An access control method, device, computer equipment and storage medium
An access control and function technology, applied in the field of information security management, can solve problems such as confusion in authorization, inability to clearly describe the function itself, and difficulty in dealing with it, so as to achieve the effect of authorization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
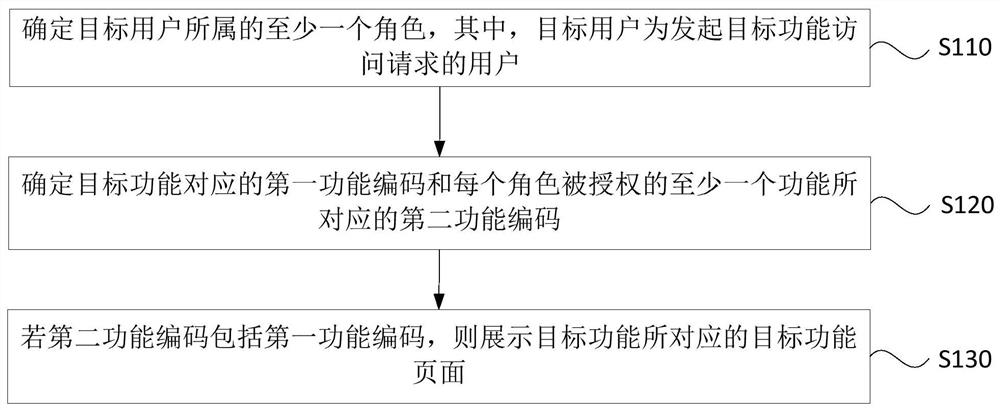
[0033] figure 1 It is a flowchart of an access control method provided by Embodiment 1 of the present disclosure. The embodiment of the present disclosure is applicable to the situation that in a complex information system, system resources need to be carefully authorized without causing authorization confusion. The method can be executed by an access control device, and the device can use software and / or or hardware, the device can be configured in computer equipment. Such as figure 1 As shown, the method may include the following steps:
[0034] S110. Determine at least one role to which the target user belongs, where the target user is a user who initiates a target function access request.
[0035] Exemplarily, the target function may be at least one operation of adding, deleting, modifying, searching, importing and exporting.
[0036] Preferably, different roles can be pre-set in the system according to actual needs, and corresponding system resources (for example, eac...
Embodiment 2
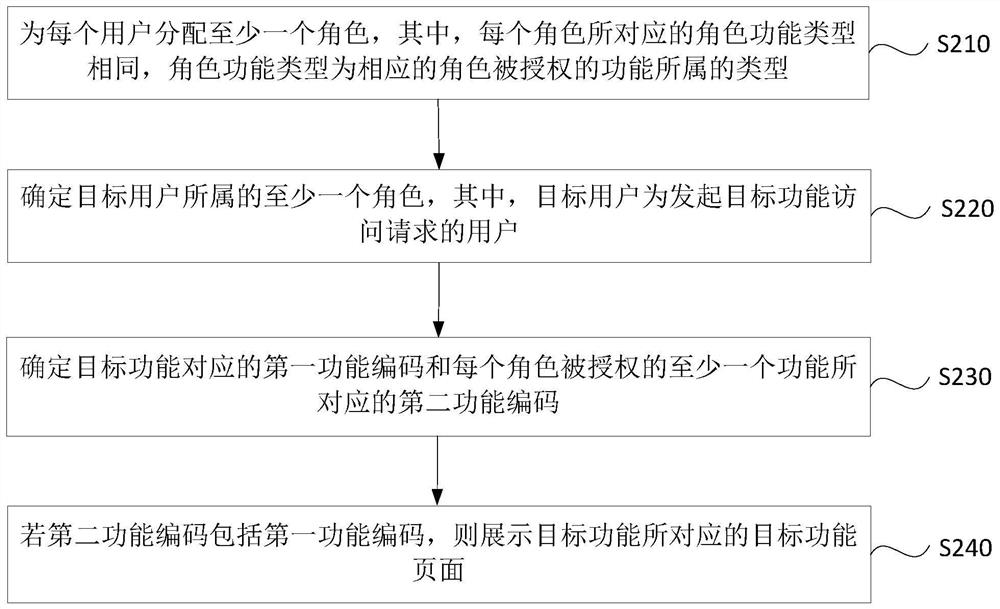
[0051] figure 2 It is a flow chart of an access control method provided in Embodiment 2 of the present disclosure. Embodiments of the present disclosure may be combined with various optional solutions in the foregoing one or more embodiments. In the embodiments of the present disclosure, before determining at least one role to which the target user belongs, it further includes: assigning at least one role to each user Roles, wherein the role function type corresponding to each role is the same, and the role function type is the type to which the function authorized by the corresponding role belongs.
[0052] Such as figure 2 As shown, the method may include the following steps:
[0053] S210. Allocate at least one role to each user, wherein each role corresponds to the same role function type, and the role function type is the type to which the function authorized by the corresponding role belongs.
[0054] Since each function in the system is refined, different functions...
Embodiment 3
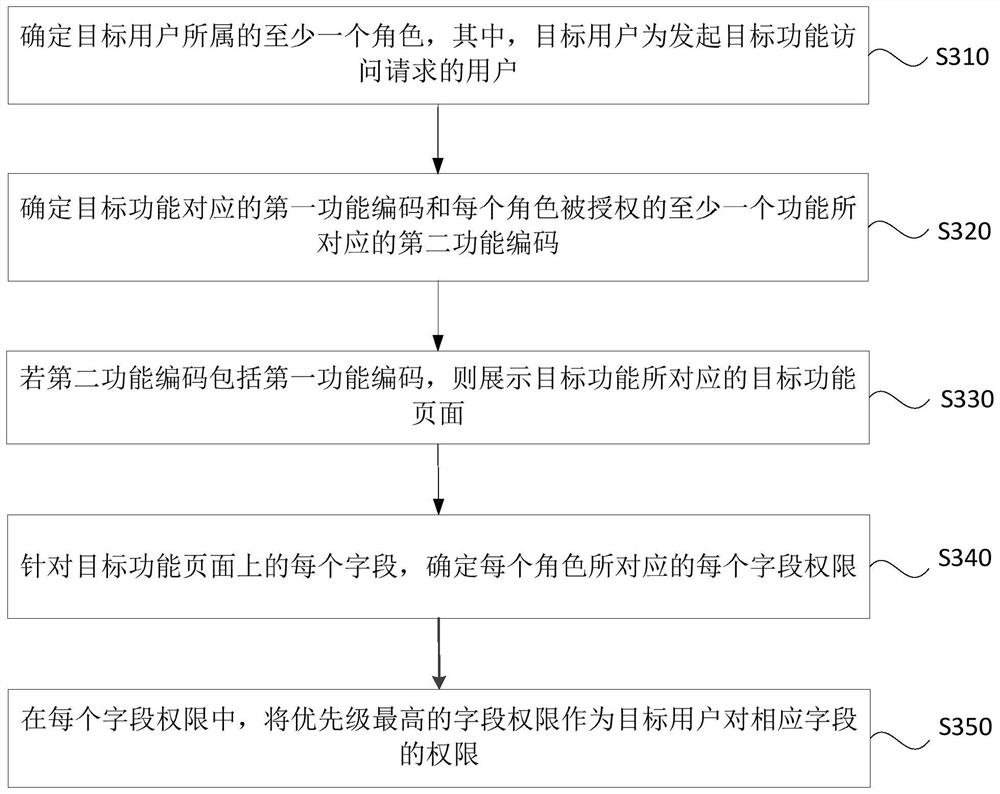
[0062] image 3 It is a flow chart of an access control method provided by Embodiment 3 of the present disclosure. Embodiments of the present disclosure may be combined with various optional solutions in one or more of the above embodiments. In the embodiments of the present disclosure, if the second function code includes the first function code, then display the target After the target function page corresponding to the function, it also includes: for each field on the target function page, determine each field authority corresponding to each role; in each field authority, prioritize The highest field authority is used as the target user's authority to the corresponding field.
[0063] Such as image 3 As shown, the method may include the following steps:
[0064] S310. Determine at least one role to which the target user belongs, where the target user is a user who initiates a target function access request.
[0065] S320. Determine the first function code corresponding...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com