System and method for performing voice encryption communication between communication terminals
A communication terminal, voice encryption technology, applied in voice analysis, wireless communication, short-distance communication services, etc., can solve the problem that the receiving end cannot be properly demodulated, weakened and cut off processing, etc., to reduce complexity and cost, and reduce communication errors. bit rate effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
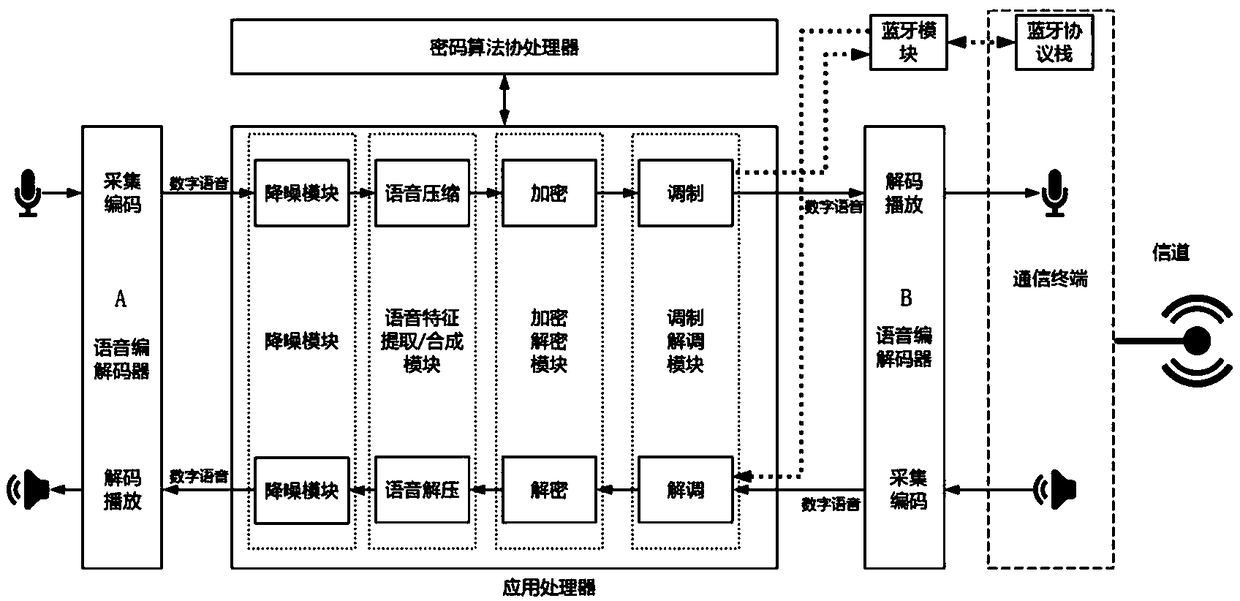
[0043] This embodiment provides a voice encryption communication system between communication terminals, such as figure 1 , the mobile terminal has audio interfaces such as Bluetooth audio interface or 3.5mm analog audio interface or TYPE-C audio interface or Lightning audio interface, and the voice encryption communication system is set on the mobile terminal, including:
[0044] Speech coder (CODEC) A: converts the analog audio signal collected by the microphone into an audio data stream, and transmits the data to the application processor through the I2S interface after encoding. The audio data stream sent by the application processor is received through the I2S interface, and after decoding, the audio data stream is converted into an analog audio signal and sent to the speaker for playback.
[0045] Speech coder (CODEC) B: Receive the modulated data stream through the I2S interface, decode it into an analog audio signal, and send the decoded analog signal to the communicat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com