Method, device and system for obtaining data authorization
A technology for data acquisition and data storage, which is applied in the security field and can solve problems such as the inability of the data provider to control the calculation logic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
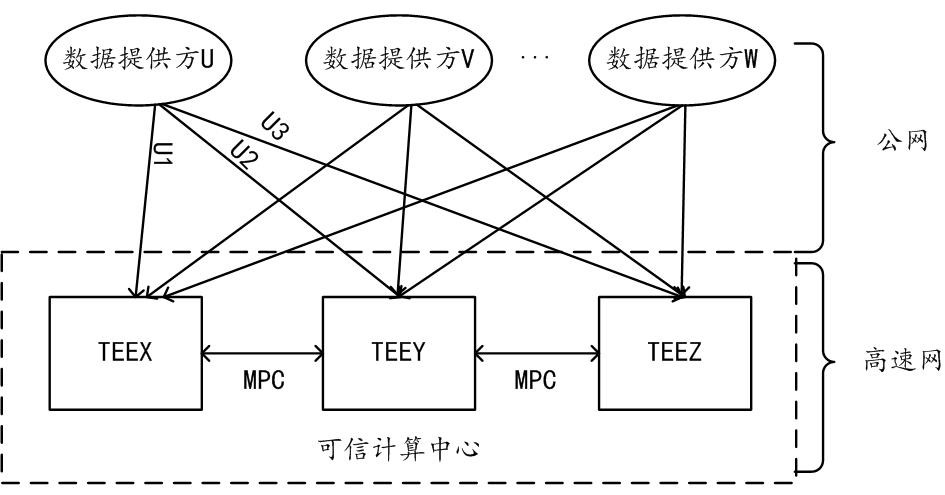
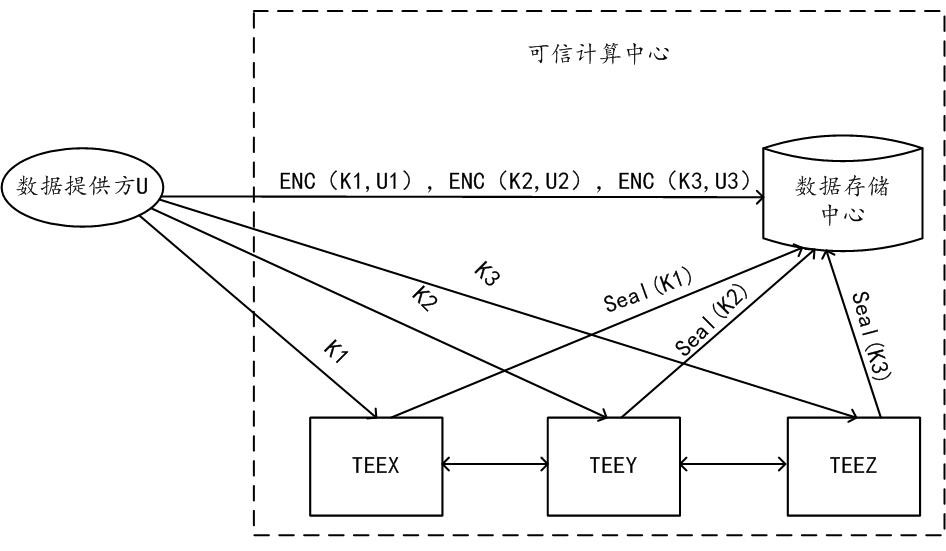
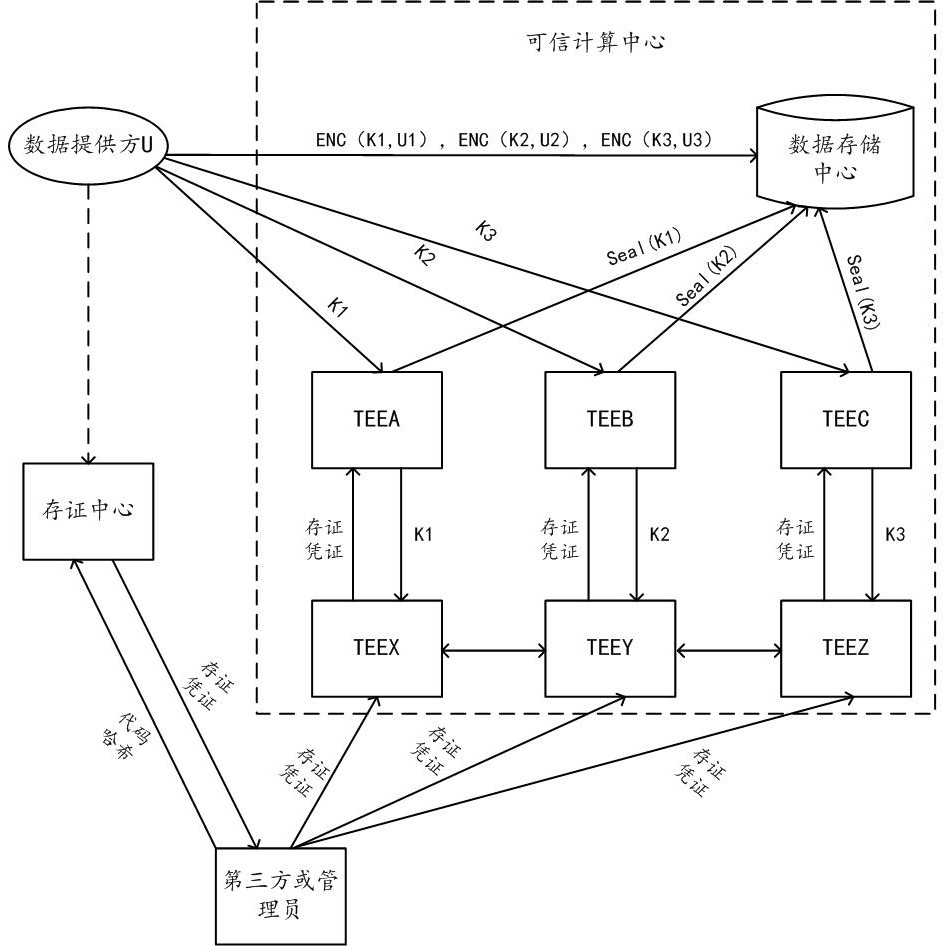
[0058] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
[0059] The scheme provided by the embodiment of this specification proposes a scheme in which the center constrains the calculation logic used by the center when it calculates the data of the data provider through Trusted Cryptographic Computing (TECC for short).
[0060] TECC is a safe and efficient secret-state computing method, which can calculate a common result for multiple data providers without disclosing any party's data. Trusted secret-state computing combines two technologies of system security and cryptography, which balances security and performance better than using only one technology, and finally achieves the ideal state of "adequate security and very fast performance".
[0061] Mathematically provably secure schemes can be constructed using cryptography, but the computational performance of such schemes is poor. Because of the inherent n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com