Implementation method for isomerizing function-equivalent executers
An implementation method and technology for implementing bodies, applied in the field of network security, can solve problems such as difficulties, complex functions and structures of executive bodies, and difficulty in constructing heterogeneous executive bodies with equivalent functions, so as to achieve a wide range of applications and reduce the cost of implementation of isomerization. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
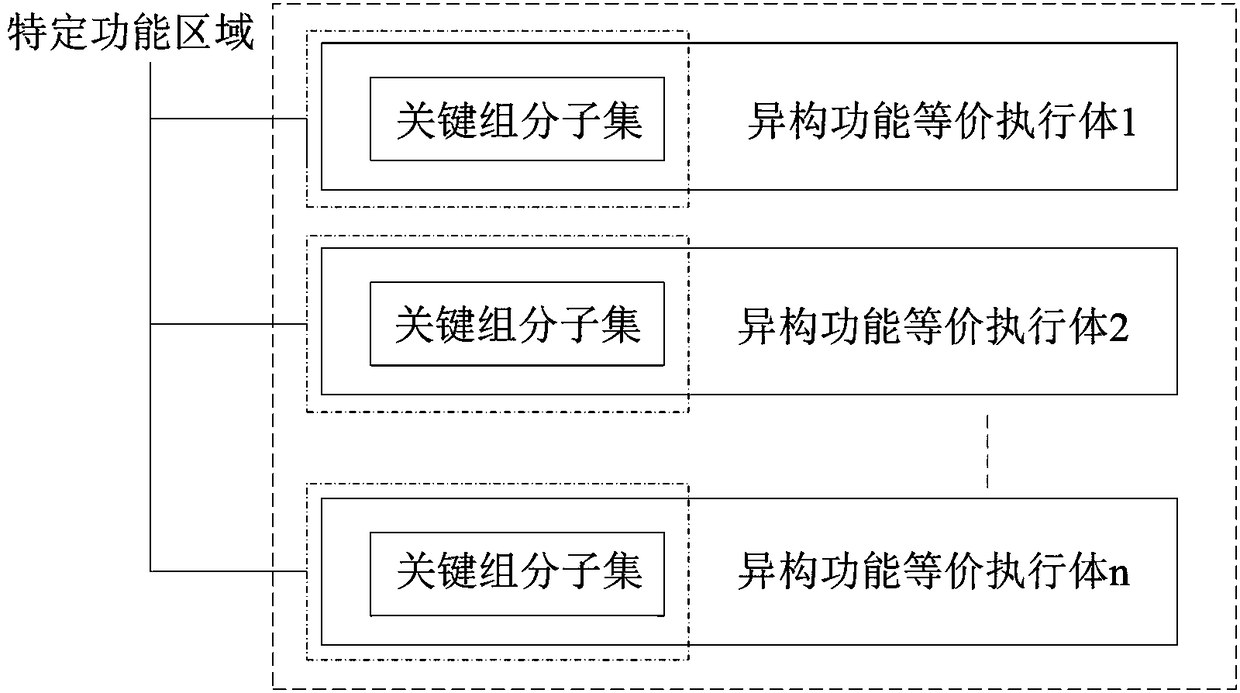
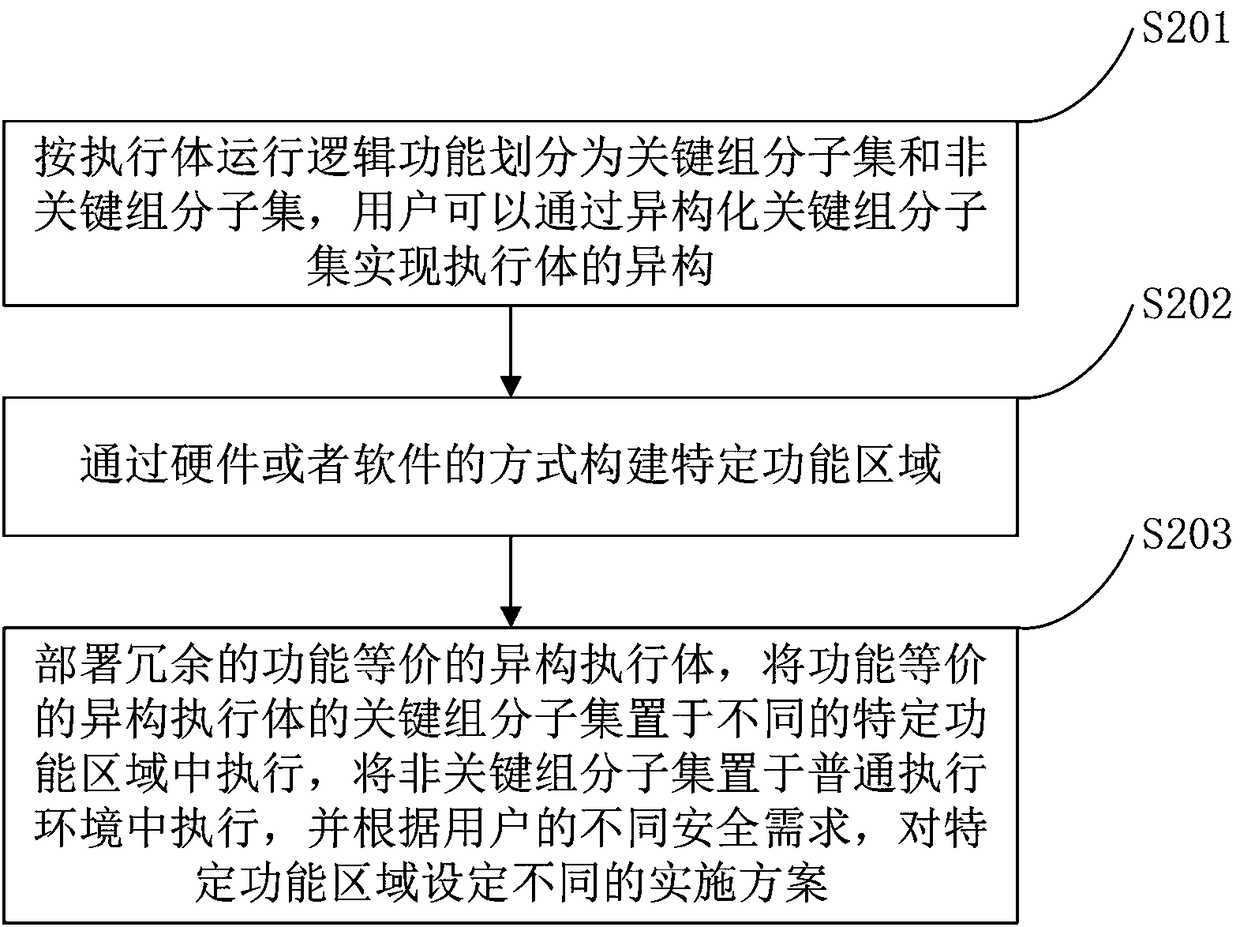
[0027] Embodiment one, such as figure 1 and figure 2 As shown, this embodiment provides a method for implementing heterogeneous functionally equivalent executives, the method including:
[0028] Step S201, according to the operation logic function of the executive body, it is divided into key group subsets and non-key group subsets, and the user can realize the heterogeneity of the executive bodies by isomerizing the key group subsets;
[0029] Preferably, the elements of the key group subset are core components hidden in the executive body or added to the executive body and do not affect the functional components of the executive body; the key group subsets are under the condition that they are not modified , which cannot be bypassed in the running logic of the execution body where it is located.
[0030] It can be understood that the elements of the key group subset may be key nodes in the data flow diagram of the executive, or a necessary condition for triggering the key...
Embodiment 2
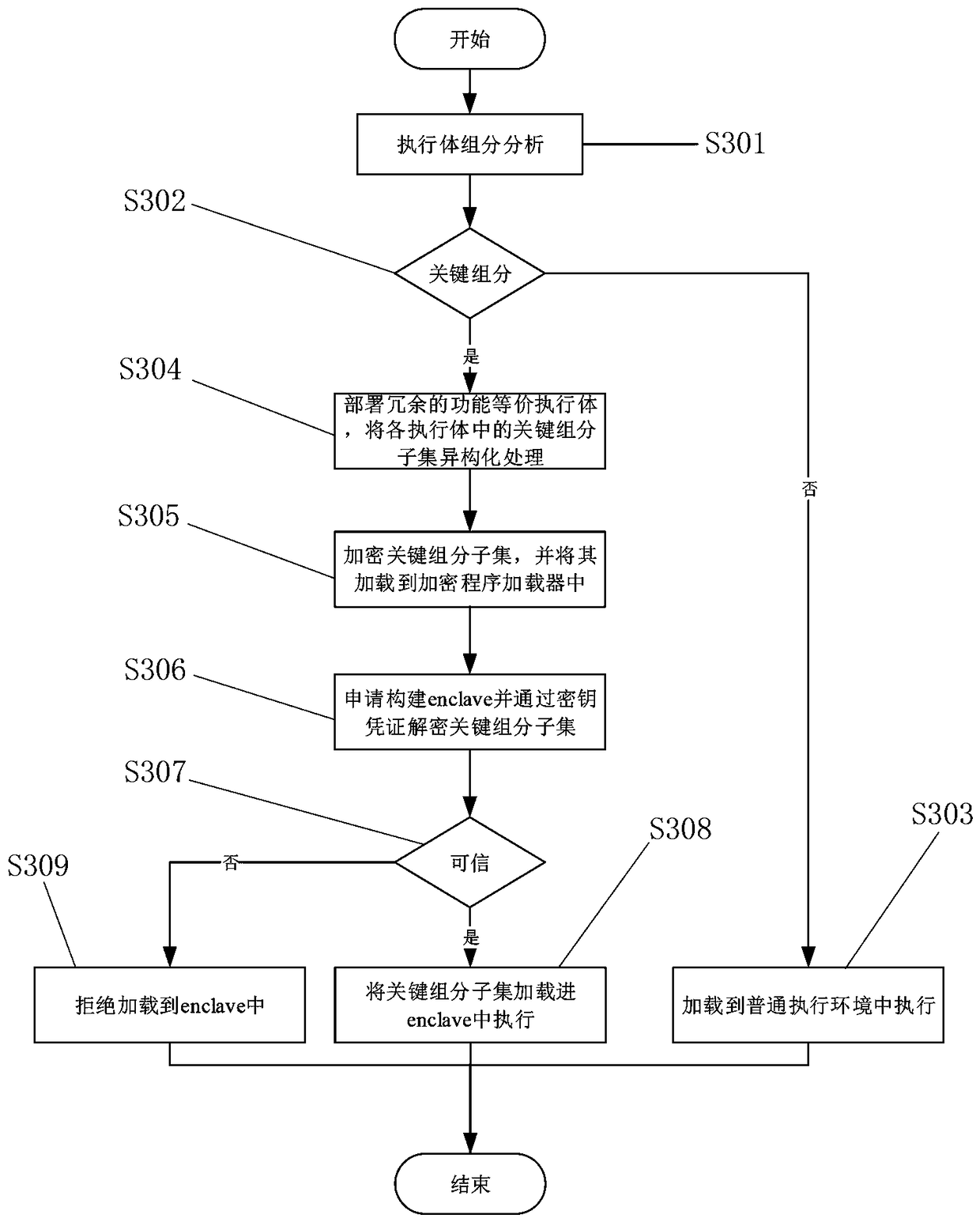
[0040] Embodiment two, such as image 3 As shown, a SGX-based implementation method for heterogeneous functional equivalent executives includes the following steps:
[0041]Step S301, perform modeling and abstraction according to the logic function of the executive body, and analyze and obtain the key group subset according to the principle of minimizing the key group subset. The elements in the key group subset can be the key modules of the internally extracted executive logic. , or add a module that does not affect its normal function at the external IO interface of the executive body;
[0042] Step S302, judge the component category of the executable, if it is a non-key group subset, go to step S303, if it is a key group subset, go to step S304;
[0043] Step S303, executing its elements in a common execution environment;
[0044] Step S304, deploy redundant functionally equivalent executives, and isomerize the key component subsets in each executive;
[0045] Step S305,...
Embodiment 3
[0050] Embodiment three, such as Figure 4 As shown, a heterogeneous function equivalent execution method based on CPU+heterogeneous computing platform includes the following steps:
[0051] Step S401: Carry out modeling and abstraction according to the logic function of the executive body, and analyze and obtain the key group subset according to the principle of minimizing the key group subset. The elements in the key group subset can be the key modules of the internally extracted executive logic. , or add a module that does not affect its normal function at the external IO interface of the executive body;
[0052] Step S402, judge the component category of the executable, if it is a non-key group subset, go to step S403, if it is a key group subset, go to step S404;
[0053] Step S403, executing its elements in a common execution environment;
[0054] Step S404, deploy redundant functionally equivalent executives, and isomerize the key component subsets in each executive; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com