Perception layer data fidelity method for local area Internet of Things
A technology for sensing data and local objects, which is applied in the field of data fidelity at the perception layer for the local Internet of Things, and can solve problems such as changes, verification information easily changed by third parties, and identity verification results being tampered with.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
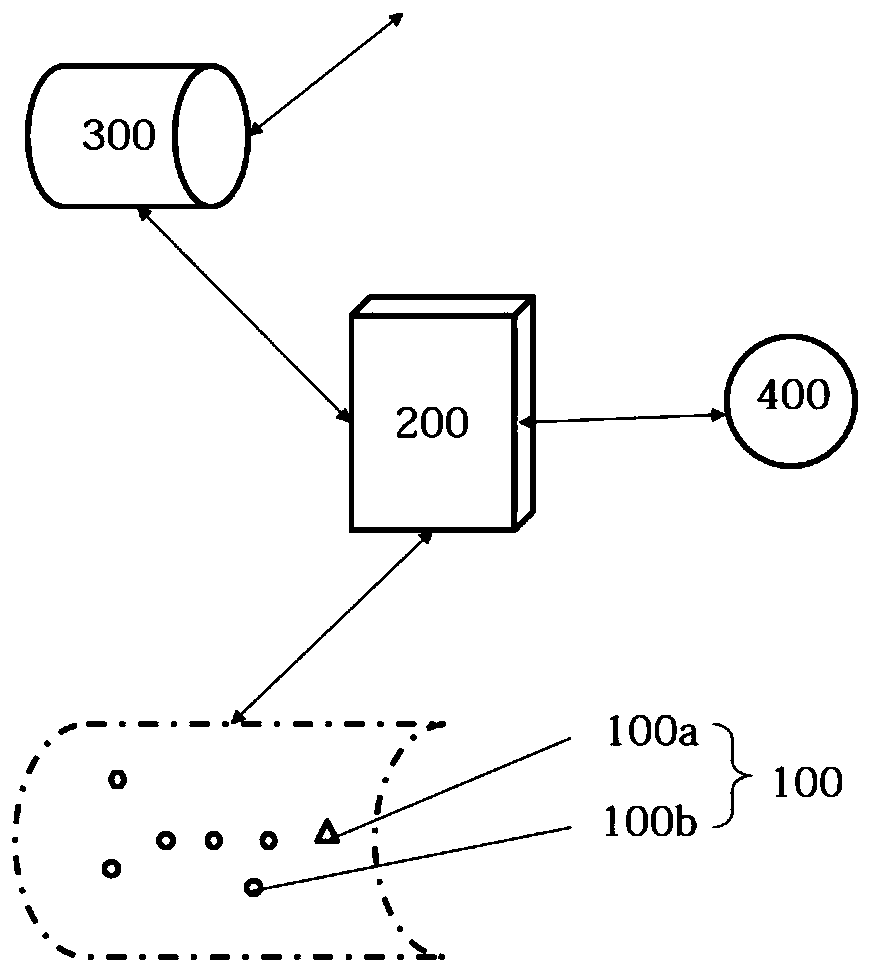
[0039] according to figure 1 As shown, this embodiment provides a data fidelity method of the perception layer oriented to the local Internet of Things. This fidelity method includes:
[0040] A trusted execution environment processor 200 is provided between the sensing node 100 and the gateway 300 in the local Internet of Things. In the prior art, the verification of the sensing node 100 is carried out in an open environment. Although the identity of the sensing node 100 can be identified, the verification method is subject to untrustworthy risks such as tampering and intrusion. Therefore, the identity verification of the sensing node 100 in an open environment may easily cause illegal sensing data to flow along with normal sensing data in the network. Specifically, first, this will increase the risk of illegal perception data tampering with normal perception data and cause normal perception data to be distorted; second, the perception node 100 of the perception layer of the In...
Embodiment 2
[0060] This embodiment may be a further improvement and / or replacement of Embodiment 1, and the repeated content will not be repeated. This embodiment discloses that the whole and / or part of the content of the preferred implementation manners of other embodiments can be used as a supplement to this embodiment without causing conflict or contradiction.
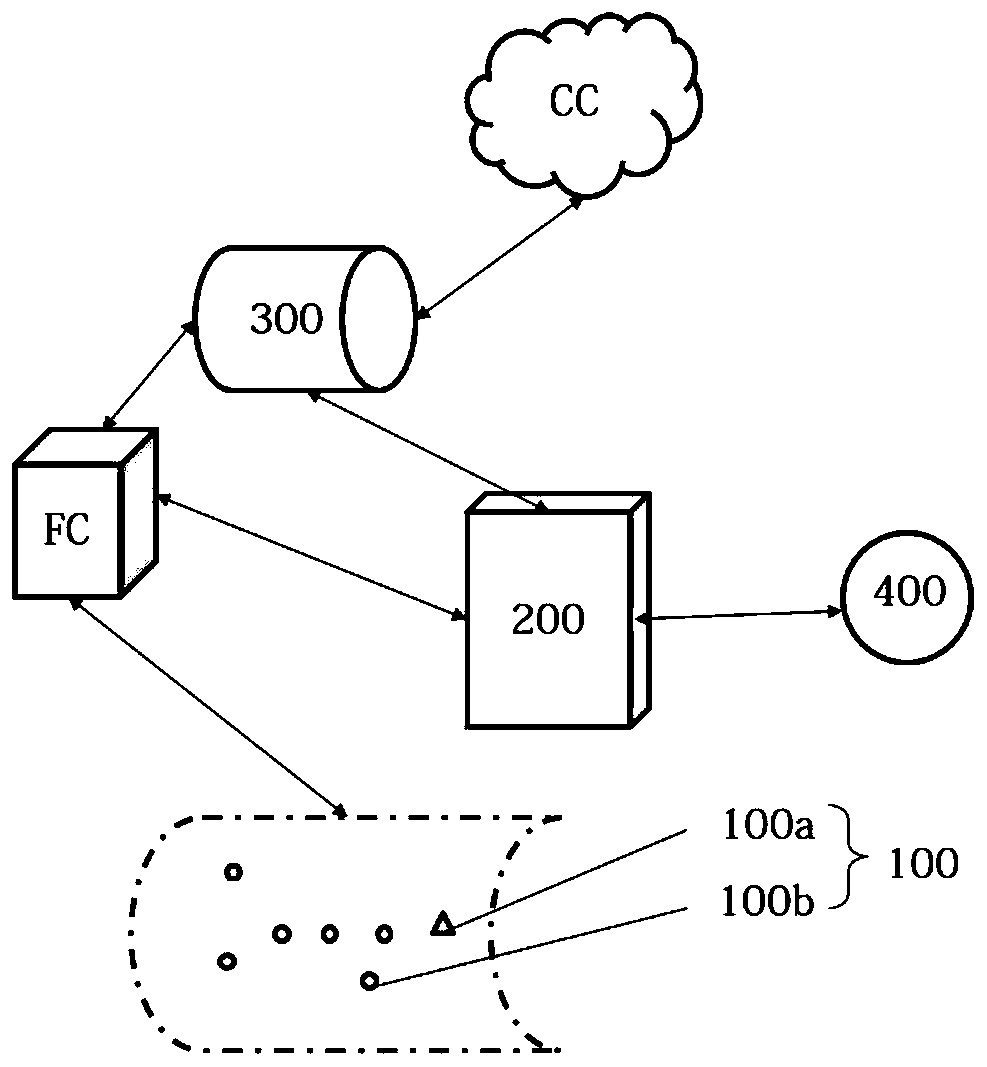
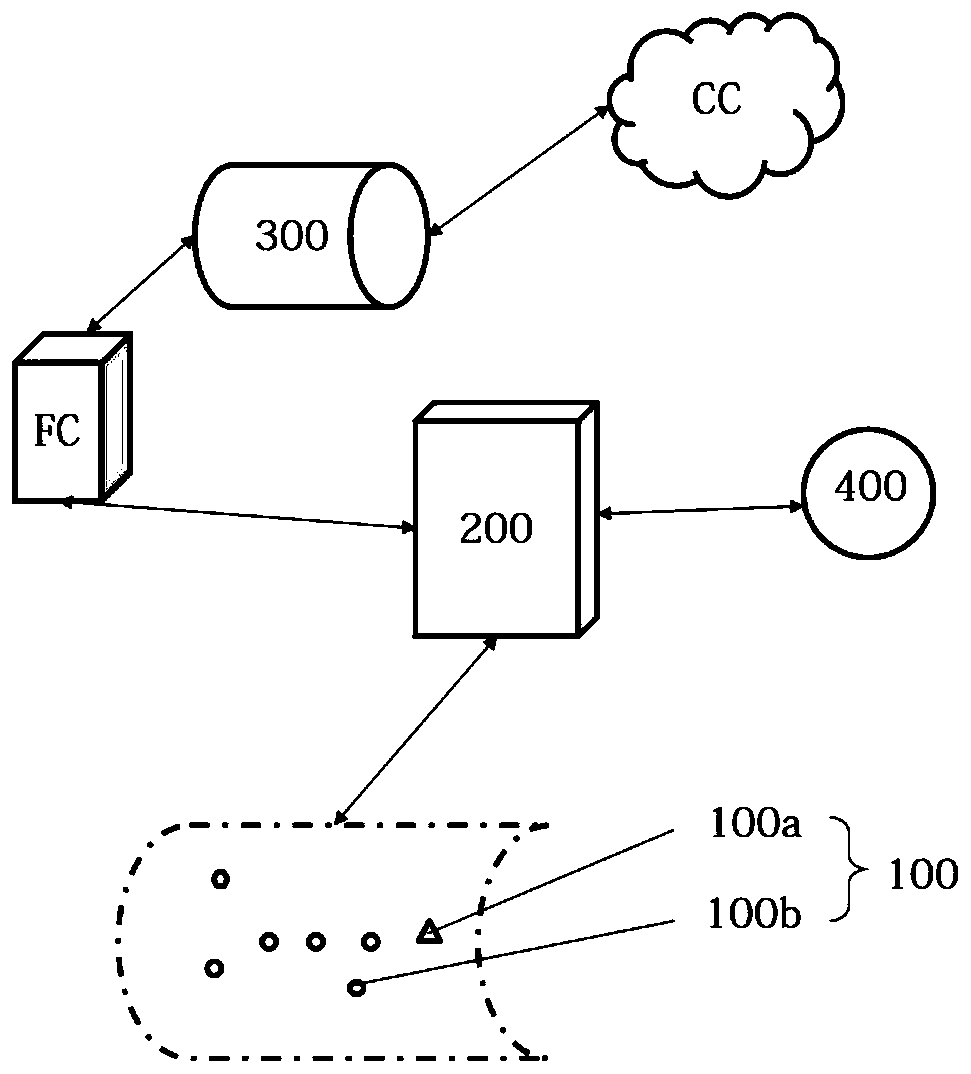
[0061] Such as image 3 As shown, preferably, the trusted execution environment processor 200 identifies each at least two sensing nodes 100 in the designated local area network that request access, and allows the sensing data collected by the sensing node 100 after successful identification verification to be transmitted To the fog end FC and / or preprocessed by the fog end FC and then transmitted to the cloud CC. 1. Set up a trusted execution environment processor 200 between the fog-side FC and the cloud CC. On the premise that the credibility of the data generated in the local local Internet of Things has been guaranteed in the...
Embodiment 3
[0063] This embodiment discloses a system for executing relevant steps and methods in Embodiments 1 and / or 2.
[0064] The perceptual layer data fidelity system for the local Internet of Things of this embodiment, such as figure 1 Shown. A trusted execution environment processor is set between the sensing node and the gateway in the local Internet of Things. The trusted execution environment processor is configured to extract the identity attribute set of the sensing node before the sensing node accesses the gateway, and based on the identity attribute Collectively identify the identity of the sensing node, so that the trusted execution environment processor can be used to intercept the risk sensing node with a suspected identity before the sensing data collected by the sensing node passes through the gateway.
[0065] Preferably, the trusted execution environment processor composes at least one identity attribute element of the sensing node into an identity attribute set in a logi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com