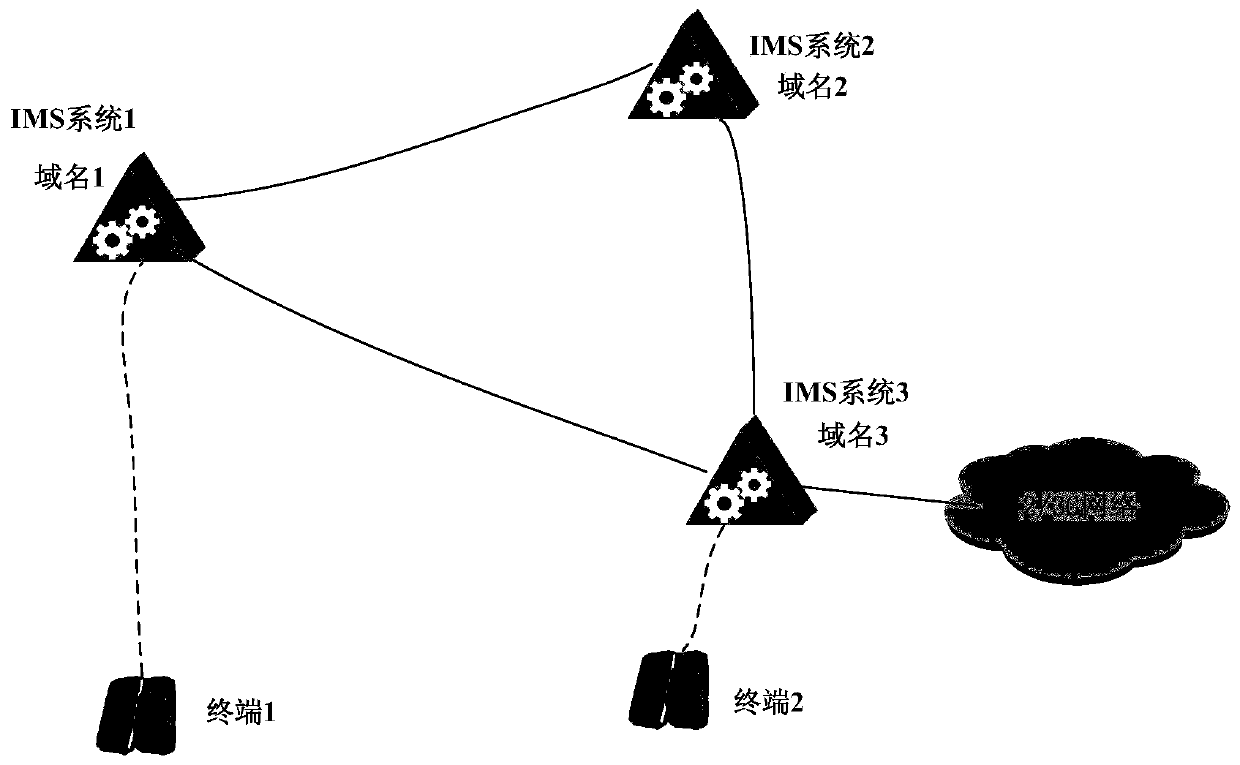
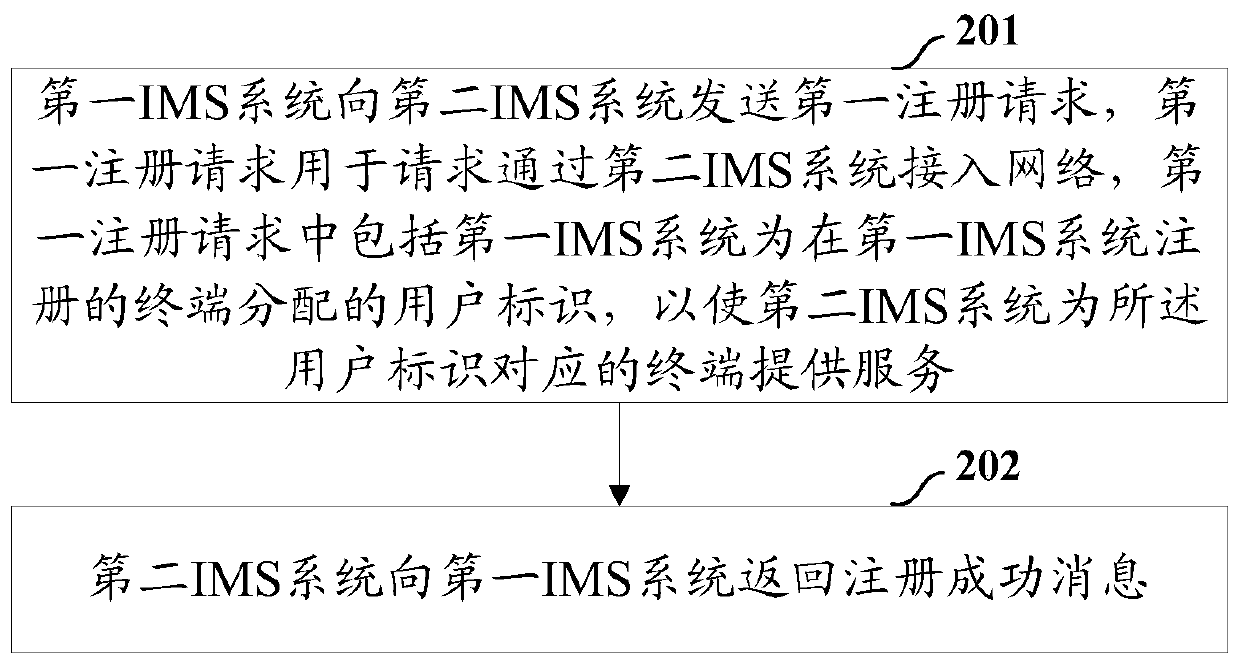
A kind of ims cascade networking method and equipment
A technology for accessing a network and a terminal, which is applied in the field of IMS cascade networking methods and equipment, and can solve the problems of heavy workload, tediousness, and expensive gateway equipment for reconfiguring routing information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
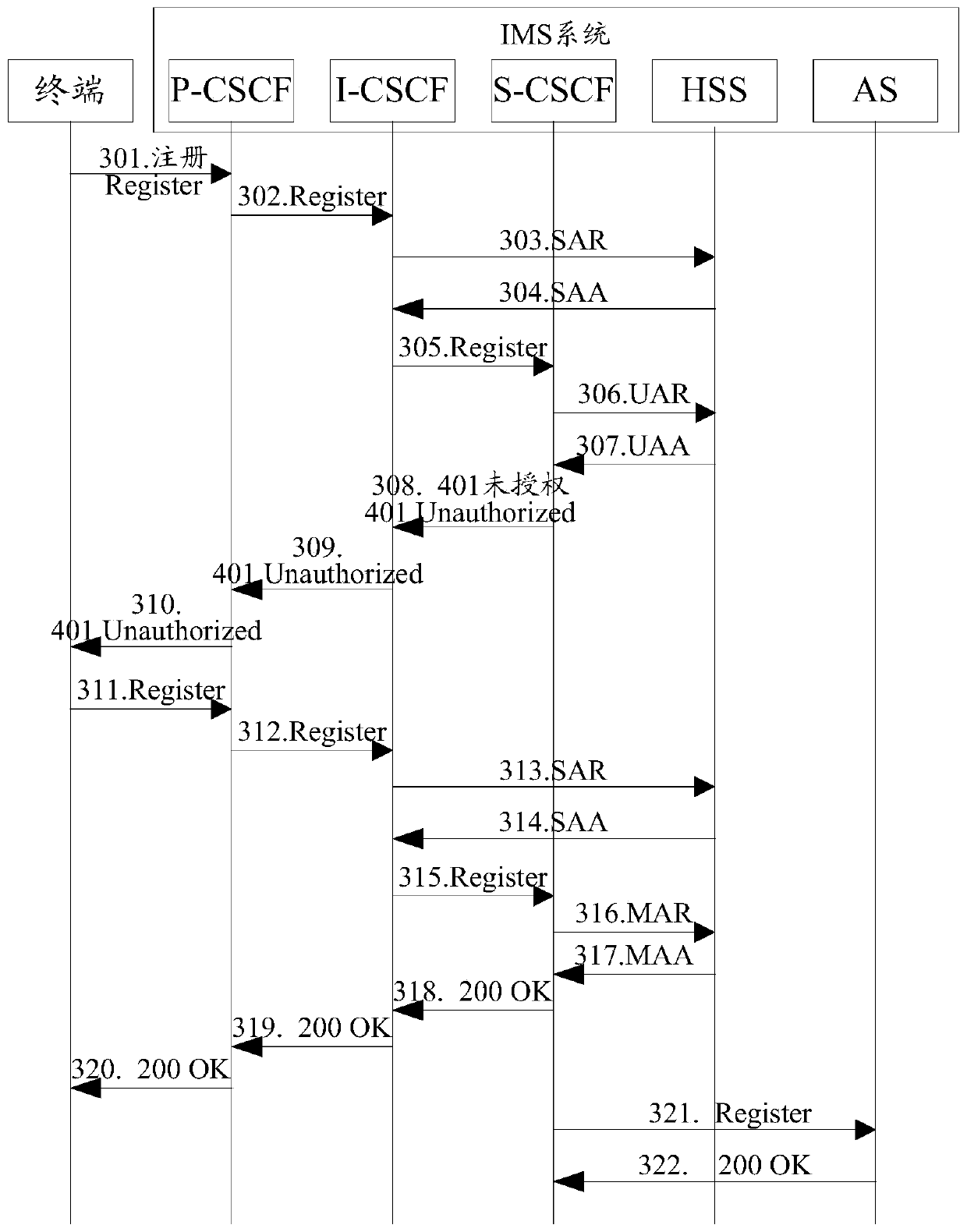
[0103] Embodiment 1. When a terminal is registered in both the first IMS system and the second IMS system, the added field in the UAA can control whether to perform authentication and encryption.
[0104] The first IMS system and the second IMS system can execute as Figure 4 The steps shown:
[0105] Step 401: The terminal sends Register to the P-CSCF in the first IMS system.
[0106] Step 402: The P-CSCF in the first IMS system determines the address of the I-CSCF in the first IMS system according to the home domain name of the terminal, and sends the Register to the I-CSCF.
[0107] Step 403: After receiving the Register, the I-CSCF in the first IMS system sends a SAR to the HSS in the first IMS system to query the address of the S-CSCF in the first IMS system.
[0108] Step 404: The HSS in the first IMS system carries the address of the S-CSCF in the SAA and sends it to the I-CSCF in the first IMS system.
[0109] Step 405: The I-CSCF in the first IMS system sends the Register to the...
Embodiment 2
[0120] Embodiment 2. The terminal needs to perform authentication and encryption when registering in the first IMS system, and when registering in the second IMS system, it can be controlled not to perform authentication and encryption by a field added in the UAA.
[0121] After the terminal completes registration in the first IMS system according to the above steps 301 to 322, the first IMS system and the second IMS system can perform the following Figure 5 The steps shown:
[0122] Step 501: The S-CSCF in the first IMS system sends the Register of the terminal to the P-CSCF in the second IMS system.
[0123] Wherein, when the S-CSCF in the first IMS system sends the Register, it needs to modify the home domain name in the original Register to the home domain name of the second IMS system.
[0124] Step 502: The P-CSCF in the second IMS system determines the address of the I-CSCF in the second IMS system according to the home domain name in the Register, and sends the REGISTER to the...
Embodiment 3
[0135] Embodiment 3. The terminal needs to perform authentication encryption when registering in the first IMS system. When registering in the second IMS system, the added field in the UAA can control authentication not encryption.
[0136] After the terminal is registered in the first IMS system, the terminal, the first IMS system, and the second IMS system can perform such as Image 6 The steps shown:
[0137] Step 601 to step 606 are consistent with the above step 501 to step 506, and will not be described again.
[0138] Step 607: The HSS in the second IMS system returns the authentication information to the S-CSCF in the second IMS system through the UAA, where the value of the bit corresponding to the Authorization-Indication field in the UAA is 0, which indicates to initiate authentication. However, the value of the bit corresponding to the SA-Indication field in the UAA is 1, that is, no encryption is required.
[0139] Step 608: The S-CSCF in the second IMS system sends a "40...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com