A Malicious Code Detection Method Inspired by Biological Genes
A malicious code detection and malicious code technology, applied in the fields of instruments, computing, electrical digital data processing, etc., can solve the problem of difficult to ensure the security detection of malicious code, achieve rapid security detection, reduce analysis scale, and ensure security detection. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
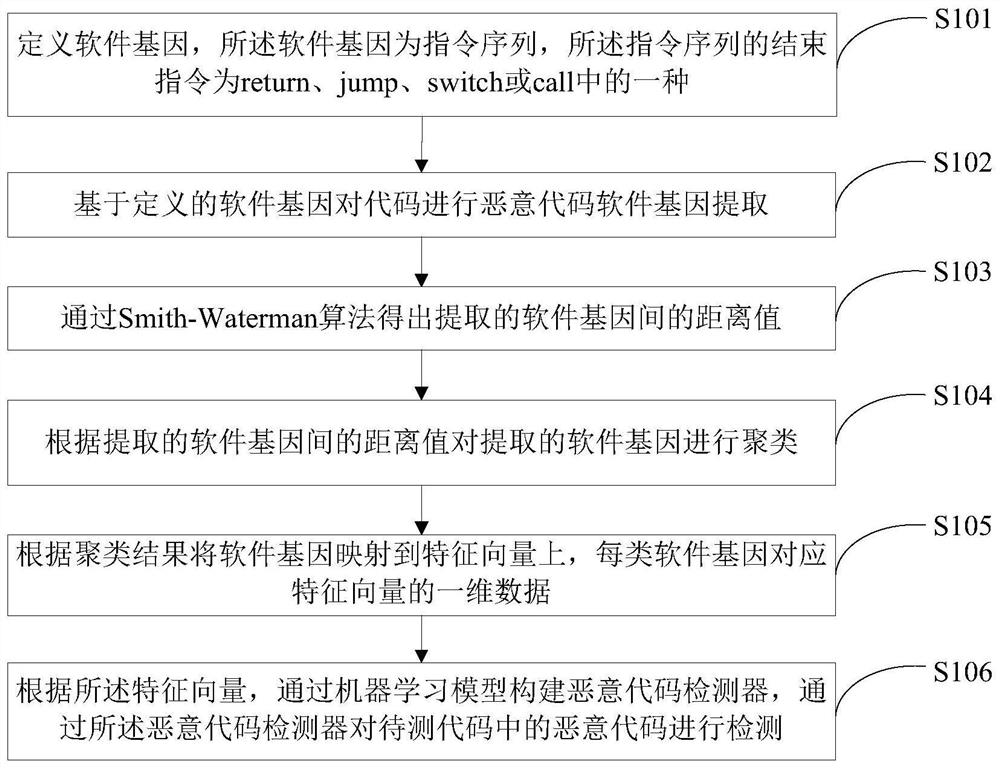
[0041] like figure 1 As shown, a malicious code detection method inspired by biological genes includes the following steps:
[0042] Step S101: defining a malicious code software gene, the malicious code software gene is an instruction sequence, and the end instruction of the instruction sequence is one of return, jump, switch or call;
[0043] Step S102: performing malware gene extraction on the code based on the defined malware gene;
[0044] Step S103: Obtain the distance value between the extracted malicious code software genes through the Smith-Waterman algorithm;
[0045] Step S104: clustering the extracted malware genes according to the distance value between the extracted malware genes;
[0046] Step S105: according to the clustering result, the malware gene is mapped to the feature vector, and each type of malware gene corresponds to the one-dimensional data of the feature vector;
[0047] Step S106: According to the feature vector, a malicious code detector is con...
Embodiment 2
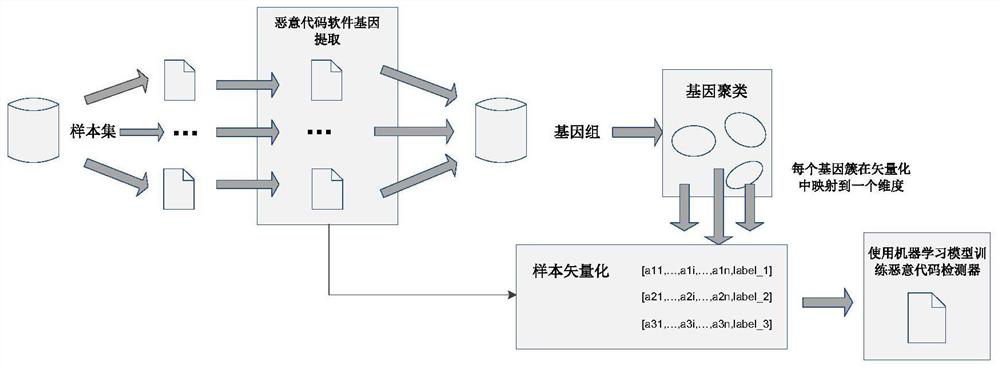
[0066] like figure 2 As shown, another malicious code detection method inspired by biological genes includes:
[0067] Step S201: defining malicious code software genes;
[0068] Biological genes exist in the form of a continuous deoxyribonucleic acid sequence. When the gene is expressed, the entire sequence is transcribed and translated. When a gene is an intron, the entire sequence is not expressed. Correspondingly, in order to describe software code fragments easily using sequences, this system regards a code sequence that executes consistently as a malicious code software gene.
[0069] Definition of malicious code software gene: malicious code software gene is an instruction sequence, and the end instruction of the instruction sequence is one of return, jump, switch or call. In fact, a gene is composed of one or more basic blocks. The basic block takes all call jump instructions as segmentation boundaries. This definition is too trivial for malicious code analysis. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com