Suspicious feature discovery method based on transaction network nodes
A technology for trading networks, discovery methods, applied in the field of suspicious feature discovery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
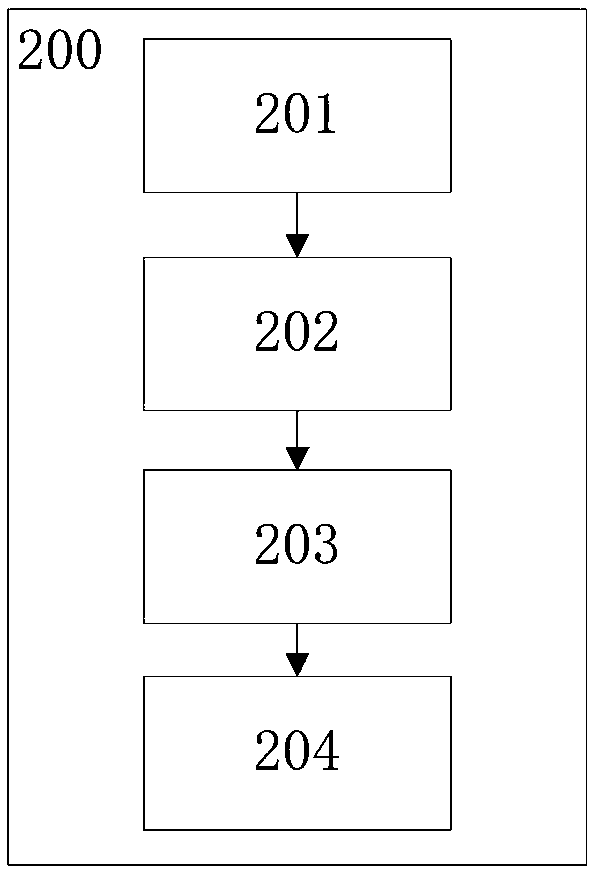
[0048] figure 1 A schematic flowchart of a suspicious feature discovery method 200 based on trading network nodes proposed according to the present invention is shown. As shown in the figure, the method 200 may include the following steps: constructing a user transaction network 201 based on original transaction characteristics; obtaining key nodes 202 from each user transaction network constructed; Extract and form a transaction feature set 203 ; perform association rule mining on the transaction feature set of each key node and obtain a frequent transaction feature set 204 .
[0049] The method 200 for discovering suspicious features based on trading network nodes according to the present invention will be further explained in detail in conjunction with a specific embodiment.
[0050] In this embodiment, the original transaction data is first obtained, wherein the original transaction data includes original transaction characteristics, such as time, amount, transaction loca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com