Method and device for setting risk control score card
A scoring card and risk control technology, applied in the Internet field, can solve the problems of not being able to reflect the real risk level of user access behaviors, repeated accumulation of scores, and a large proportion of similar rules, so as to achieve the effect of avoiding the real risk level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
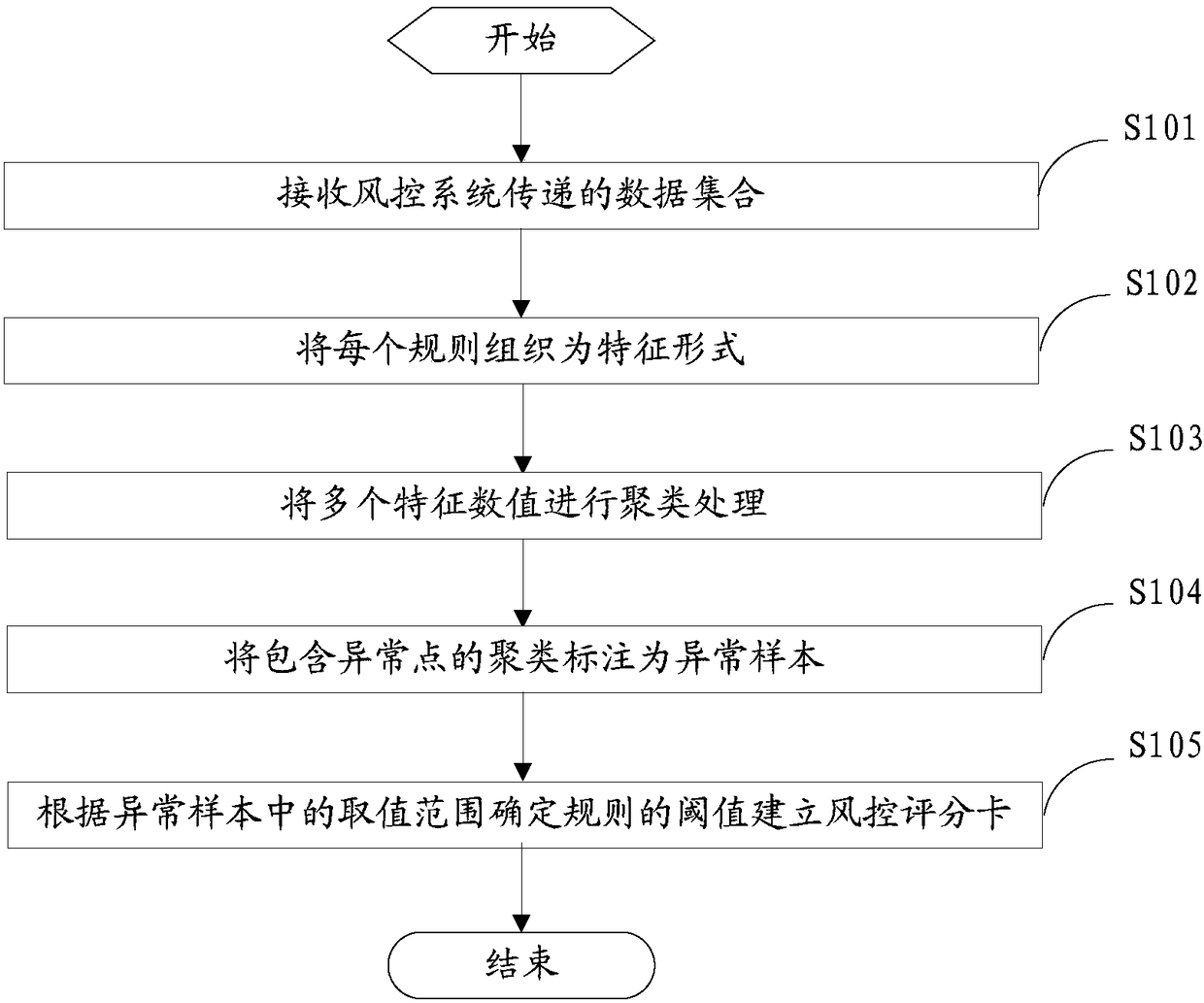
[0048] figure 1 It is a flowchart of steps of a method for setting a risk control scorecard provided by an embodiment of the present invention.
[0049] refer to figure 1 As shown, the setting method of the risk control scorecard provided by this embodiment is applied to the risk control system of the website, and the risk control system is used to detect the nature of user access behaviors imported from the business system to avoid damage to the website caused by dangerous behaviors . This setting method is used to set the risk control scorecard required by the rule engine of the risk control system to detect user access behavior. The setting method specifically includes steps:
[0050] S101: Receive the data set delivered by the wind control system.
[0051] This data set comes from the results obtained by the wind control system through processing the log files of the website. Device id, device fingerprint, etc. Correspondingly, a corresponding rule name can be configu...
Embodiment 2
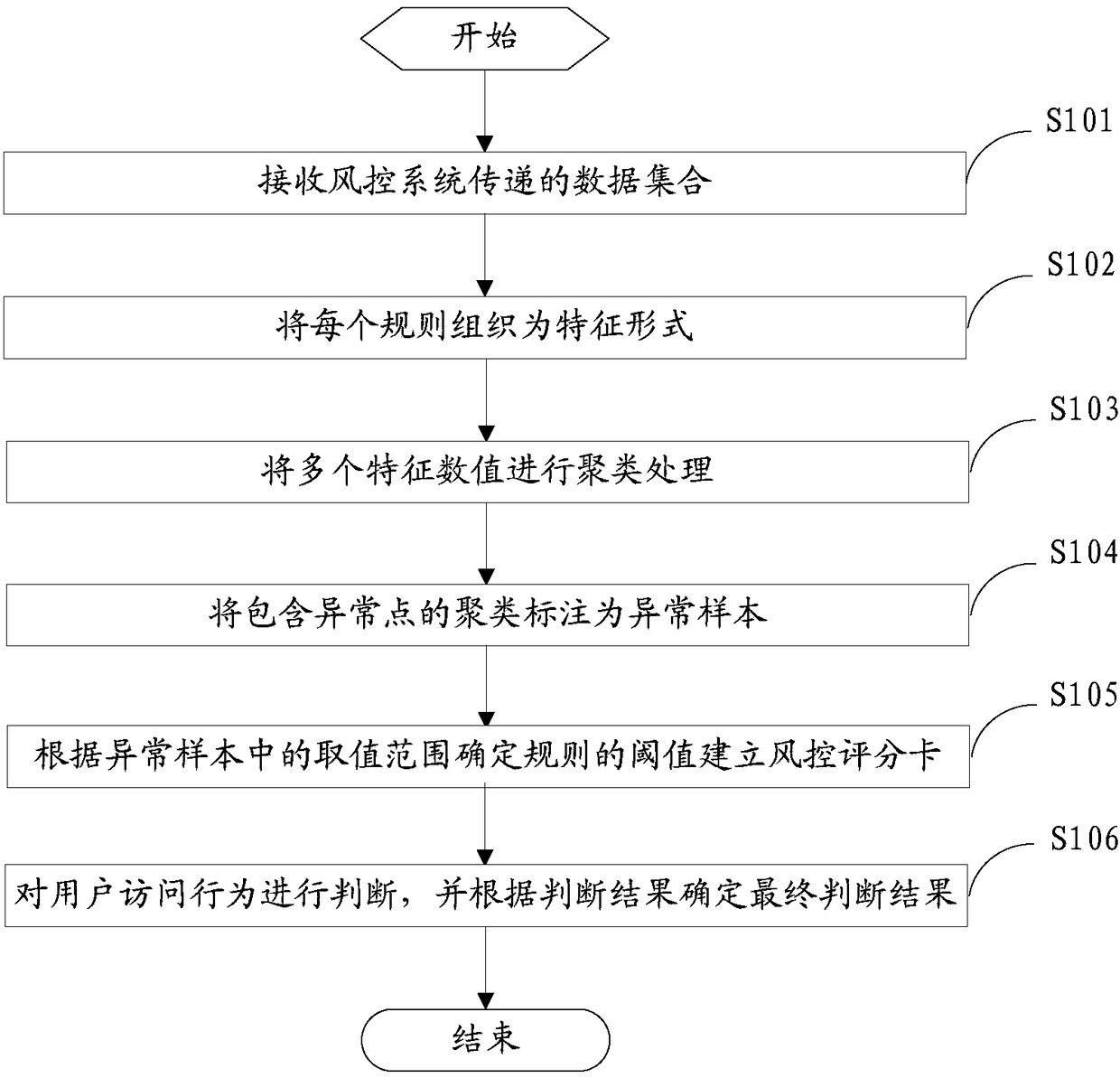
[0081] Figure 4 A final structural block diagram of a risk control scorecard provided by an embodiment of the present invention.
[0082] refer to Figure 4 As shown, the setting of the risk control scorecard provided by this embodiment is finally applied to the risk control system of the website. The risk control system is used to detect the nature of user access behaviors imported from the business system, and to avoid damage to the website caused by dangerous behaviors. . This setting method is used to set the risk control scorecard required by the rule engine of the risk control system to detect user access behavior. The setting device specifically includes a data receiving module 10 , a feature organizing module 20 , a cluster processing module 30 , a cluster labeling module 40 and a scorecard output module 60 .
[0083] The data receiving module is used to receive the data set delivered by the wind control system.
[0084] This data set comes from the results obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com