Image scrambling method of two-dimensional mapping groups
An image scrambling and image technology, applied in the field of information security, can solve the problem of mapping characteristics, affecting the encryption effect, and the key space is not large, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
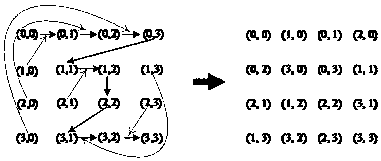
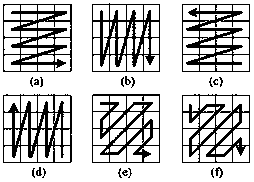
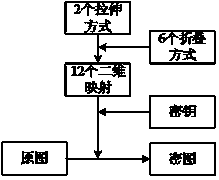
[0095] Two-dimensional mapping principles and examples are as figure 1 , 2 Shown. Regarding the image as an array, the principle of mapping is to sequentially insert the image column pixels into two pixels in the corresponding row from two directions to stretch the image. Repeat the process and connect sequentially, the original image is stretched into a long N 2 Straight line.
[0096] figure 2 Take a 4×4 picture as an example. First, insert the pixels in the first column from left to right between the pixels in the first row from top to bottom, such as (1,0) inserted between (0,0), (0,1), (2, 0) Insert between (0,1) and (0,2), (3,0) between (0,2) and (0,3), and then insert the pixels in the first column from right to left To the pixels in the first row from bottom to top, that is, (2,3) is inserted between (3,2) and (3,3), (1,3) is inserted into (3,1), Between (3,2)... Repeat the above process, the original image is stretched into a straight line of pixels: (0,0), (1,0), ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com