A social media individual abnormal user detection method based on the evolution of self-network structure
A social media and network structure technology, applied in the field of social media individual abnormal user detection based on the evolution of the self-network structure, can solve the problems of abnormal false positives, regardless of interaction, and the inability to judge whether two users interact one-way or two-way, and achieve The effect of avoiding abnormal false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be further described below in conjunction with the accompanying drawings.
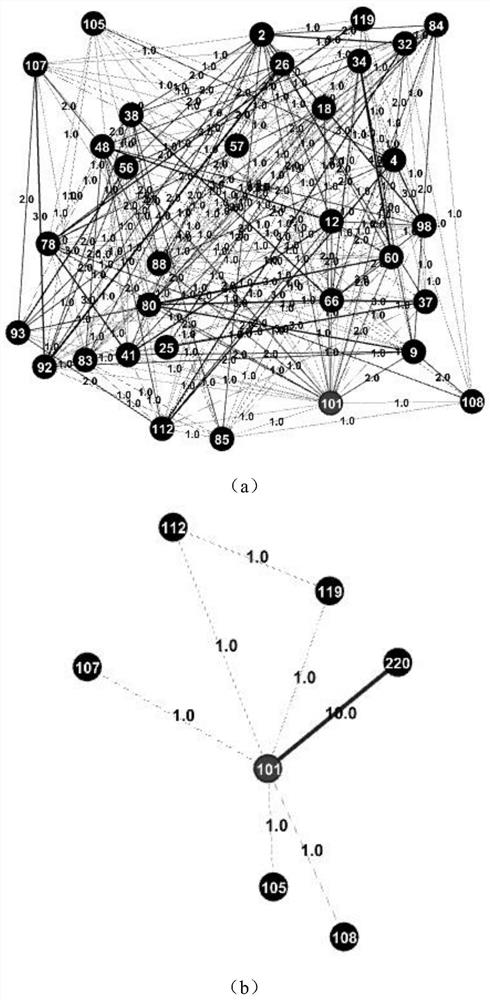
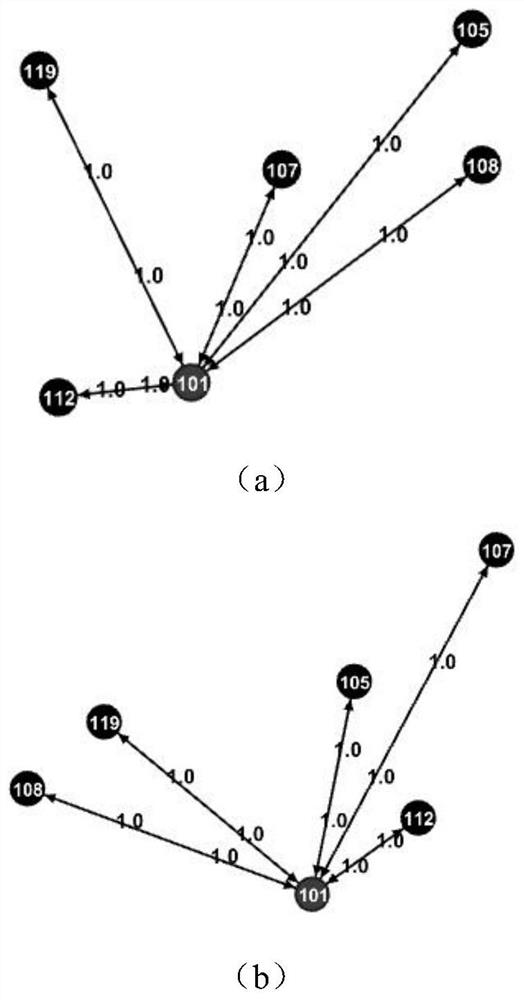
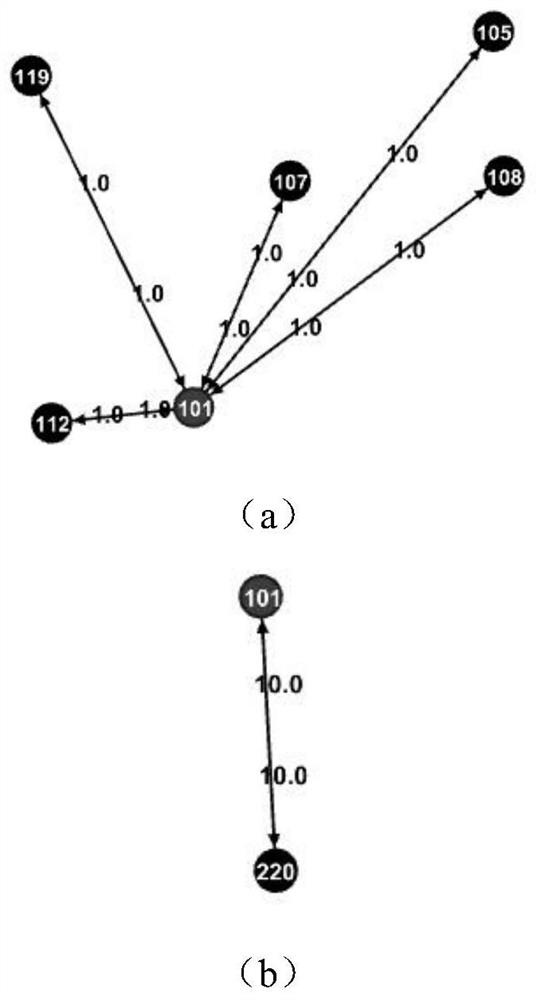
[0043] 1. Express the social media user interaction state at time T as a directed weighted graph G T =(V,E,W), where V represents a collection of vertices, and the vertices are used to represent users. Represents an edge set composed of a set of vertices, and an edge is used to indicate whether there is an interactive relationship between users, such as two nodes v i ,v j ∈V, if there exists a i point to v j The directed edge of , then it means v i to v j Initiate a one-way interaction. W represents the weight of the edge, and the weight is used to represent the number of one-way interactions between users.
[0044] 2. Construct a set of suspicious abnormal nodes SAN-Set(T)
[0045] (1) By comparing the snapshot G T-1 and G T To identify the time-varying component, Table 1 describes the meaning and related symbols of the time-varying component.
[0046] Tab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com