Patents
Literature
37results about How to "Normal service" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
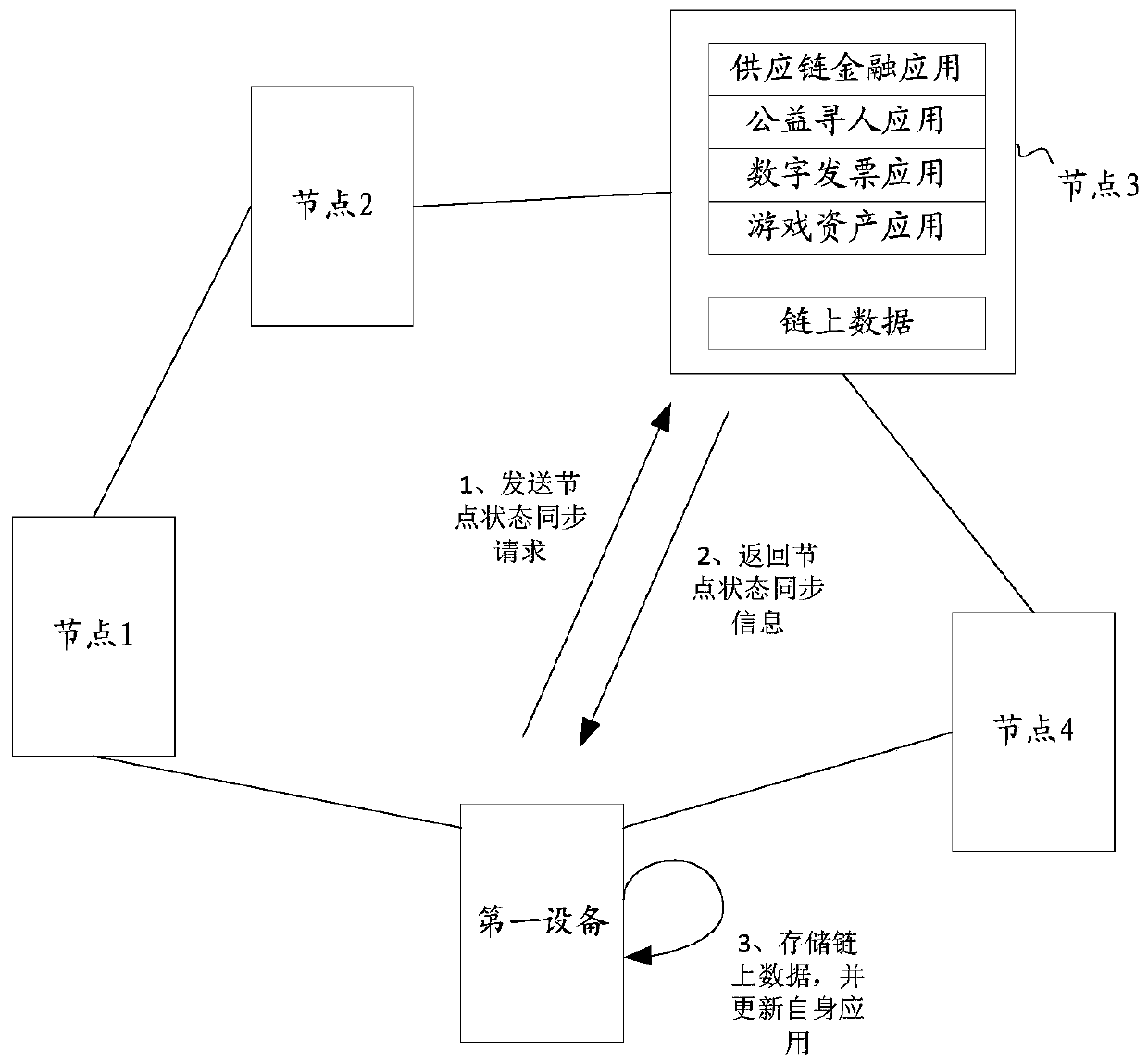
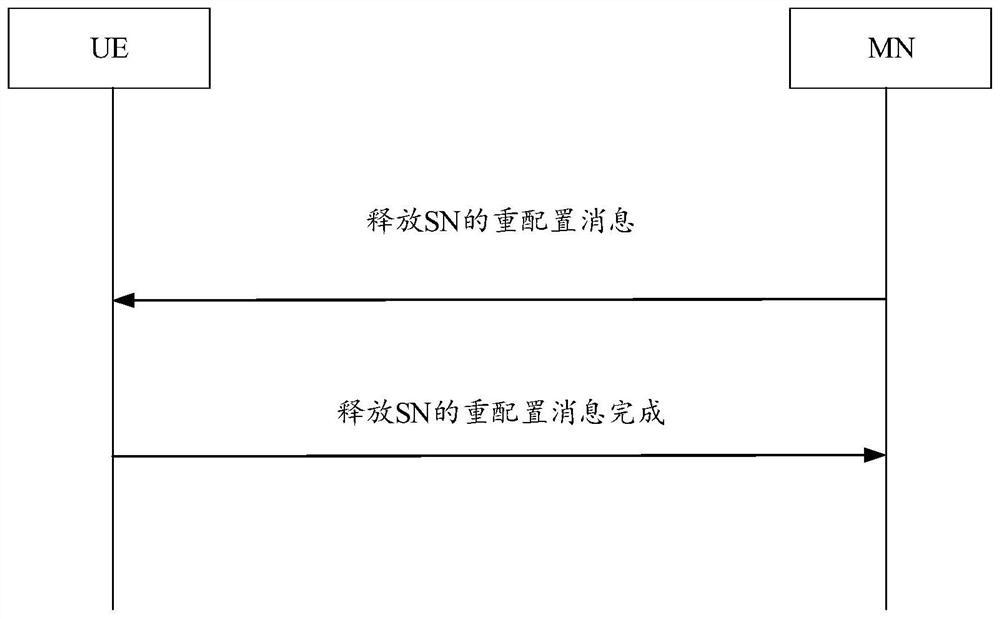
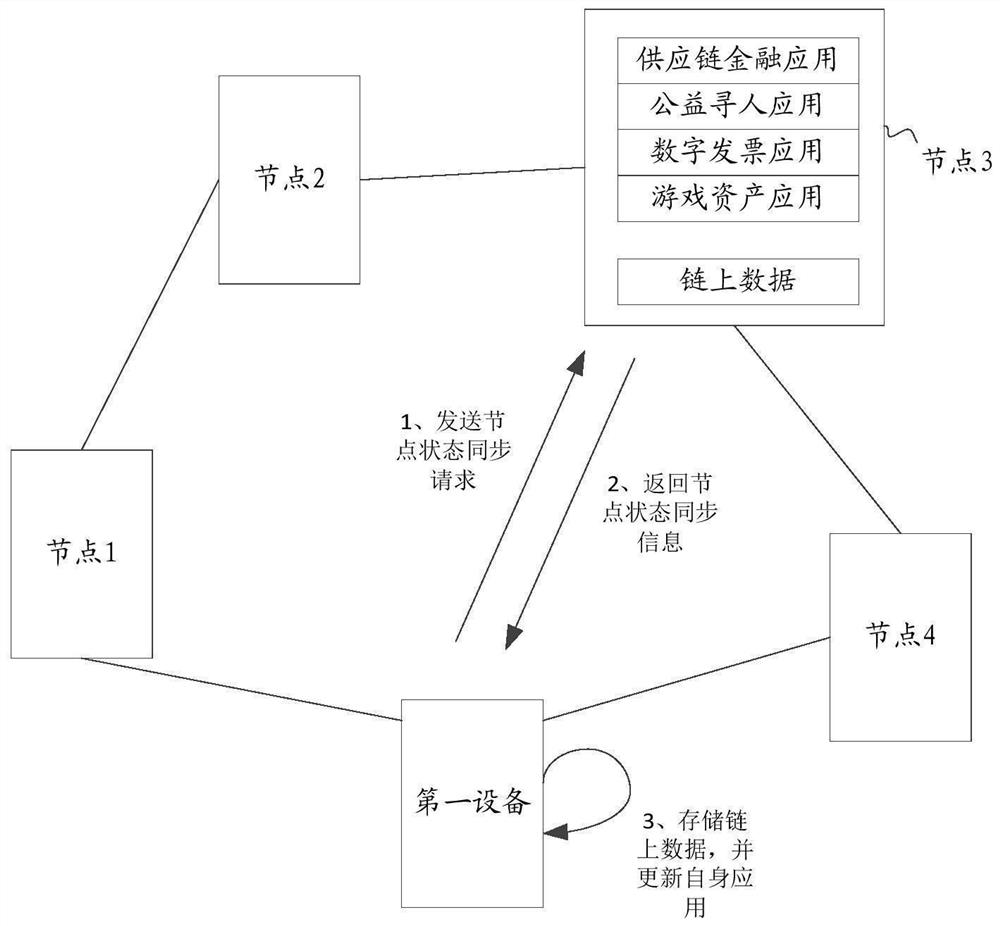
Block chain node deployment method and related equipment
ActiveCN110855791AAutomate deploymentNormal serviceSecuring communicationCommunications securityNode deployment
The embodiment of the invention discloses a block chain node deployment method and related equipment, and the method comprises the steps: obtaining a node deployment mirror image file which comprisesa communication safety agent script, a node bottom layer script and a node service script; running the communication security agent script to establish a security connection with the node management device, and receiving a node configuration file through the established security connection; running a node underlying script to obtain node information of all nodes in the target blockchain from the node configuration file, and determining the node information of all nodes in the target blockchain as attribution blockchain node information; running a node synchronization script according to the attribution block chain node information, obtaining node state synchronization information from any node of the target block chain, and updating the node state of the first device according to the nodestate synchronization information; and running the node service script, and responding to the received blockchain service request of the user. According to the invention, the deployment efficiency ofthe blockchain nodes can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
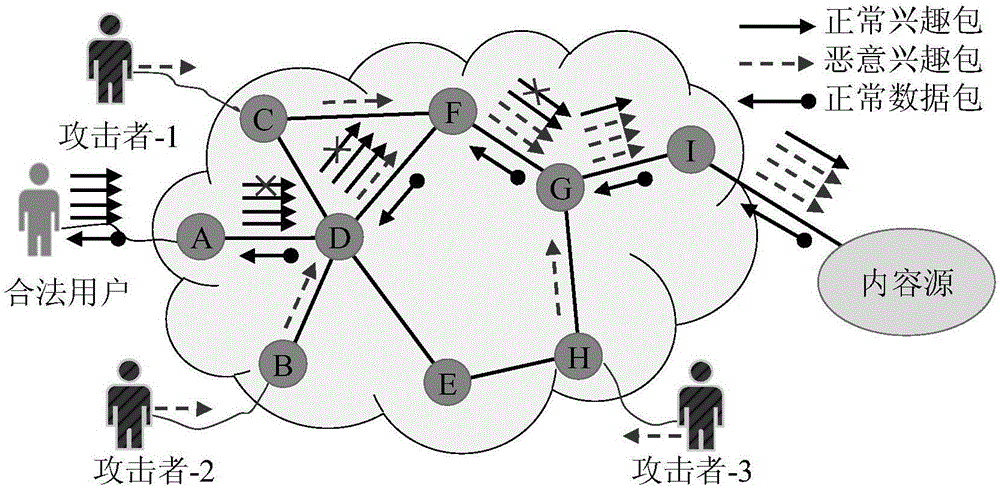
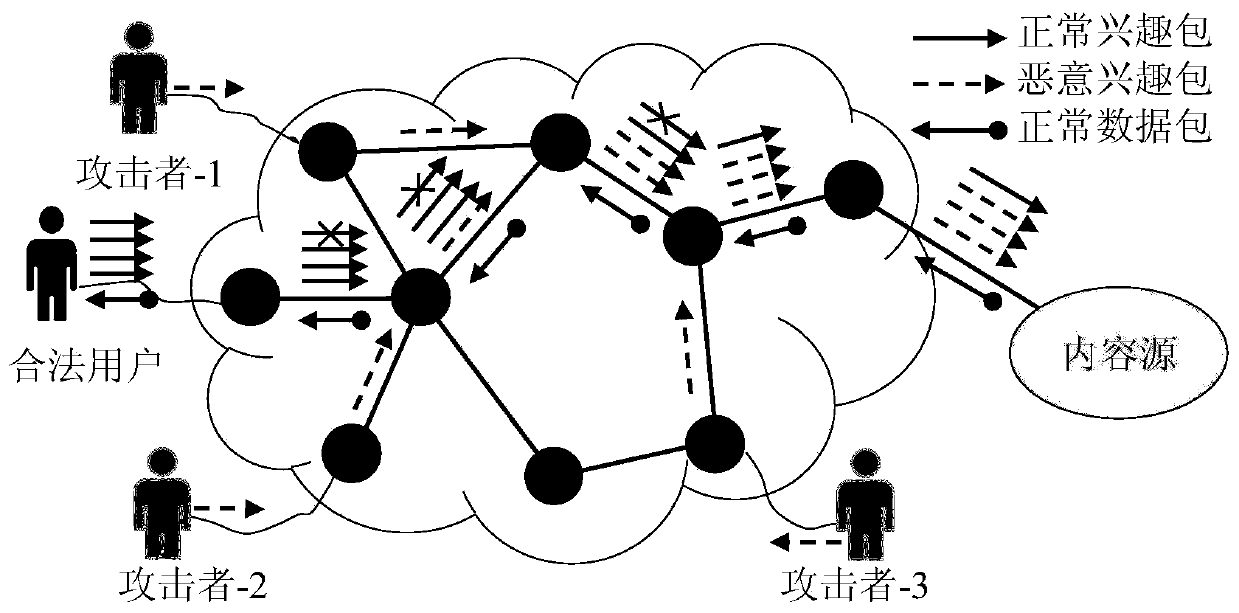
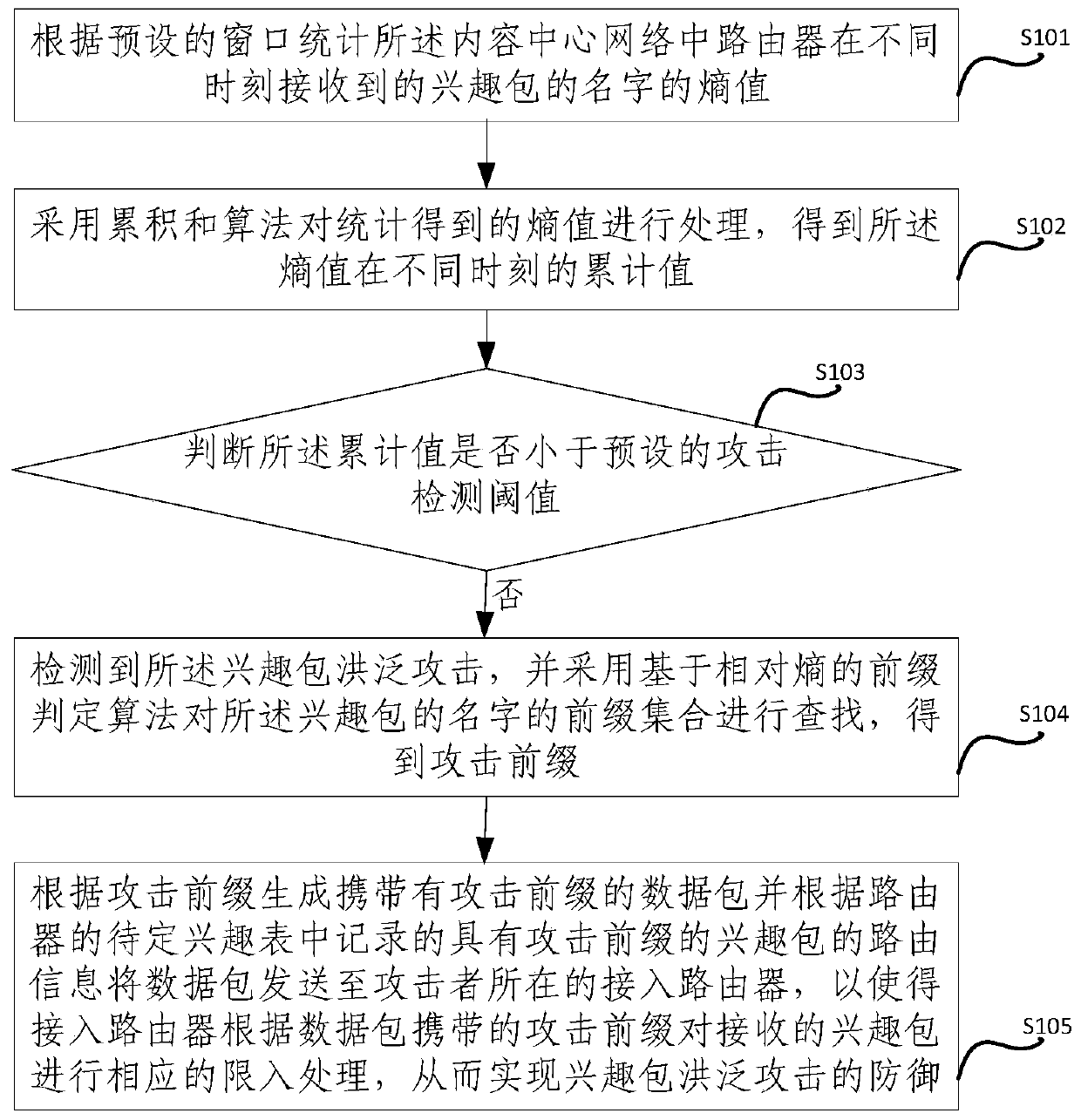
Method and device for defending interest flooding attacks in information centric network
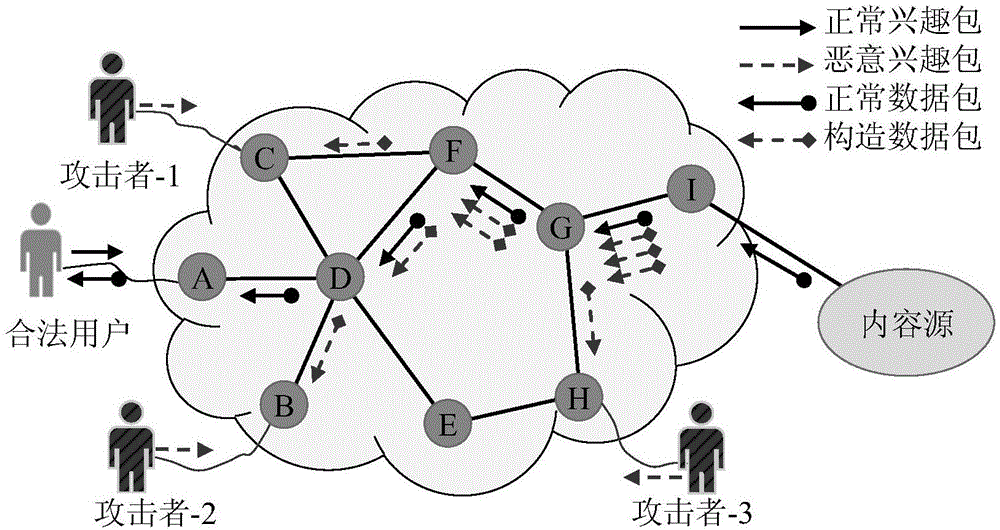
ActiveCN106357641AImprove accuracyReduce false positivesTransmissionFlooding attackKullback–Leibler divergence
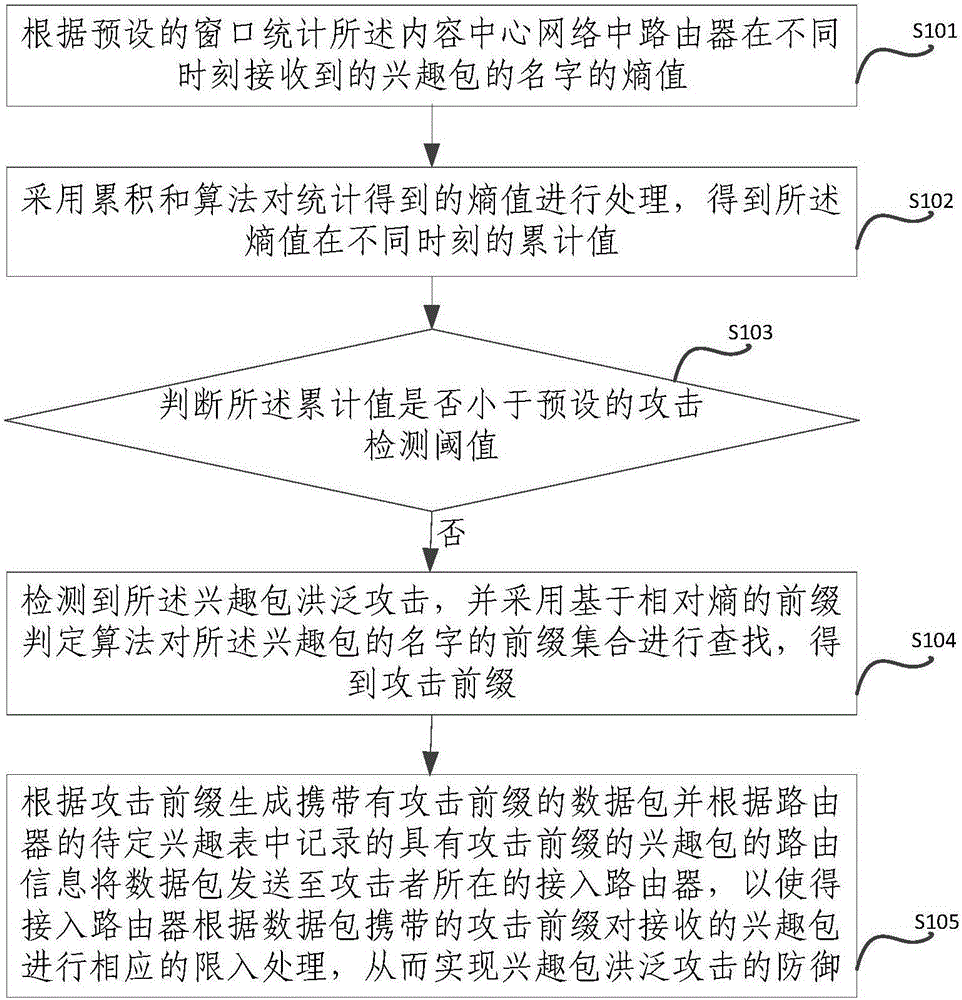
The invention provides a method and device for defending interest flooding attacks in an information centric network and relates to the field of network security. The method includes: statistically counting the entropy of the names of interest packets received by a router in the information centric network after different moments according to a preset window; using a cumulative sum algorithm to process the obtained entropy to obtain the accumulative values of the entropy at different moments; judging whether the accumulative values are smaller than a preset attack detecting threshold or not, if not, judging that interest flooding attacks are detected, and using a prefix determining algorithm based on relative entropy to search the prefix set of the names of the interest packets so as to obtain attack prefixes; generating data packets containing the attack prefixes according to the attack prefixes, and transmitting the data packets to the access router where an attacker is located according to the router information of the interest packets, containing the attack prefixes, recorded in the pending interest table of the router so as to allow the access router to perform corresponding access limitation on the received interest packets according to the attack prefixes in the data packets.
Owner:INST OF INFORMATION ENG CAS
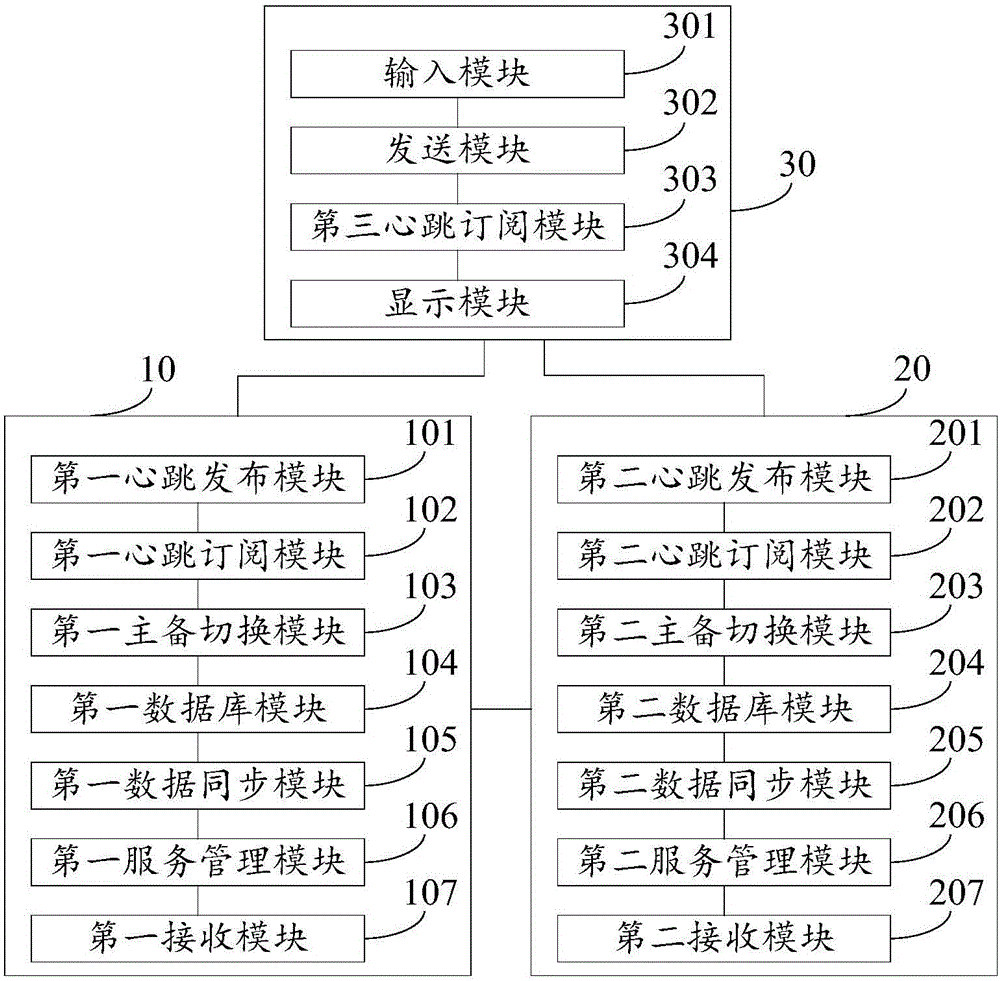
Server dual hot backup system
The invention discloses a server dual hot backup system, and belongs to the technical field of backup. The system comprises a first server and a second server; the first server comprises a first heartbeat release module, a first heartbeat subscription module and a first master-salve switching module, and the second server comprises a second heartbeat release module, a second heartbeat subscription module and a second master-salve switching module; when the first server is a master server, the first heartbeat release module is used for sending a first heartbeat signal; the second master-salve switching module is used for switching the second server into the master server when the times of not receiving the first heartbeat signal exceed a threshold; when the second server is the master server, the second heartbeat release module is used for sending a second heartbeat signal; the first heartbeat subscription module is used for obtaining the first heartbeat signal and the second heartbeat signal; and the first master-salve switching module is used for switching the first server into the master server when the server startup time of the first heartbeat signal is later than the server startup time of the second heartbeat signal.
Owner:武汉船舶通信研究所
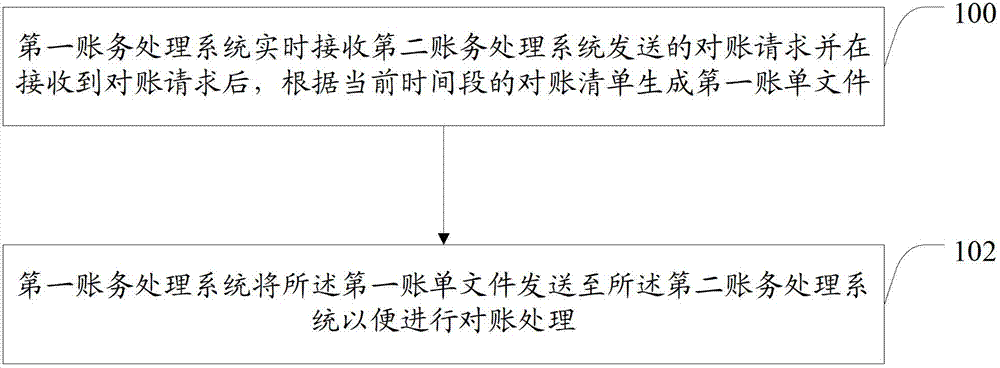
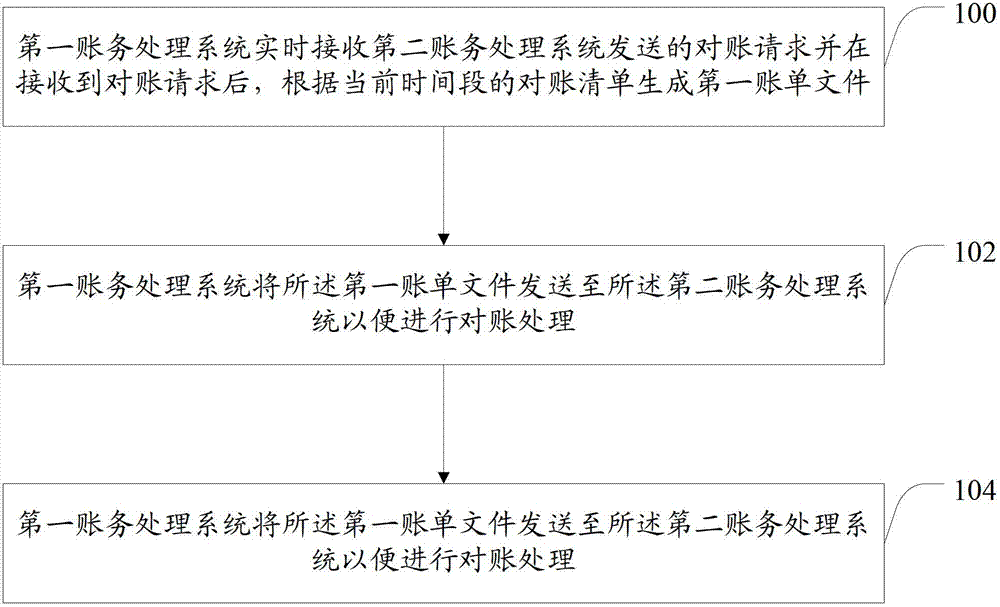
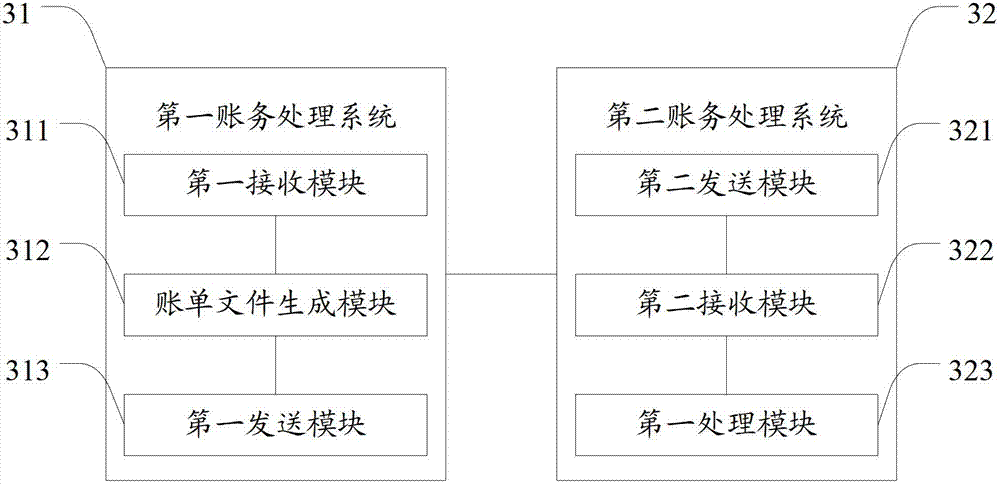
Reconciliation method and system for electronic commerce system
The invention provides a reconciliation method and system for an electronic commerce system. The method comprises the following steps: after receiving the reconciliation request sent by a second account processing system in real time, a first account processing system is used for generating a first bill file according to the reconciliation list at the current time section, and the first account processing system is used for sending the first account file to the second account processing system so as to perform the reconciliation processing. According to the reconciliation method and system for the electronic commerce system provided by the invention, the system performance is free from great influence, the system can provide normal client service, and the reconciliation success rate can be improved through a bill file resending system or a backtracking sending system, and the client experience is improved.
Owner:CHINA CONSTRUCTION BANK
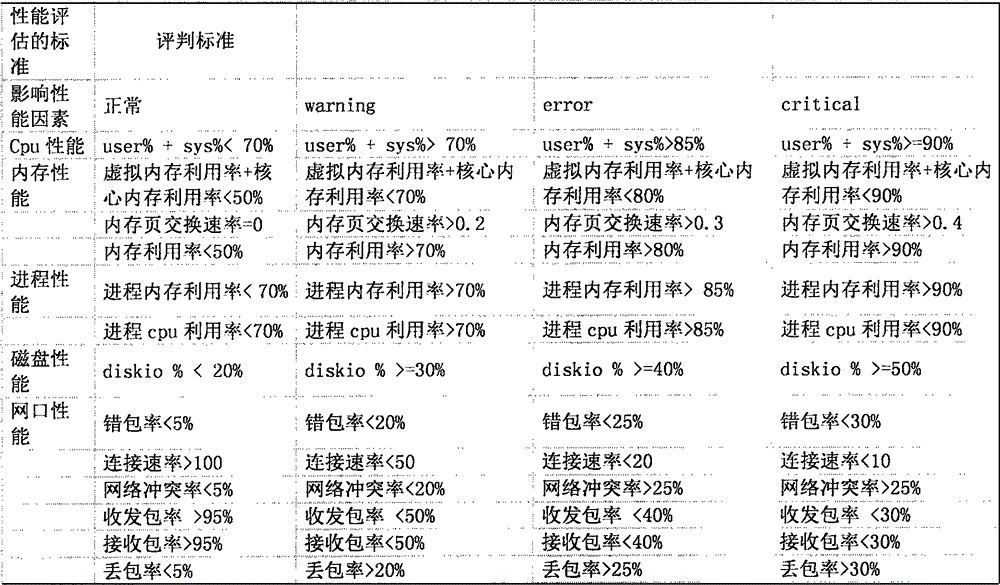
Detection method for detecting running state of IT operation server
The invention provides a detection method for detecting the running state of an IT operation server, and relates to the field of the electronic information. The detection method for detecting the running state of the IT operation server adopts the system monitoring manner and acquires parameters on the following three aspects at the same time, namely the performance of a server, the capacity of the server and the state of the server. In this way, the overall state of the server can be evaluated locally based on the parameters of the above three aspects at the same time. When one aspect of the server goes wrong, a user is notified of the condition in the alarming manner. Furthermore, a visual prompt on whether the server is normal or not is provided for the user, so that the user can take corresponding measures. Therefore, the server is ensured to normally provide services.
Owner:BEIJING HOLYSTONE TECH CO LTD
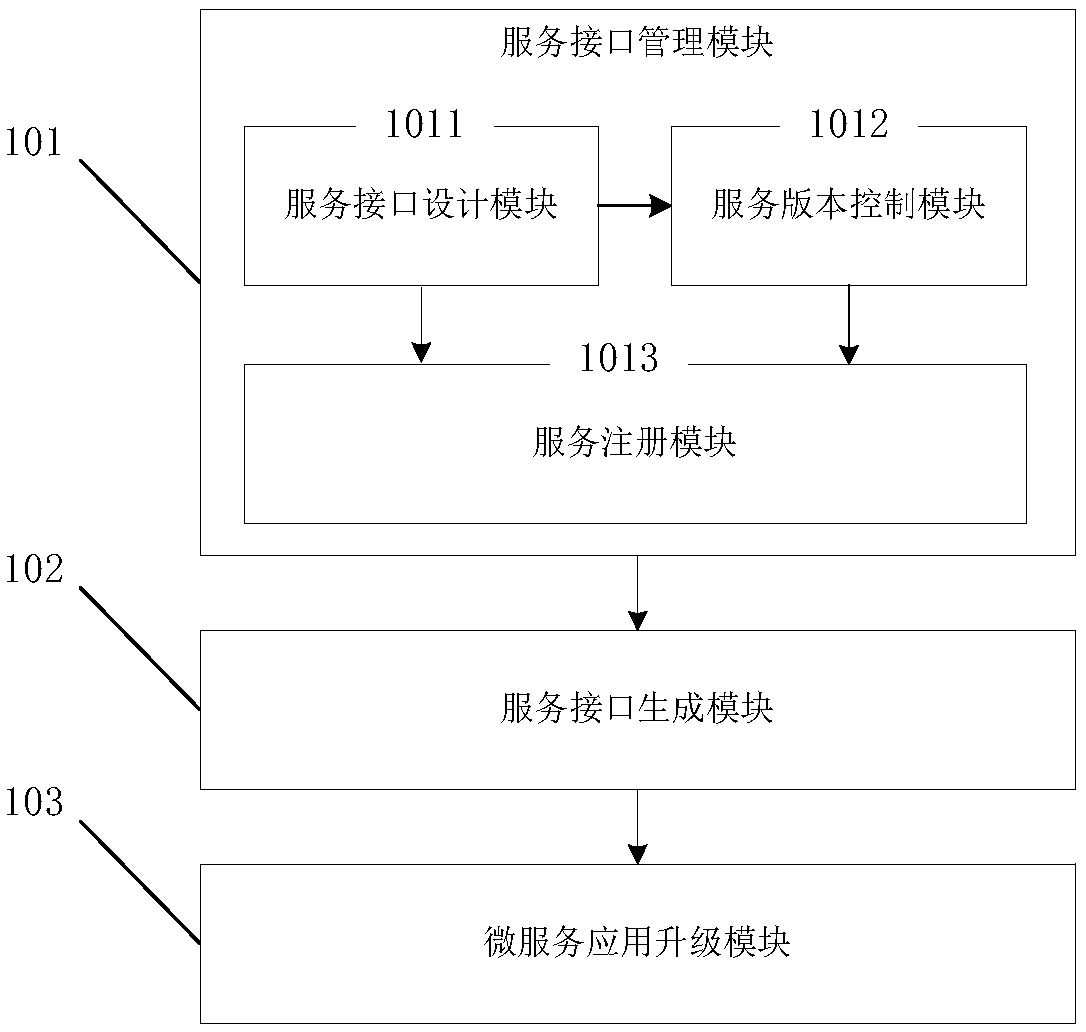
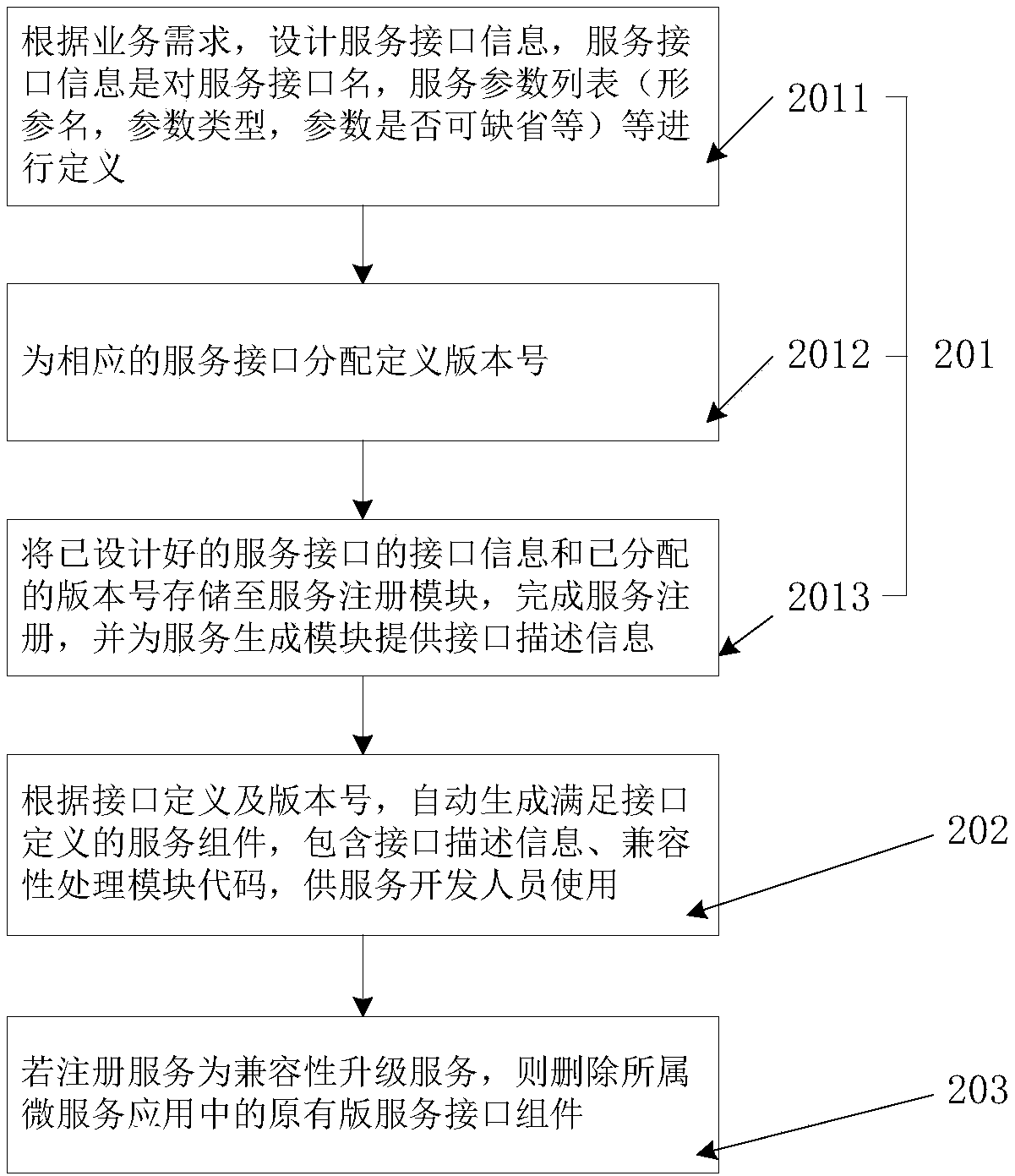
Micro-service development management system and method supporting service upgrading version compatibility
ActiveCN108733406AImprove call success rateUnbind the interfaceVersion controlProgram code adaptionComputer compatibilitySoftware engineering
The invention discloses a micro-service development management system and method supporting service upgrading version compatibility. The management system comprises a service interface management module used for designing a service interface in a micro-service application, controlling and managing a service version of the service interface, storing service interface description information and judging a registration service type, a service interface generating module used for generating a service component in the micro-service application meeting a service interface definition according to interface information of the designed service interface and a distributed version number, and a micro-service application upgrading module used for performing compatibility service upgrading on a registration service when the registration service is a compatibility upgrading service, and deleting an original version service interface of the compatibility upgrading service. The micro-service development management system and method has the advantages that by adding an interface compatibility processing capability for each micro-service application, and in combination with an independent version control mechanism, an interface binding relationship between micro-services is effectively eliminated, the success rate of service calling is greatly increased, and the service operation resource occupation rate is controlled.
Owner:DAREWAY SOFTWARE
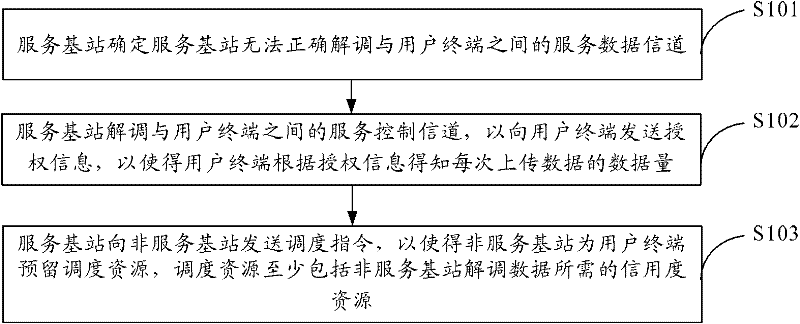
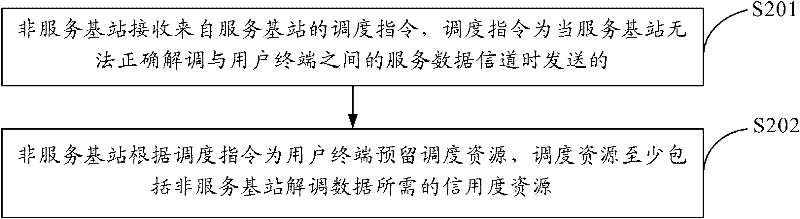
Scheduling method, link unbalance judging method and device and communication system
The embodiment of the invention provides a scheduling method, a link unbalance judging method, a link unbalance judging device and a communication system, relates to the field of communications, can enable user equipment to know the data volume of data uploaded at every time, and can modulate the data uploaded by the user equipment through a non-service base station. The scheduling method comprises the following steps that: a service base station determines that the service base station cannot correctly modulate a service data channel between the service base station and the user equipment; the service base station modulates a service control channel between the service base station and the user equipment so as to send authorization information to the user equipment, so that the user equipment knows the data volume of the data uploaded at every time according to the authorization information; and the service base station sends a scheduling instruction to the non-service base station, so that the non-service base station preserves scheduling resources for the user equipment, wherein the scheduling resources at least comprise a credit degree resource required by the non-service base station to modulate data.
Owner:HUAWEI TECH CO LTD
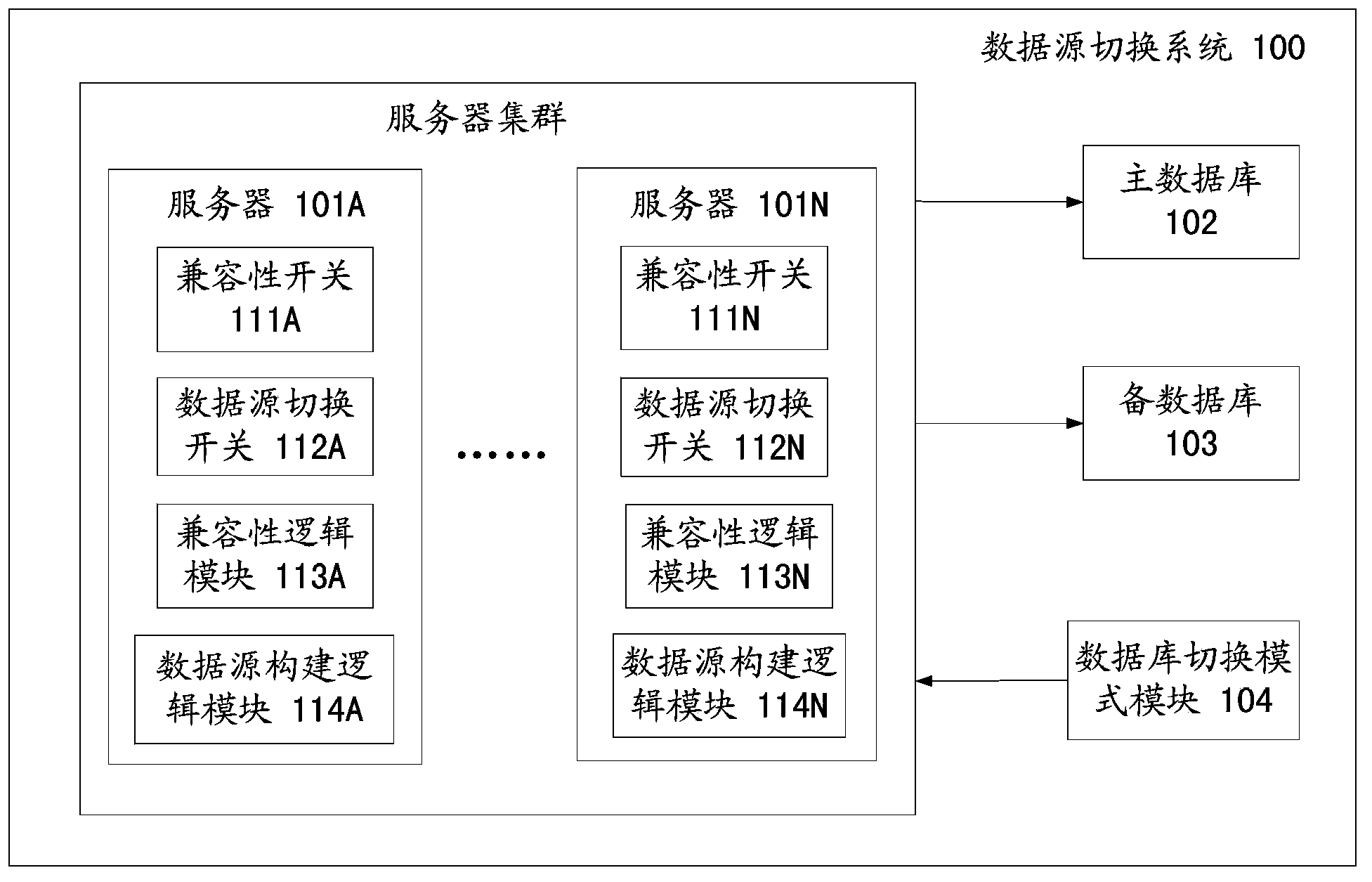
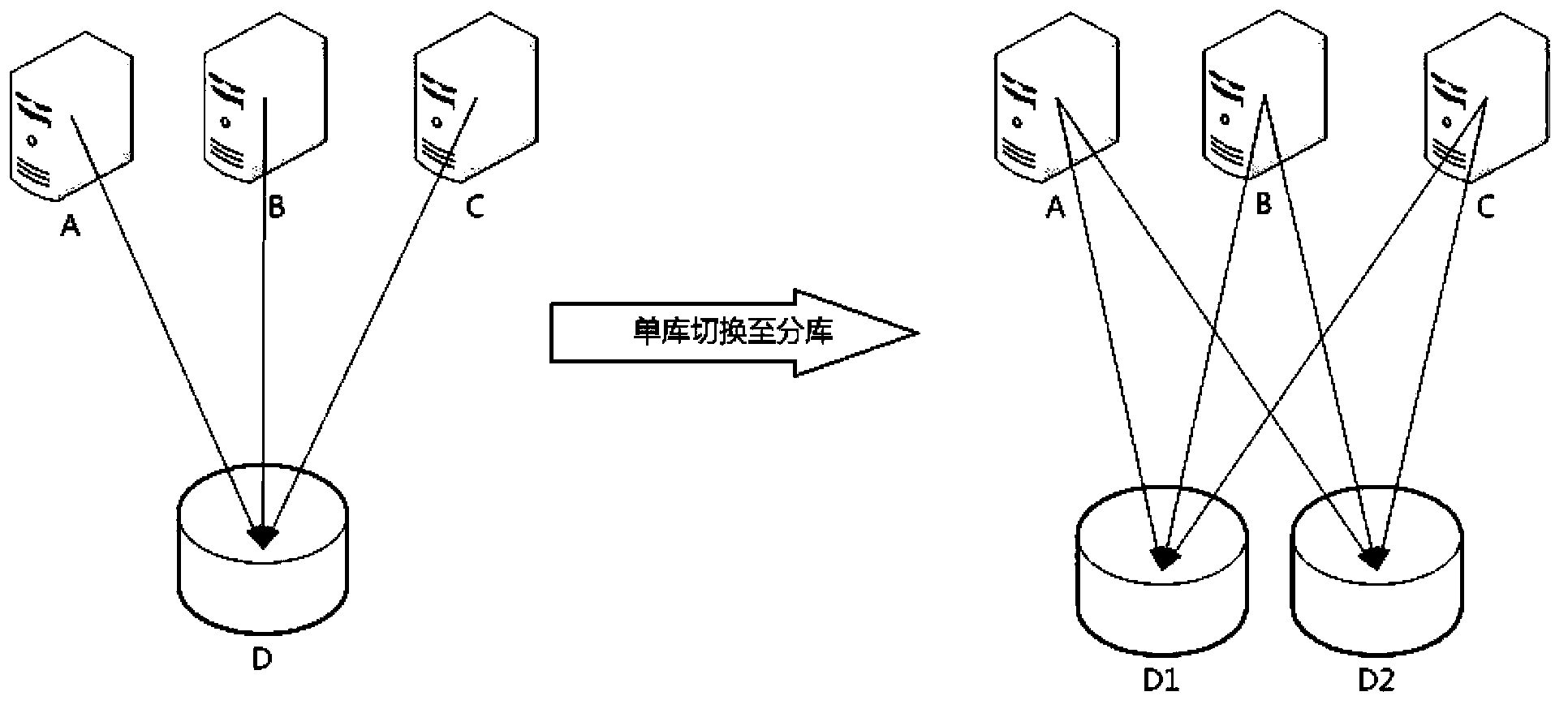
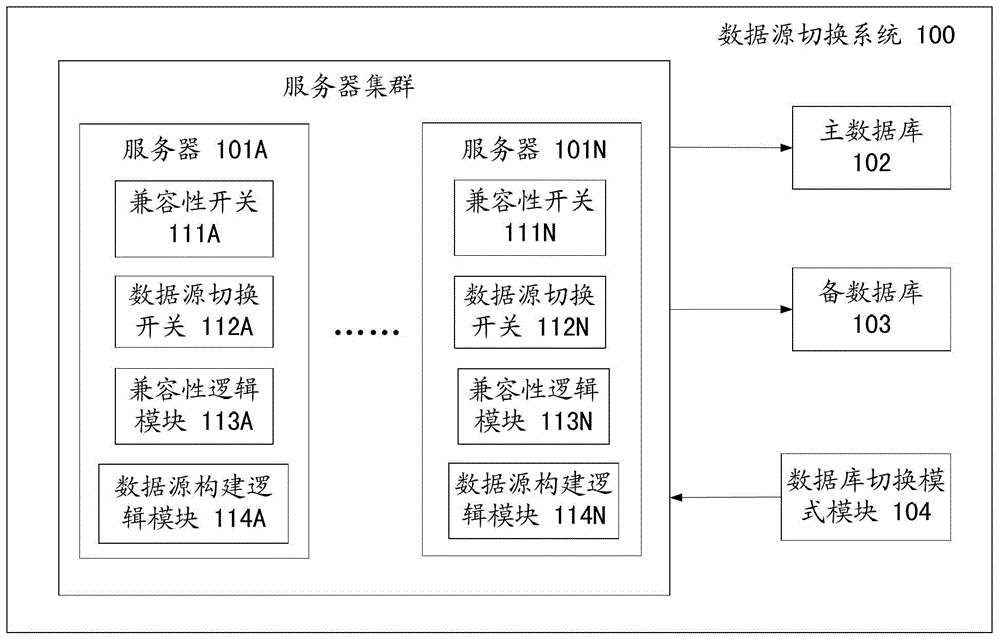
Database switching method and database switching system
ActiveCN103810174ASmooth switchingNormal serviceError detection/correctionDatabase distribution/replicationComputer compatibilityData source
The invention provides a database switching method and a database switching system. The method comprises the steps that a compatible switch of each server is started to start a compatible logic module of the corresponding server, the compatible logic modules execute compatible processing of service compatibility of a main database and a spare database, a data source building logic module makes the main database be built into a main data source and makes the spare database be built into a spare data source on the basis of the switched-off states of data source switches; the data source switch of each server is switched on, so that each server is connected with the spare database rather than being connected with the main database, the compatible logic modules continue to execute compatible processing, and the data source building logic module makes the main database be built into the spare data source and makes the spare database be built into the main data source on the basis of the switched-on states of the data source switches; the compatible switch of each server is switched off after preset time.
Owner:ADVANCED NEW TECH CO LTD
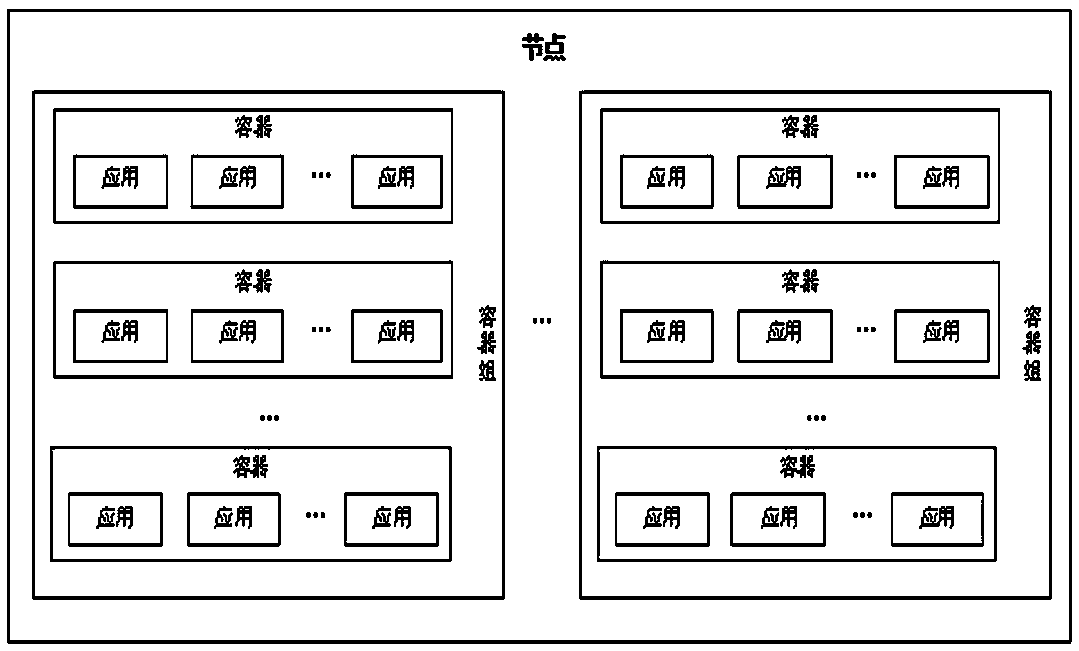
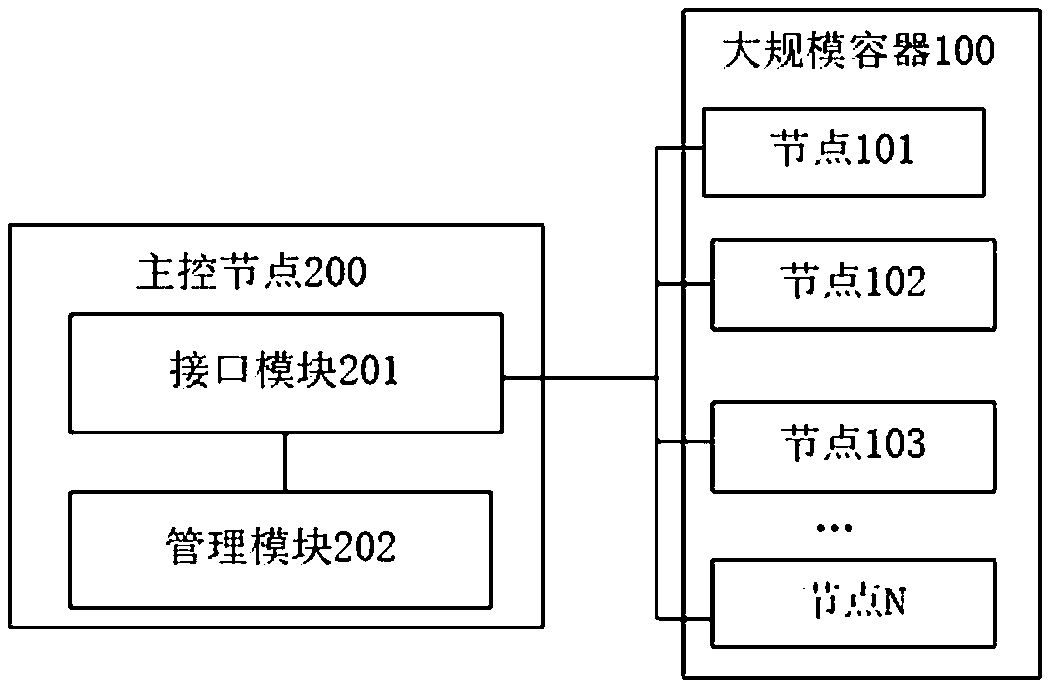
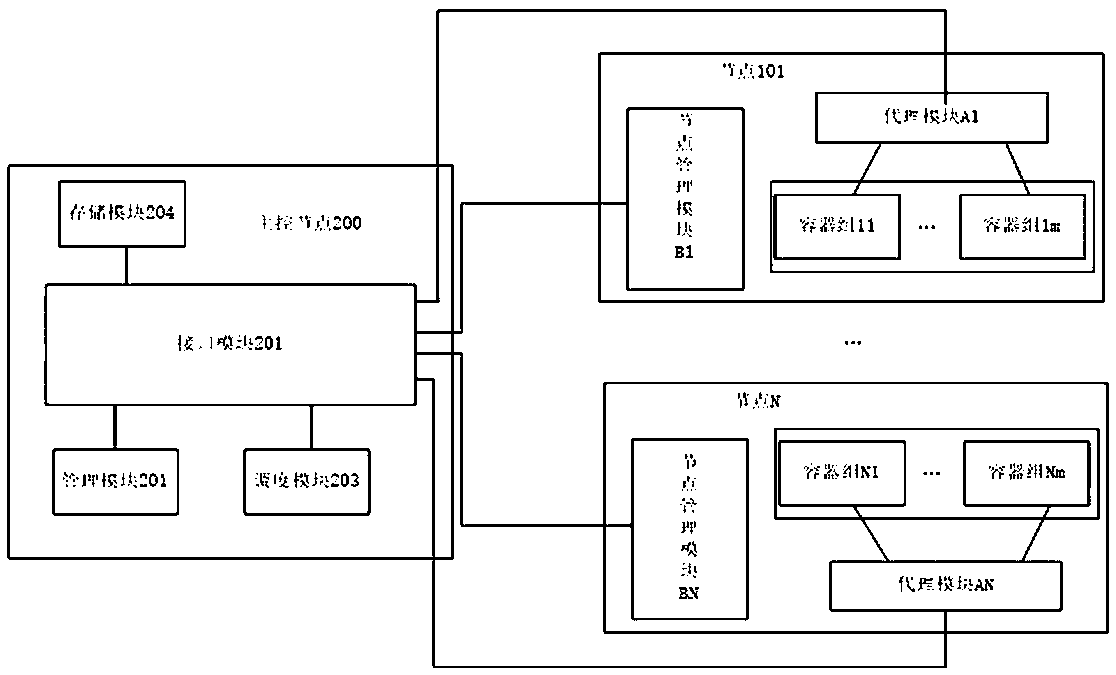
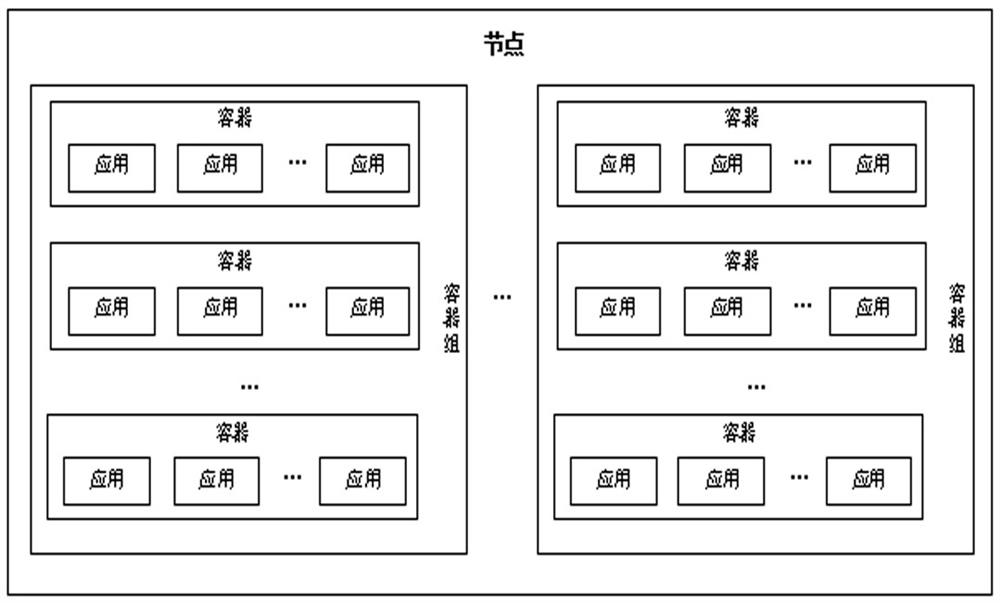
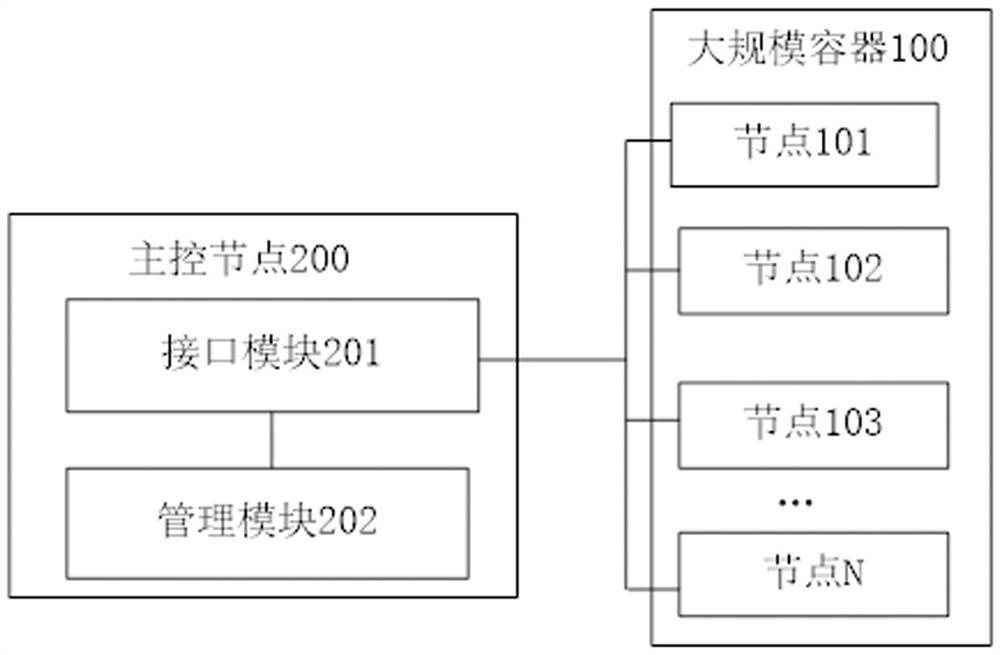
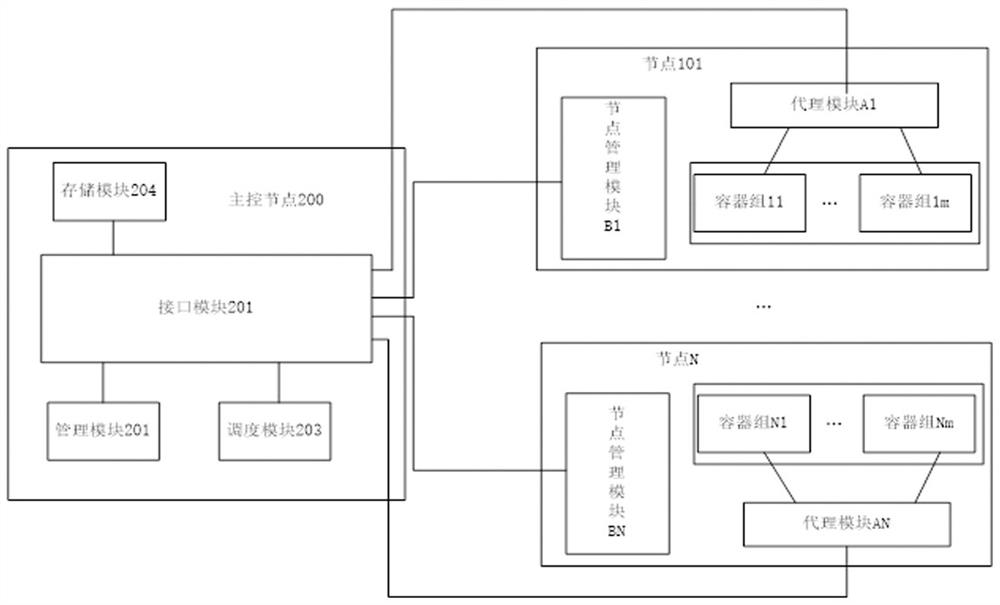
System for managing large-scale container application
The invention provides a system for managing large-scale container application. A large-scale container comprises at least one container group, and at least one container group forms a node. The system comprises a master control node, wherein an interface module in the master control node receives an operation request for a target container group sent by a request node. A management module monitors the operation request through the interface module, and sends the operation request to a target node where the target container group is located through the interface module if the large-scale container comprises the target container group. The target node manages the target container group to execute corresponding operation, and the request node monitors the operation execution state of the target container group in the target node through the interface module. The system realizes management of the large-scale containers in a cluster mode, and large-scale access pressure is distributed to the container groups in different target nodes according to needs through the main control node, so that each container in each container group has high availability, and a corresponding number of container groups can be started according to needs.
Owner:北京零研科技有限公司
A secure smartphone and control method based on a split-core virtual machine
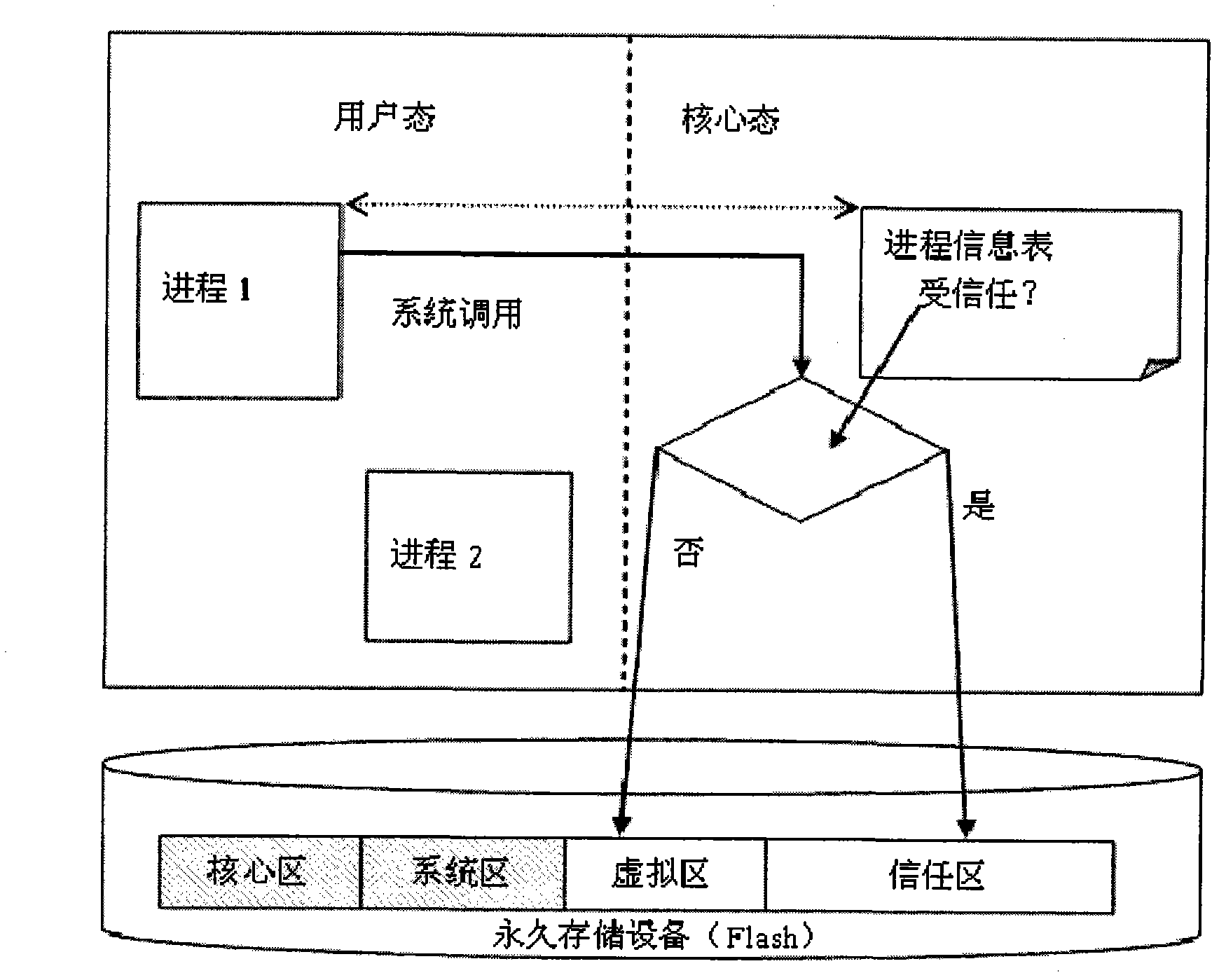
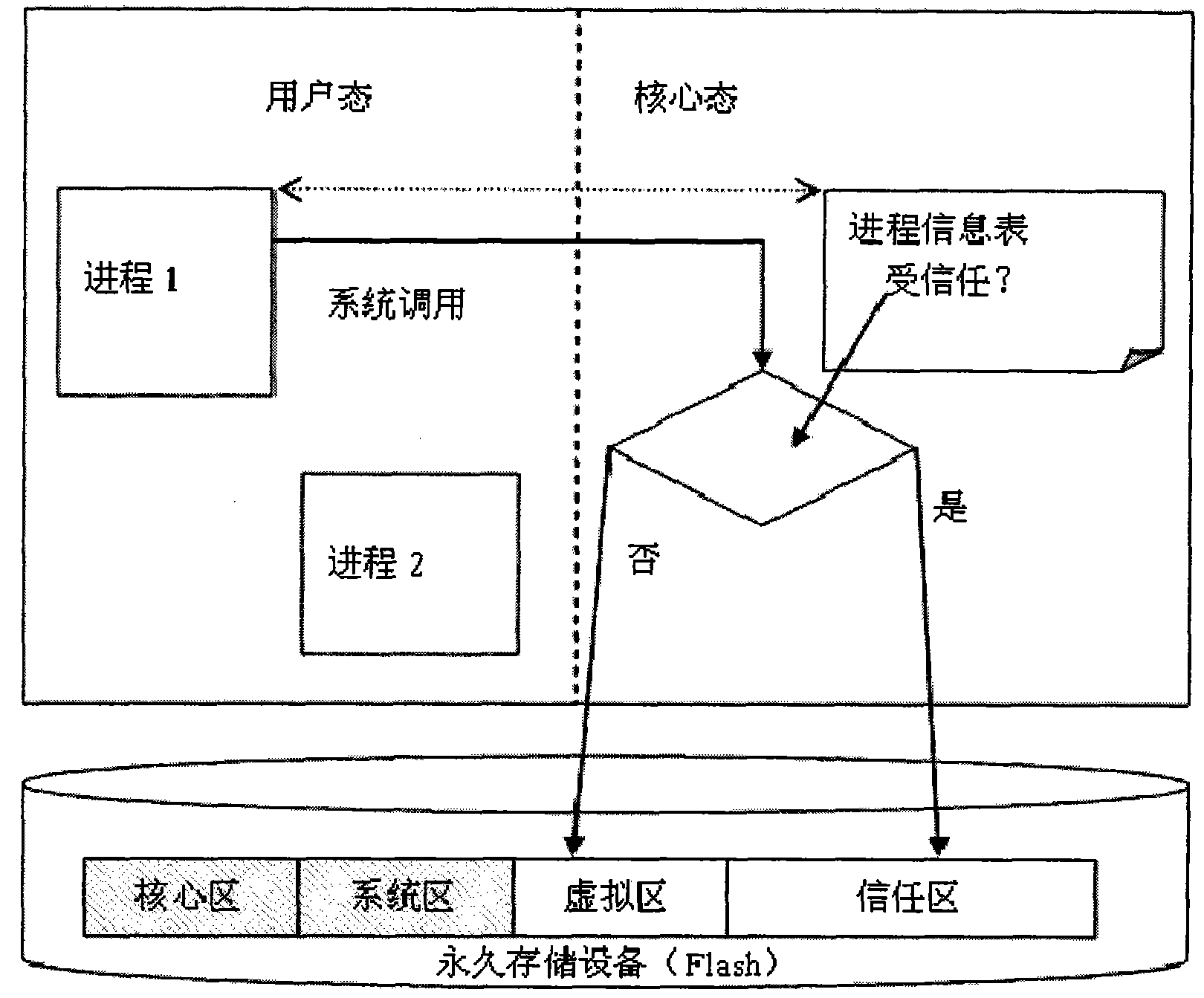
InactiveCN102289621AEliminate potential safety hazardsCannot stealSubstation equipmentPlatform integrity maintainanceVirtual machineProcess information
A security smart phone based on a split core virtual machine and its control method, which includes an operating system with a core state and a user state, and a permanent storage device for storing system data, programs and configuration information; the permanent storage device is divided into Four different partitions: core area, system area, virtual area and trust area; by loading the operating system core and various service programs in the core area and system area when starting the system, and establishing user processes and process information tables, it is possible to determine whether the process is trusted If it is trusted, it is directed to the trusted zone, otherwise it is directed to the virtual zone. The present invention redirects system calls that may affect the system to different data areas according to the nature of the program in the core state, so that a lightweight virtual machine can be realized, and high security can be realized with few resources.
Owner:PENGKUN COMM KUNSHAN CO LTD
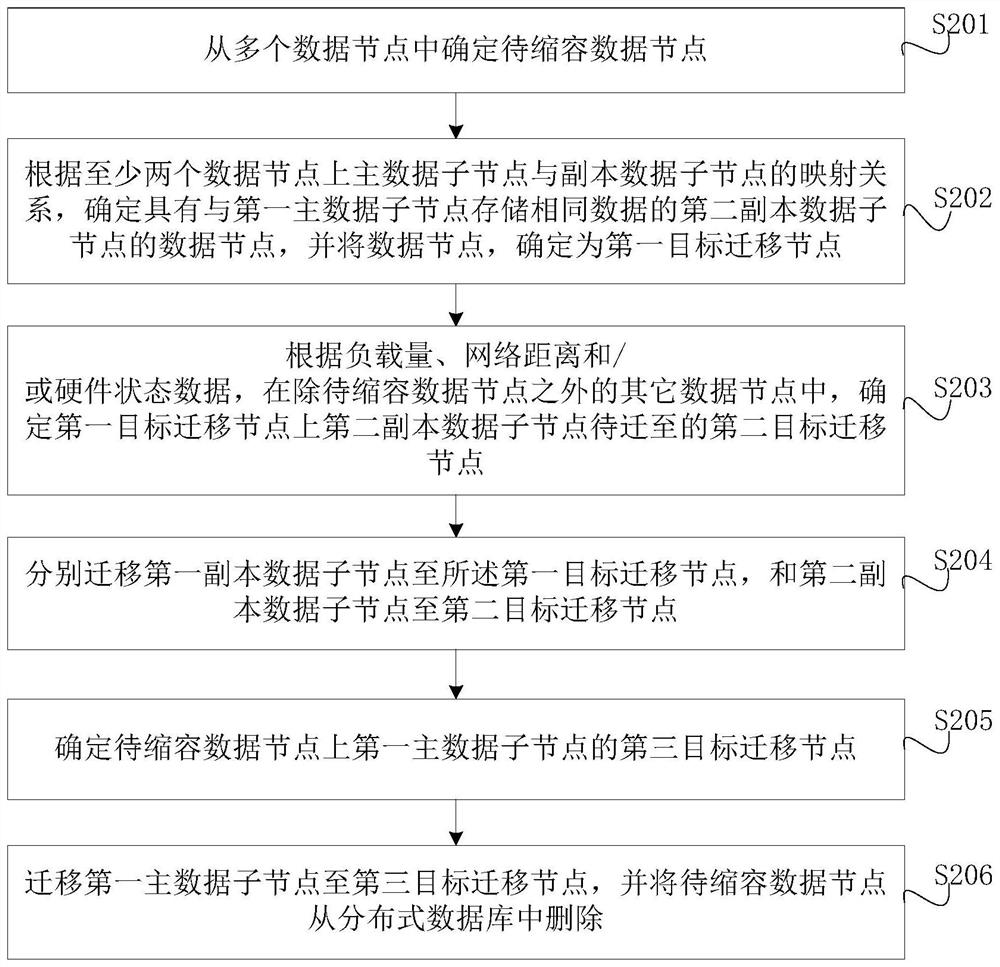
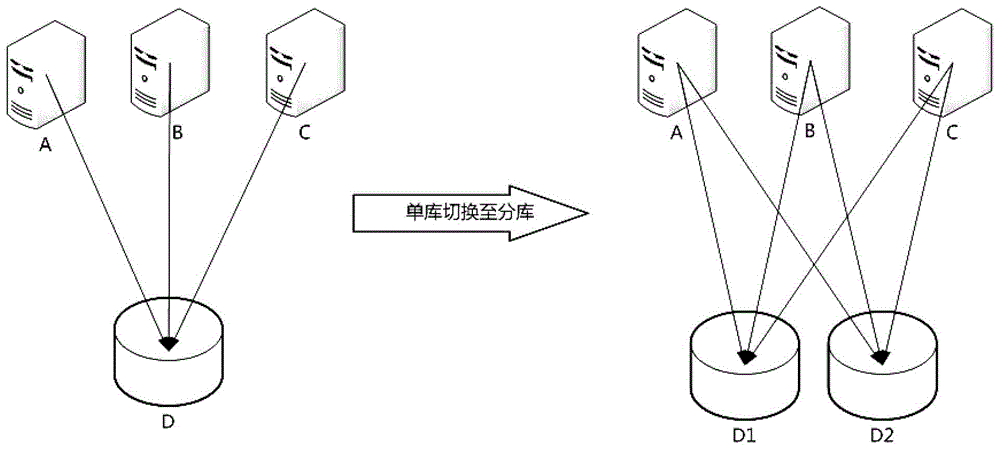
Distributed database capacity reduction method and device, equipment and medium
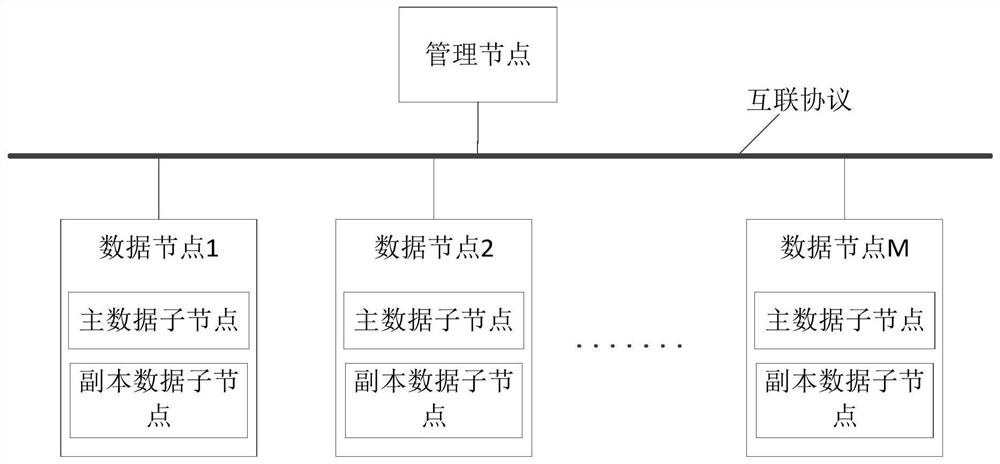
PendingCN114253936ANormal serviceDatabase updatingDatabase distribution/replicationEngineeringData library
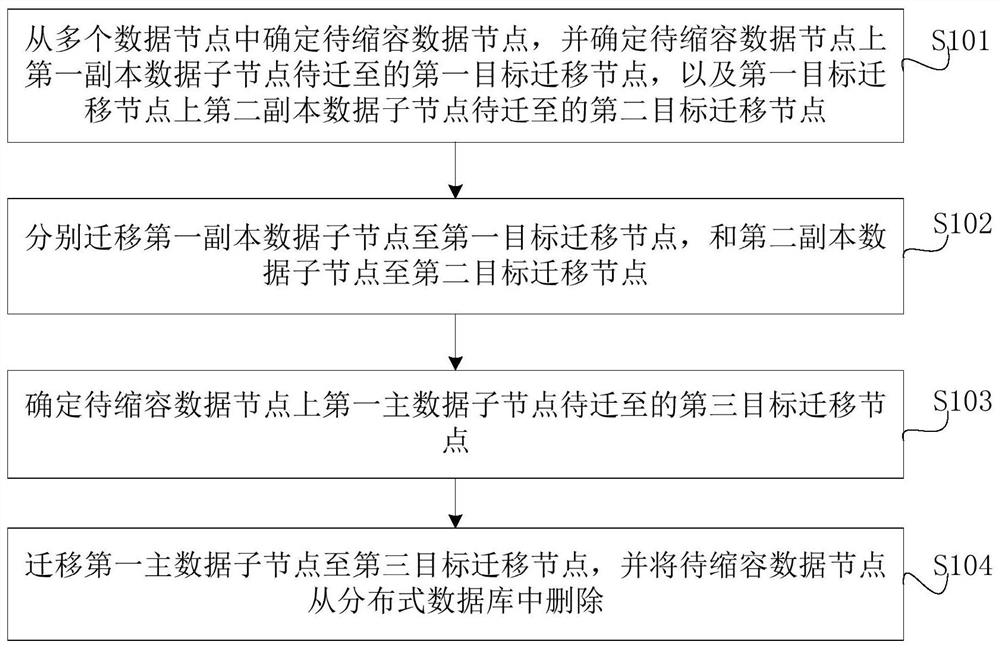
The invention discloses a capacity reduction method and device for a distributed database, equipment and a medium. The method comprises the following steps: determining a data node to be subjected to capacity reduction from a plurality of data nodes, and determining a first target migration node to which a first copy data child node on the data node to be subjected to capacity reduction is to be migrated and a second target migration node to which a second copy data child node on the first target migration node is to be migrated; respectively migrating the first copy data sub-node to a first target migration node and the second copy data sub-node to a second target migration node; determining a third target migration node to which the first main data child node on the data node to be subjected to capacity reduction is to be migrated; and migrating the first main data child node to a third target migration node, and deleting the data node to be subjected to capacity reduction from the distributed database. According to the method and the device, the capacity of the distributed database is reduced through an online capacity reduction scheme, so that the distributed database does not need to interrupt service in the capacity reduction process, and the service can be normally provided.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
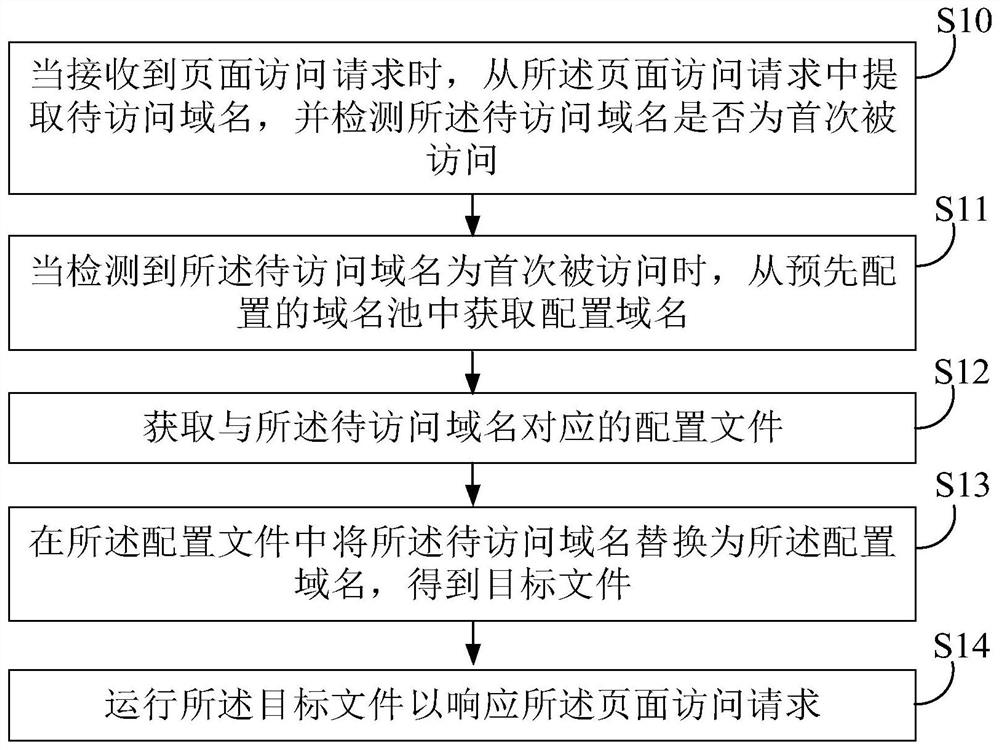
Domain name access method and device, electronic equipment and storage medium
The invention relates to a domain name resolution technology, and provides a domain name access method and device, electronic equipment and a storage medium. According to the method, when a page access request is received, a domain name to be accessed is extracted from the page access request, whether the domain name to be accessed is accessed for the first time or not is detected, and when the domain name to be accessed is accessed for the first time, a configuration domain name is obtained from a pre-configured domain name pool, a configuration file corresponding to the domain name to be accessed is obtained, the domain name to be accessed is replaced with the configuration domain name in the configuration file to obtain a target file, and the target file operates to respond to the pageaccess request. Although the domain name of the webpage is blocked or hijacked, the webpage can still be accessed normally. In addition, the invention also relates to a blockchain technology, and thetarget file can be stored in a blockchain.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
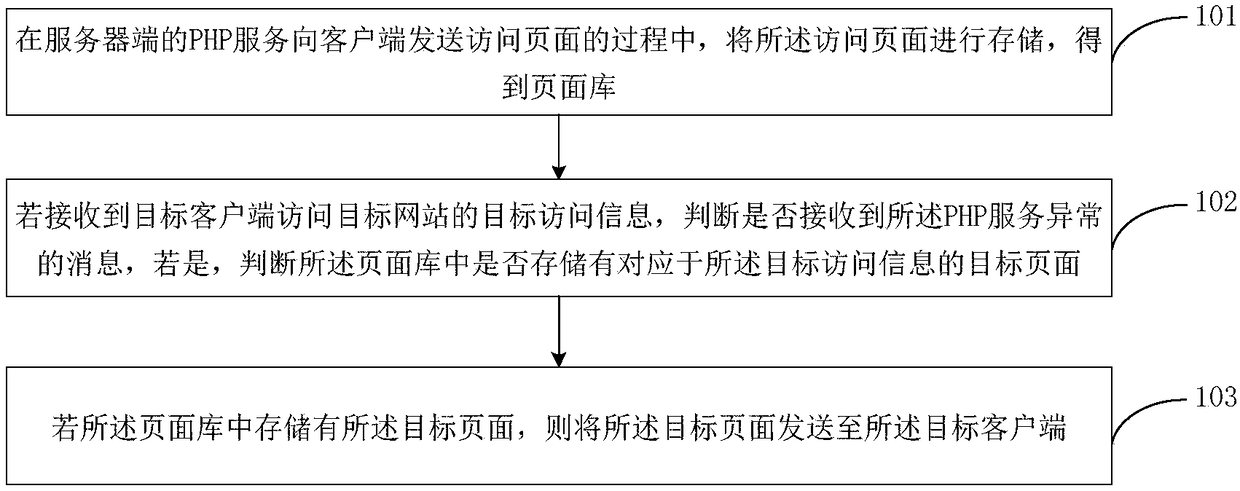
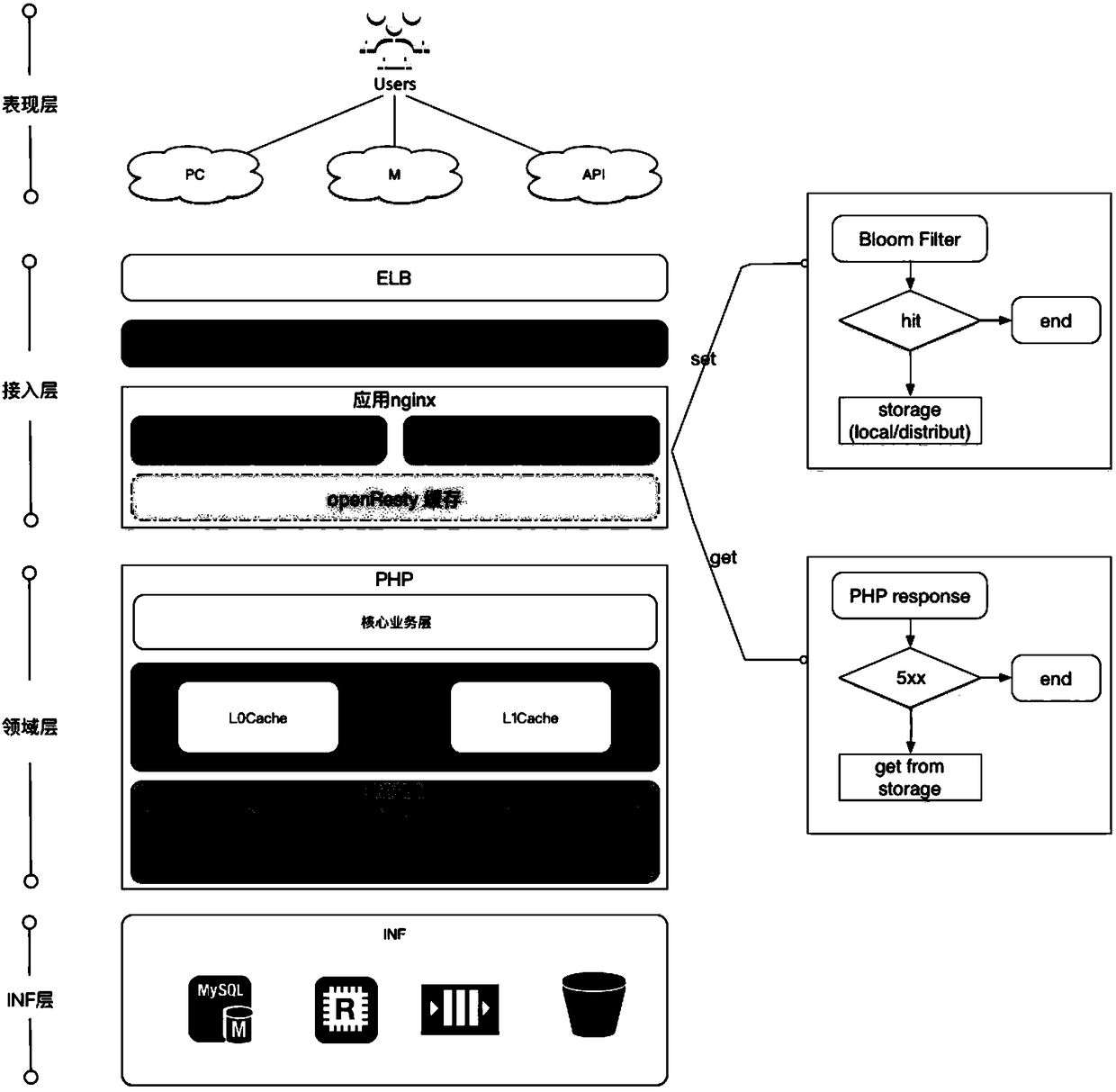
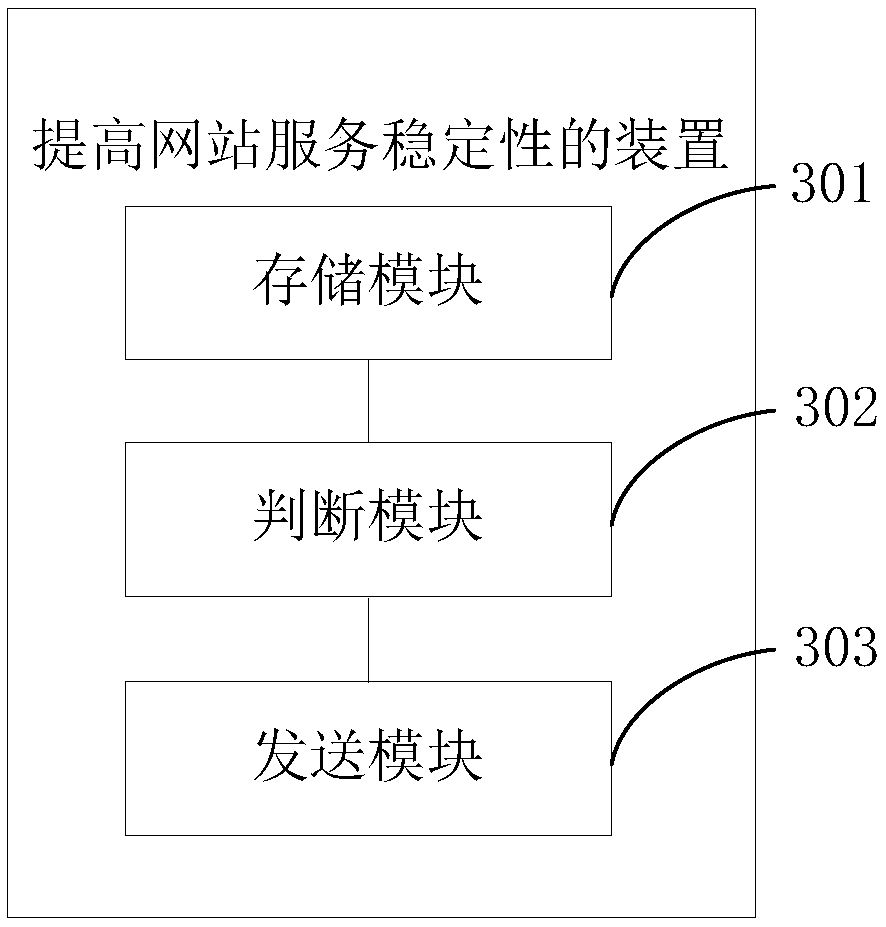
Method, system and apparatus for improving website service stability
ActiveCN108400884AImprove stabilityNormal serviceWebsite content managementData switching networksWeb pageWeb site
The embodiment of the invention discloses a method, system and apparatus for improving website service stability. According to the method, when the PHP service of a server has no abnormality, an access page sent to a client is stored, thereby after the PHP service is abnormal, the corresponding access page is provided for the client through the stored access page. According to the method, after the PHP service is abnormal, it is ensured that the normal service is provided for the client to a certain extent, and compared with the method in which the webpage cannot be accessed once the PHP service is faulty, the method has the advantages of improving the stability of website access.
Owner:KE COM (BEIJING) TECHNOLOGY CO LTD
Wireless communication method, terminal equipment and network equipment
ActiveCN112367716AImprove experienceNormal serviceConnection managementHigh level techniquesTime informationTerminal equipment
Provided are a wireless communication method, terminal equipment and network equipment, the terminal equipment can trigger and release at least one wireless connection other than a first wireless connection among a plurality of wireless connections maintained by the terminal equipment, therefore, the user experience can be improved when adverse effects such as terminal body temperature rise, powerconsumption increase and terminal battery power shortage occur. The wireless communication method comprises the following steps: the terminal equipment sends first information, wherein the first information is used for requesting to release at least one wireless connection except a first wireless connection in a plurality of wireless connections maintained by the terminal equipment; wherein the first information comprises time information and / or a connection release reason, the time information is used for indicating that the terminal equipment does not expect to add a time window of the wireless connection, and the connection release reason is used for indicating a reason for releasing the at least one wireless connection.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
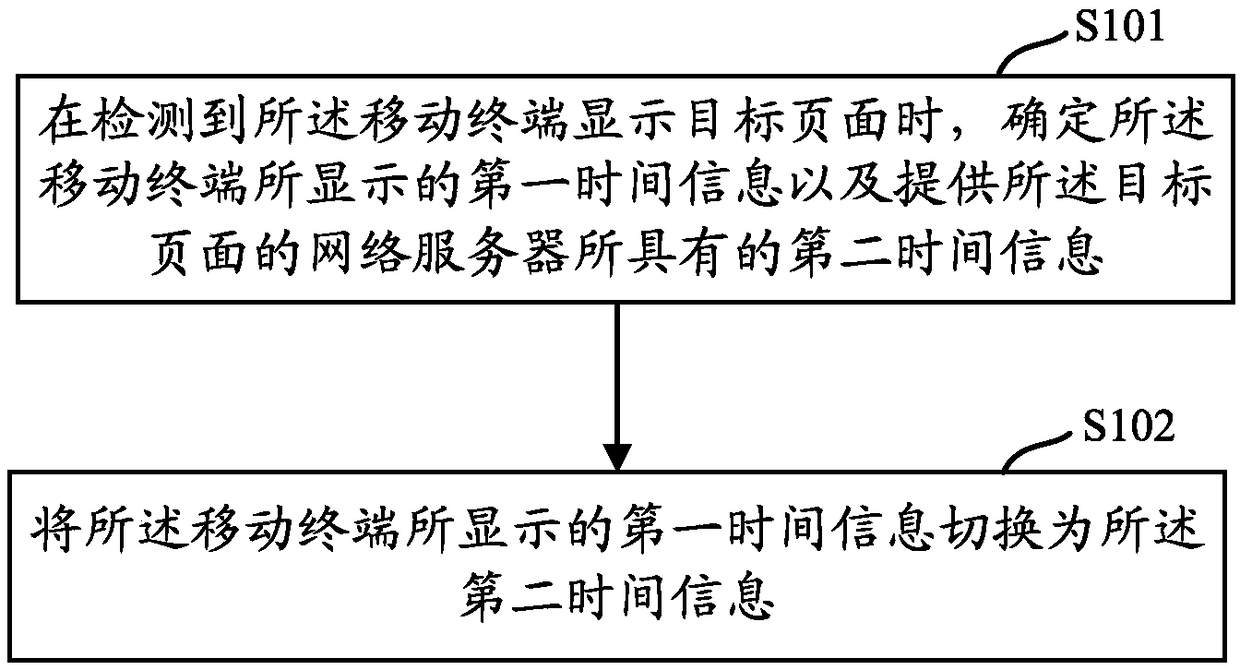
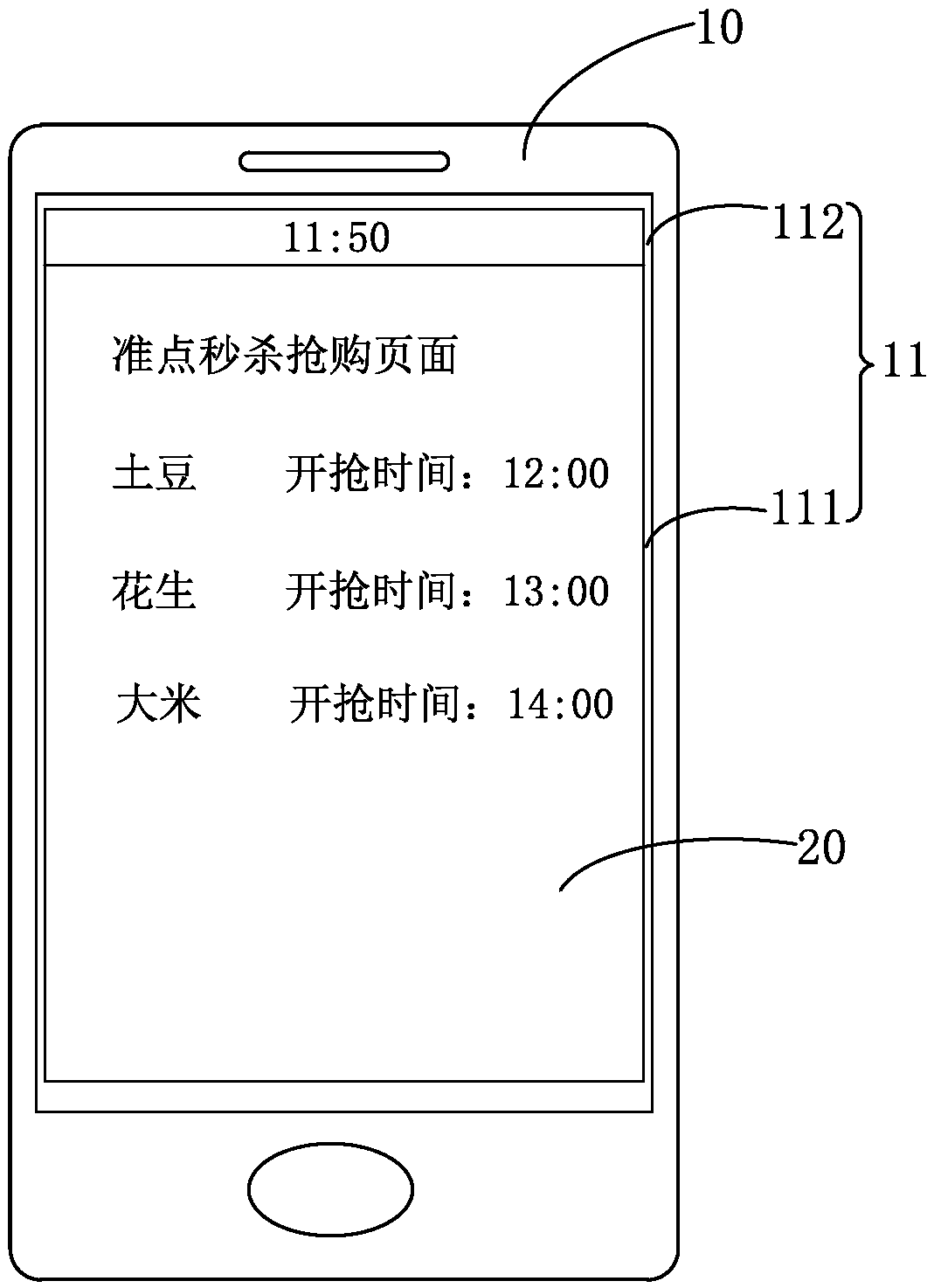
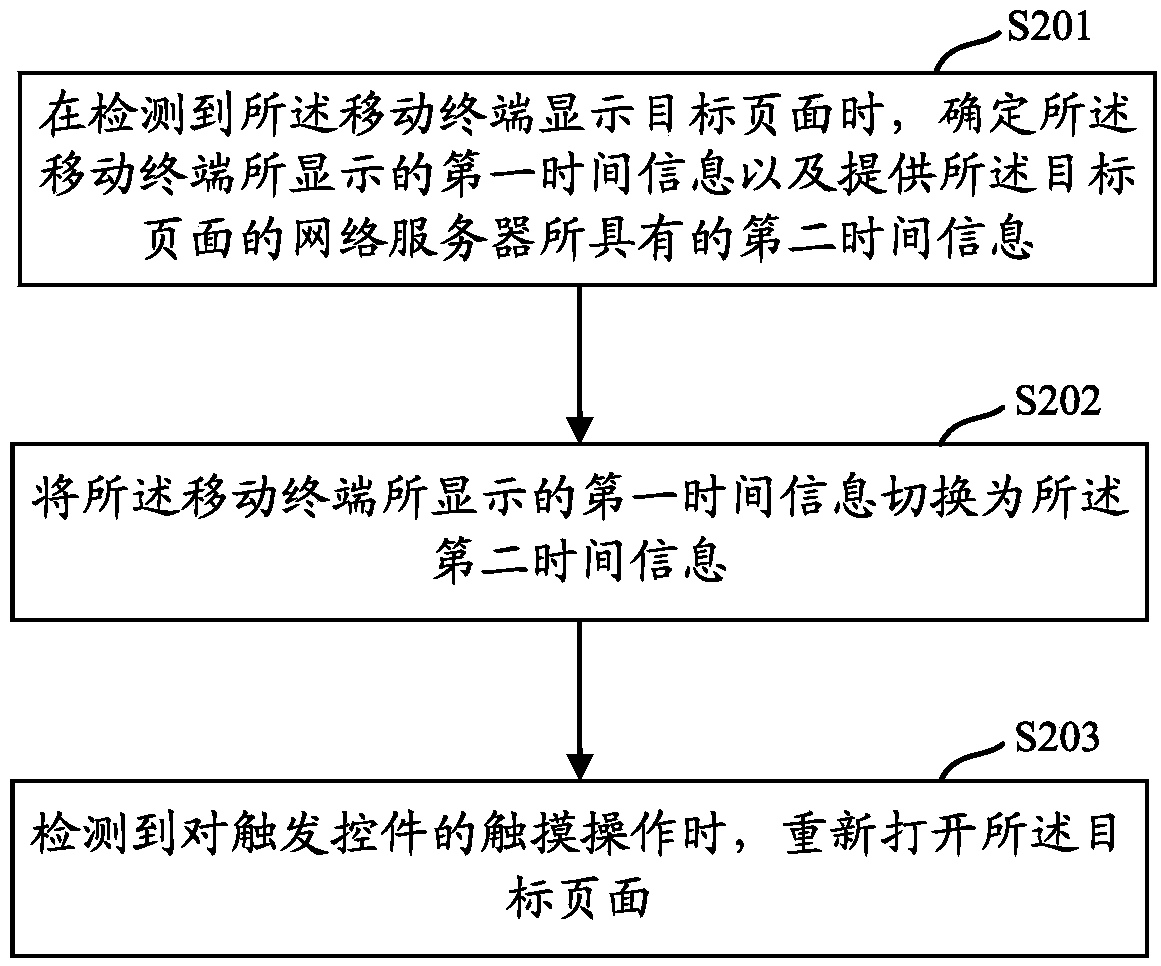
Time display method and mobile terminal
PendingCN108650397ANormal serviceSubstation equipmentSpecial data processing applicationsTime informationNetwork service
The invention discloses a time display method and a mobile terminal applying the method. The method comprises the following steps: when detecting that the mobile terminal displays a target page, determining first time information displayed by the mobile terminal and second time information of a network server providing the target page; and switching the first time information displayed by the mobile terminal into the second time information. In the embodiment of the invention, when the target page is displayed by the mobile terminal, the first time information displayed by the mobile terminalis switched into the second time information of a target page server, so that a user can simultaneously view the second time information synchronized with the target page when viewing the target page,and the user can normally use some network services with relatively high time requirements according to the time displayed by the mobile terminal.
Owner:VIVO MOBILE COMM CO LTD
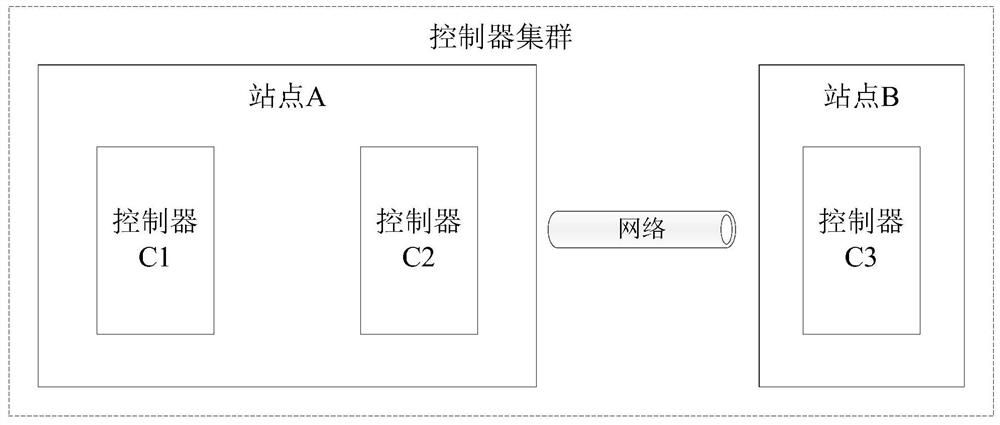
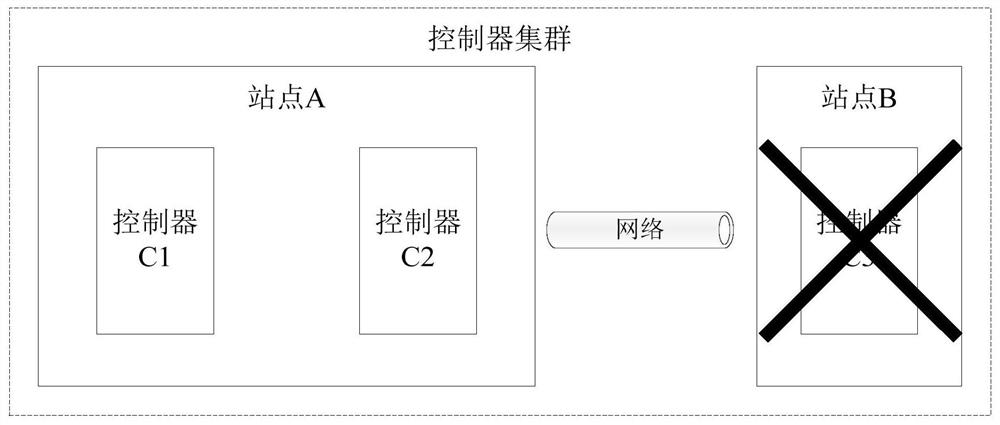
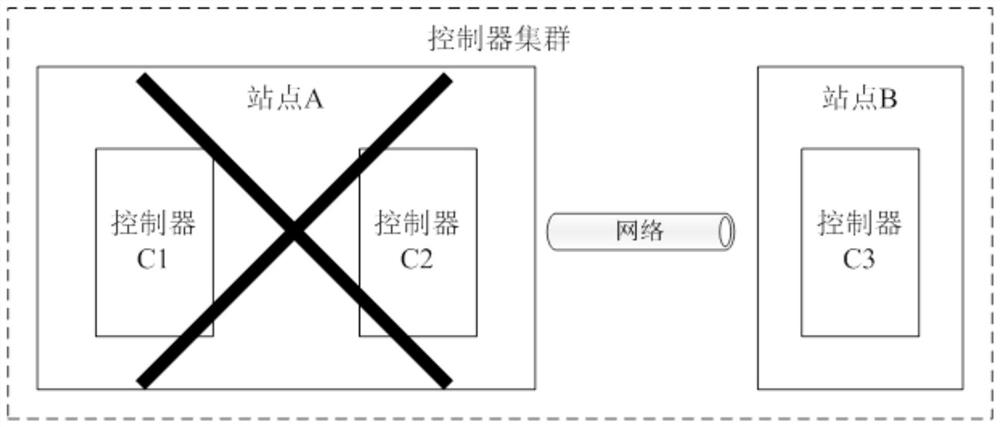
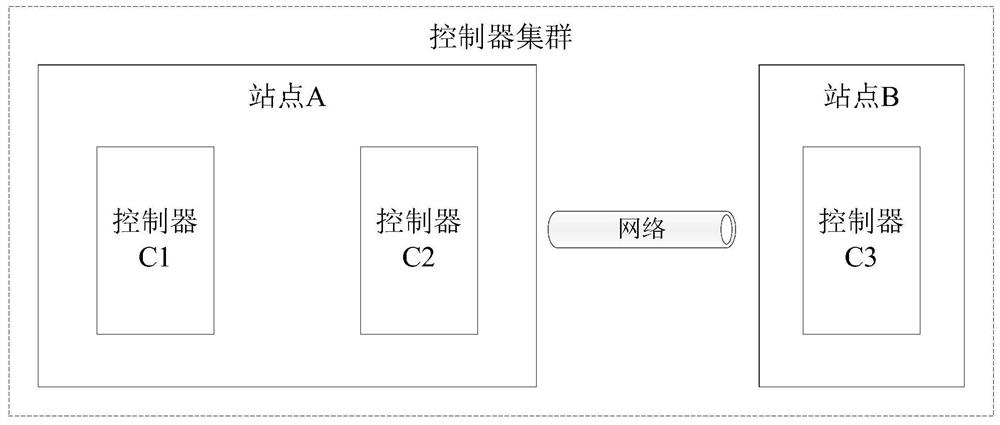
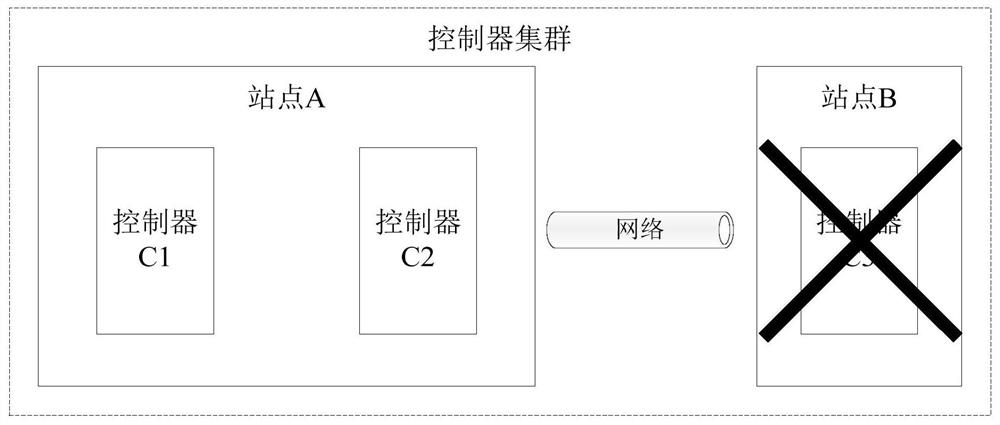
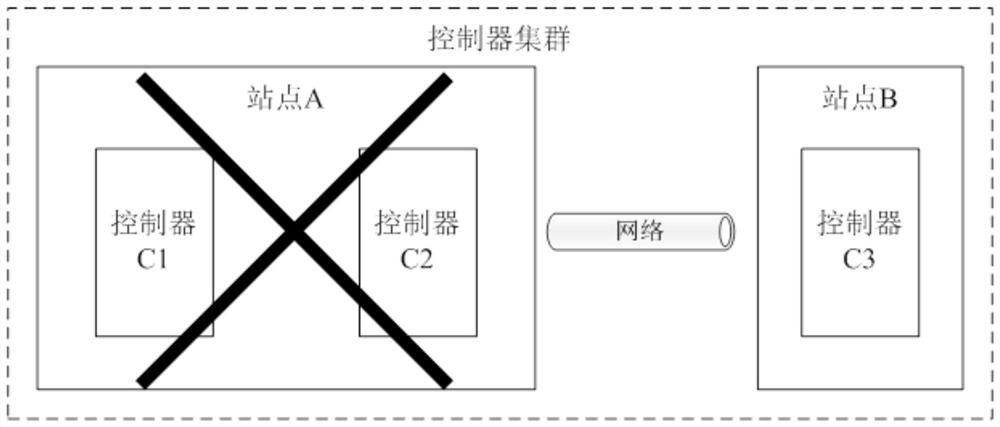
Controller cluster fault processing method and device, controller and controller cluster
The embodiment of the invention provides a controller cluster fault processing method and device, a controller and a controller cluster. The controller cluster comprises a first controller and 2N + 1second controllers. The node attribute of the first controller is a learner, and the controller is forbidden to participate in election and voting of the main controller; the node attribute of the second controller is an elector, and the controller is allowed to participate in election and voting of the main controller. The first controller detects whether each second controller fails or not; if the first controller detects that the N + 1 second controllers fail, the node attribute of the first controller is changed into an elector. Under the condition that N + 1 second controllers break down,the first controller changes the node attributes of the first controller into electors; at the moment, the node attributes of the N + 1 controllers are the electors and exceed half of the electors, and the purpose that the controller cluster normally provides service under the condition that the controllers break down is achieved.
Owner:NEW H3C SECURITY TECH CO LTD
Defense method and device for interest packet flooding attack in content-centric network
ActiveCN106357641BImprove accuracyReduce false positivesTransmissionDetection thresholdKullback–Leibler divergence
The invention provides a method and device for defending interest flooding attacks in an information centric network and relates to the field of network security. The method includes: statistically counting the entropy of the names of interest packets received by a router in the information centric network after different moments according to a preset window; using a cumulative sum algorithm to process the obtained entropy to obtain the accumulative values of the entropy at different moments; judging whether the accumulative values are smaller than a preset attack detecting threshold or not, if not, judging that interest flooding attacks are detected, and using a prefix determining algorithm based on relative entropy to search the prefix set of the names of the interest packets so as to obtain attack prefixes; generating data packets containing the attack prefixes according to the attack prefixes, and transmitting the data packets to the access router where an attacker is located according to the router information of the interest packets, containing the attack prefixes, recorded in the pending interest table of the router so as to allow the access router to perform corresponding access limitation on the received interest packets according to the attack prefixes in the data packets.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
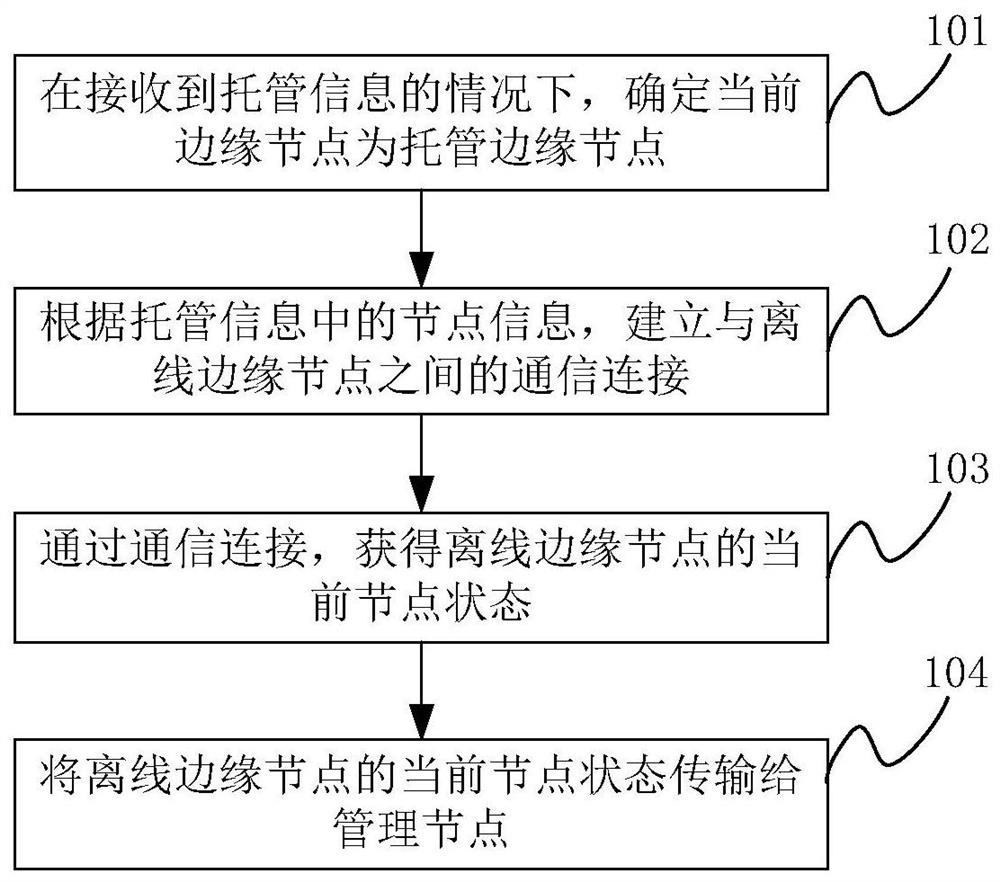
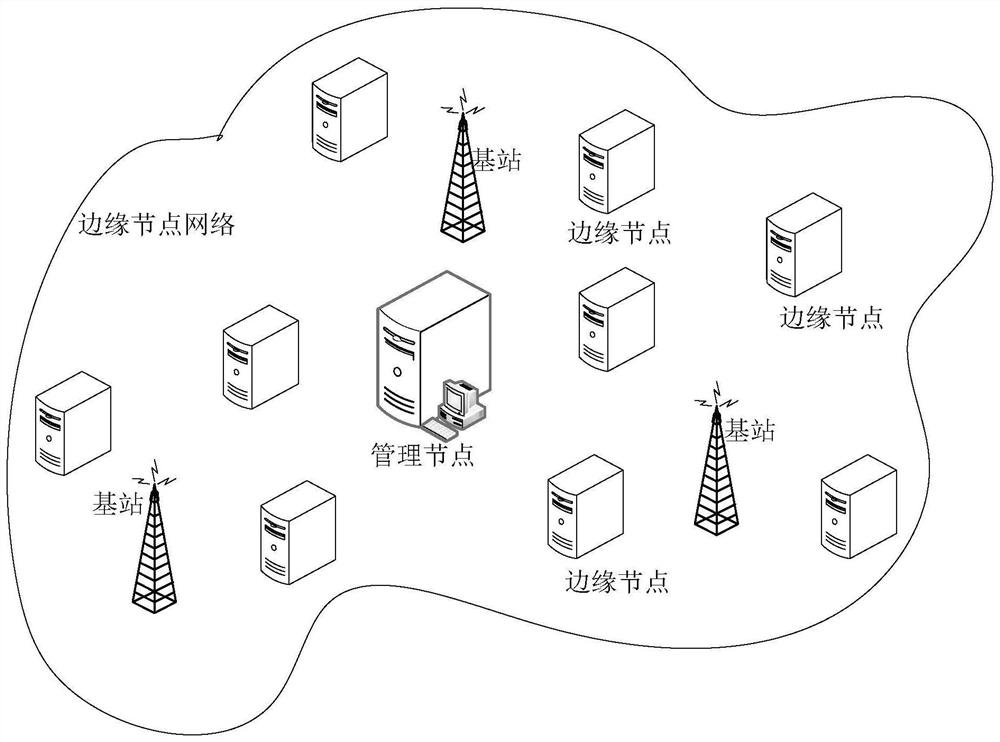
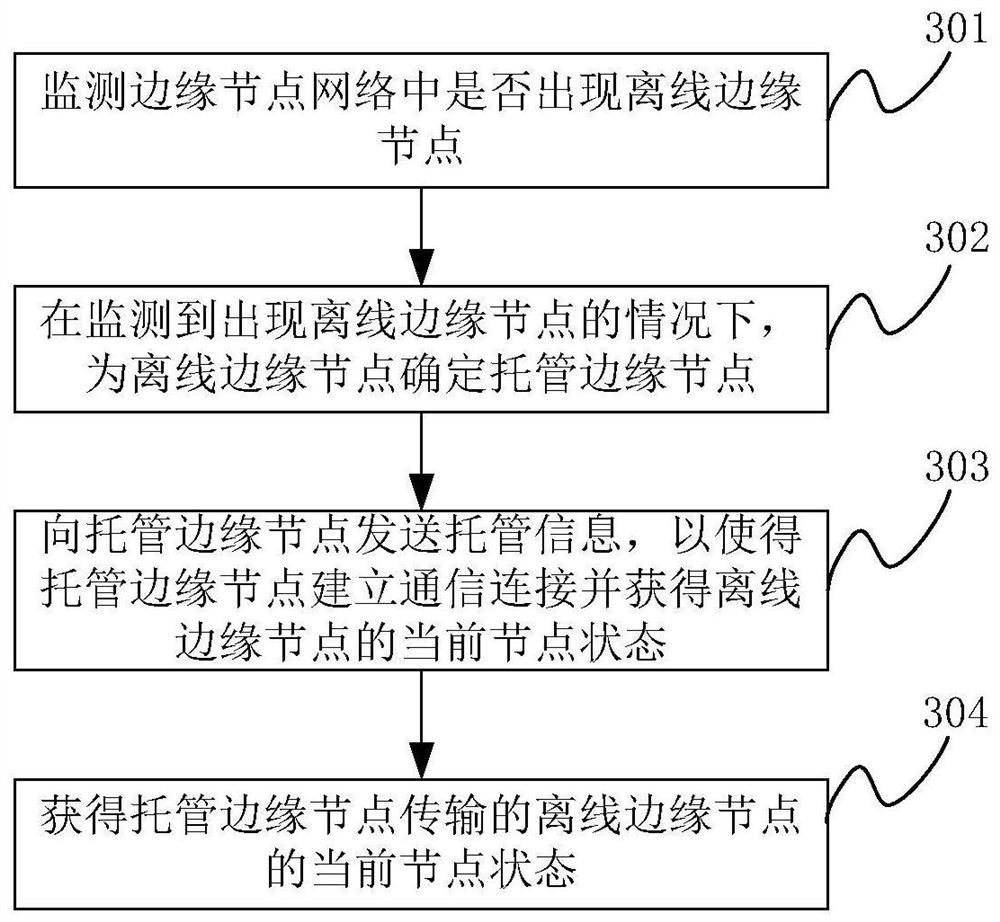
Control method and device
The invention discloses a control method and device. The control method comprises the following steps: monitoring whether an offline edge node appears in an edge node network; when it is monitored that at least one off-line edge node appears, determining a trusteeship edge node for the off-line edge node; sending trusteeship information to the trusteeship edge node, so that the trusteeship edge node establishes communication connection with the offline edge node according to the node information of the trusteeship offline edge node contained in the trusteeship information; obtaining the current node state of the offline edge node through the communication connection; and obtaining the current node state of the offline edge node transmitted by the trusteeship edge node.
Owner:LENOVO (BEIJING) LTD
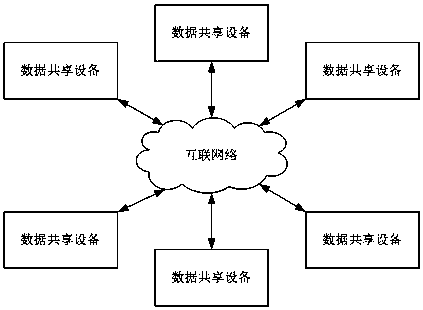
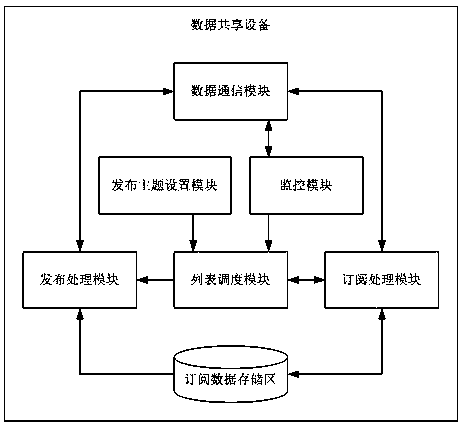
An Electronic Whiteboard Data Sharing System Based on Subscription Information Publishing
ActiveCN106230914BReduce chance of interruptionFix stability issuesData switching networksData synchronizationWhiteboard
The present invention provides an electronic whiteboard data sharing system based on subscription information publishing. By data communication connection between each data sharing device in the system, the electronic content data synchronization of the subscription publishing mechanism is performed between different data sharing devices. At the same time, distributed backup and storage of electronic whiteboard content data is also performed on different data sharing devices. Once the data sharing device as the information publisher has abnormal operation status, each corresponding information subscriber will start the corresponding subscription topic. The allocation and scheduling mechanism of information publishers and information subscribers in the type, the other information subscribers of the corresponding subscription topic type with normal operation status determine the new proxy information publisher according to the principle of the highest subscription priority, and execute the corresponding subscription topic on their behalf The type of electronic whiteboard content data release task reduces the probability of interruption of electronic whiteboard data sharing services, and improves the fluency and stability of information sharing services provided by the system.
Owner:CHONGQING RUICHANG TECH
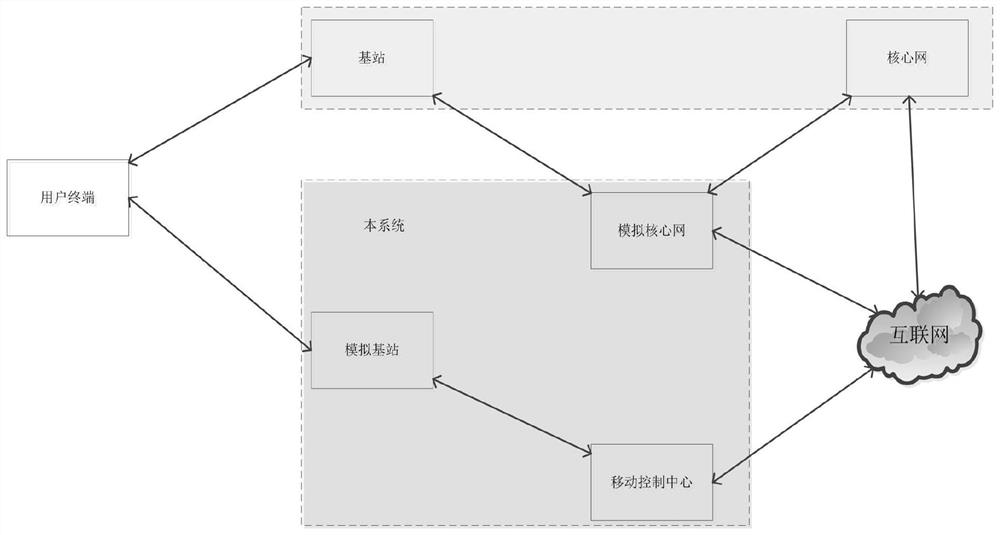
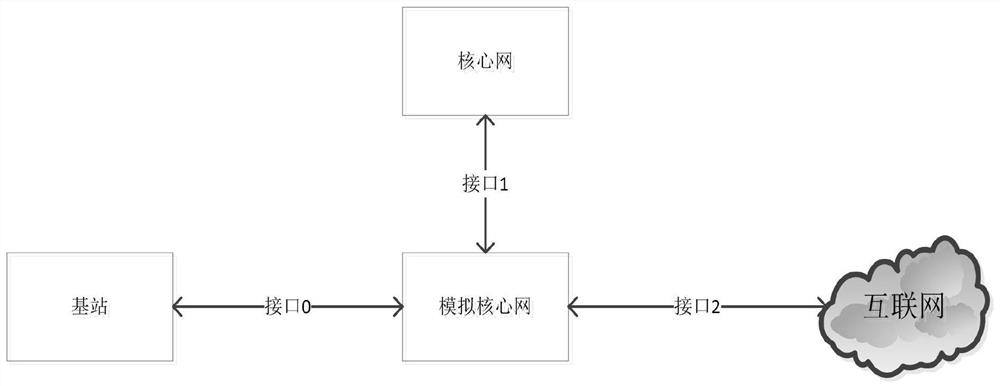
Monitoring system and method based on 5G wireless communication technology
The invention discloses an interception system and method based on the 5G wireless communication technology. The interception system comprises a user terminal, a public network base station, a public network core network and the Internet which are connected in sequence. The mobile control center is accessed to the Internet; the simulation base station is respectively connected with the user terminal and the mobile control center; an interface 0 of the analog core network is connected with the public network base station, an interface 1 of the analog core network is connected with the public network core network, and an interface 2 of the analog core network is accessed to the Internet. According to the monitoring system and method, the user terminal accessed to the 5G system is monitored; and meanwhile, the target user terminal can normally access the network of the operator through the simulation base station, so that the user terminal can use all normal services, and the access method can ensure that the user terminal does not sense whether to access the simulation base station or not.
Owner:西安讯智通达科技有限公司
Method for obtaining terminal context, method for location management, system and network element
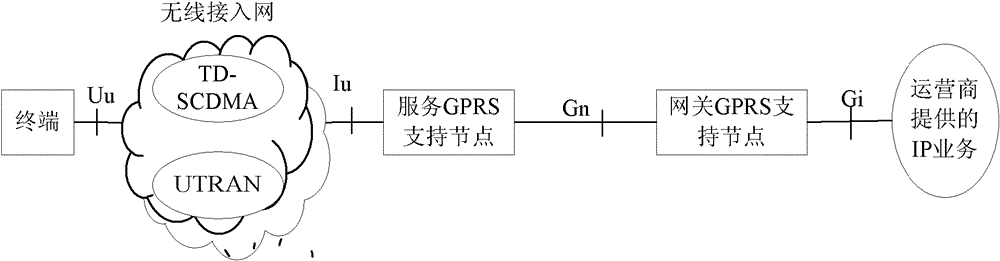
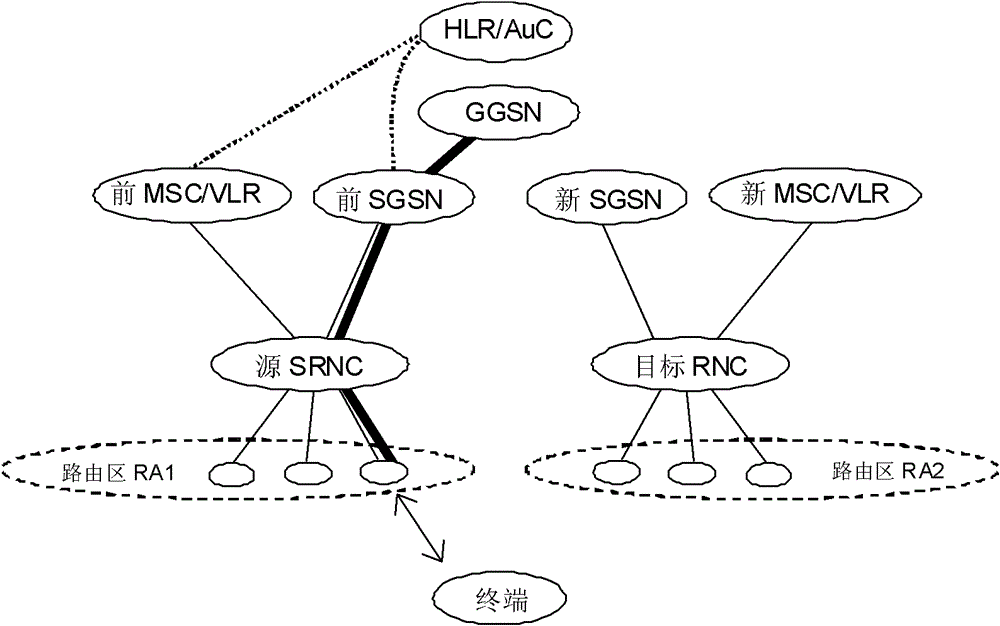
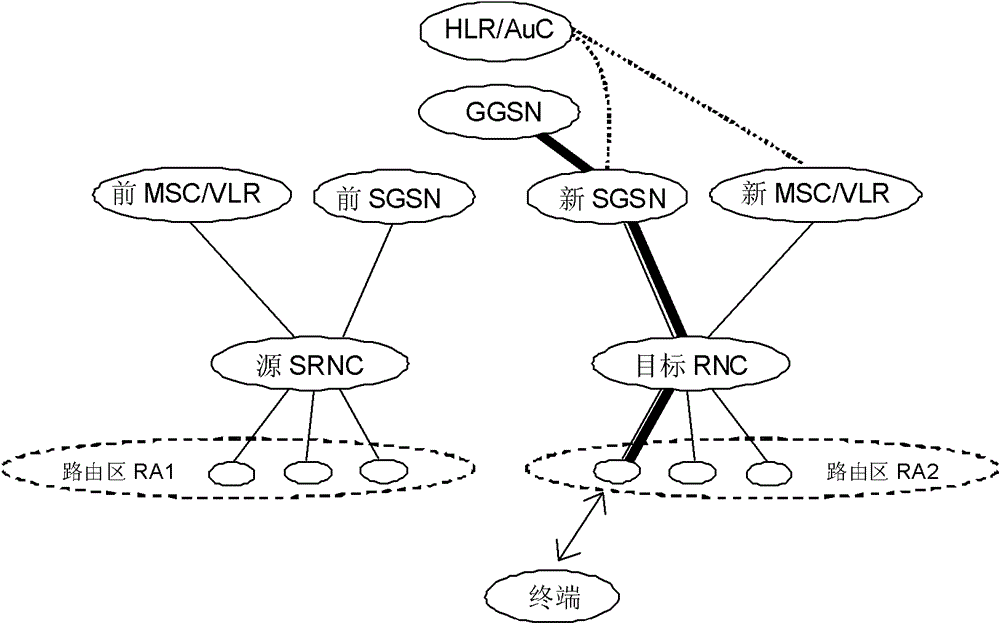
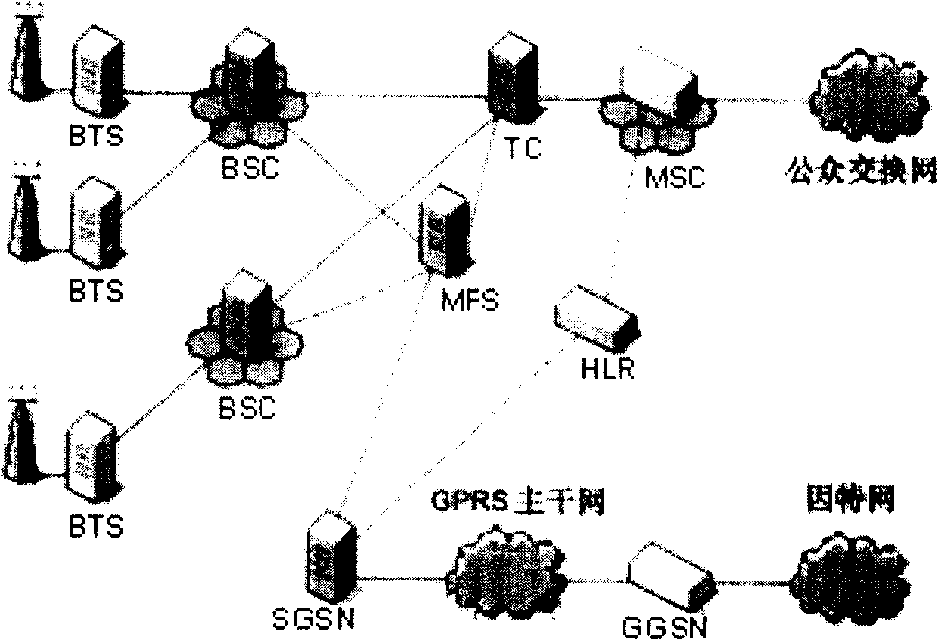
ActiveCN102625275BNormal serviceSolve roundabout problemsNetwork data managementComputer terminalComputer science
The present invention relates to a method for acquiring terminal context, a method for position management, a system, and a network element. The method for acquiring terminal context includes: a new gateway GPRS support node (GGSN) sends a message to the original GGSN to request context information of a mobile terminal , which carries the identifier of the terminal; the old GGSN provides context information of the terminal to the new GGSN, and the context information includes the PDP context of the terminal. The invention solves the problem that the new GGSN cannot serve normally, and at the same time solves the problem of the circuitous path through the triggering of the new SGSN.
Owner:昆山创智汇知识产权运营有限公司
Database processing method and system, electronic equipment and storage medium
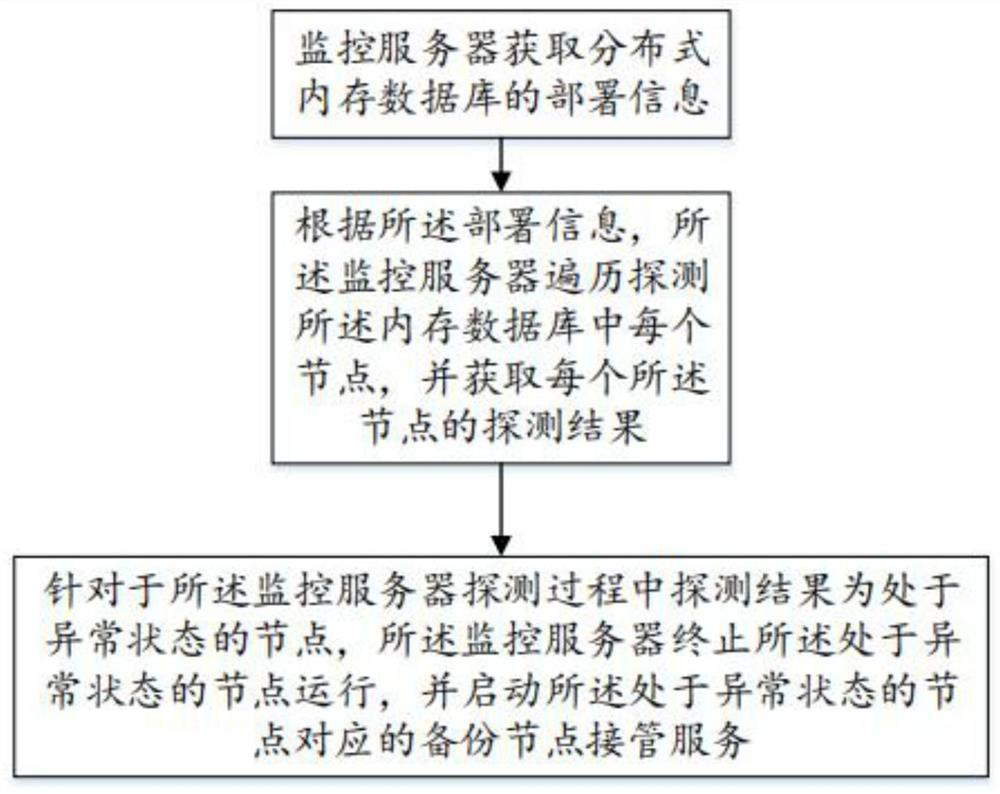
PendingCN112131310ANormal serviceDatabase distribution/replicationSpecial data processing applicationsIn-memory databaseDistributed memory
The invention discloses a database processing method and system, electronic equipment and a storage medium, and belongs to the technical field of communication, and the method comprises the steps thata monitoring server obtains deployment information of a distributed memory database; according to the deployment information, the monitoring server traverses and detects each node in the memory database, and obtains a detection result of each node; and for the node with the detection result in the abnormal state in the detection process of the monitoring server, the monitoring server terminates the operation of the node in the abnormal state and starts a backup node corresponding to the node in the abnormal state to take over the service. According to the invention, the abnormal nodes of thedistributed memory database can be automatically identified, and the abnormal nodes are replaced by the backup nodes, so that services can be normally provided when the distributed memory database isabnormal.
Owner:北京思特奇信息技术股份有限公司
Building public lighting supervision system and supervision method
InactiveCN107016833AImprove the level of intelligent managementTimely monitoringAlarmsTransport engineeringComputer module
The invention belongs to the technical field of building lighting, and specifically relates to a building public lighting supervision system and a supervision method. The building public lighting supervision system comprises light sensors distributed in all areas needing lighting in a building, a regional sensor information collection unit, a monitoring center, a database, an alarm system, and a management server. The light sensors are connected with the regional sensor information collection unit. The regional sensor information collection unit communicates with the monitoring center through a built-in communication module. The monitoring center is connected with the database and the alarm system. The management server is connected with the monitoring center. Through the building public lighting supervision system and the supervision method provided by the invention, lighting facilities in a building can be monitored in time, and lighting facilities needing maintenance can be found in time. Therefore, the level of intelligent management of lighting facilities in buildings is improved, and normal service of lighting facilities in buildings is ensured.
Owner:SHENZHEN RUIRONGCHUANG ELECTRONICS TECH CO LTD
Dynamic community adjusting method
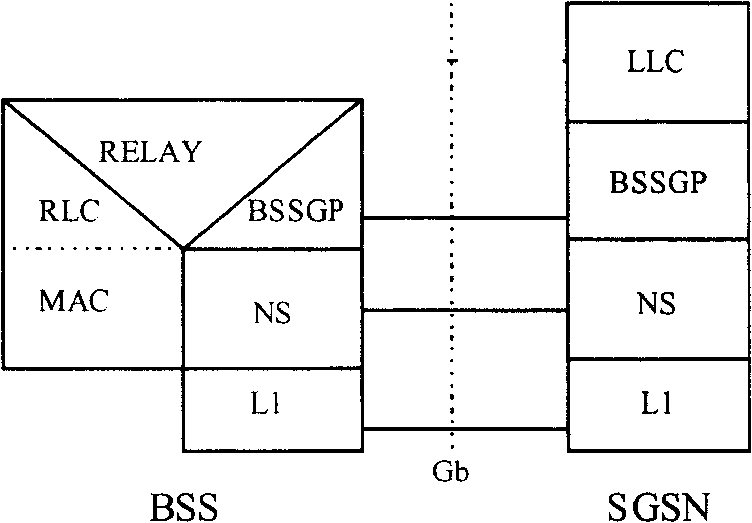
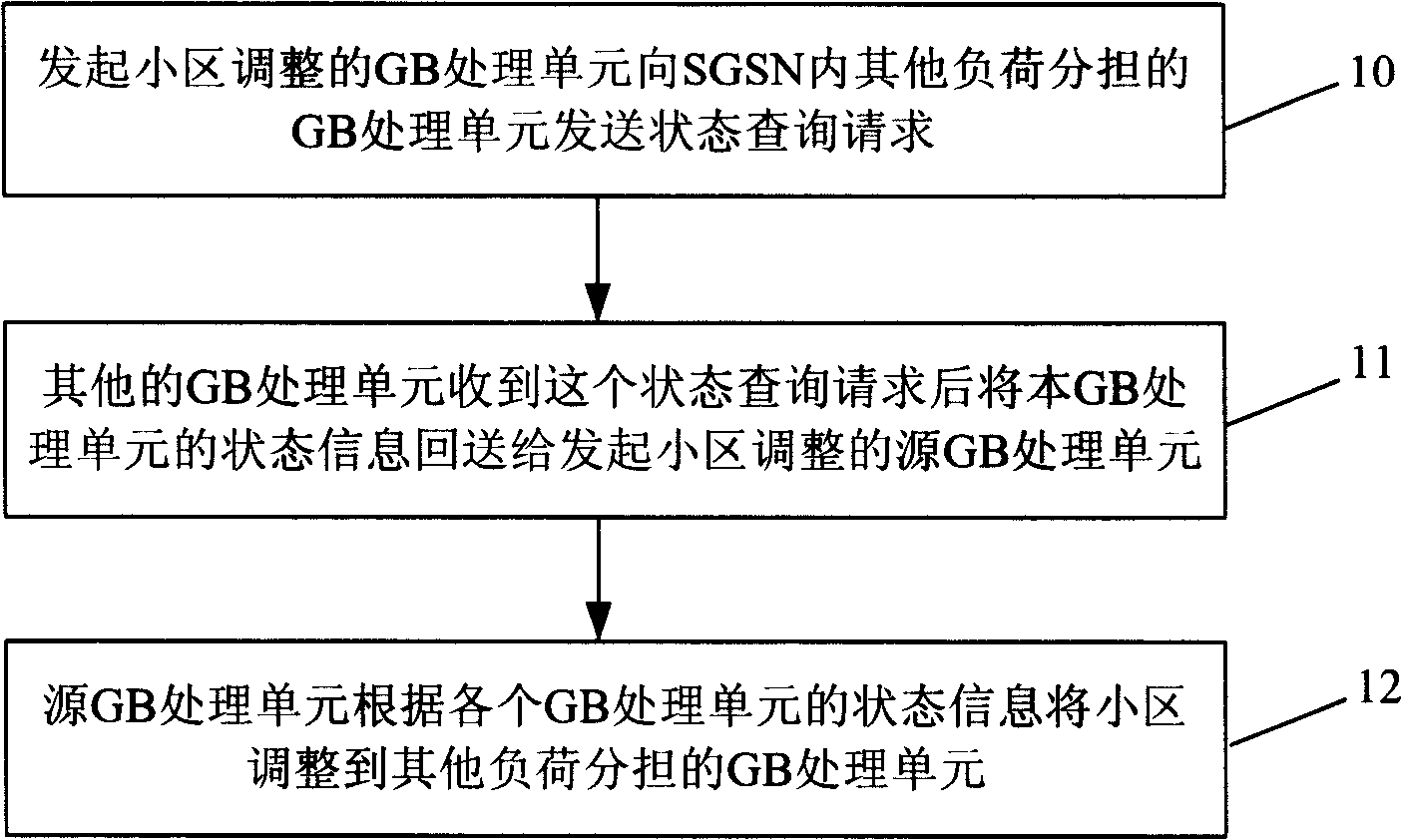
InactiveCN100415035CReasonable useIncrease flexibilityNetwork traffic/resource managementRadio/inductive link selection arrangementsGeneral Packet Radio ServiceComputer network
The method is applicable to general packet radio service (GPRS) system. The method includes steps: (1) source GB process unit of initiating adjustment of subzone sends request for state query to other GB of sharing burthen in serving GPRS support node SGSN; (2) receiving the said request, other GB returns own information of state to the source GB process unit; (3) based on information of state, the source GB process unit adjusts subzone to other GB process unit of sharing burthen. When GB process unit in 'hotspot area' occurs in network, the invention can adjust subzone in hotspot area to other GB process unit. Advantages are: in favor of using network resources reasonably, and raising flexibility for system to treat user access.
Owner:HUAWEI TECH CO LTD
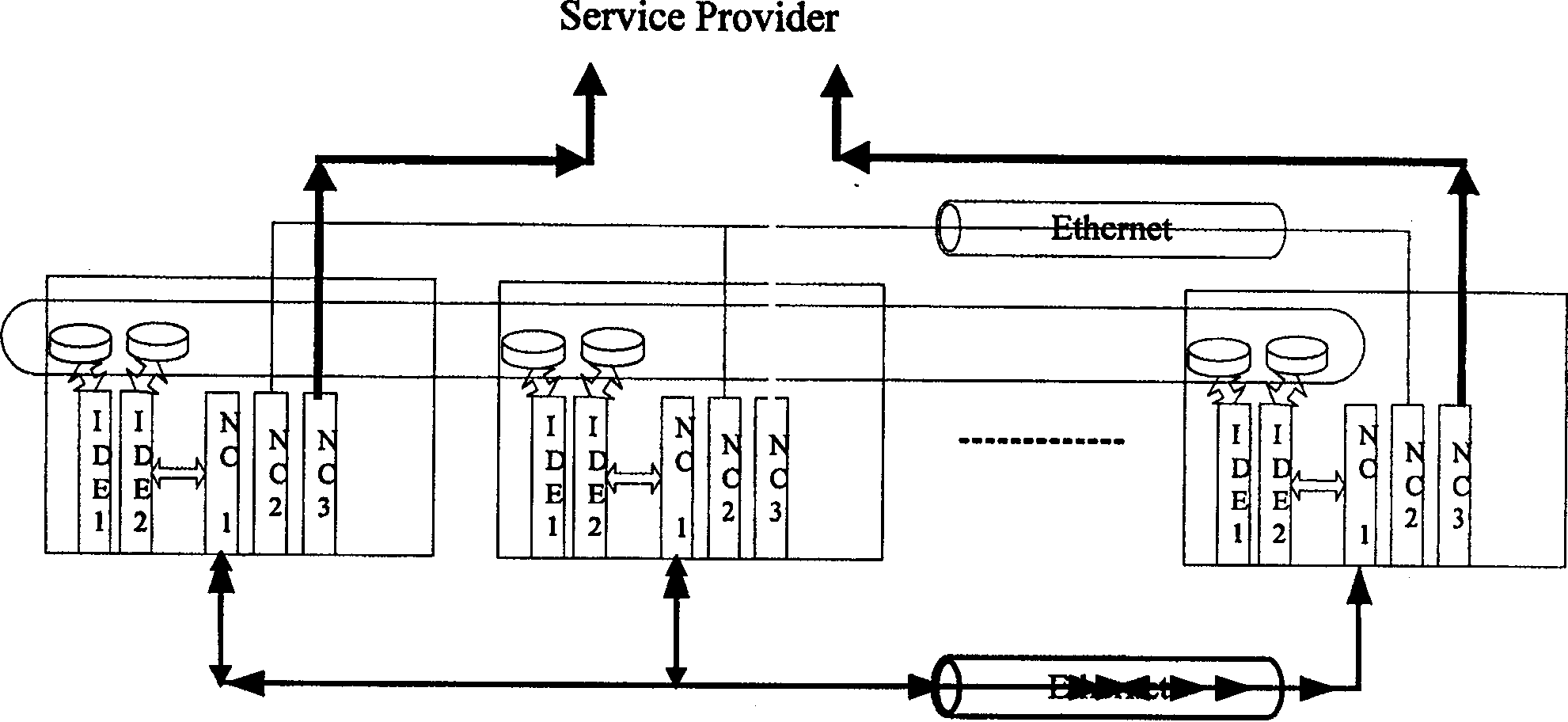
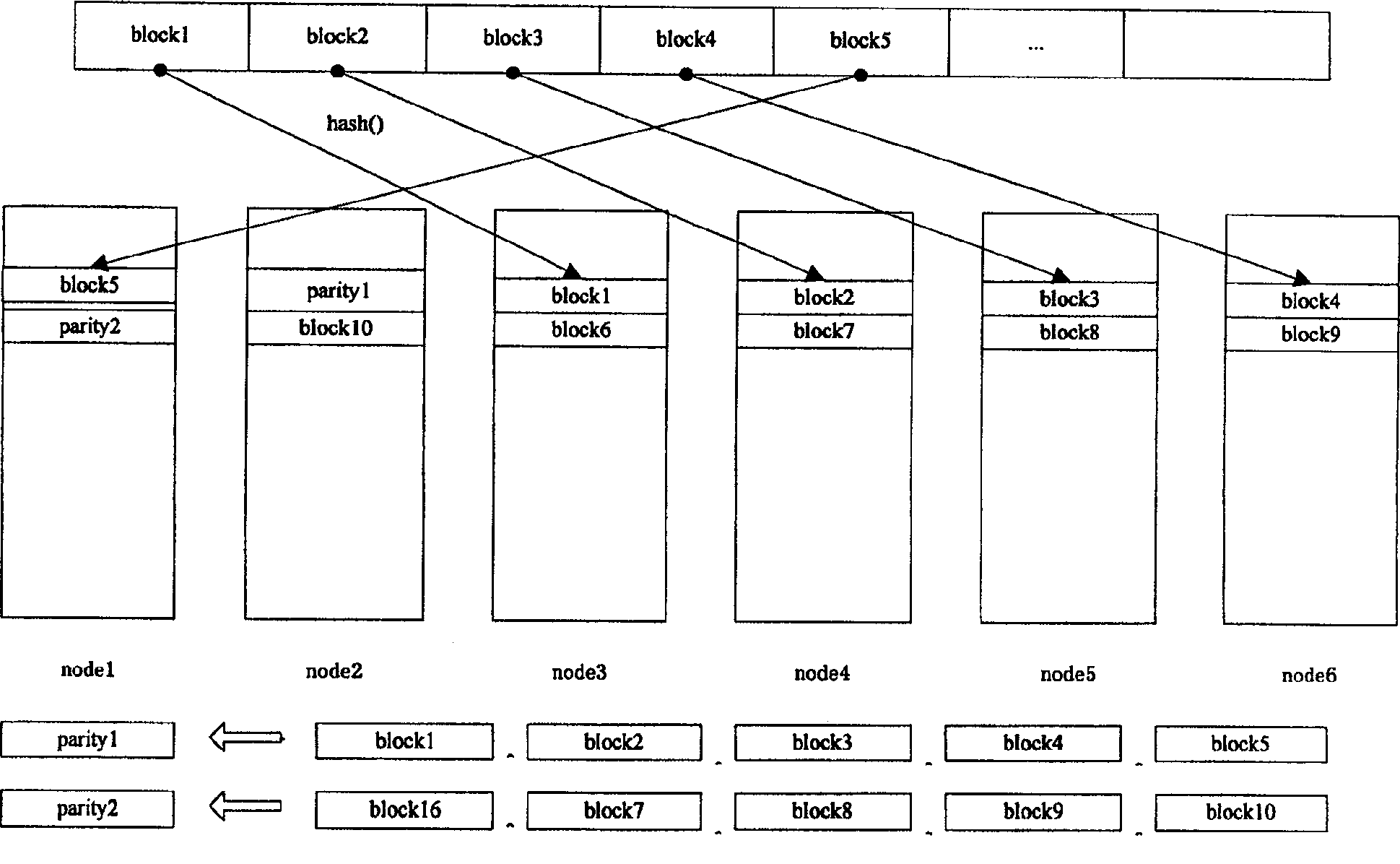
Multiple machine file storage system and method
ActiveCN100543743CImprove availabilityImprove performanceTransmissionSpecial data processing applicationsMulti machine systemMulti machine
The present invention provides a multi-machine file storage system and method, the system mainly includes a plurality of server nodes, each server node is connected by high-speed Ethernet, communicates through high-speed Ethernet, and each server node performs file storage in sections save and read. The method mainly includes: reading a corresponding data block from a file to be saved, and storing the read data block in segments in each server node in the multi-machine file storage system. With the invention, a low-cost, high-availability and high-performance multi-machine file storage scheme can be realized.
Owner:HUAWEI TECH CO LTD
Database switching method and database switching system
ActiveCN103810174BSmooth switchingNormal serviceError detection/correctionDatabase distribution/replicationData sourceComputer module
The invention provides a database switching method and a database switching system. The method comprises the steps that a compatible switch of each server is started to start a compatible logic module of the corresponding server, the compatible logic modules execute compatible processing of service compatibility of a main database and a spare database, a data source building logic module makes the main database be built into a main data source and makes the spare database be built into a spare data source on the basis of the switched-off states of data source switches; the data source switch of each server is switched on, so that each server is connected with the spare database rather than being connected with the main database, the compatible logic modules continue to execute compatible processing, and the data source building logic module makes the main database be built into the spare data source and makes the spare database be built into the main data source on the basis of the switched-on states of the data source switches; the compatible switch of each server is switched off after preset time.
Owner:ADVANCED NEW TECH CO LTD
A blockchain node deployment method and related equipment
ActiveCN110855791BAutomate deploymentNormal serviceSecuring communicationCommunications securityNode deployment
The embodiment of the present invention discloses a block chain node deployment method and related equipment. The method includes: obtaining a node deployment image file, which includes a communication security agent script, a node underlying script, and a node service script; running a communication The security proxy script establishes a secure connection with the node management device, and receives the node configuration file through the established secure connection; runs the underlying node script to obtain the node information of all nodes in the target blockchain from the node configuration file, and converts all nodes in the target blockchain The node information of the node is determined as the node information of the belonging blockchain; according to the node information of the belonging blockchain, run the node synchronization script, obtain the node status synchronization information from any node of the target blockchain, and update the first node status according to the node status synchronization information. The node status of a device; run the node service script and respond to the received user's blockchain service request. The deployment efficiency of blockchain nodes can be improved through the present invention.
Owner:TENCENT TECH (SHENZHEN) CO LTD
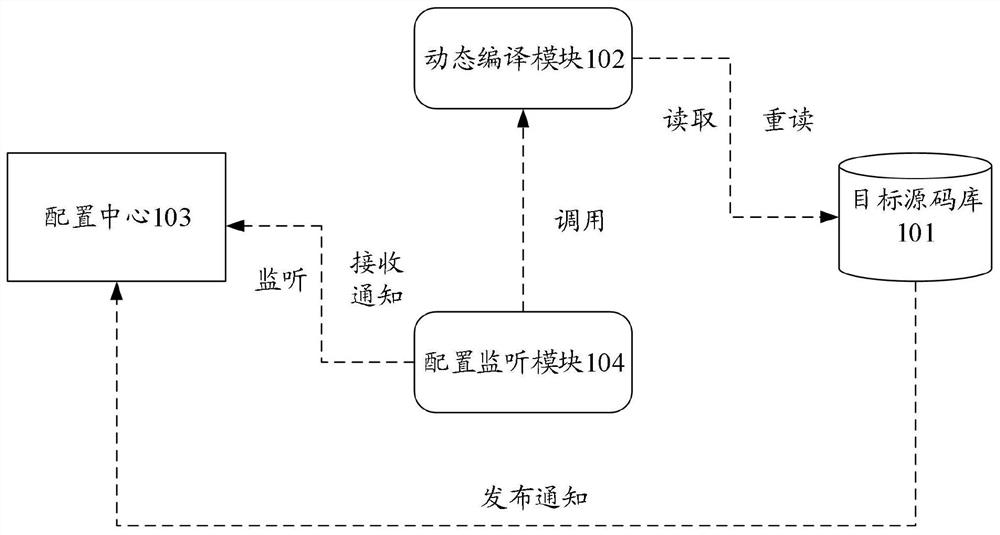
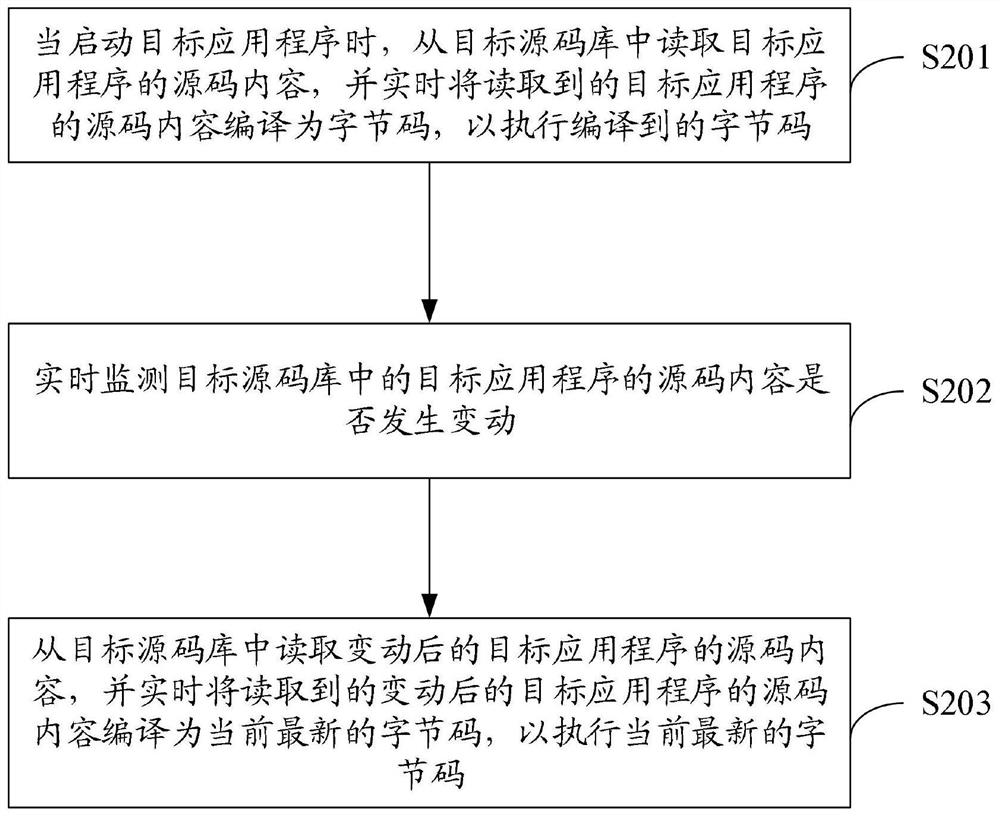
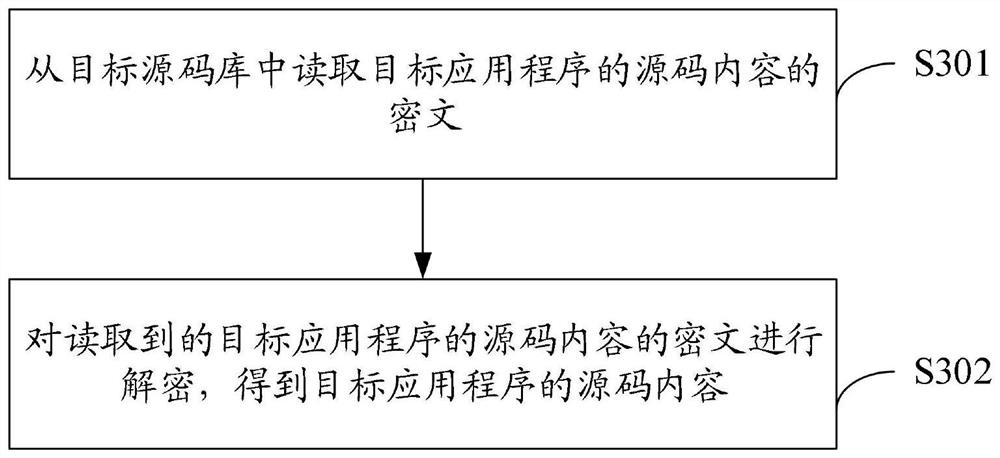
Source code hot loading method and device, electronic device and storage medium
PendingCN113703820AImplement hot loadingNormal serviceCode compilationSoftware engineeringSource code
The invention discloses a source code hot loading method and device, an electronic device and a storage medium, and can be applied to the distributed field or the financial field. The source code hot loading method comprises the steps of when a target application program is started, reading the source code content of the target application program from a target source code library, compiling the read source code content of the target application program into the byte codes in real time so as to execute the compiled byte codes; monitoring whether the source code content of the target application program in the target source code library is changed or not in real time; if it is monitored that the source code content of the target application program in the target source code library is changed, reading the changed source code content of the target application program from the target source code library, and compiling the read changed source code content of the target application program into a current latest byte code in real time; and executing the current latest byte code.
Owner:BANK OF CHINA
A system for managing large-scale container applications
ActiveCN110119308BImprove availabilityNormal serviceResource allocationHigh availabilityComputer engineering
Owner:北京零研科技有限公司
Controller cluster fault handling method, device, controller and controller cluster
Owner:NEW H3C SECURITY TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com