method
An encryption method and video technology, applied in the field of video encryption and decryption, can solve the problems of few research results and the inability to fully apply the encryption scheme.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
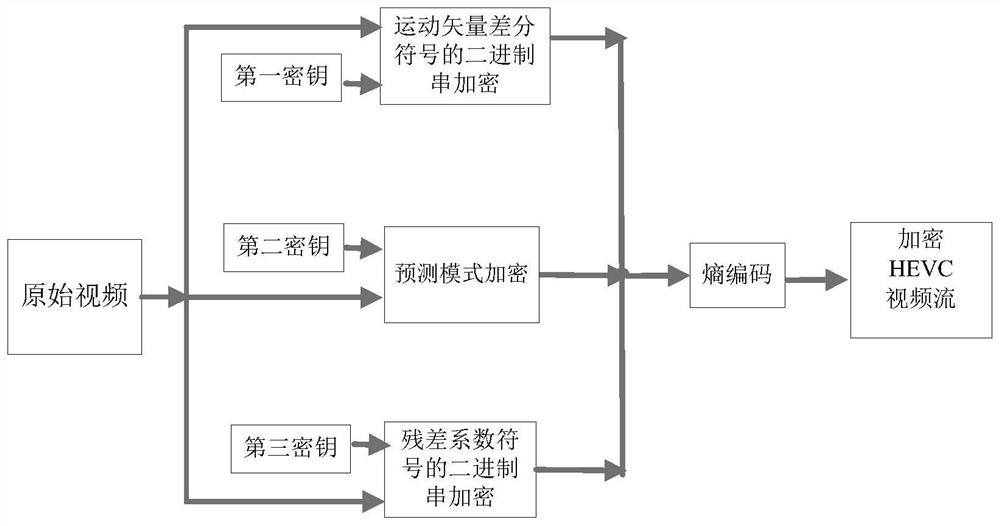
[0055] A kind of HEVC video encryption method that this embodiment proposes, it is to reduce computational complexity, and guarantee high perceptual security, keep the code rate change of the HEVC video code stream after the encryption at the same time little, choose motion vector difference (MVD ) symbol of the CABAC binary string (bin string), prediction mode, and the CABAC binary string of the quantized residual coefficient symbol for encryption, such as figure 1 As shown, the processing procedure of the HEVC video encryption method is: for the original HEVC video, for all macroblocks whose prediction mode is the inter prediction mode and whose motion vector difference is not 0, use the binary pseudo-random The sequence performs bit XOR encryption on the CABAC binary string of the motion vector difference sign of the macroblock to complete the encryption of the motion vector difference of the macroblock; for all macroblocks whose prediction mode is inter-frame prediction mod...
Embodiment 2
[0083] This embodiment proposes a HEVC video decryption method corresponding to the HEVC video encryption method proposed in Embodiment 1. The processing process is: for the encrypted HEVC video, partially decode the encrypted HEVC video, and decode to obtain all encrypted motion Vector difference, all encrypted prediction modes, all encrypted quantized residual coefficients; for all encrypted motion vector differences, use the binary pseudo-random sequence generated by the first key to compare the CABAC binary string of the encrypted motion vector difference symbol Specific or decryption, to complete the decryption of the encrypted motion vector difference; for all encrypted prediction modes, use the binary pseudo-random sequence generated by the second key to decrypt the encrypted prediction mode; for all encrypted quantized residual coefficients, use The binary pseudo-random sequence generated by the third key performs bit XOR decryption on the CABAC binary string of the enc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com